Discover and read the best of Twitter Threads about #BlueKeep
Most recents (3)
RDP brute-force attacks were up again in T2 2021, with 55 billion detections – a 104% increase compared to T1 2021. #ESETreserach also saw a massive surge in #RDP attacks against Spanish entities in August, accounting for a third of global all detections that month. 1/4 
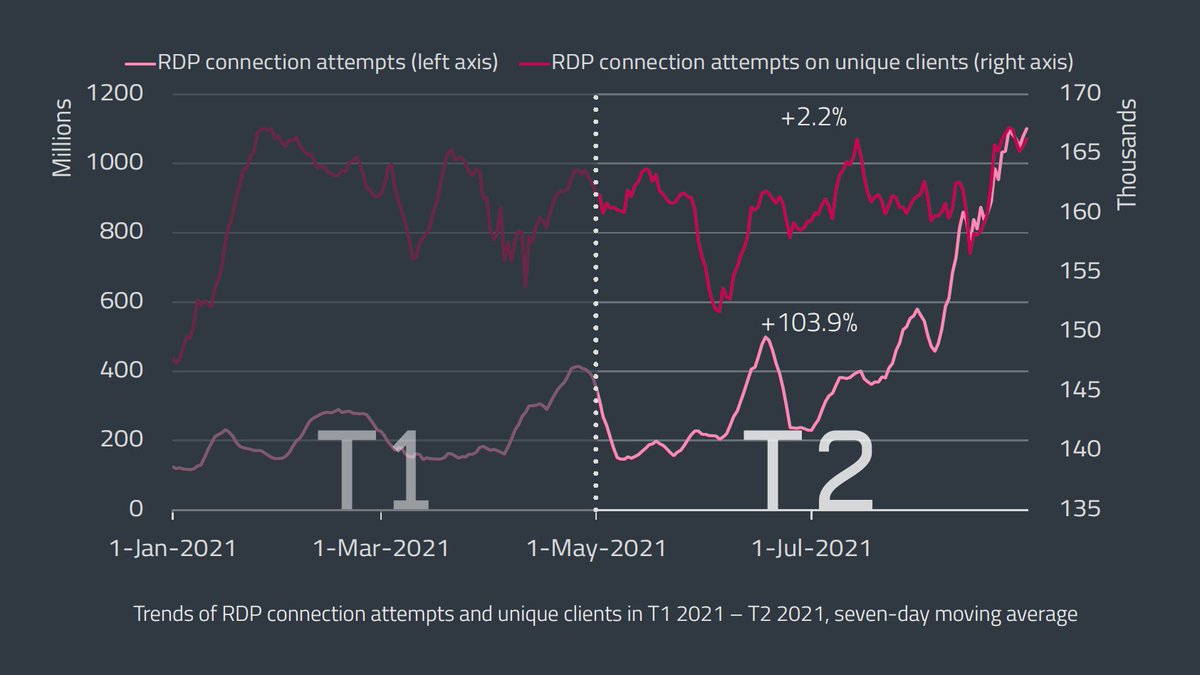
Attackers seem to have a hard time finding new #RDP targets, yet those that are already on their list are hit more aggressively, confirmed by an increase in average daily attacks per unique client, which doubled from 1,392 attempts in T1 2021 to 2,756 in T2 2021. 2/4 

Password guessing was the top external network intrusion vector with 53%, followed by attempts to exploit #ProxyLogon #vulnerabilities (22%) and attempted deployment of NSA backdoor #DoublePulsar (10%). 3/4 

Please enable Network Level Authentication (NLA) for a layer of pre-auth before a connection is established.
This not only reduces the terrifying #DejaBlue & #BlueKeep RDP attack surface, it's also a top ransomware protection recommendation from @Mandiant: fireeye.com/blog/threat-re…
This not only reduces the terrifying #DejaBlue & #BlueKeep RDP attack surface, it's also a top ransomware protection recommendation from @Mandiant: fireeye.com/blog/threat-re…

MSRC's @n0x08 notes in his regular checks that "RDP exposure is nearly 3x that of SMB & ~100% are running Windows." Keep an eye on his tweets and recommendations straight from the @msftsecresponse team.
Mandiant's protection & containment strategies (direct link: fireeye.com/content/dam/fi…) gives insight into methods observed and defenses that have worked against interactive, post-compromise deployment of ransomware.
@cglyer & I have covered this extortion trend on #StateOfTheHack
@cglyer & I have covered this extortion trend on #StateOfTheHack

New Unpatched Bug Could Allow Client-Side Attackers to Bypass #Windows Lock Screen On RDP Sessions
Read more — thehackernews.com/2019/06/rdp-wi…
All the attacker needs to do is… interrupt the network connectivity of a targeted client system and Tadaaaa...! the lock screen will disappear
Read more — thehackernews.com/2019/06/rdp-wi…
All the attacker needs to do is… interrupt the network connectivity of a targeted client system and Tadaaaa...! the lock screen will disappear
Starting with Windows 10 1803 and #Windows Server 2019, this flaw exists when login over #RDP requires the clients to authenticate with Network Level Authentication, an option that #Microsoft recently recommended as a workaround against the critical #BlueKeep RDP vulnerability.
Moreover...
"Two-factor authentication systems that integrate with the Windows login screen, such as Duo Security MFA, are also bypassed using this mechanism. Any login banners enforced by an organization will also be bypassed." @wdormann confirmed.
"Two-factor authentication systems that integrate with the Windows login screen, such as Duo Security MFA, are also bypassed using this mechanism. Any login banners enforced by an organization will also be bypassed." @wdormann confirmed.
