Discover and read the best of Twitter Threads about #CVE
Most recents (24)
1/5🚨
@Beosin_com discovered a vulnerability in #Circom verification library (CVE-2023-33252) and warns #ZK projects about the associated risks. Circom is a Rust-based compiler for zero-knowledge proof circuits, developed alongside the #SnarkJS library.
@identhree
@Beosin_com discovered a vulnerability in #Circom verification library (CVE-2023-33252) and warns #ZK projects about the associated risks. Circom is a Rust-based compiler for zero-knowledge proof circuits, developed alongside the #SnarkJS library.
@identhree
2/5
#SnarkJS enables proof systems implementation, including trusted setups, proof generation, and verification. It supports algorithms like #Groth16, #PLONK, and #FFLONK. @Beosin_com found a severe vulnerability in #SnarkJS versions up to 0.6.11.
#SnarkJS enables proof systems implementation, including trusted setups, proof generation, and verification. It supports algorithms like #Groth16, #PLONK, and #FFLONK. @Beosin_com found a severe vulnerability in #SnarkJS versions up to 0.6.11.
3/5
The vulnerability allowed attackers to forge multiple proofs that passed verification, enabling double-spending attacks. @Beosin_com promptly reported it, assisted in fixing the issue, and the vulnerability has now been patched. Upgrade to #SnarkJS 0.7.0 for security.
The vulnerability allowed attackers to forge multiple proofs that passed verification, enabling double-spending attacks. @Beosin_com promptly reported it, assisted in fixing the issue, and the vulnerability has now been patched. Upgrade to #SnarkJS 0.7.0 for security.
As auth coercion is blowing up due to #cve-2023-23397, I've put together a quick thread about how we at @MDSecLabs have been leveraging these techniques in our red team engagements for quite some time. Its timely, but I presented much of this at @FiestaCon_RT last week 🧵 

Traditionally if you wanted to abuse SMB auth coercion during a red team & over a c2, you were somewhat limited. It was however achievable using a mix of portbender, rportfwd and socks though. The main limitations were admin rights, dropping a driver and opsec of increased c2 

Just over two years ago, we evolved the tradecraft around this by documenting an alternate approach using WebDAV and a number of file primitives to coerce auth mdsec.co.uk/2021/02/farmin… 

#ESETResearch analyze first in-the-wild UEFI bootkit bypassing UEFI Secure Boot even on fully updated Windows 11 systems. Its functionality indicates it is the #BlackLotus UEFI bootkit, for sale on hacking forums since at least Oct 6, 2022. @smolar_m welivesecurity.com/2023/03/01/bla… 1/11
BlackLotus brings legit but vulnerable binaries to the victim’s system (#BYOVD) to exploit #CVE-2022-21894 and bypass UEFI Secure Boot on up-to-date Windows systems. In some samples, these binaries are downloaded directly from the MS Symbol Store. cve.mitre.org/cgi-bin/cvenam… 2/11 

Although the vulnerability was fixed in Microsoft’s January 2022 update, its exploitation is still possible by bringing vulnerable drivers to the system, as the affected binaries have still not been added to the UEFI revocation list. msrc.microsoft.com/update-guide/e… 3/11
1. Follina (CVE-2022-30190)
2. Log4Shell (CVE-2021-44228)
3. Spring4Shell (CVE-2022-22965)
2. Log4Shell (CVE-2021-44228)
3. Spring4Shell (CVE-2022-22965)
4. F5 BIG-IP (CVE-2022-1388)
5. Google Chrome zero-day (CVE-2022-0609)
6. Old but not forgotten - Microsoft Office bug (CVE-2017-11882)
5. Google Chrome zero-day (CVE-2022-0609)
6. Old but not forgotten - Microsoft Office bug (CVE-2017-11882)
#ESETResearch discovered and reported to the manufacturer 3 vulnerabilities in the #UEFI firmware of several Lenovo Notebooks. The vulnerabilities allow disabling UEFI Secure Boot or restoring factory default Secure Boot databases (incl. dbx): all simply from an OS. @smolar_m 1/9
Reported vulnerabilities – #CVE-2022-3430, #CVE-2022-3431, and #CVE-2022-3432 – affect various Lenovo Yoga, IdeaPad and ThinkBook devices. All affected devices with an active development support have been fixed after we reported them to the manufacturer. 2/9
While disabling UEFI Secure Boot allows direct execution of unsigned UEFI apps, restoring factory default dbx enables the use of known vulnerable bootloaders (e.g., #CVE-2022-34301 found by @eclypsium) to bypass Secure Boot, while keeping it enabled.
eclypsium.com/2022/08/11/vul… 3/9
eclypsium.com/2022/08/11/vul… 3/9
#WestAfrica: THREAD - "Militarized Border Security Will Not Stop the Spread of Extremism into Coastal States."
My latest with @lmcsanders and Jordon Moss for @PolicyCenterNS where we provide some suggestions to avoid/limit the spread to #Benin #Togo #IvoryCoast and #Ghana 1/
My latest with @lmcsanders and Jordon Moss for @PolicyCenterNS where we provide some suggestions to avoid/limit the spread to #Benin #Togo #IvoryCoast and #Ghana 1/
#WestAfrica: Border strategies must enable trade, communication, and travel. Increasing the burden
of legitimate behaviors will make communities more vulnerable, alienate essential allies, and
lead people to see border officers as the enemy. 2/
of legitimate behaviors will make communities more vulnerable, alienate essential allies, and
lead people to see border officers as the enemy. 2/
#WestAfrica: Border security must serve & engage border communities and their leaders. Those who
live in border zones understand local dynamics better than external forces. They have critical information of what is changing, and have the most to lose from extremist influence. 3/
live in border zones understand local dynamics better than external forces. They have critical information of what is changing, and have the most to lose from extremist influence. 3/
#CVE-2017-0199
An interesting example, using Vietnam's YSEALI College as bait.Vulnerability links are github.com/efimovah/abcd/… in the link contains multiple pieces of malware that have been confused.
Hash
A33AF82EBA873349ABB1CDE3BBD2D7F6
8691B36952F9B5842A9A26D391F70D88

An interesting example, using Vietnam's YSEALI College as bait.Vulnerability links are github.com/efimovah/abcd/… in the link contains multiple pieces of malware that have been confused.
Hash
A33AF82EBA873349ABB1CDE3BBD2D7F6
8691B36952F9B5842A9A26D391F70D88


A Critical Unauth RCE through arbitrary file upload was found in management console of following WSO2 products by @orange_8361
🔴 API Manager
🔴 Identity Server
🔴 Enterprise Integrator
🔴 API Manager
🔴 Identity Server
🔴 Enterprise Integrator
The vulnerability has CVSSv3 9.8 score assigned with CVE-2022-29464 & WSO2 Security Advisory WSO2-2021-1738
WSO2 has released security updates and mitigation guides docs.wso2.com/display/Securi…
Dr Anne (Azza) Aly, Aussie politician
Anne actively supports the Countering Violent Extremism (CVE) narrative & has a background in "counter-terrorism" & "counter-radicalization". Anne isn't part of the solution rather she is a Trojan horse within our faith community ... #1

Anne actively supports the Countering Violent Extremism (CVE) narrative & has a background in "counter-terrorism" & "counter-radicalization". Anne isn't part of the solution rather she is a Trojan horse within our faith community ... #1


Why certain personalities within the daw'aah, charity & academic spheres ignore this speaks volumes!
The "fruits" of Anne's support of Obama's CVE "initiative" are laid bare below 👇
sadruddinganjshakar.medium.com/houston-muslim… #2
The "fruits" of Anne's support of Obama's CVE "initiative" are laid bare below 👇
sadruddinganjshakar.medium.com/houston-muslim… #2
Spent some time today at work playing with @msftsecurity Windows InstallerFileTakeOver LPE (CVE-2021-41379 bypass - github.com/klinix5/Instal…) and managed to create some detections on it.
Detection will be based on Sysmon/SIEM, here we go... 1/n #threathunting #detection #dfir
Detection will be based on Sysmon/SIEM, here we go... 1/n #threathunting #detection #dfir
The exploit requires the user to overwrite elevation_service.exe with a compromised one (in this case with InstallerFileTakeOver.exe).
We can monitor this using #Sysmon event ID 11 - File Creation events:
We can monitor this using #Sysmon event ID 11 - File Creation events:
event_id:11 AND event_data.TargetFilename:*\\elevation_service.exe
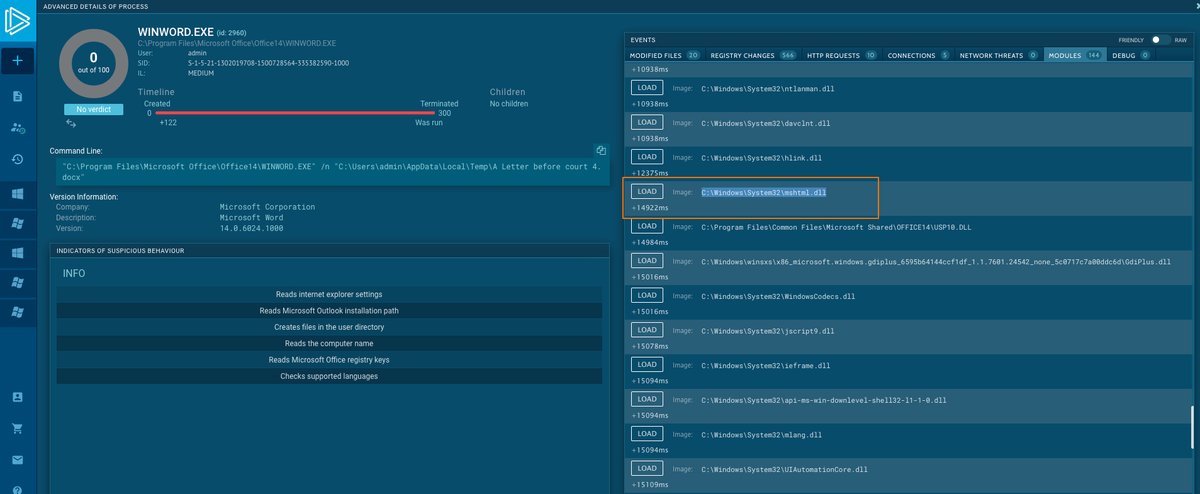
mshtml.dll was loaded into winword process, when Microsoft MSHTML used? I guess, it will be nice for #threathunting perspective
based on sample: app.any.run/tasks/36c14029…
possible another suspicious loads: ExplorerFrame.dll, ieproxy.dll
#CVE-2021-40444 #DFIR #BlueTeam
based on sample: app.any.run/tasks/36c14029…
possible another suspicious loads: ExplorerFrame.dll, ieproxy.dll
#CVE-2021-40444 #DFIR #BlueTeam
...run query on prod enviroment, last 30 days - 0 FPs hists. via (MDATP) @MSThreatProtect 

#RaisinaEdit offers a selection of commentaries that unpack, interpret, and problematise contemporary global developments corresponding to the Raisina Dialogue thematic pillars of 2021.
Curated by Harsh Pant and @WarjriLaetitia
#Raisina2021
Read ➡ bit.ly/32h18pv
Curated by Harsh Pant and @WarjriLaetitia
#Raisina2021
Read ➡ bit.ly/32h18pv

#RaisinaEdit | If “Data is the New Oil” then our individual data has intrinsic value and, thus, the monetisation of the collective data of millions of our citizens is the proverbial gold mine, says Abdul Hakeem Ajijola: or-f.org/85352
Economic interdependence, imperatives of political geography, and Beijing’s successful elite capture in many societies have made it difficult for many in Asia to contest the unfolding Chinese dominance over the region, points out @MohanCRaja #RaisinaEdit: or-f.org/85281
Upps an alle #Gamer mit Nvidia Treiber drauf ihr werdet zurzeit gehackt deinstall #GeForce #experience now #CVE is exploited #Hack
When the dust clears, folks will inevitably start talking about "countering violent extremism" #CVE aimed at the types of folks who stormed the capitol today. Here are a few things to think about.
What is CVE? Well, its a lot of diff things, lets go through them:
➡️ trying to ID potentially violent folks, very hard to do, where do you even start when you can't focus your resources on an identifiable minority as #CVE has done so far. No evidence it works at all.
➡️ trying to ID potentially violent folks, very hard to do, where do you even start when you can't focus your resources on an identifiable minority as #CVE has done so far. No evidence it works at all.
➡️ community outreach to build relations with "affected communities" in the hope they will tell you what's going on. Generally cops/DHS/FBI have mtgs with ppl they identify as community leaders. Not clear how this translates when you can't really identify a "community."
A hashtag appeared on panel asking for public hangings of rapists. I did initial data comparison of people who participated in this hashtag and various other hashtags. I found that
1) 27% users who were propagating "a woman shouldn't travel without a Mehram escorting her"
1) 27% users who were propagating "a woman shouldn't travel without a Mehram escorting her"
demanded public hangings of rapists.
2) 13% of "Travel with Mehram" advocates used abusive word "Randi" in their recent tweets while addressing some women on social media.
3) Out of users of "Randi" word in their recent tweets, 13% asked for public hangings
2) 13% of "Travel with Mehram" advocates used abusive word "Randi" in their recent tweets while addressing some women on social media.
3) Out of users of "Randi" word in their recent tweets, 13% asked for public hangings
4) 12% users who contributed to a hashtag glorifying Khalid's act of killing a person in the court, demanded public hangings of rapists.
5) 8% users who labelled #AuratMarch2020 as Fahashi and Aurat Barbadi march, now asked for public hangings of rapists
5) 8% users who labelled #AuratMarch2020 as Fahashi and Aurat Barbadi march, now asked for public hangings of rapists
#niet_in_journaal #nieuwsuur #1V #OP1 #bbvpro #NPORadio1 #global_jihad #Daesh Inside the secret plan to reboot #Isis from a huge digital backup wired.co.uk/article/isis-d…
Here's a digest of my understanding of #CVE-2020-1472 for the Microsoft Netlogon secure channel vulnerability and what you need to do to protect yourself. Thread. ⬇️
Firstly, what's the issue? Well it seems an attacker could essentially become a domain admin, without needing to authenticate to the DC. They just need line-of-site. Yikes.
What is netlogon? Domain-joined systems use the Netlogon Remote Protocol (MS-NRPC) for secure communications between a client machine and a DC for things such as DC discovery, authentication, password changes, etc. Is is also used for trusts between forests.
As a Romanian Jew, let me clear this up - Codreanu was to Romania what Hitler was to Germany and Mussolini was to Italy. ANY #CVE "deradicalization" expert who calls Codreanu "a Saint in my book" & rages about a (((parasite class))) is not a "former" neo-Nazi but an active one. 
Check this out - a "former" neo-Nazi working in CVE & proclaiming expertise in reforming extremists is openly praising the Romanian Iron Guard. @FFRAFAction @JoeMulhall_ @MichaelEHayden @letsgomathias @jaredlholt @egavactip @hopenothate @AmarAmarasingam @MackLamoureux @Hatewatch
TIP: if you're an anti-racist group led by former neo-Nazis who claim expertise in deradicalizing extremists - having a spokesman who worships the Iron Guard, praises David Irving's "valuable insight" & lauds "degeneracy" laws that "threw homosexuals in jail" is a bad look. #CVE
It's a total grift. I put 3 white supremacists leaders in jail solely on my testimony, helped shut down a hate group, turned 30 affidavits to police re guns/crime and lived in poverty & hiding for yrs. And unlike those who risked nothing, I wasn't offered a book, movie or TV deal
The CVE field is rampant w/ grifters & profiteers. After being groomed & exploited by neo-Nazis as a teen girl, I was exploited by @CBC, who took my life from headlines & made a movie that attributed it to another woman - a "former" who stole my story and marketed it as her own.
As I lived in hiding & dumpster-dived for food to stay alive, @CBC & @onemooreliz were making money & publicity from my life story. I made a difference - and others tried to steal it from me, knowing I wasn't well-connected & didn't have $$ to hire lawyers incognitopress.wordpress.com/2020/02/02/the…
In non-impeachment news, @ewarren just put out a plan to fight white nationalist violence. Thread on why it's really pretty good. elizabethwarren.com/plans/confront…
It focuses on white nationalist VIOLENCE, rather than speech or ideology thus avoiding slippage between speech and action that we have seen in other contexts (e.g., targeting Muslims for terrorism based on their religious beliefs rather than their actions).
Recent @UN Security Council report @UN_CTED the current state of ISIL, Al-Qaeda, and associated individuals and entities. un.org/securitycounci… Grab a fresh cup of coffee and follow along as I highlight some key points that stood out to me......
@UN @UN_CTED 1. “ISIL, however, remains much stronger than AQ in terms of finances, media profile and current combat experience and terrorist expertise and remains the more immediate threat to global security.” There there's the death of Hamza bin Ladin. brookings.edu/blog/order-fro… @dbyman
@UN @UN_CTED @dbyman 2. @azelin‘s has documented how AQ has “survived drones, uprisings, and the Islamic State.” Read more about the group’s survival mechanisms in this @WashInstitute Policy Focus. washingtoninstitute.org/policy-analysi…
THREAD: here is some expansion on what I discussed on @MSNBC @KasieDC RE: what could be done yesterday to elevate our Federal #DomesticTerrorism prevention efforts, h/t to @tribelaw for the thread prompt and @SeamusHughes for his insight 1/
My former office, @DHSgov Ofc of Targeted Violence and Terrorism Prevention once had a budget of $22 mil now $2.7-3 mil and once 40 FTEs now 7-10 FTEs, the #Trump Admin actively atrophied the office w/ specific focus on #DomesticTerrorism prevention programming 2/
This systematic atrophy included the pulling back of announced grant funding for programs specific to #DomesticTerrorism (DT) prevention, grant award were pulled back from #LifeAfterHate bc the org was critical of #Trump for example (evidence in FOIA req) 3/




