Discover and read the best of Twitter Threads about #Encryption
Most recents (24)
Smartphone storage capacity stats:
- 62% run out of storage space every 3 months
- 65% regretted deleting precious photos or videos to free up storage space
- 36% would delete a photo of themselves instead of friends, pets or family
Research from India> timesnownews.com/technology-sci… twitter.com/i/web/status/1…
- 62% run out of storage space every 3 months
- 65% regretted deleting precious photos or videos to free up storage space
- 36% would delete a photo of themselves instead of friends, pets or family
Research from India> timesnownews.com/technology-sci… twitter.com/i/web/status/1…
DeNet aims to address these issues. No need to worry about security of cloud storages or their prices as DeNet Storage is the solution with unique file replication and #encryption. Its pay-as-you-go pricing model ensures users only pay for what they use.
Switch to DeNet for hassle-free decentralized storage > links.denet.app/mobile?tw=both… 

Go is a programming language that comes with a rich standard library containing many useful packages and modules. In this, I provide an overview of the standard library modules in Go.
#golang #library
🧵👇
#golang #library
🧵👇
From your bank statements and travel documents, to your company’s financial data and customer details – you can easily make sure they don’t become exposed on the internet.
Here are some ways to protect your sensitive documents when exchanging them online 🧵👇 (1/6)
Here are some ways to protect your sensitive documents when exchanging them online 🧵👇 (1/6)

Here's how you can protect the emails you send to recipients who don't use Proton Mail: proton.me/support/open-p…. (3/6) 

🧵 While #ChatGPT is grabbing the headlines, pushing @GoogleAI (#LaMDA) and @Baidu_Inc to rush their plans to launch competitors, maybe it’s time to explore the security/privacy concerns generative AIs raise.
Here's a #thread on some of these, brought to you by @InfosecurityMag.
Here's a #thread on some of these, brought to you by @InfosecurityMag.

@GoogleAI @Baidu_Inc @InfosecurityMag First, @OpenAI’s #ChatGPT has already been used to develop #malware and other malicious tools, as @a_mascellino reported on January 9, 2023. #encryption #cybercrime cc @SShykevich @_CPResearch_
infosecurity-magazine.com/news/chatgpt-d…
infosecurity-magazine.com/news/chatgpt-d…
@GoogleAI @Baidu_Inc @InfosecurityMag @OpenAI @a_mascellino @SShykevich @_CPResearch_ Here’s the original @_CPResearch_ report 👇
Wanna know bout the effect on national security & global stability of #QuantumHacking in #Web3 #Crypto #AI #VR & #AR by nation-state-backed hacker groups like #USCyberCommand, #NorthKorea, #Iran, #Russia, & #China?
You do? Here's you're TL;DR to minimize your Units of Attention
You do? Here's you're TL;DR to minimize your Units of Attention
APT (Advanced Persistent Threat) groups are a prime example of nation-state-backed hacker groups
#CozyBear (APT29), #LazarusGroup (APT38), #DoubleDragon (APT41), #FancyBear (APT28), and #HelixKitten (APT34) are some of the most well-known APT groups
#CozyBear (APT29), #LazarusGroup (APT38), #DoubleDragon (APT41), #FancyBear (APT28), and #HelixKitten (APT34) are some of the most well-known APT groups
These groups have been known to carry out cyber espionage, intellectual property theft, and sabotage. For instance, the #FancyBear APT group was responsible for the alleged 2016 US election interference
Thread alert! 🚨
If you are #newtocrypto & #web3, this thread🧵 should be just what you need to begin understanding the basics of #crypto, and why you should care:
So...What are #cryptocurrencies, and why should you care?!
If you are #newtocrypto & #web3, this thread🧵 should be just what you need to begin understanding the basics of #crypto, and why you should care:
So...What are #cryptocurrencies, and why should you care?!

At the heart of it, cryptocurrencies are digital currencies or assets that exist independently from governments or central banks. #Bitcoin is the first, and best known cryptocurrency.
Because of the underlying technology that cryptocurrencies are built upon, they give users the ability to transfer value & digital assets to other people without the need for an intermediary such as a bank. This is known as a peer-to-peer transaction.
1/6 📢Today the @EU_Commission's @YlvaJohansson is presenting the Child Sexual Abuse Regulation #CSAR to the Members of the European Parliament @EP_Justice. #KeepItSecure
➡️Our take: edri.org/our-work/johan…
📹LIVE now: multimedia.europarl.europa.eu/en/webstreamin…
➡️Our take: edri.org/our-work/johan…
📹LIVE now: multimedia.europarl.europa.eu/en/webstreamin…

2/6 In the name of protecting children, the EU wants to surveil people’s private messages.
🙅🏾♀️The verdict is: everyone is guilty until proven innocent.
They suggest using dangerous tech that will undermine #encryption & block people from accessing legitimate online services.🔓
🙅🏾♀️The verdict is: everyone is guilty until proven innocent.
They suggest using dangerous tech that will undermine #encryption & block people from accessing legitimate online services.🔓
3/6 UN’s top human rights authority confirms that privacy keeps everyone safe.
This includes journalists, human rights defenders, minoritised groups & children.
Without privacy, young people facing abuse online & offline won't be able to use safe digital spaces to seek help.
This includes journalists, human rights defenders, minoritised groups & children.
Without privacy, young people facing abuse online & offline won't be able to use safe digital spaces to seek help.
What is a #consensus mechanism?
Quick 🦉 fact before we dive in..
Did you know that the collective noun for a group of owls is a ‘Parliament’?
This is a great starting point to understanding #consensus mechanisms on a #blockchain
Quick 🦉 fact before we dive in..
Did you know that the collective noun for a group of owls is a ‘Parliament’?
This is a great starting point to understanding #consensus mechanisms on a #blockchain
1/ A #consensus mechanism on #blockchain is the process by which participants ‘agree’.
A bit like #voting in a #parliament.
This simple diagram describes the basic process:
A bit like #voting in a #parliament.
This simple diagram describes the basic process:

2/ #consensus is critical to #blockchain because it determines how #data is added to the #database - that is, how the next #block is added to the chain, which as we explained last week is secured by #encryption
Today the European Commission will publish a proposal for a new law which will make the interception, analysis and monitoring of *ALL* digital communications (messengers, forums, direct messages etc.) mandatory.
#privacy #humanrights #chatcontrol #surveillance #dignity #csam
#privacy #humanrights #chatcontrol #surveillance #dignity #csam
Let me be clear - this is ILLEGAL under EU Treaties and Case Law under the principles of proportionality and necessity. This new law will turn the EU into a surveillance state.
#privacy #humanrights #chatcontrol #surveillance #dignity #csam #childsexualabuse
#privacy #humanrights #chatcontrol #surveillance #dignity #csam #childsexualabuse
So...What is DERO?
I hope to have created something we can all use. I try to draw as much context as I reasonably can
Lets get it
We on our way fam 😉
$DERO #DERO
#privacy #encryption
1/49...eesh
I hope to have created something we can all use. I try to draw as much context as I reasonably can
Lets get it
We on our way fam 😉
$DERO #DERO
#privacy #encryption
1/49...eesh
What is DERO?
DERO is a general purpose platform for building unstoppable decentralised applications and securely transferring value. It has been built from scratch.
DERO is a general purpose platform for building unstoppable decentralised applications and securely transferring value. It has been built from scratch.
It is the goal of DERO to create a sound monetary framework that will globally safeguard the privacy of all users and empower free markets to thrive, while maintaining complete auditability.
In an opinion-editorial by @htTweets, the study by DeepStrat & @_DialogueIndia - ‘Analysing the #NationalSecurity Implications of Weakening #Encryption’ was featured for its account on the #security vs. security debate involving the fundamental nature of #endtoendencryption. 

The article sheds light on the #traceability challenges in #India, as identified in the report, which could potentially create vulnerabilities in modern #devices, #communication architecture and #cybersecurity, that can be exploited by bad actors.
hindustantimes.com/opinion/in-per….
hindustantimes.com/opinion/in-per….
The importance of #endtoendencryption (#E2EE) is in ensuring #InformationalPrivacy, #safety & #security of the #citizens; and, the #nationalsecurity of the State. Here are the key recommendations of the report - Analysing National Security Implications of Weakening #Encryption. 

Ppl fundamentally don't understand what is #crypto #defi #nfts, what's revolutionary about them, and why they exist.
Elaborating on @Wonderland_fi @danielesesta @0xSifu Scandal.
#Wonderland #FrogNation $FTM $ICE $TIME $MIM $SPELL
Thread (0/17) 🧵👇👇👇
Elaborating on @Wonderland_fi @danielesesta @0xSifu Scandal.
#Wonderland #FrogNation $FTM $ICE $TIME $MIM $SPELL
Thread (0/17) 🧵👇👇👇
1/ Now, I understand that you're scared, cuz that's your money & it's totally normal to be emotional.
But emotions and money don't work well together, if they work together at all.
A 99% of the rich are emotionless shits, &never care about anyone and anything except themselves
But emotions and money don't work well together, if they work together at all.
A 99% of the rich are emotionless shits, &never care about anyone and anything except themselves
2/ That's exactly why we built all these #dApps, #DAOs, protocols, blockchains, communities, and networks. That's why we fight for #privacy & #security, for end-to-end #encryption. That's why we build on top of #mathematics and #cryptography. That's why multi-sig exist.
🇬🇧 The EU Commission could break securely #E2EE encrypted communications with the upcoming #chatcontrol2.0 proposal. If all messaging providers were forced to search private messages, this would require backdoors and undermine security! (1/7)
Attacks on #encryption are brought forward by governments time and again. Most recently here, in a November Council resolution: data.consilium.europa.eu/doc/document/S…
The idea: access to encrypted messages only "for the good guys/law enforcement authorities"
A fallacy.. (2/7)
The idea: access to encrypted messages only "for the good guys/law enforcement authorities"
A fallacy.. (2/7)
..because #encryption either works for all of us, or it works for no one at all. Once broken, and be it with best intentions, backdoors in encrypted communications are accessible to anyone who wants to use them – including criminal hackers (3/7)
Right, I've had enough. We need to talk about what #encryption, #hashing and #encoding are. They are distinct things that do distinct jobs and whether you are in #CyberSecurity or not, every #coder should know the difference. So... 🧵👇
#learning #webdev #100DaysofCode
#learning #webdev #100DaysofCode
Let's start with the simplest; encoding. This is a reversible process where you transform some data into another format, then transform it back (decode) to the original without any keys etc.
Examples: json encoding, base64 encoding, html characters conversion and compression.
Examples: json encoding, base64 encoding, html characters conversion and compression.
Encoding is most useful for transmitting and storing data. For instance, base64 is great to ensure that "unusual" characters like {};[]!'" etc can be saved / sent safely.
ENCODING PROVIDES ZERO SECURITY. None. Anyone can decode your data, it's not meant for that.
I'm calm... 😅
ENCODING PROVIDES ZERO SECURITY. None. Anyone can decode your data, it's not meant for that.
I'm calm... 😅
So what *is* this "Digital Regulation: Driving growth & unlocking innovation" policy paper? Another "strategy"? A white paper for #DPA2022?
If it's about #regulation, then how will @OliverDowden's "unashamedly pro-tech approach" protect people's #rights?
gov.uk/government/pub…
If it's about #regulation, then how will @OliverDowden's "unashamedly pro-tech approach" protect people's #rights?
gov.uk/government/pub…
In his introduction to "#ThePlan", @OliverDowden says he'll "shortly publish a #plan for a pro-growth data regime" 🤔
If he has an ACTUAL plan, or frankly a clue, then why not just #publish the damn thing? Why all the waffle?
Hand-wavy platitudes like these 👇 ain't worth Jack:
If he has an ACTUAL plan, or frankly a clue, then why not just #publish the damn thing? Why all the waffle?
Hand-wavy platitudes like these 👇 ain't worth Jack:

Just so we're clear, this "#Plan" is supposed to "start a #conversation" about "#TenTechPriorities" that @DCMS published on a "shorthand stories"(?) page that DOESN'T ONCE MENTION PEOPLE'S #RIGHTS!!
dcms.shorthandstories.com/Our-Ten-Tech-P…
Does this Government think it can take us for fools?
dcms.shorthandstories.com/Our-Ten-Tech-P…
Does this Government think it can take us for fools?
Here are the seven key recommendations from the Expert Stakeholder Consultation Report on the Indian #Encryption Debate.
Access the full report here: thedialogue.co/wp-content/upl…
1/8
Access the full report here: thedialogue.co/wp-content/upl…
1/8

A mandate for #backdoors to #encryption or originator #traceability does not fulfill the #Puttaswamy test and must be revisited.
2/8
2/8
#OriginatorTraceability mandate would result in practical complications for industry; become an obstacle to small businesses & #innovation; & the end product will be difficult to sell in the Int'l market. Such a mandate should not be implemented without further consultation.
3/8
3/8
#WhatsApp is taking the Indian government to court over the traceability clause in the new IT Rules 2021.The new IT rules include a traceability clause that requires #socialmedia platforms to locate “the first originator of the information” if required by authorities.
In its plea, it is learnt #WhatsApp is invoking the 2017 Justice KS Puttaswamy vs Union Of India case to argue that the traceability provision is unconstitutional and against people’s fundamental right to #privacy as underlined by the SC decision indianexpress.com/article/techno…
The #ITRules 2021 came into effect on February 25, and today is the deadline for significant social media intermediaries to comply with new obligations under the IT Rules 2021.
sflc.in/analysis-infor…
#OTTGuidelines
#SocialMediaguidelines
sflc.in/analysis-infor…
#OTTGuidelines
#SocialMediaguidelines
The Rules could undermine the principles of open & accessible internet, the fundamental #RightToPrivacy & #FreeSpeech & expression enshrined in the Constitution.
#DigitalIndia #SocialMedia #ILRules #DigitalDefenders
#DigitalIndia #SocialMedia #ILRules #DigitalDefenders
#SocialMediaGuidelines
What are the major due diligence requirements that have to be observed by an #intermediary ?
#Datacracy #ottguidelines #SocialMedia #ITRules



What are the major due diligence requirements that have to be observed by an #intermediary ?
#Datacracy #ottguidelines #SocialMedia #ITRules




A thread on how I managed to encrypt and store a video using #Flutter
Scroll for links, code snippets, and my general thought process...
Scroll for links, code snippets, and my general thought process...
Recording and saving videos locally isn't too difficult.
Dependencies:
- camera
- path_provider
#flutter #android #s21 #video #coding
Below is the code for getting a file reference:
Created with @carbon_app
Dependencies:
- camera
- path_provider
#flutter #android #s21 #video #coding
Below is the code for getting a file reference:
Created with @carbon_app

Encryption on the other hand is a foreign language to me. From my research, I learned that each user needs an #AsymmetricKeyPair that can be used to #encrypt and #decrypt data.
To generate these, I used the rsa_encrypt package.
pub.dev/packages/rsa_e…
To generate these, I used the rsa_encrypt package.
pub.dev/packages/rsa_e…
This thread brings together all my #infographics until today (2years of work).
These are all infographics about #infosec 🔐
Feel free to share this tweet if you think it may be useful for your #community 📚
Follow me ➡ @SecurityGuill fore more about #security #hacking #news



These are all infographics about #infosec 🔐
Feel free to share this tweet if you think it may be useful for your #community 📚
Follow me ➡ @SecurityGuill fore more about #security #hacking #news
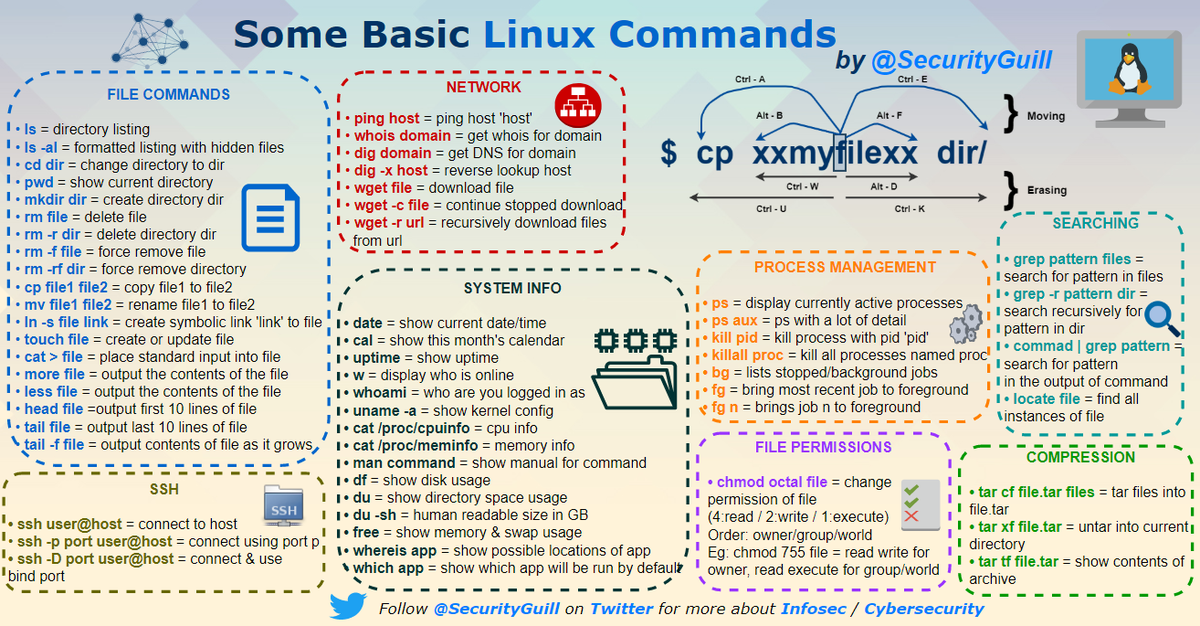



How does an #Antivirus works? 

Quick presentation of the different #Bluetooth Hacking Techniques 

(1/of a few) Doing some training #threathunting runs with #suricata -with pcap from bit.ly/3jNUCyw
Fun fact: Alerts count only for 8% of the total logs produced - we also have protocol logs like Flow records, KRB5, SMB, DNS, TLS, HTTP, DCERPC,Fileinfo
Fun fact: Alerts count only for 8% of the total logs produced - we also have protocol logs like Flow records, KRB5, SMB, DNS, TLS, HTTP, DCERPC,Fileinfo

(2/of a few)
Just as regular protocol and flow logging of #Suricata gives us:
633 FLOW logs
295 HTTP logs
182 TLS logs
130 DNS logs
114 SMB logs
90 DCERPC logs
66 FILEINFO logs
23 KRB5 logs
2 NTP logs
Let's see some examples of the generated data...
Just as regular protocol and flow logging of #Suricata gives us:
633 FLOW logs
295 HTTP logs
182 TLS logs
130 DNS logs
114 SMB logs
90 DCERPC logs
66 FILEINFO logs
23 KRB5 logs
2 NTP logs
Let's see some examples of the generated data...
(3/of a few)
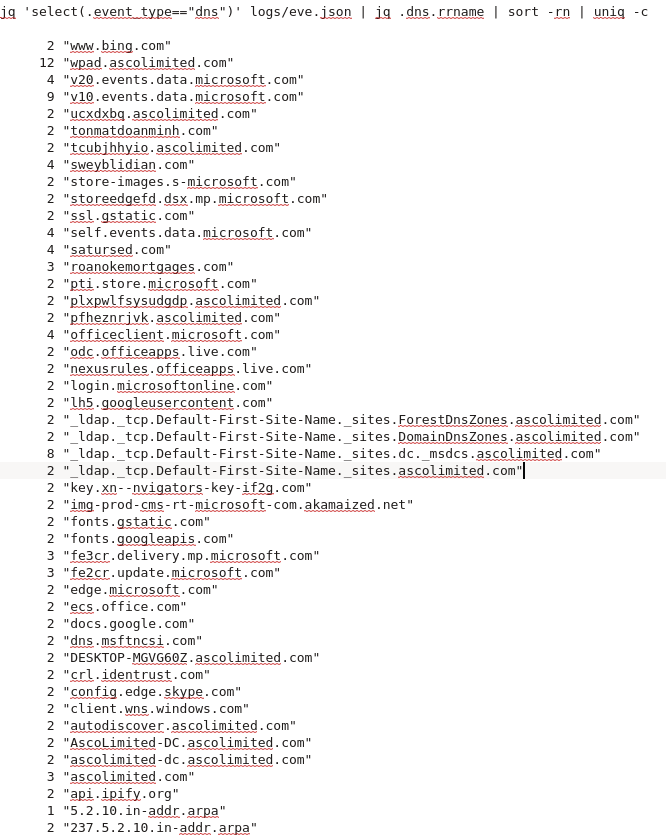
Quick and dirty cmd look at the DNS logs generated by #Suricata gives us the domain list for our #threathunting review
Couple of those jump out (at lest to me)
Quick and dirty cmd look at the DNS logs generated by #Suricata gives us the domain list for our #threathunting review
Couple of those jump out (at lest to me)
#Sidewinder #APT
It seems that #Indian APTs have been raging war on #Pakistan with the same payloads over and over again. Meanwhile, Pakistani #Government and #Military is either helpless or over occupied. Following is another new sample that goes ages back.
It seems that #Indian APTs have been raging war on #Pakistan with the same payloads over and over again. Meanwhile, Pakistani #Government and #Military is either helpless or over occupied. Following is another new sample that goes ages back.
A variant of this sample has attributed to #Sidewinder #APT by Govt. of Pak. The #malware is deployed using the shared image in a #phishing email using a similar methodology to that of 

Daily Bookmarks to GAVNet 01/18/2021 greeneracresvaluenetwork.wordpress.com/2021/01/18/dai…
Millions Flock to Telegram and Signal as Fears Grow Over Big Tech
nytimes.com/2021/01/13/tec…
#privacy #CommunicationPlatforms #MessagingServices #encryption
nytimes.com/2021/01/13/tec…
#privacy #CommunicationPlatforms #MessagingServices #encryption





