Discover and read the best of Twitter Threads about #SwearEngine
Most recents (3)
Sure this doc
C:\Users\zhenmingda\Desktop\application_form.doc
created by "Bil Smith" 🙈
contains an embedded stylesheet (coal.xsl) launched with #squiblytwo
and downloads loprtaf[.]icu/dctch.exe
But it also has some dirty macros. #SwearEngine
VT (14/58): virustotal.com/gui/file/324ac…


C:\Users\zhenmingda\Desktop\application_form.doc
created by "Bil Smith" 🙈
contains an embedded stylesheet (coal.xsl) launched with #squiblytwo
and downloads loprtaf[.]icu/dctch.exe
But it also has some dirty macros. #SwearEngine
VT (14/58): virustotal.com/gui/file/324ac…



Here's a link to the file on @virusbay_io:
💾beta.virusbay.io/sample/browse/…
Some interesting techniques - including some unique obfuscation. No wonder Bil was working on it for 3 hours...
Here's the extracted MSXSL: beta.virusbay.io/paste/browse/5…
💾beta.virusbay.io/sample/browse/…
Some interesting techniques - including some unique obfuscation. No wonder Bil was working on it for 3 hours...
Here's the extracted MSXSL: beta.virusbay.io/paste/browse/5…

@virusbay_io loprtaf[.]icu SSL certificate is not at all suspicious
Issuer: C=US, CN=Let's Encrypt Authority X3, O=Let's Encrypt
Validity
Not Before: 2019-08-03 11:07:50
Not After: 2019-11-01 11:07:50
Subject: CN=pofhssri[.]pw
Issuer: C=US, CN=Let's Encrypt Authority X3, O=Let's Encrypt
Validity
Not Before: 2019-08-03 11:07:50
Not After: 2019-11-01 11:07:50
Subject: CN=pofhssri[.]pw
🆕 🔥 Research on PDB Paths from @stvemillertime: fireeye.com/blog/threat-re…
#DFIR primer & exploration of these wonderful artifacts.
Followed by a survey of malware PDB conventions, PDB anomalies, attacker mistakes. All with attribution, including Western gov.
THREAD (1/n)



#DFIR primer & exploration of these wonderful artifacts.
Followed by a survey of malware PDB conventions, PDB anomalies, attacker mistakes. All with attribution, including Western gov.
THREAD (1/n)




Includes considerations for #threatintel shops, red teams/operators, and weaknesses in PDB paths.
Blog also has: the most malware code families and threat groups we've ever published, some spicy groups, and some light swearing (malware devs are potty mouths) #SwearEngine
2/n

Blog also has: the most malware code families and threat groups we've ever published, some spicy groups, and some light swearing (malware devs are potty mouths) #SwearEngine
2/n


I love that @stvemillertime surfaced a bunch of strange PDB path anomalies and dug in with @mikesiko's #FLARE team to get to ground truth & replicate the artifact.
fireeye.com/blog/threat-re…
Where my #DFIR followers at?
❓ Curious if you've found other anomalies not listed?
3/n

fireeye.com/blog/threat-re…
Where my #DFIR followers at?
❓ Curious if you've found other anomalies not listed?
3/n


The basis for #SwearEngine is that malware developers are developers too. The catharses in their malware code manifest in a multitude of coarse expressions. Thus we can use the presence of swear words as a "weak signal" to surface interesting files. #threathunting 
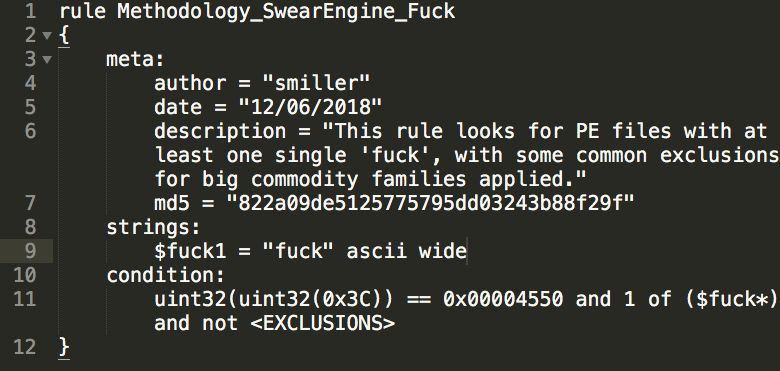
You may balk at #SwearEngine for being #basic but consider that this rule, looking for PEs with one single "fuck", detects malware samples used by APT5, APT10, APT18, APT22, APT26, Turla, FIN groups, dozens of UNC espionage clusters. Too many to list.
At least one single "fuck" is present in some samples of the following malware families: AGENTBTZ, ASCENTOR, ZXSHELL, SOGU, TRICKBOT, GHOST, VIPER, WANNACRY, WARP, NETWIRE, COREBOT, REMCOS, VIPER, ORCUSRAT, PONY, etc. I can't even name the coolest ones. There are hundreds.
