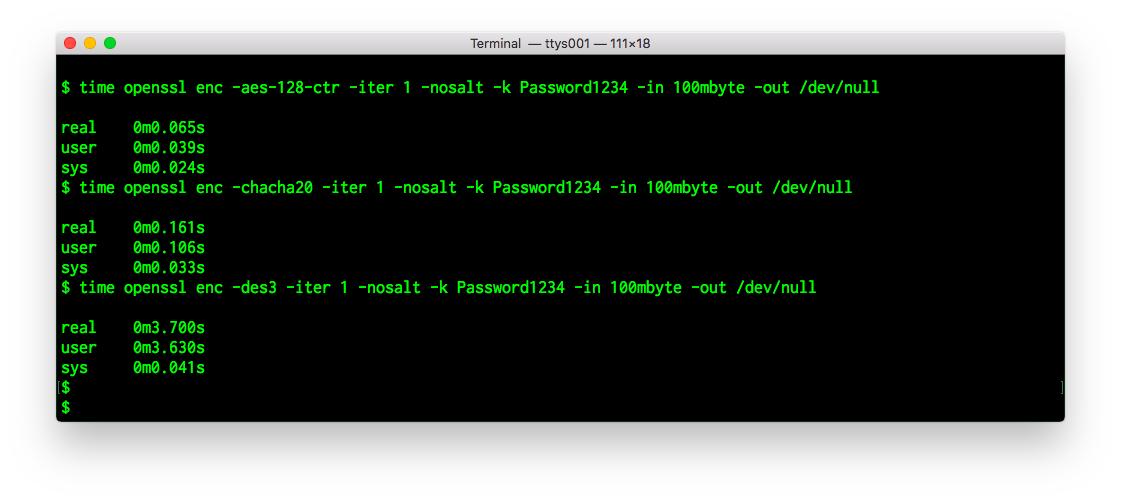
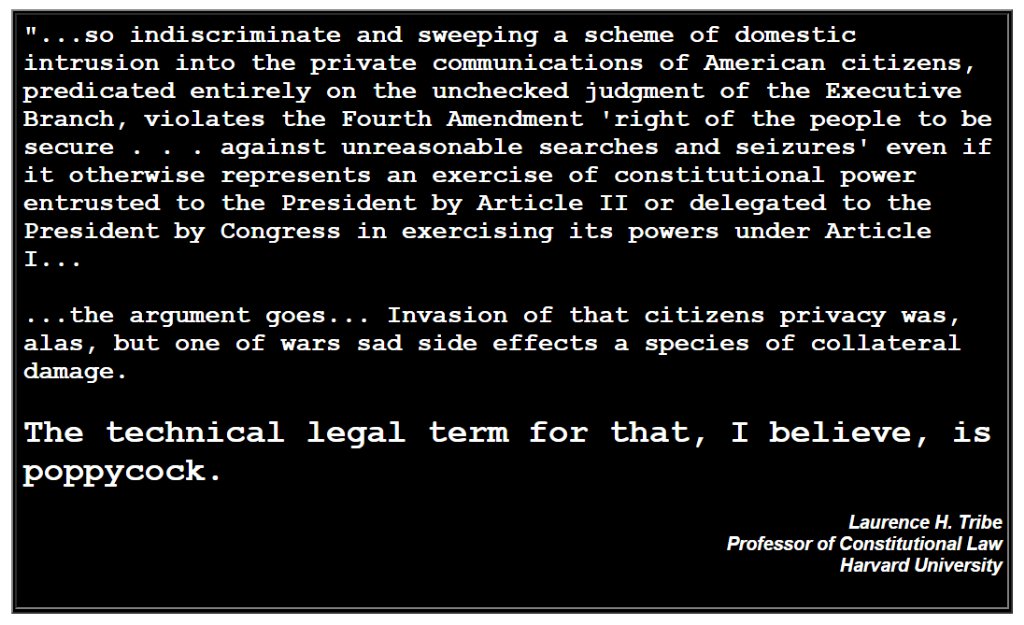
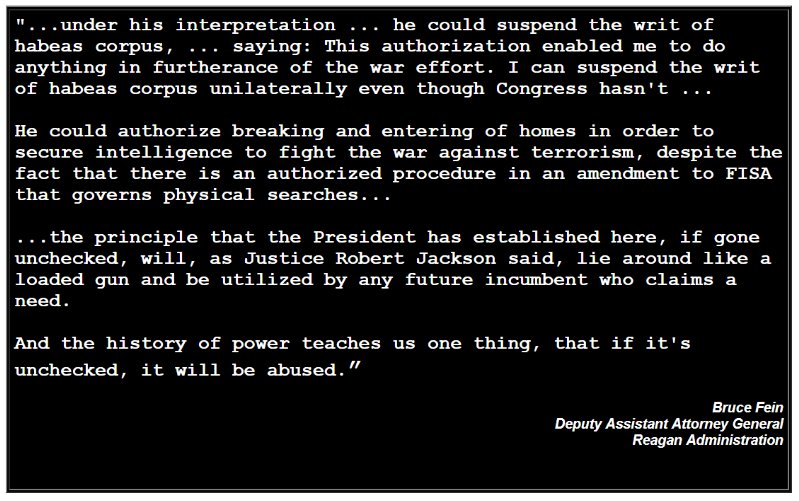
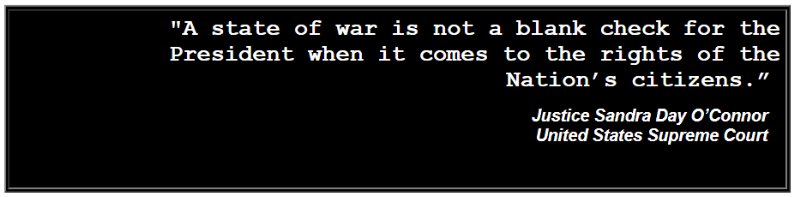
DES was the algorithm first standardized in 1977 that was then successfully cracked with Deep Crack in 1998, because it has only a 56-bit key that can be easily brute-forced (guessing all possible keys) by modern desktop computers.
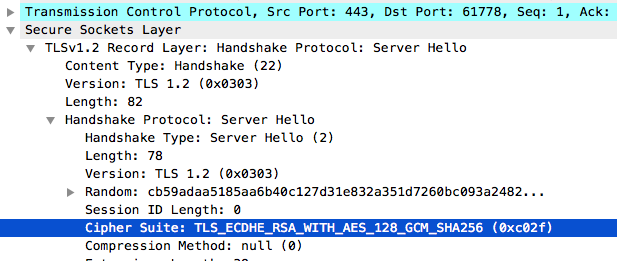
TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256