Discover and read the best of Twitter Threads about #Decoding
Most recents (5)
Go is a programming language that comes with a rich standard library containing many useful packages and modules. In this, I provide an overview of the standard library modules in Go.
#golang #library
🧵👇
#golang #library
🧵👇
🐀 AsyncRAT 🐀 - Defeating Obfuscation Using CyberChef
An overview of some advanced CyberChef tricks for decoding malware
[1/12] 🧵
#AsyncRAT #Decoding #CyberChef #Malware



An overview of some advanced CyberChef tricks for decoding malware
[1/12] 🧵
#AsyncRAT #Decoding #CyberChef #Malware

[2/] First, some links if you wish to follow along.
The Malware File: bazaar.abuse.ch/sample/26c9f29…
Links to CyberChef Recipes:
github.com/embee-research…
The Malware File: bazaar.abuse.ch/sample/26c9f29…
Links to CyberChef Recipes:
github.com/embee-research…
Ursnif Loader (Javascript) - Manual Decoding Using Cyberchef
[1/13] 👇🧵
#Cyberchef #Decoding #Ursnif #Malware



[1/13] 👇🧵
#Cyberchef #Decoding #Ursnif #Malware




[1.1] A quick summary/TLDR before we get started
- Remove comments (manually or using regex)
- Remove "split" strings (manually or using regex)
- Remove obfuscated numbers
- (optional) Rename Variables
- Apply beautifier and syntax highlight
- Remove comments (manually or using regex)
- Remove "split" strings (manually or using regex)
- Remove obfuscated numbers
- (optional) Rename Variables
- Apply beautifier and syntax highlight
[2] First, I downloaded the sample from Malware Bazaar and loaded it into a safe analysis VM.
You can find the same sample here
bazaar.abuse.ch/sample/2a72302…
You can find the same sample here
bazaar.abuse.ch/sample/2a72302…
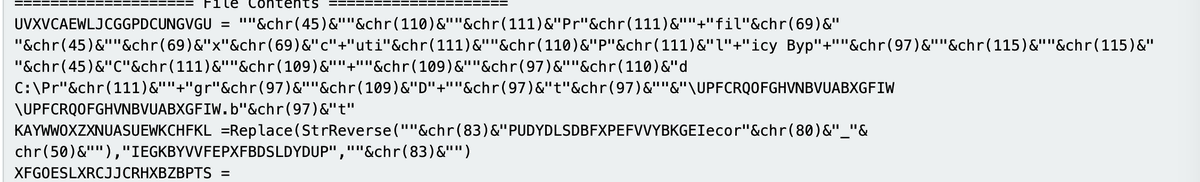
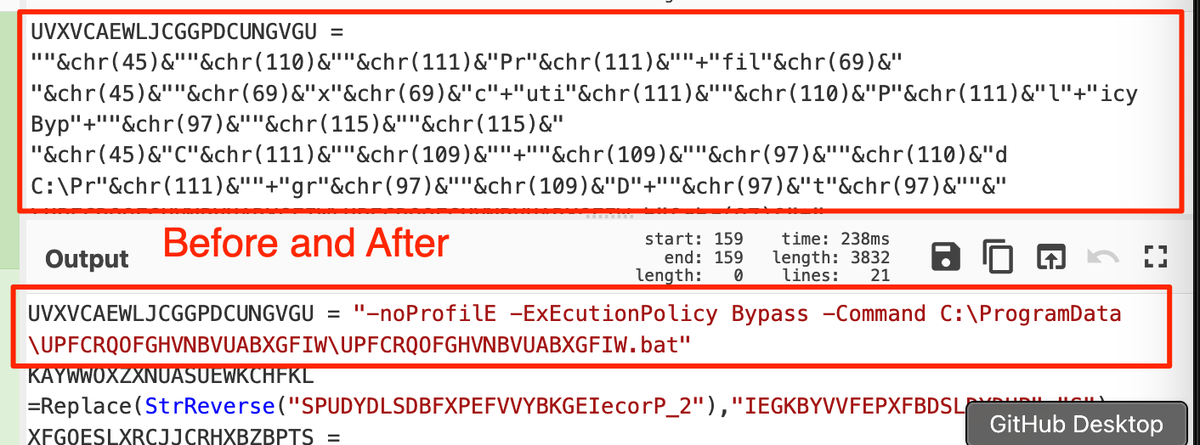
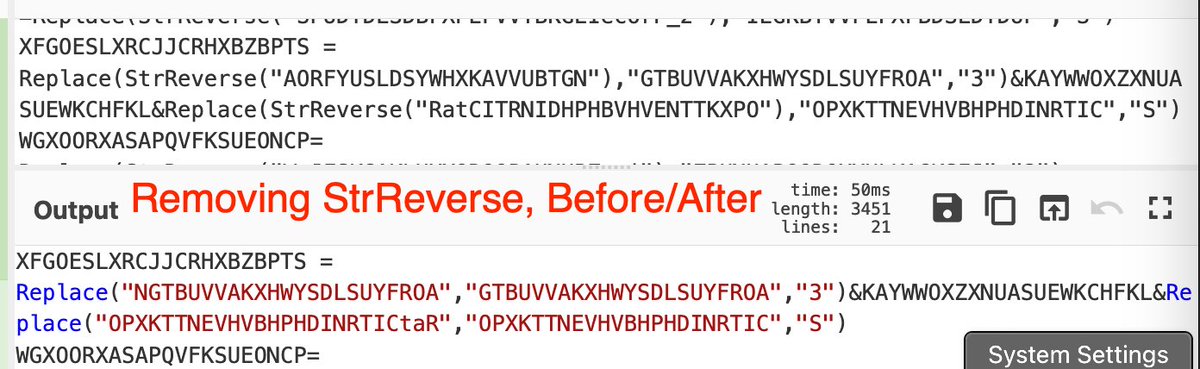
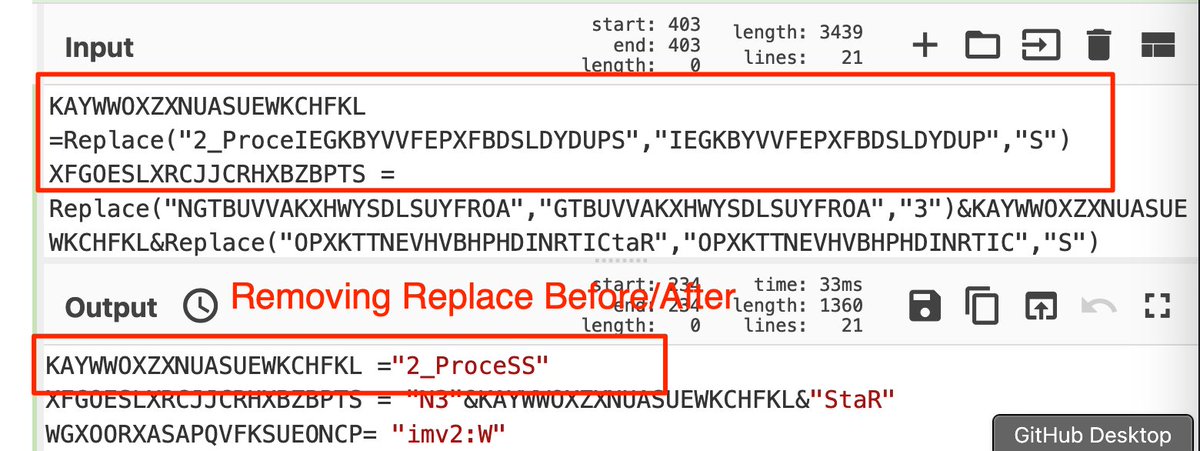
(Possible) AsyncRat loader - Interesting regex to decode the obfuscated C2.
Script was found on host with an active #AsyncRat infection.
#malware #regex #decoding


Script was found on host with an active #AsyncRat infection.
#malware #regex #decoding


[1/6] The team at @HuntressLabs are still observing IronPython executables used to load #malware.
In these cases - IronPython (ipyw.exe) file is typically renamed to SupportTool.exe or Ctfmon.exe
Since ipyw.exe is "legitimate", the VT detection rate is very low (0/72).

In these cases - IronPython (ipyw.exe) file is typically renamed to SupportTool.exe or Ctfmon.exe
Since ipyw.exe is "legitimate", the VT detection rate is very low (0/72).


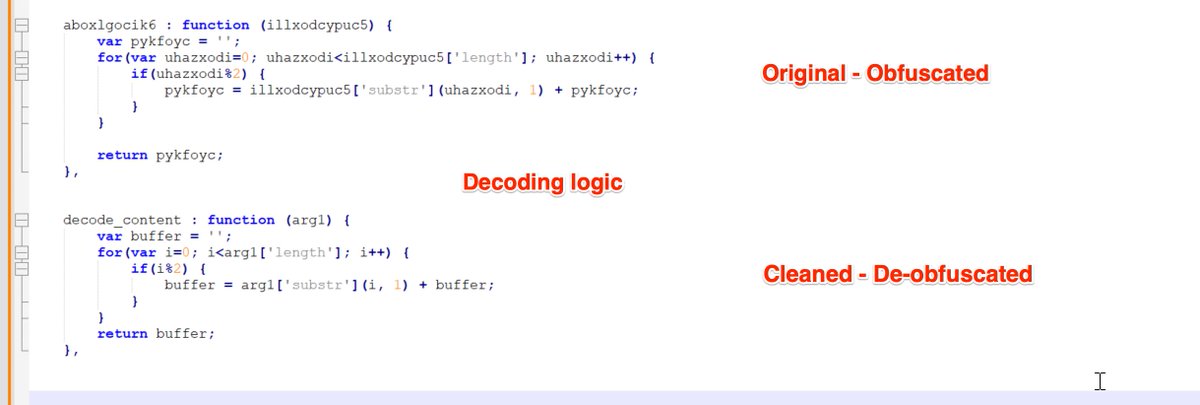
[2/6] The "update.py" is where the malicious action starts.
This is usually a simple python file containing an additional obfuscated script.
Below you can see this decoded via #CyberChef.

This is usually a simple python file containing an additional obfuscated script.
Below you can see this decoded via #CyberChef.


Who's ready to start trying to decode some NBTV? I'll be transmitting some via radio waves soon, but the decoding is tricky... so for anyone interested, I've posted the original audio files to sound cloud so you can practice and get the hang of it. #radio #NBTV
First Step: You'll need to download some open source NBTV decoding software. This site has three versions. I recommend experimenting with all three (the NBTV viewer on the left and "The Big Picture" in the middle - try the older version)
users.tpg.com.au/users/gmillard…
users.tpg.com.au/users/gmillard…
Next step: Go to soundcloud to the NBTV audio files I uploaded and try to decode them (open the NBTV viewing software, set your source to the sound card of your computer, then just play the audio file straight from sound cloud.