Discover and read the best of Twitter Threads about #HTB
Most recents (4)
🧵 (1/3) How well do you know your tools? 🔧
We have gathered a list of resources for you to explore and practice the most powerful #pentesting tools.
We have gathered a list of resources for you to explore and practice the most powerful #pentesting tools.

(2/3) 📚 Your next #HTB Academy lessons:
➡️ Explore the #Linux Fundamentals: bit.ly/3HpAAIu
➡️ Learn Network Enumeration with Nmap: bit.ly/44dY2kM
➡️ Metasploit Framework: bit.ly/3GoN68t
➡️ Web Requests: bit.ly/41KqOb3
➡️ Explore the #Linux Fundamentals: bit.ly/3HpAAIu
➡️ Learn Network Enumeration with Nmap: bit.ly/44dY2kM
➡️ Metasploit Framework: bit.ly/3GoN68t
➡️ Web Requests: bit.ly/41KqOb3
(3/3) Don't forget about these #pentesting tools 🫡
➡️ Cracking Passwords with Hashcat: bit.ly/3n9CYvl
➡️ Active Directory BloodHound: bit.ly/3VcoW8P
➡️ Intro to Network Traffic Analysis: bit.ly/3HmHZHU
➡️ Cracking Passwords with Hashcat: bit.ly/3n9CYvl
➡️ Active Directory BloodHound: bit.ly/3VcoW8P
➡️ Intro to Network Traffic Analysis: bit.ly/3HmHZHU
/1 #Hardening:
@0xdf_ finds credentials in the ConsoleHost_history.txt file in the latest walkthrough of the #HTB machine Timelapse. [1]
In our Compromise Assessments, we regularly audit the PowerShell history to find (stored) credentials in this file. 🧵
#CyberSecurity
@0xdf_ finds credentials in the ConsoleHost_history.txt file in the latest walkthrough of the #HTB machine Timelapse. [1]
In our Compromise Assessments, we regularly audit the PowerShell history to find (stored) credentials in this file. 🧵
#CyberSecurity

2/ Hunting for credentials in the PowerShell history is quickly done with @Velocidex Velociraptor.
We can get the file's entire content from the hosts or search specifically for keywords within the file.
We can get the file's entire content from the hosts or search specifically for keywords within the file.

3/ The content of this file (the PowerShell history), is not only interesting for searching stored credentials in it but also an excellent forensic artifact.
In the case of a CA, we can specifically search for (older) traces of TAs (Invoke-commands, downloading of tools/code..)
In the case of a CA, we can specifically search for (older) traces of TAs (Invoke-commands, downloading of tools/code..)
#Windows Tip:
Change file permissions on Windows using cacls.
Cacls files /e /p {USERNAME}:{PERMISSION}
#HTB #infosec
Change file permissions on Windows using cacls.
Cacls files /e /p {USERNAME}:{PERMISSION}
#HTB #infosec
/p : Set new permission
/e : Edit permission
{USERNAME} : Name of user
{PERMISSION} : Permission can be:
R – Read
W – Write
C – Change (write)
F – Full control
Source: @nixcraft
/e : Edit permission
{USERNAME} : Name of user
{PERMISSION} : Permission can be:
R – Read
W – Write
C – Change (write)
F – Full control
Source: @nixcraft
@threadreaderapp unroll
In a second order SQL injection, an application takes a user input from an HTTP request and stores it for future retrieval. It is two parts injection
#HTB #infosec #websecurity
#HTB #infosec #websecurity
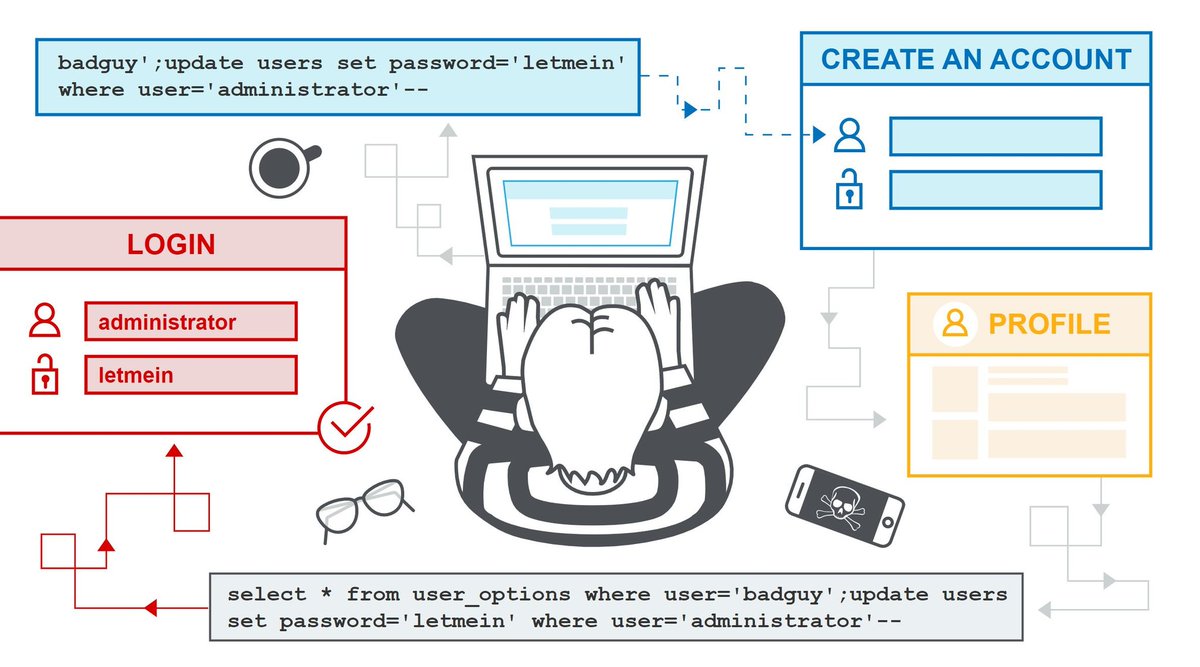
An example of this would be a vulnerable application that has "sign up" page and "login page". The sign up page would be used to send POST requests to store data in the db in a form of SQL query and the login page would be used to send different POST requests to retrieve thedata
@LissanonCedric actually, no both requests are POST requests. That was a typo, I fix it . Thanks for bring it up 👍
