Discover and read the best of Twitter Threads about #M365
Most recents (5)
OK, so there is definitely a problem with the Search-UnifiedAuditLog cmdlet in #Microsoft365. Confirmed this in multiple tenants - here's what I'm seeing: 🧵
#threathunting #threathunt #auditlogs #M365 #Office365 #O365 #M365Security
#threathunting #threathunt #auditlogs #M365 #Office365 #O365 #M365Security
First, go to security.microsoft.com -> Audit and perform a new search for all events in a given timeframe (a few hours, total). Have this available for reference.
Next, open PowerShell and connect to Exchange Online:
Connect-ExchangeOnline
You ran a search in the Defender portal with a date range of a few hours. Within that same timeframe, pick an even smaller date/time range that has < 100 events. You'll need those timestamps next.
Connect-ExchangeOnline
You ran a search in the Defender portal with a date range of a few hours. Within that same timeframe, pick an even smaller date/time range that has < 100 events. You'll need those timestamps next.
Top 3 #M365 Account Takeover (ATO) actions spotted by our SOC in Q1:
1. New-inbox rule creation to hide attacker emails
2. Register new MFA device for persistence
3. Create mailbox forwarding rules to monitor victim comms and intercept sensitive info
More details in 🧵...
1. New-inbox rule creation to hide attacker emails
2. Register new MFA device for persistence
3. Create mailbox forwarding rules to monitor victim comms and intercept sensitive info
More details in 🧵...
50% of ATO activity in M365 we identified was for New-inbox rules created by an attacker to automatically delete certain emails from a compromised account. By deleting specific emails, an attacker can reduce the chance of the victim or email admins spotting unusual activity.
25% percent of ATO activity we identified was for the registration of a new MFA device in Azure. Registering a new MFA device allows an attacker to maintain persistence.
We're seeing more and more M365 session cookie theft for initial access....
We're seeing more and more M365 session cookie theft for initial access....
BEC threat actors favorite #M365 Inbox-rule names:
'.'
'..'
'.;'
'l'
'r'
By deleting specific emails, an attacker can reduce the chance of the victim spotting unusual activity.
You can build high quality detections to spot this activity. A 🧵with real-world examples...
'.'
'..'
'.;'
'l'
'r'
By deleting specific emails, an attacker can reduce the chance of the victim spotting unusual activity.
You can build high quality detections to spot this activity. A 🧵with real-world examples...
Account takeover (ATO) activity in M365 can involve various unauthorized actions performed by an attacker who has gained control over the account.
Of the ATO activity we identified in M365 in Q1 '23:
50% of all ATO in M365 we identified was for New-inbox rules created by the attacker to automatically delete or hide certain emails from the compromised account.
50% of all ATO in M365 we identified was for New-inbox rules created by the attacker to automatically delete or hide certain emails from the compromised account.
I'm a huge fan of Azure Automation. If you're an #AzureAD / #M365 Admin and haven't used it before, then this thread is for you
You will need an Azure subscription, but the first 500 minutes/month are free!
Here's an example of how to automate Azure AD device cleanup :)
You will need an Azure subscription, but the first 500 minutes/month are free!
Here's an example of how to automate Azure AD device cleanup :)
First, we're going to log into the Azure portal: portal.azure.com
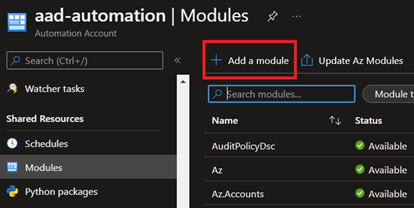
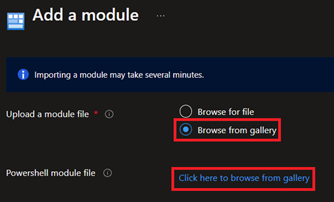
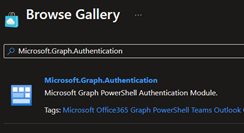
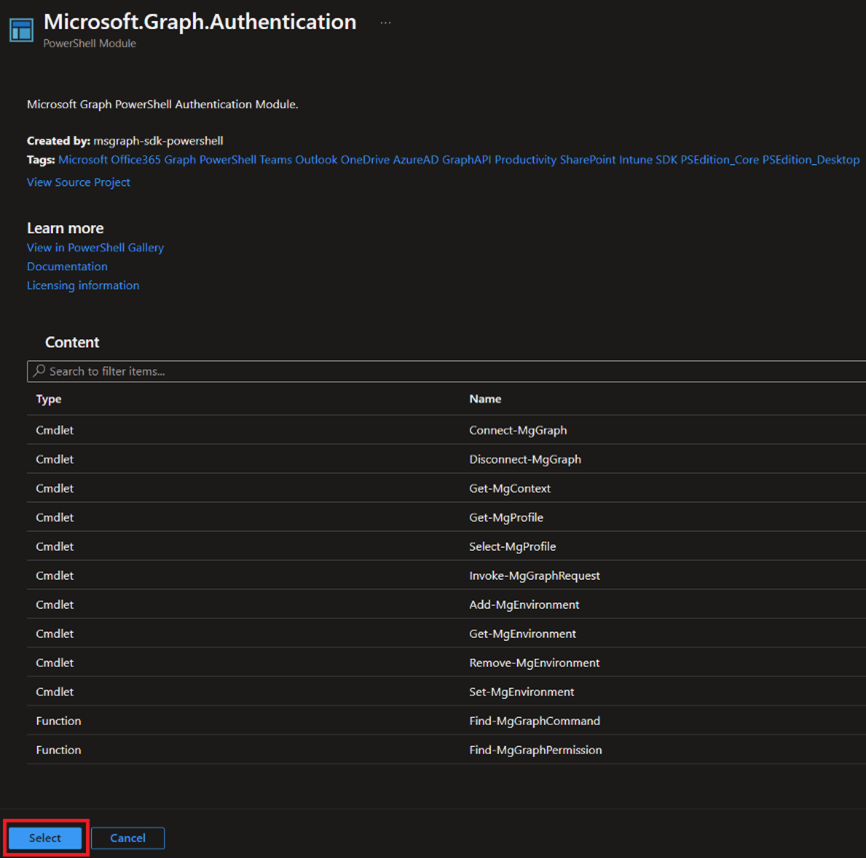
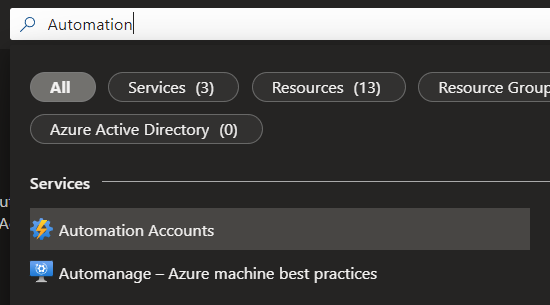
Search for Automation and click on Automation Accounts
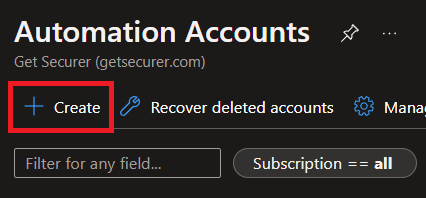
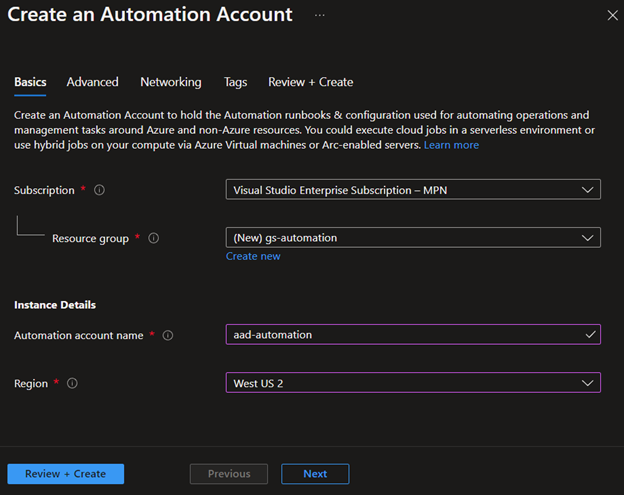
Then we'll click Create, pick the sub and resource group (or create one), give it a descriptive name, select a location, and hit Review + Create


Search for Automation and click on Automation Accounts
Then we'll click Create, pick the sub and resource group (or create one), give it a descriptive name, select a location, and hit Review + Create
Office 365 Automated Investigation and Response (AIR) coming soon to ATP P2 or Office 365 E5 tenants. In this video I am showing one of the playbooks triggered by an Alert from Security and Compliance Center.
An Alert was triggered because malware was detected and removed from user mailbox after email message delivery. AIR analyzed: who else received similar emails, if user that received the malware violated DLP rules, had mailbox forwarding configured
or had any anomalies in sign-in activities. Investigation was also continued by Microsoft Defender ATP on user's workstation. Instead of collecting this information manually from different tools I had all that done automatically and report was presented to me.