Discover and read the best of Twitter Threads about #MSTIC
Most recents (5)
We've been tracking DEV-0537 since 2021 (overlaps: Lapsus$, UNC3661). Here's a comprehensive 🆕 BLOG 📰 covering observed TTPs: microsoft.com/security/blog/…
#MSTIC and Defender threat intel collab
➕#DART 👻 incident response team experience from the trenches [1/3]
#MSTIC and Defender threat intel collab
➕#DART 👻 incident response team experience from the trenches [1/3]
The blog highlights varied initial access vectors and a slew of [inconsistent?] end goals: data theft, extortion, chaos...
One way to interpret "this actor's TTPs and infrastructure are constantly changing" is that they are loosely-organized (see: ) [2/3]

One way to interpret "this actor's TTPs and infrastructure are constantly changing" is that they are loosely-organized (see: ) [2/3]


DEV-0537 / Lapsus$ shows that 𝘢𝘵𝘵𝘢𝘤𝘬𝘦𝘳𝘴 can be creative opportunists and still be successful.
Luckily, the same goes for 𝘥𝘦𝘧𝘦𝘯𝘥𝘦𝘳𝘴.
Use this opportunity to strengthen your security controls to protect far beyond this threat actor [3/3] microsoft.com/security/blog/…

Luckily, the same goes for 𝘥𝘦𝘧𝘦𝘯𝘥𝘦𝘳𝘴.
Use this opportunity to strengthen your security controls to protect far beyond this threat actor [3/3] microsoft.com/security/blog/…


There’s a lot to unpack in @MsftSecIntel’s latest blog on the CVE-2021-40444 vulnerability. Here’s a thread of some of the details that I think are notable
The volume of initial exploitation was limited. Most security orgs I talked to didn’t observe it directly in their telemetry
“In August…MSTIC identified a small number of attacks (less than 10) that attempted to exploit a remote code execution vulnerability in MSHTML”
“In August…MSTIC identified a small number of attacks (less than 10) that attempted to exploit a remote code execution vulnerability in MSHTML”
So you want to talk about the massive software supply chain intrusion & the most carefully-planned, complex espionage I’ve ever helped uncover?
Start here: fireeye.com/blog/threat-re… 🤩
But then what?? Let’s talk about some post-compromise techniques...
Start here: fireeye.com/blog/threat-re… 🤩
But then what?? Let’s talk about some post-compromise techniques...
Please read the above blog to appreciate multiple backdoors used, careful & unique tradecraft used on-premise...
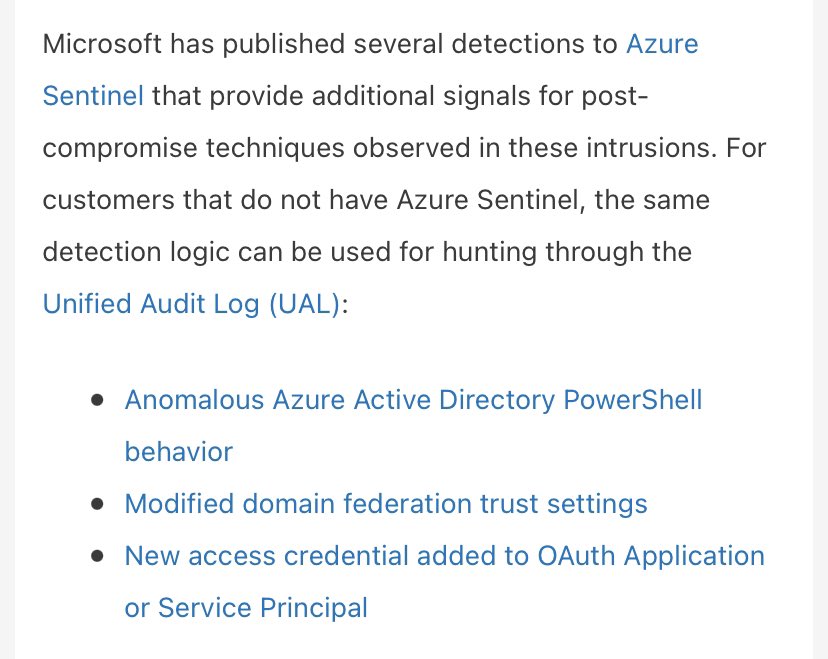
We just published more details on what we’ve been finding post-compromise: blogs.microsoft.com/on-the-issues/…
ADFS key material compromise, SAML shenanigans, OAuth keys added...
We just published more details on what we’ve been finding post-compromise: blogs.microsoft.com/on-the-issues/…
ADFS key material compromise, SAML shenanigans, OAuth keys added...

Within the technical companion blog (msrc-blog.microsoft.com/2020/12/13/cus…) we provide some late stage killchain activity observed many places.
I want to highlight the additional detections pushed to cover these techniques in @MSAzureSentinel (but anyone can use on the UAL for #DFIR) ...
I want to highlight the additional detections pushed to cover these techniques in @MSAzureSentinel (but anyone can use on the UAL for #DFIR) ...
Added #STRONTIUM election-related credential harvesting campaign "detection" to #AzureSentinel: github.com/Azure/Azure-Se…
Yes - it's hardcoded for netblocks released in the #MSTIC report (microsoft.com/security/blog/…)
This is just extra coverage on top of existing cred harvesting logic
Yes - it's hardcoded for netblocks released in the #MSTIC report (microsoft.com/security/blog/…)
This is just extra coverage on top of existing cred harvesting logic
That said, the logic posted there finds some high fidelity #STRONTIUM campaigns from at least June through... recently (more details in above blog).
You'll see a User-Agent, first/last attempt, # of total attempts, # of unique IPs & unique accounts attempted + a list of accounts
You'll see a User-Agent, first/last attempt, # of total attempts, # of unique IPs & unique accounts attempted + a list of accounts
As shipped, it's looking over the past 30 days. But if you have #AzureSentinel, I recommend pasting that same KQL in & searchings logs w/ expanded timeframe.
The # authAttempts can stay where it's at ... #STRONTIUM activity is approx 100 attempts per IP per account
The # authAttempts can stay where it's at ... #STRONTIUM activity is approx 100 attempts per IP per account
🆕 Job Update: I'm joining @Microsoft!
On the #MSTIC R&D team:
☁️🏹hunting & investigations in the cloud (#AzureSentinel, @Office365)
🎯✍️🏽writing detections for several platforms
👥🎁community-based research & sharing
🛡️🤲🏽protecting those who need it the most #DefendingDemocracy
On the #MSTIC R&D team:
☁️🏹hunting & investigations in the cloud (#AzureSentinel, @Office365)
🎯✍️🏽writing detections for several platforms
👥🎁community-based research & sharing
🛡️🤲🏽protecting those who need it the most #DefendingDemocracy
Honored to work for @JohnLaTwC & @LeahLease
I'm pumped to grow with & learn from so many amazing security engineers and analysts in #MSTIC: twitter.com/i/lists/112798… #FF
My new East Coast crew includes the #APT hunters in Reston, @Cyb3rWard0g, and some random @cglyer guy 😅
Also:
I'm pumped to grow with & learn from so many amazing security engineers and analysts in #MSTIC: twitter.com/i/lists/112798… #FF
My new East Coast crew includes the #APT hunters in Reston, @Cyb3rWard0g, and some random @cglyer guy 😅
Also:
I'm going to lean on (& try¹ to contribute to) teams across the MS security family:
• @MicrosoftMTP crew w/ @jepayneMSFT @endisphotic @GossiTheDog et al🤩
• @msftsecresponse w/ the awesome @n0x08
• @Lee_Holmes for everything Azure
¹if I say it here, it has to happen right?😉
• @MicrosoftMTP crew w/ @jepayneMSFT @endisphotic @GossiTheDog et al🤩
• @msftsecresponse w/ the awesome @n0x08
• @Lee_Holmes for everything Azure
¹if I say it here, it has to happen right?😉

