Discover and read the best of Twitter Threads about #enigma2021
Most recents (24)
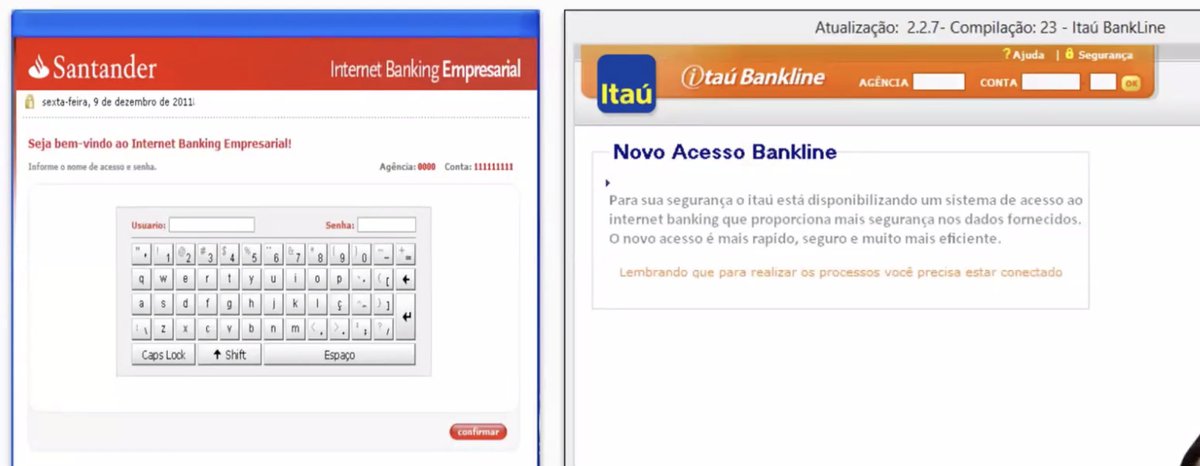
Last talk of #enigma2021 by Marcus Botacin: "DOES YOUR THREAT MODEL CONSIDER COUNTRY AND CULTURE? A CASE STUDY OF BRAZILIAN INTERNET BANKING SECURITY TO SHOW THAT IT SHOULD!"
usenix.org/conference/eni…
usenix.org/conference/eni…
The outcomes I get from my analysis of malware I find in Brazil were quite different than what I saw in analysis of malware from other researchers. Why? Because the malware attacks were different!
@gianluca_string is up at #enigma2021 speaking about "COMPUTATIONAL METHODS TO UNDERSTAND AND MITIGATE ONLINE AGGRESSION"
[Make sure to catch the talks when they're posted -- my hands can't keep up with these speakers and the talks are 🔥]
usenix.org/conference/eni…
[Make sure to catch the talks when they're posted -- my hands can't keep up with these speakers and the talks are 🔥]
usenix.org/conference/eni…
Content note: this talk is about online abuse as some of the content may be upsetting
Got pulled into this after a screenshot of a class assignment sending folks to post on 4chan to post about race/gender/etc issues got posted on 4chan without the email address... so the 4chan folks thought it was @gianluca_string. It wasn't, but they doxxed and harassed anyway
Kicking off the last session of #enigma2021, @katestarbird is speaking about an extremely pressing topic: "ONLINE RUMORS, MISINFORMATION AND DISINFORMATION: THE PERFECT STORM OF COVID-19 AND ELECTION2020"
usenix.org/conference/eni…
usenix.org/conference/eni…
"THE LIMITS OF SANDBOXING AND NEXT STEPS" from Chris Palmer at #enigma2021
usenix.org/conference/eni…
usenix.org/conference/eni…
This talk is going to go through the experience pushing the boundaries on sandboxing in the Chrome browser
What is sandboxing?
* breaking something into lower/higher privileged process
* necessary for browers, OSes, VMs etc.
What is sandboxing?
* breaking something into lower/higher privileged process
* necessary for browers, OSes, VMs etc.

Chromium uses to reduce the amount of privilege of the application: also to reduce the amount of privilege for code that touches websites (renderer)
* split different websites into different processes
* good defense against logic bugs (e.g. same-origin policy)
* split different websites into different processes
* good defense against logic bugs (e.g. same-origin policy)
Next up at #enigma2021, Alex Gaynor from @LazyFishBarrel (satirical security company) will be talking about "QUANTIFYING MEMORY UNSAFETY AND REACTIONS TO IT"
usenix.org/conference/eni…
usenix.org/conference/eni…
It's time to talk about @zoom_us security over @zoom_us at #enigma2021 by Merry Ember Mou with the talk "BUILDING E2EE AND USER IDENTITY"
usenix.org/conference/eni…
usenix.org/conference/eni…
@carmelatroncoso is speaking about "CONTACT TRACING APPS: ENGINEERING PRIVACY IN QUICKSAND" at #enigma2021
usenix.org/conference/eni…
usenix.org/conference/eni…
Engineering contact-tracing apps has been a marathon
Why make them?
* manual contact-tracing became totally overwhelmed with covid cases
* can we supplement with technology?
Why make them?
* manual contact-tracing became totally overwhelmed with covid cases
* can we supplement with technology?

Constraints: security and privacy
* protect from misuse: surveillance, target marginalized individuals, etc.
* purpose limitation by default
* hide user's identity, location, behaviour
* preserve system integrity
* protect from misuse: surveillance, target marginalized individuals, etc.
* purpose limitation by default
* hide user's identity, location, behaviour
* preserve system integrity
In more pandemic talks at #enigma2021, Mark Funk is here to talk about "DESIGNING VERIFIABLE HEALTH SOLUTIONS FOR GLOBAL PANDEMIC"
usenix.org/conference/eni…
usenix.org/conference/eni…
Last day of #enigma2021 and we're kicking off with @cooperq from @EFF talking about "DETECTING FAKE 4G LTE BASE STATIONS IN REAL TIME"
usenix.org/conference/eni…
usenix.org/conference/eni…
Last talk at #enigma2021 today is @iMeluny speaking about "DA DA: WHAT SHARK CONSERVATION TEACHES US ABOUT EMOTIONALITY AND EFFECTIVE COMMUNICATION STRATEGIES FOR SECURITY AND PRIVACY"
usenix.org/conference/eni…
usenix.org/conference/eni…
I dreamt of being a shark scientist and worked my ass off to get a scholarship to one of the top programs. My career took a loop, but to this day I find lessons from sharks for security and privacy.
Kicking off the final session of today at #enigma2021: Sofia Celi with ""I THOUGHT I WAS BEING STRONG WITH A COMPLICATED PERSON": THE TALES OF INTIMATE GENDER-BASED ONLINE ABUSE IN THE GLOBAL SOUTH"
[Content disclaimer: difficult content.]
usenix.org/conference/eni…
[Content disclaimer: difficult content.]
usenix.org/conference/eni…
Finishing up this session at #enigma2021 is from Trey Herr speaking about "BREAKING TRUST – SHADES OF CRISIS ACROSS AN INSECURE SOFTWARE SUPPLY CHAIN"
[ *cough* #SolarWinds #SolarWindsHack *cough* ]
usenix.org/conference/eni…
[ *cough* #SolarWinds #SolarWindsHack *cough* ]
usenix.org/conference/eni…
The software supply chain is huge and reaches everywhere.
In the US and elsewhere there's a lot of COTS (commercial off the shelf) software being used.
We don't build most of the software that we use, from mobile phones to container architechture.
In the US and elsewhere there's a lot of COTS (commercial off the shelf) software being used.
We don't build most of the software that we use, from mobile phones to container architechture.
Our mental models around supply chain (and regulatory architecture) are built around the hardware supply chain
Kicking off the next session at #enigma2021 is @maddiestone with "THE STATE OF 0-DAY IN-THE-WILD EXPLOITATION"
usenix.org/conference/eni…
usenix.org/conference/eni…
What do you think of when I say 0-day? Only the most elite hackers and most elite targets, that they're super hard and expensive to develop.
I started looking back over what we're really seeing in the wild, looking at all of these bugs together to look at the bugs and gaps.
I started looking back over what we're really seeing in the wild, looking at all of these bugs together to look at the bugs and gaps.
It became clear that we are not requiring the most elite skills to exploit 0-days. But there are mitigations that can make it much harder.
Kicking off #enigma2021 second day with our Contact Notification panel, moderated by @benadida with panelists Mike Judd, CDC COVID-19 Exposure Notification Initiative; Ali Lange, Google; Tiffany C. Li, Boston University School of Law; Marcel Salathé, EPFL
usenix.org/conference/eni…
usenix.org/conference/eni…
Ben: The reason why we cannot be here in the same physical space is the same reason we have this panel on Contact Tracing. What is that?
* Run around looking for people who have been infected
* And looking for people who have been exposed to the people who have been infected
* Run around looking for people who have been infected
* And looking for people who have been exposed to the people who have been infected
* To try to contain the spread
Last talk at #enigma2021 for today by Pardis Emami-Naeini on "PRIVACY AND SECURITY NUTRITION LABELS TO INFORM IOT CONSUMERS"
usenix.org/conference/eni…
usenix.org/conference/eni…
Kicking off our Humans Making Decisions session with @patrickgage speaking about how "PRIVACY, MEASURABLY, ISN'T DEAD"
usenix.org/conference/eni…
usenix.org/conference/eni…
[ Personal note: this study was literally the MOST EXPENSIVE THING in my opex budget. For years. I'm so excited you all can see it now. ]
... on with the talk
... on with the talk
I hear all the time that privacy is dead. But you know it's not. Every time you tell someone a secret, write something in a journal, have a thought inside of your own mind you're having a moment of privacy as trust or secrecy or freedom.
Last up in Privacy Tech for #enigma2021, @xchatty speaking about "IMPLEMENTING DIFFERENTIAL PRIVACY FOR THE 2020 CENSUS"
usenix.org/conference/eni…
usenix.org/conference/eni…
Next up in Privacy Technology at #enigma2021, Kelly Huang from @ethyca speaking about "GONE, BUT NOT "FORGOTTEN"—TECHNICAL & PRACTICAL CHALLENGES IN OPERATIONALIZING MODERN PRIVACY RIGHTS"
usenix.org/conference/eni…
usenix.org/conference/eni…
Just imagine there's a global pandemic forcing everyone to stay home and buy their stuff over the internet. And you've been working on your sanitization-on-demand startup. You've got more users than you can count! ... literally, because your data's all over.
Now you're a multi-national international country with privacy issues because your information is all over the place.
Now a user writes to request you delete their data. Where is it? How do you do that? Who's responsible for privacy in your business.
Now a user writes to request you delete their data. Where is it? How do you do that? Who's responsible for privacy in your business.
We're kicking off the Privacy Tech session at #enigma2021 with Mitch Negus speaking about "NO DATA, NO PROBLEM—GIVING NUCLEAR INSPECTORS BETTER TOOLS WITHOUT REVEALING STATE SECRETS"
usenix.org/conference/eni…
usenix.org/conference/eni…
A nuclear catastrophe hasn't occurred... yet. So we need to stay vigilant. Nuclear inspectors go in according to treaties to check what's going on and check compliance with treaty rules.
But as sophisticated analytics become more common, states will only want to share the minimum amount of information necessary under the treaty.
But perhaps we can use MPC -- secure multi-party computation
But perhaps we can use MPC -- secure multi-party computation
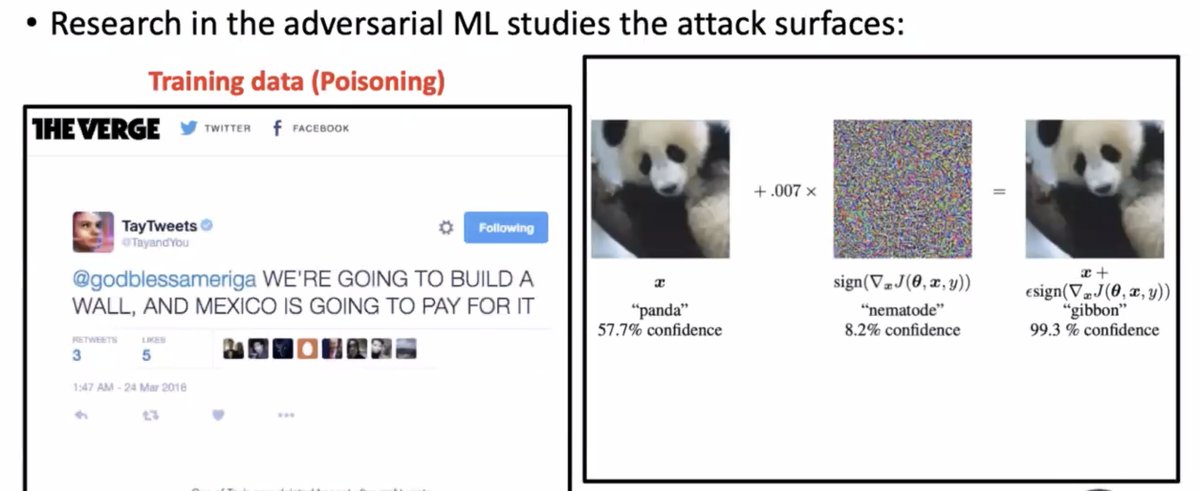
Next up at #enigma2021, Sanghyun Hong will be speaking about "A SOUND MIND IN A VULNERABLE BODY: PRACTICAL HARDWARE ATTACKS ON DEEP LEARNING"
(Hint: speaker is on the market)
usenix.org/conference/eni…
(Hint: speaker is on the market)
usenix.org/conference/eni…
In recent years ML models have worked from research labs to production, which makes ML security important. Adversarial ML research studies how to mess with ML
Last talk about Securing Democracy at #enigma2021: @jackhcable speaking about "THE FULL STACK PROBLEM OF ELECTION SECURITY"
usenix.org/conference/eni…
usenix.org/conference/eni…
Let's imagine that elections use all the security measures security people have been advocating: risk-limiting audits, paper ballots, etc. Would people trust the elections more?
Jack would argue no. Most people don't understand this stuff and most of the claims people are making can't be disproven. And are massively bogus already.
Georgia did a full recount on paper ballots and it very much didn't stop people from doubting the election!
Georgia did a full recount on paper ballots and it very much didn't stop people from doubting the election!
In more Securing Democracy at #enigma2021, @ChrFolini talking about "THE ADVENTUROUS TALE OF ONLINE VOTING IN SWITZERLAND"
usenix.org/conference/eni…
usenix.org/conference/eni…
Switzerland is a direct democracy where citizens get to vote at least 4x/year, with a lot of mail-in voting. We have a long history of online voting.
Disclaimer: THIS IS NOT SWEDEN.
[I get the picture that @ChrFolini has had to explain the difference several times.]
Disclaimer: THIS IS NOT SWEDEN.
[I get the picture that @ChrFolini has had to explain the difference several times.]

Next up at #enigma2021, Sunny Consolvo will be speaking about "SECURITY & U.S. POLITICAL CAMPAIGNS: A STUDY & EXPERT ROUNDTABLE"
usenix.org/conference/eni…
usenix.org/conference/eni…
What if your personal account getting hacked could lead to years of harassment, allow election interference, and subvert democracy?
What if to avoid this you have to fundamentally change your online habits? And you work in politics, not tech.
What if to avoid this you have to fundamentally change your online habits? And you work in politics, not tech.
Not all hacks will lead to outsized outcomes like that, but some will! And it's especially hard in a fast-paced temporary environment of a political campaign.
First talk at #enigma2021 is coming up in just a moment: @scottjshapiro speaking about "IS CYBER WAR LEGAL: A FOUR HUNDRED YEAR RETROSPECTIVE".
Don't worry, it's a 20-minute talk, not 400 years. 😅
usenix.org/conference/eni…
Don't worry, it's a 20-minute talk, not 400 years. 😅
usenix.org/conference/eni…
Imagine you log into Twitter one morning and see that the Pentagon's network was taken down, chlorine gas is being released, NYC stock exchange is taken down, and then the electric grid is taken down... by Iran by cyber-attacks in retaliation for sanctions.
Would this be legal?
Would this be legal?
It would be illegal for Iran to bomb is. Chemical warfare is illegal.
Did the outlawing of kinetic war outlaw cyber-law or not, thought?
Did the outlawing of kinetic war outlaw cyber-law or not, thought?