Discover and read the best of Twitter Threads about #fireeyesummit
Most recents (10)
Hey #ATTACKcon here's a recap of
#GuardrailsOfTheGalaxy: The Prologue
including the *first* three awards – #Guardies 🏆
+ the slides
I'm your thread host, @ItsReallyNick from the #AdvancedPractices 🦅 Adversary Methods team where we "reverse engineer" attacker techniques...

#GuardrailsOfTheGalaxy: The Prologue
including the *first* three awards – #Guardies 🏆
+ the slides
I'm your thread host, @ItsReallyNick from the #AdvancedPractices 🦅 Adversary Methods team where we "reverse engineer" attacker techniques...


Why a lightning talk on Execution Guardrails (#T1480)?
• We worked with @stromcoffee & @MITREattack team who added the new technique in April 2019:
• Smart people suggest that guardrails are correlated with adversary sophistication
• 💂🛤️ are fun! ...


• We worked with @stromcoffee & @MITREattack team who added the new technique in April 2019:
• Smart people suggest that guardrails are correlated with adversary sophistication
• 💂🛤️ are fun! ...



🎟️🍿Movie Night: "Between Two Steves"
🆕#StateOfTheHack
@cglyer & I chat with the top two Steves from #AdvancedPractices 🦅: @stonepwn3000 & @stvemillertime to talk about the front-line technical stories and research presented at the 2019 #FireEyeSummit.
pscp.tv/w/1YpJkYjBleMKj
🆕#StateOfTheHack
@cglyer & I chat with the top two Steves from #AdvancedPractices 🦅: @stonepwn3000 & @stvemillertime to talk about the front-line technical stories and research presented at the 2019 #FireEyeSummit.
pscp.tv/w/1YpJkYjBleMKj
@cglyer @stonepwn3000 @stvemillertime 🗣️
• tracking the groups and techniques that matter
• recent #FIN7 events: fireeye.com/blog/threat-re…
• recent #AdvancedPractices team research, including PDB dossier & summit talks on proactive identification of C2, deep code signing research, and rich header hunting at scale...
• tracking the groups and techniques that matter
• recent #FIN7 events: fireeye.com/blog/threat-re…
• recent #AdvancedPractices team research, including PDB dossier & summit talks on proactive identification of C2, deep code signing research, and rich header hunting at scale...
We highlight a favorite talk
🍎 𝗟𝗶𝘃𝗶𝗻𝗴 𝗼𝗳𝗳 𝘁𝗵𝗲 𝗢𝗿𝗰𝗵𝗮𝗿𝗱 🍎
by @williballenthin, @nicastronaut, @HighViscosity
revealing TTPs & artifacts left behind from the million mac engagement
fireeye.com/blog/threat-re…
We kinda want to do a full #StateOfTheHack on that one...
🍎 𝗟𝗶𝘃𝗶𝗻𝗴 𝗼𝗳𝗳 𝘁𝗵𝗲 𝗢𝗿𝗰𝗵𝗮𝗿𝗱 🍎
by @williballenthin, @nicastronaut, @HighViscosity
revealing TTPs & artifacts left behind from the million mac engagement
fireeye.com/blog/threat-re…
We kinda want to do a full #StateOfTheHack on that one...
🤙💰 Mahalo FIN7: fireeye.com/blog/threat-re…
• On several on-going investigations we saw #FIN7 trying to retool 🏄🏼
• Used DLL search order hijacking of a legit POS management utility with a signed backdoor (0 detections on VirusTotal)
• Hunting for #BOOSTWRITE and #RDFSNIFFER 💳
• On several on-going investigations we saw #FIN7 trying to retool 🏄🏼
• Used DLL search order hijacking of a legit POS management utility with a signed backdoor (0 detections on VirusTotal)
• Hunting for #BOOSTWRITE and #RDFSNIFFER 💳
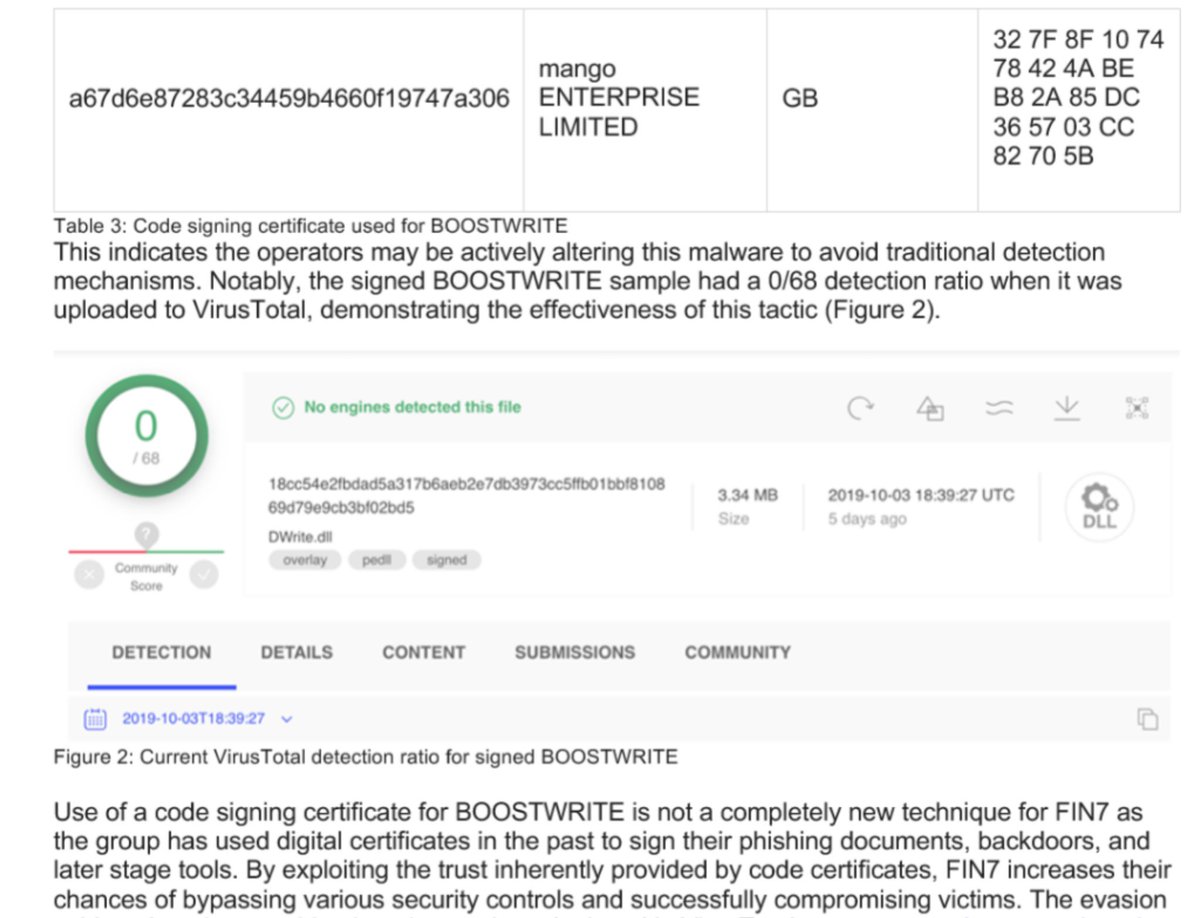
.@josh__yoder & I stayed up much of the night to get this blog out.
The signed #BOOSTWRITE sample is still undetected by static VT scanners: virustotal.com/gui/file/18cc5…
We were fair on why that is and how that doesn't fully represent detection posture.
Then we provided hunting rules.
The signed #BOOSTWRITE sample is still undetected by static VT scanners: virustotal.com/gui/file/18cc5…
We were fair on why that is and how that doesn't fully represent detection posture.
Then we provided hunting rules.

#FIN7's code signing certificate is purportedly from Mango Enterprise Limited in the UK.
Prob not theirs - based on the street address, I suspect there's more car theft than certificate theft 😜: maps.app.goo.gl/MbznDeJPHJr4n5…
We analyze & discuss how to find the certificate anomalies!



Prob not theirs - based on the street address, I suspect there's more car theft than certificate theft 😜: maps.app.goo.gl/MbznDeJPHJr4n5…
We analyze & discuss how to find the certificate anomalies!




@HoldSecurity Harvests information periodically from various botnet information panels (that give them view into the size and systems in the botnet).
Fun fact - Gozi botnet has so many systems connected all queries on the information panel time out
#FireEyeSummit
Fun fact - Gozi botnet has so many systems connected all queries on the information panel time out
#FireEyeSummit
So FEYE just opened up some internal security APIs (detection as a service, virtual NX) and launched a developer relations program. 😯
That's a very... different @FireEye & a surprise even to employees.
🌐Developer hub: fireeye.dev
🔗AWS Apps: aws.amazon.com/marketplace/se…
That's a very... different @FireEye & a surprise even to employees.
🌐Developer hub: fireeye.dev
🔗AWS Apps: aws.amazon.com/marketplace/se…

@FireEye @FireEyeDev @GradyS @jtviolet I wasn't involved with this effort, but I just met our new dev relations guy @jtviolet at #FireEyeSummit and this was dropped on the main stage by @GradyS
It looks like more APIs are coming? @FireEyeDev👀
Time to go see what we're exposing and hope we're storing *some* telemetry
It looks like more APIs are coming? @FireEyeDev👀
Time to go see what we're exposing and hope we're storing *some* telemetry
@FireEye @FireEyeDev @GradyS @jtviolet Hopefully we can get more of our @Mandiant & #FLARE microservices*⃣ available via public API for the right price.
~thinking to myself~ "maybe if I post publicly it will happen"
😉🙏🏽
*⃣config extractors, traffic decoders, forensic artifact analyzers, toolmark highlighters
~thinking to myself~ "maybe if I post publicly it will happen"
😉🙏🏽
*⃣config extractors, traffic decoders, forensic artifact analyzers, toolmark highlighters
1/ File under #BadSpeaker - Former U.S. Secretary of State Hillary Rodham Clinton is a "featured" keynote at our #FireEyeSummit. Intimate Q&A includes: the old lady wrist prop technique to support your hammer hand; & how to avoid "eye" splatter from bleach-bit by using a cloth. 



2/ With special followup diatribe by #CrookedHillary on "how to ignore security warnings for the State Department and #FBI when your computer is infected and forwarding all your E-mails to China". Finally get Hillary's inside scoop on "What Difference Does it [AKAsecurity] Make" 

3/ Be amazed that a legitimate security conference actually invited the most inept, corrupt, and "security lazy" SOS in US history.
"You've Got Mail"
@danielcabaniel @CyberAmyntas discussing email phishing and mail server attack trends
#FireEyeSummit
@danielcabaniel @CyberAmyntas discussing email phishing and mail server attack trends
#FireEyeSummit
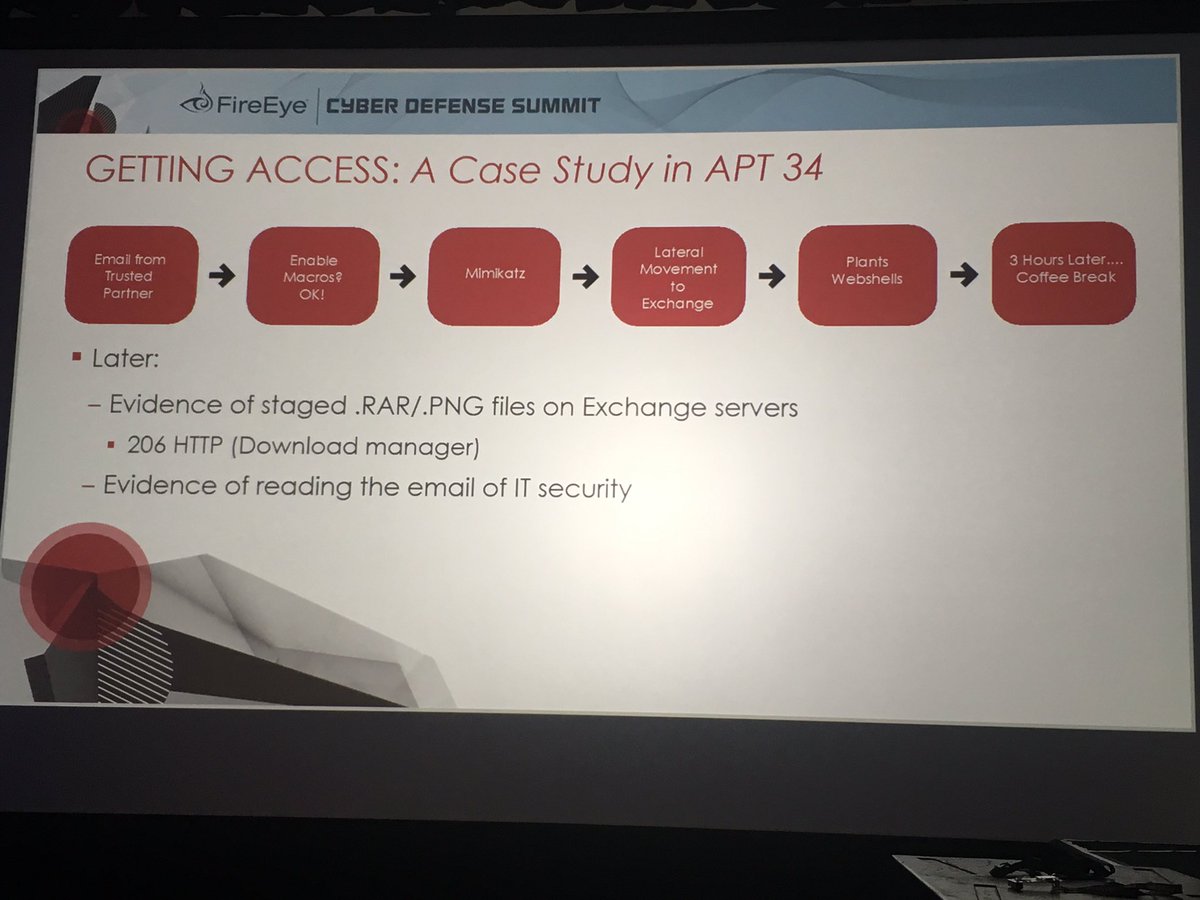
APT34 compromised a trusted partner org - and used that to abuse trust (convinced user to enable macros) and successfully phish victim
Subsequently staged data theft files on the Exchange server as .png files and downloaded from the server.
#FireEyeSummit
Subsequently staged data theft files on the Exchange server as .png files and downloaded from the server.
#FireEyeSummit
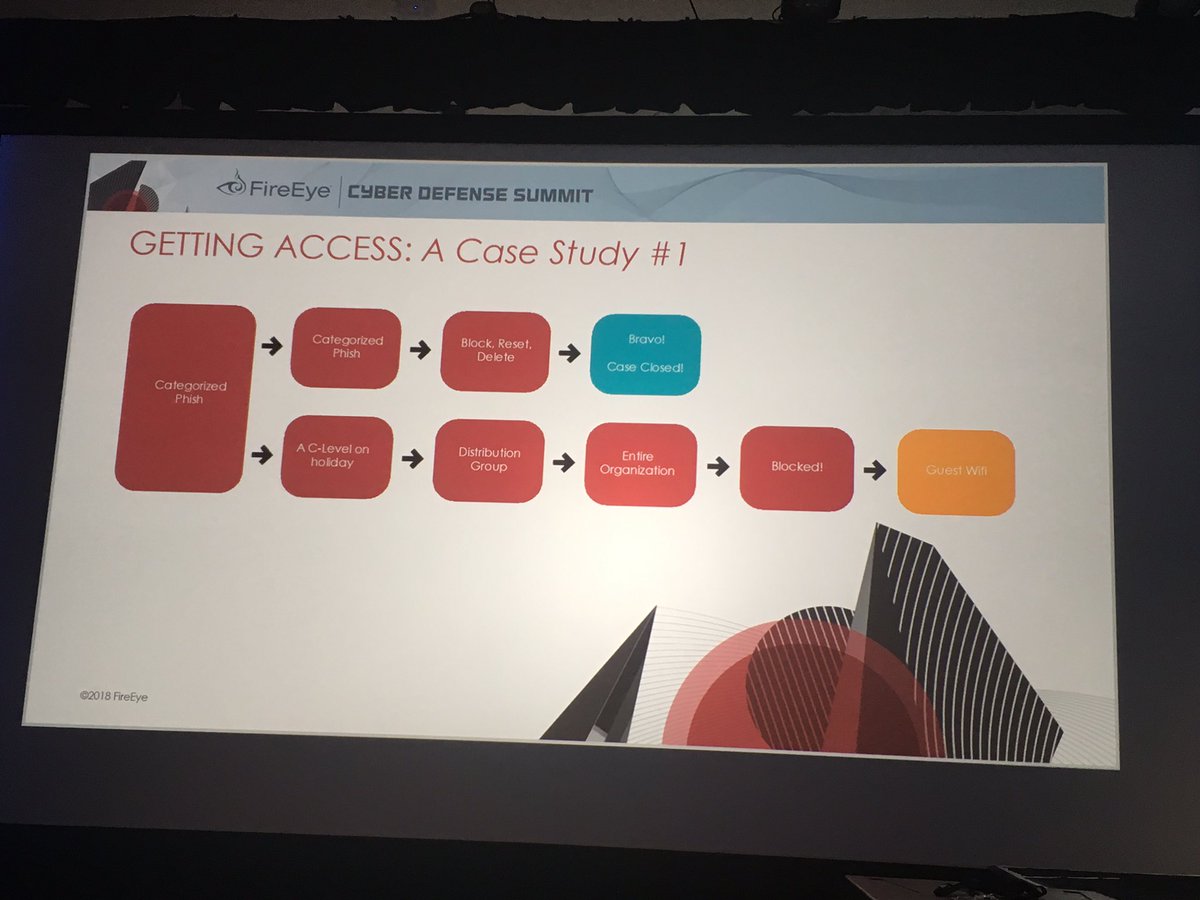
C-level credential phished while on vacation - APT34 used account access to phish entire company. Even though infosec team blocked URL on web proxy - employees switched to guest wi-fi to access the URL.
#FireEyeSummit
#FireEyeSummit
.@TekDefense introducing our next talk about unmasking APT38 - a North Korean threat actor focused on financial attacks
Blog released today with more details
fireeye.com/blog/threat-re…
#FireEyeSummit
Blog released today with more details
fireeye.com/blog/threat-re…
#FireEyeSummit

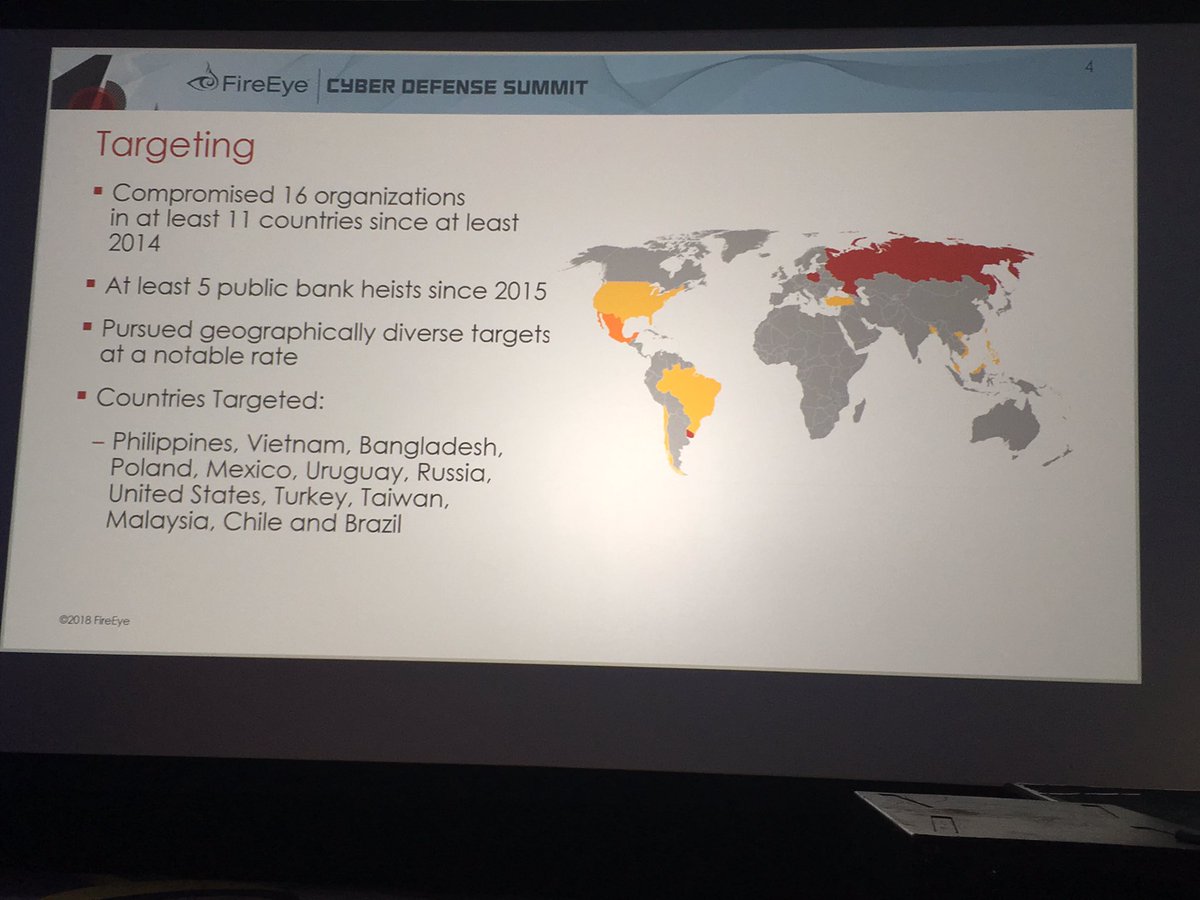
APT38 targeted banks (SWIFT messaging initiated wire transfers you've read about in the news) and crypto currency exchanges (among other orgs)
#FireEyeSummit
#FireEyeSummit
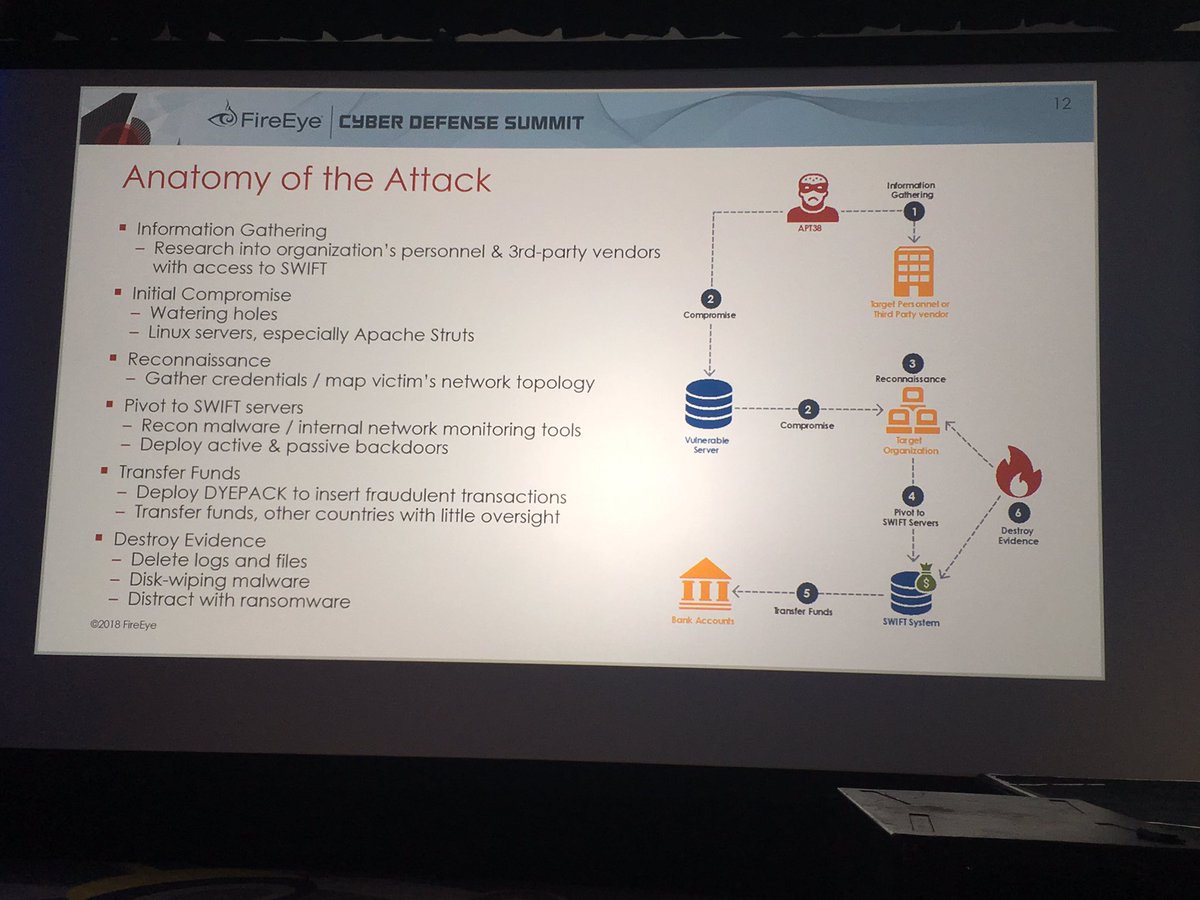
Yes - you read that right. APT38 has used multiple different (and escalating tactics over time) to destroy evidence including deploying ransomware and running disk wiping malware
#FireEyeSummit
#FireEyeSummit
First up Matias and Adrian discussing investigating the threat actor that MSFT calls Platinum
...and right out of the gate the threat actor steals your EDR agent installer 😮 #SignsThisProbablyIsntAScriptKiddie
#FireEyeSummit
...and right out of the gate the threat actor steals your EDR agent installer 😮 #SignsThisProbablyIsntAScriptKiddie
#FireEyeSummit

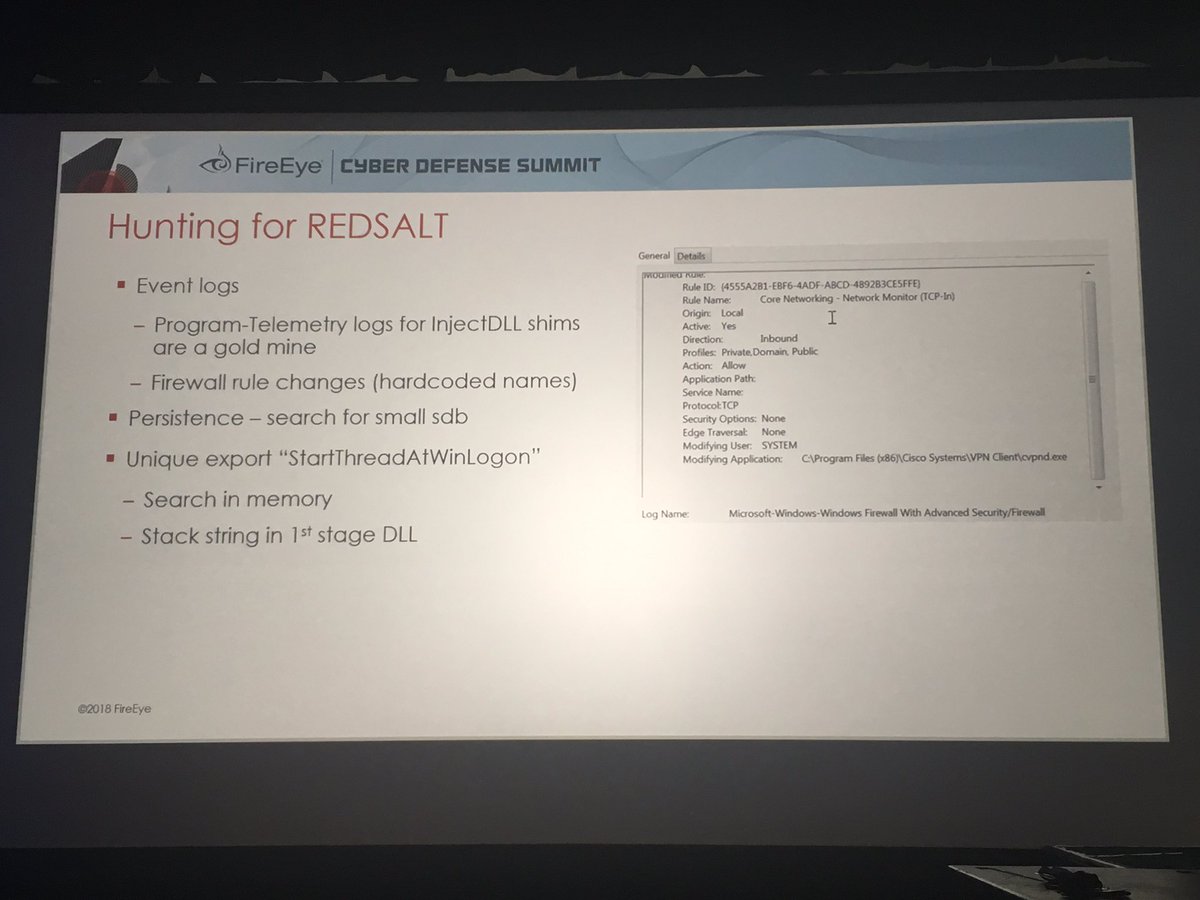
How do you hunt for ACI Shim persistence? Multiple different techniques - but the Windows Program-Telemetry logs are a great place to look
#FireEyeSummit
#FireEyeSummit
What they thought *might* be a boring IR based on initial leads, quickly became interesting when the attacker snapped up the endpoint tooling they just deployed.
Peep that renamed rar.exe snapping up our files for nation state attackers (PLATINUM) to analyze 😅
#FireEyeSummit
Peep that renamed rar.exe snapping up our files for nation state attackers (PLATINUM) to analyze 😅
#FireEyeSummit
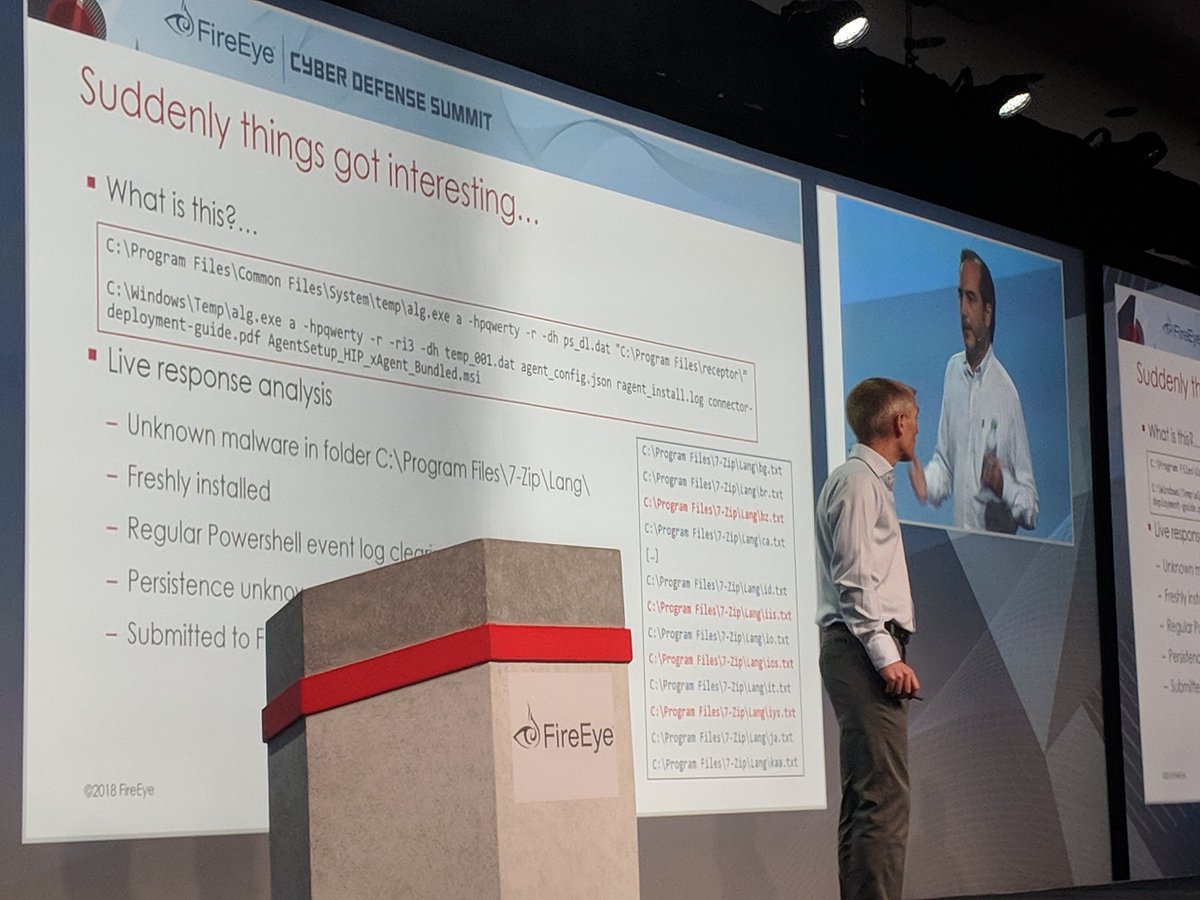
It takes hard #DFIR work to get this point but there is nothing quite like uncovering novel/rare persistence and playing around with new attacker tools to understand them. A bit jealous of Adrien and Matias finding Platinum's #REDSALT. 



Platinum undetected for 9 years at victim.
These guys found multiple APT groups on network.
The talk then gets into additional advanced backdoors with crazier capabilities that were first.
There's so much here. I'm hearing we *might* upload #FireEyeSummit videos to YouTube 🤞
These guys found multiple APT groups on network.
The talk then gets into additional advanced backdoors with crazier capabilities that were first.
There's so much here. I'm hearing we *might* upload #FireEyeSummit videos to YouTube 🤞






