Discover and read the best of Twitter Threads about #FIN7
Most recents (10)
🚨 NEW REPORT ALERT
FIN7 UNVEILED: A deep dive into notorious cybercrime gang
The big day is finally here! 🎊After months of tireless research and analyses, we can present you with the most insightful information: an extensive report on the notorious #cybercrime gang #FIN7.
FIN7 UNVEILED: A deep dive into notorious cybercrime gang
The big day is finally here! 🎊After months of tireless research and analyses, we can present you with the most insightful information: an extensive report on the notorious #cybercrime gang #FIN7.

Thanks to the PTI team, we obtained never-seen-before information about FIN7’s inner workings. We got a deeper understanding of their organizational structures, identities, attack vectors, and proof-supported affiliations with other ransomware groups, among others.
The most enticing remarks of the report are:
🔹 Unveiling FIN7’s development of an auto attack system to exploit the most profitable targets based on their revenue, employee count, headquarters’ location, and website information
Read more👇
🔹 Unveiling FIN7’s development of an auto attack system to exploit the most profitable targets based on their revenue, employee count, headquarters’ location, and website information
Read more👇
🚨New #MicrosoftExchange #vulnerabilities were disclosed, including CVE-2022-41040 and CVE-2022-41082. Threat actors can easily exploit the new vulnerabilities, and bypass #ProxyNotShell URL rewrite mitigations, resulting in many companies facing further #ransomware #attacks.
An example of what such an exploit can do is shown in the picture below, where the #threat actor #FIN7 developed tailored systems to quickly discover and infiltrate the high-value targets by performing mass scans using #Microsoft #exchange #vulnerabilities. 

Our PTI team has already observed activities involving recent vulnerabilities in the wild. Therefore, #PRODAFT recommends that companies fix the vulnerabilities as soon as possible to avoid serious consequences.
#FIN7
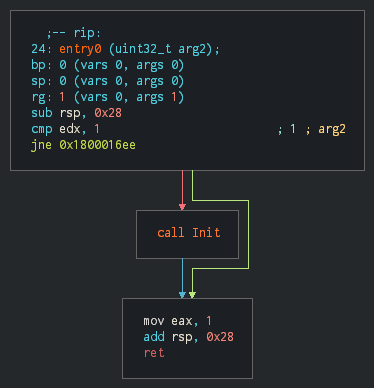
As reported by @KorbenD_Intel, the initial powershell script use DeflateStream method for uncompress the zip in memory and extract it. This execute the second layer that heavily obfuscated. More 70 functions are used for reorder the data for sensible strings and the implant

As reported by @KorbenD_Intel, the initial powershell script use DeflateStream method for uncompress the zip in memory and extract it. This execute the second layer that heavily obfuscated. More 70 functions are used for reorder the data for sensible strings and the implant


OK so this is my last week at @Mandiant / @FireEye 😢
Here's the truth:
♥️ Joining Mandiant was the best decision of my career – the people & company have been SO good to me
🧠 Many of the brilliant minds in security are here & we have FUN every day
1/8
Here's the truth:
♥️ Joining Mandiant was the best decision of my career – the people & company have been SO good to me
🧠 Many of the brilliant minds in security are here & we have FUN every day
1/8
💻🔍 There is no better professional #infosec experience than responding to the intrusions that matter & defending at-scale alongside awesome people. If you have the chance to work here – .
🗓️ One year here is worth many more in experience. So here are some highlights:
2/8
🗓️ One year here is worth many more in experience. So here are some highlights:
2/8
☕️ Doing LRs & writing decoders during my first Mandiant breach response - with #APT17's HIKIT & also BLACKCOFFEE malware using technet for C2: fireeye.com/blog/threat-re…
💰 I was fortunate to lead the first IR for the group that would come to be known as #FIN7
3/8
💰 I was fortunate to lead the first IR for the group that would come to be known as #FIN7
3/8
Just in time for the holidays: #StateoftheHack swag 🖱️👕
You'll never look better enabling those macros. #DailyWoolDrop 😉
customink.com/fundraising/st…
You'll never look better enabling those macros. #DailyWoolDrop 😉
customink.com/fundraising/st…
Most recent order: 3 shirts 👕
with the anonymous message: “Just in time to gift one to Hass, Jimbo, and Oleg, your comrade Andy.” 😂
#FIN7 / Combi Security shirt order extended until tomorrow, #CyberMonday2019: customink.com/fundraising/st… Final cutoff.
with the anonymous message: “Just in time to gift one to Hass, Jimbo, and Oleg, your comrade Andy.” 😂
#FIN7 / Combi Security shirt order extended until tomorrow, #CyberMonday2019: customink.com/fundraising/st… Final cutoff.
All of our new Combi Security “employees” should be receiving their on-boarding packages soon!
There is simply no better shirt to wear to your local payment card-processing establishment! #FIN7 🍟🏨🎰🏪🏦
There is simply no better shirt to wear to your local payment card-processing establishment! #FIN7 🍟🏨🎰🏪🏦

🎟️🍿Movie Night: "Between Two Steves"
🆕#StateOfTheHack
@cglyer & I chat with the top two Steves from #AdvancedPractices 🦅: @stonepwn3000 & @stvemillertime to talk about the front-line technical stories and research presented at the 2019 #FireEyeSummit.
pscp.tv/w/1YpJkYjBleMKj
🆕#StateOfTheHack
@cglyer & I chat with the top two Steves from #AdvancedPractices 🦅: @stonepwn3000 & @stvemillertime to talk about the front-line technical stories and research presented at the 2019 #FireEyeSummit.
pscp.tv/w/1YpJkYjBleMKj
@cglyer @stonepwn3000 @stvemillertime 🗣️
• tracking the groups and techniques that matter
• recent #FIN7 events: fireeye.com/blog/threat-re…
• recent #AdvancedPractices team research, including PDB dossier & summit talks on proactive identification of C2, deep code signing research, and rich header hunting at scale...
• tracking the groups and techniques that matter
• recent #FIN7 events: fireeye.com/blog/threat-re…
• recent #AdvancedPractices team research, including PDB dossier & summit talks on proactive identification of C2, deep code signing research, and rich header hunting at scale...
We highlight a favorite talk
🍎 𝗟𝗶𝘃𝗶𝗻𝗴 𝗼𝗳𝗳 𝘁𝗵𝗲 𝗢𝗿𝗰𝗵𝗮𝗿𝗱 🍎
by @williballenthin, @nicastronaut, @HighViscosity
revealing TTPs & artifacts left behind from the million mac engagement
fireeye.com/blog/threat-re…
We kinda want to do a full #StateOfTheHack on that one...
🍎 𝗟𝗶𝘃𝗶𝗻𝗴 𝗼𝗳𝗳 𝘁𝗵𝗲 𝗢𝗿𝗰𝗵𝗮𝗿𝗱 🍎
by @williballenthin, @nicastronaut, @HighViscosity
revealing TTPs & artifacts left behind from the million mac engagement
fireeye.com/blog/threat-re…
We kinda want to do a full #StateOfTheHack on that one...
🤙💰 Mahalo FIN7: fireeye.com/blog/threat-re…
• On several on-going investigations we saw #FIN7 trying to retool 🏄🏼
• Used DLL search order hijacking of a legit POS management utility with a signed backdoor (0 detections on VirusTotal)
• Hunting for #BOOSTWRITE and #RDFSNIFFER 💳
• On several on-going investigations we saw #FIN7 trying to retool 🏄🏼
• Used DLL search order hijacking of a legit POS management utility with a signed backdoor (0 detections on VirusTotal)
• Hunting for #BOOSTWRITE and #RDFSNIFFER 💳
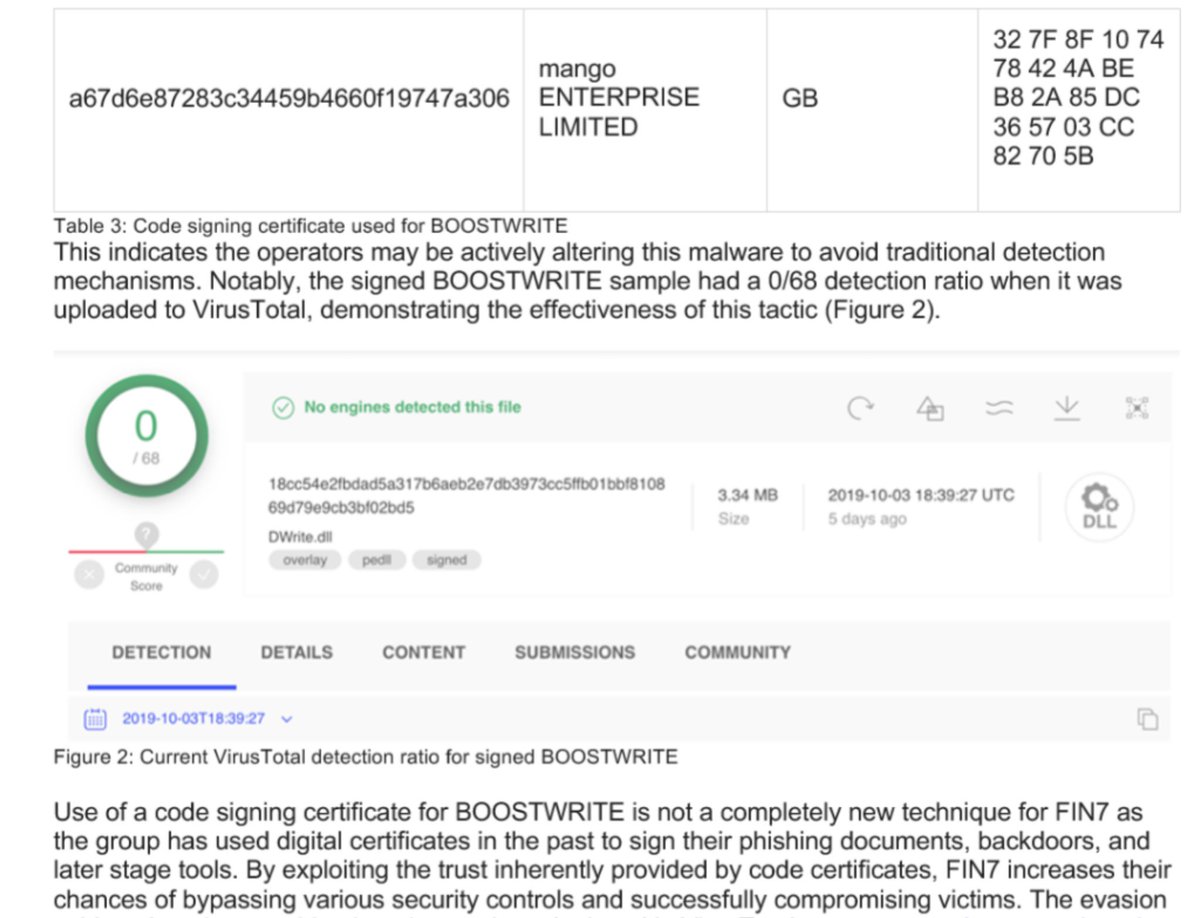
.@josh__yoder & I stayed up much of the night to get this blog out.
The signed #BOOSTWRITE sample is still undetected by static VT scanners: virustotal.com/gui/file/18cc5…
We were fair on why that is and how that doesn't fully represent detection posture.
Then we provided hunting rules.
The signed #BOOSTWRITE sample is still undetected by static VT scanners: virustotal.com/gui/file/18cc5…
We were fair on why that is and how that doesn't fully represent detection posture.
Then we provided hunting rules.

#FIN7's code signing certificate is purportedly from Mango Enterprise Limited in the UK.
Prob not theirs - based on the street address, I suspect there's more car theft than certificate theft 😜: maps.app.goo.gl/MbznDeJPHJr4n5…
We analyze & discuss how to find the certificate anomalies!



Prob not theirs - based on the street address, I suspect there's more car theft than certificate theft 😜: maps.app.goo.gl/MbznDeJPHJr4n5…
We analyze & discuss how to find the certificate anomalies!




Hey I recognize that #AdvancedPractices 🦅 hoodie!
I had a tiny cameo in this 1st part of
a new series highlighting #DFIR/researchers
"hacker:HUNTER - Cashing In" tomorrowunlocked.com/hacking-atms
I expect the series will have #CARBANAK twists & turns + plenty of #FIN7 payment card theft
I had a tiny cameo in this 1st part of
a new series highlighting #DFIR/researchers
"hacker:HUNTER - Cashing In" tomorrowunlocked.com/hacking-atms
I expect the series will have #CARBANAK twists & turns + plenty of #FIN7 payment card theft

@FireEye @TmrwUnlocked "It's very hard to arrest a piece of code." -@stefant
📺 hacker:HUNTER - Cashing In Finale
Showcases the challenges of pursuing & meaningfully impacting fragmented cybercrime group operations.
Also answers the question: "will Nick have a shorter cameo?" 🤣
📺 hacker:HUNTER - Cashing In Finale
Showcases the challenges of pursuing & meaningfully impacting fragmented cybercrime group operations.
Also answers the question: "will Nick have a shorter cameo?" 🤣
In light of the #FIN7 "Combi Security" DOJ indictment, we've released our massive technical post and indicator release: fireeye.com/blog/threat-re…
We reveal new information from @Mandiant IRs about the extent of FIN7's crimes, their innovative techniques, & how to find them today.
We reveal new information from @Mandiant IRs about the extent of FIN7's crimes, their innovative techniques, & how to find them today.
#FIN7 targeted other financial data when they encountered encryption in POS networks. New information today - and certainly helped stack up the charges against Combi Security.
Also @BarryV @stvemillertime first shared SEC filing targeting in March 2017: fireeye.com/blog/threat-re…
Also @BarryV @stvemillertime first shared SEC filing targeting in March 2017: fireeye.com/blog/threat-re…

Crime doesn't pay. Unless you worked for Combi Security, in which case it paid a pretty decent wage for Russian/Ukrainian "pen testers" 😄
Sidenote: @FireEye's red team is hiring but their operations *are* authorized and the only payment card hijinks is over who expenses dinner.
Sidenote: @FireEye's red team is hiring but their operations *are* authorized and the only payment card hijinks is over who expenses dinner.