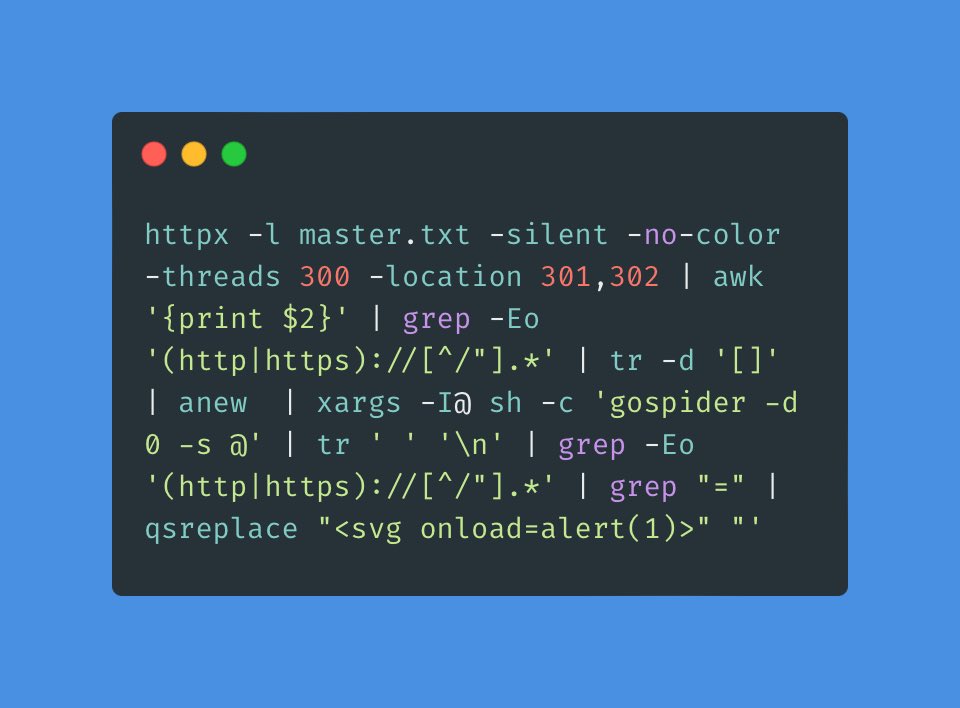
Discover and read the best of Twitter Threads about #BugBountyTip
Most recents (24)
Complete Bug Bounty tool List :)
dnscan github.com/rbsec/dnscan
Knockpy github.com/guelfoweb/knock
Sublist3r github.com/aboul3la/Subli…
massdns github.com/blechschmidt/m…
nmap nmap.org
masscan github.com/robertdavidgra…
#bugbounty #bugbountytips #cybersecurity #hacking
dnscan github.com/rbsec/dnscan
Knockpy github.com/guelfoweb/knock
Sublist3r github.com/aboul3la/Subli…
massdns github.com/blechschmidt/m…
nmap nmap.org
masscan github.com/robertdavidgra…
#bugbounty #bugbountytips #cybersecurity #hacking
EyeWitness github.com/ChrisTruncer/E…
DirBuster sourceforge.net/projects/dirbu…
dirsearch github.com/maurosoria/dir…
Gitrob github.com/michenriksen/g…
git-secrets github.com/awslabs/git-se…
sandcastle github.com/yasinS/sandcas…
bucket_finder digi.ninja/projects/bucke…
DirBuster sourceforge.net/projects/dirbu…
dirsearch github.com/maurosoria/dir…
Gitrob github.com/michenriksen/g…
git-secrets github.com/awslabs/git-se…
sandcastle github.com/yasinS/sandcas…
bucket_finder digi.ninja/projects/bucke…
GoogD0rker github.com/ZephrFish/Goog…
Wayback Machine web.archive.org
waybackurls gist.github.com/mhmdiaa/adf6bf…
Sn1per github.com/1N3/Sn1per/
XRay github.com/evilsocket/xray
wfuzz github.com/xmendez/wfuzz/
patator github.com/lanjelot/patat…
datasploit github.com/DataSploit/dat…
Wayback Machine web.archive.org
waybackurls gist.github.com/mhmdiaa/adf6bf…
Sn1per github.com/1N3/Sn1per/
XRay github.com/evilsocket/xray
wfuzz github.com/xmendez/wfuzz/
patator github.com/lanjelot/patat…
datasploit github.com/DataSploit/dat…
🧵NEW THREAD🧵
Here is how I was able to takeover the whole company's AWS infrastructure under 10 min after a new asset launch at @Hacker0x01 private program

Here is how I was able to takeover the whole company's AWS infrastructure under 10 min after a new asset launch at @Hacker0x01 private program
1. I was invited in the morning to a private program at H1 and the program updated the scope in the evening, So I decided to take a look to see if there is something to hack
2. I visited the main website in scope, to my surprise and thanks to @trufflesec Chrome extension Trufflehog which could be found here chrome.google.com/webstore/detai…
🧵NEW Thread🧵
Here is how I found the easiest SQLi and possible RCE in less than 30 min of recon and dorking
1. I was invited to a private program at @Hacker0x01 and the first thing I usually do is to look at the scope and see if it is a wildcard domain or just a small scope.

Here is how I found the easiest SQLi and possible RCE in less than 30 min of recon and dorking
1. I was invited to a private program at @Hacker0x01 and the first thing I usually do is to look at the scope and see if it is a wildcard domain or just a small scope.


2. Found that the program accepts all vulnerabilities related to their assets and of course third party assets are OOS
3. I used @leak_ix search engine at leakix.net and used this dork [+target_name ++plugin:"GitConfigHttpPlugin"]
Note : this is used to search for already scanned websites that have /.git exposed
Note : this is used to search for already scanned websites that have /.git exposed
Top free #Cybersecurity and ethical #hacking certification⚔️📓
1./Introduction to IT & Cybersecurity (Cybrary) = cybrary.it/course/introdu…
2./Mobile App Security (Cybrary) = cybrary.it/course/mobile-…
3./Introduction to Cybersecurity (edx) = edx.org/course/introdu…
1./Introduction to IT & Cybersecurity (Cybrary) = cybrary.it/course/introdu…
2./Mobile App Security (Cybrary) = cybrary.it/course/mobile-…
3./Introduction to Cybersecurity (edx) = edx.org/course/introdu…
4./Introduction to Cyber Security (Future Learn) = futurelearn.com/courses/introd…
5./Introduction to Encryption and Cryptography (Future Learn) = futurelearn.com/courses/encryp…
6./Fundamentals of Red Hat Linux (edx) = edx.org/course/fundame…
5./Introduction to Encryption and Cryptography (Future Learn) = futurelearn.com/courses/encryp…
6./Fundamentals of Red Hat Linux (edx) = edx.org/course/fundame…
7./ Introduction to Cybersecurity (Codecademy) = codecademy.com/learn/introduc…
8./ Cisco Networking Academy = netacad.com/courses/all-co…
9./ SANS Cyber Aces (covers foundation areas of cybersecurity) - cyberaces.org/courses.html
10./ Opensecurity - = opensecuritytraining.info/Training.html
8./ Cisco Networking Academy = netacad.com/courses/all-co…
9./ SANS Cyber Aces (covers foundation areas of cybersecurity) - cyberaces.org/courses.html
10./ Opensecurity - = opensecuritytraining.info/Training.html
Vulnexp 90 | Day69
CRLF Areas to Inspect
➡️Areas to Inspect:
#bugbountytips #bugbountytip
Thread 🧵 : 👇
CRLF Areas to Inspect
➡️Areas to Inspect:
#bugbountytips #bugbountytip
Thread 🧵 : 👇

Areas to Inspect:
• HTTP Headers: CRLF Injection attacks can occur in HTTP headers, such as the "User-Agent" or "Referer" headers. Attackers can insert CRLF sequences into these headers to inject additional headers or modify the response.
• HTTP Headers: CRLF Injection attacks can occur in HTTP headers, such as the "User-Agent" or "Referer" headers. Attackers can insert CRLF sequences into these headers to inject additional headers or modify the response.
• Cookies: Cookies are often used to store user session information, and they can also be vulnerable to CRLF Injection attacks. An attacker can insert CRLF sequences into a cookie value to modify the response or inject additional headers.
Vulnexp 90 | Day68
CRLF Injection
CRLF is a type of web-based attack that allows an attacker to inject malicious code or unwanted data into the HTTP response of a web application.
➡️Vulnerabilities Occur:
#bugbountytips #bugbountytip
Thread 🧵 : 👇
CRLF Injection
CRLF is a type of web-based attack that allows an attacker to inject malicious code or unwanted data into the HTTP response of a web application.
➡️Vulnerabilities Occur:
#bugbountytips #bugbountytip
Thread 🧵 : 👇

Vulnerabilities Occur:
• CRLF can occur when a web application fails to properly sanitize user-supplied input or validate input parameters. Specifically, they can occur in any part of the HTTP response that accepts user input, including HTTP headers, cookies, and form input.
• CRLF can occur when a web application fails to properly sanitize user-supplied input or validate input parameters. Specifically, they can occur in any part of the HTTP response that accepts user input, including HTTP headers, cookies, and form input.
• For example, an attacker can insert a CRLF sequence into an HTTP header to inject additional headers or modify the response. Alternatively, they may use CRLF to inject malicious code, such as JavaScript, into the response body, leading to cross-site scripting (XSS) attacks.
In the world of bug bounty hunting, Insecure Direct Object References (IDORs) can be a goldmine. In this thread, we'll share advanced tips to sharpen your IDOR detection skills. Let's dive in! 🌊🔍
#bugbountytip #bugbountytips #CyberSecurityAwareness
1/n
#bugbountytip #bugbountytips #CyberSecurityAwareness
1/n
Always begin with a thorough understanding of the application you're testing. Identify all possible user roles and their access rights. This knowledge is crucial for accurately identifying IDOR vulnerabilities. 🧠📝
Pay attention to API endpoints that handle user-specific data. Keep an eye out for patterns in URL parameters or request payloads. Examine how the application validates user input and authorization checks for these sensitive resources. 📡🔬
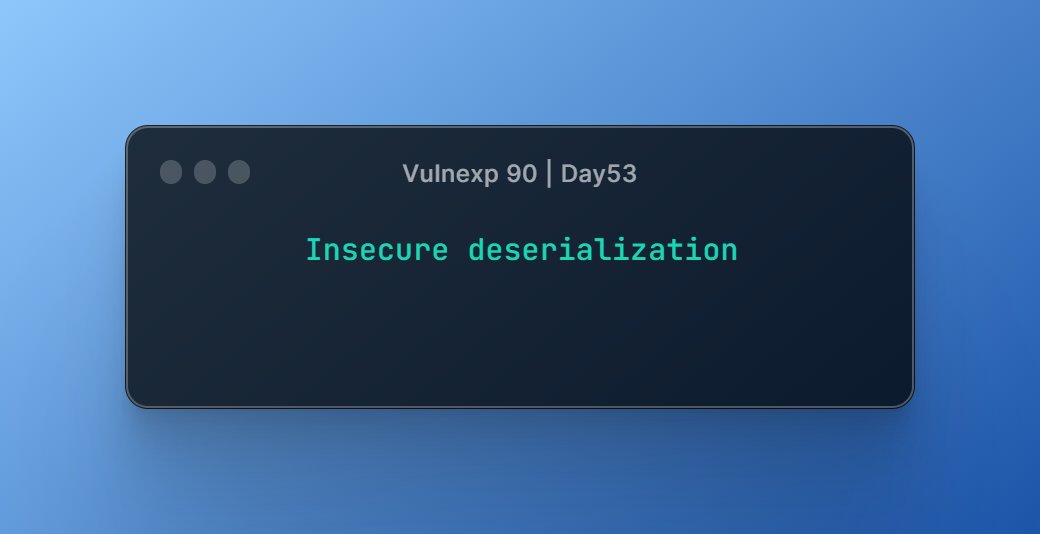
Vulnexp 90 | Day53
➡️Insecure deserialization
when an attacker manipulates the way that HTTP requests are interpreted by a web server or a proxy server.
#bugbountytips #bugbountytip
Thread 🧵 : 👇
➡️Insecure deserialization
when an attacker manipulates the way that HTTP requests are interpreted by a web server or a proxy server.
#bugbountytips #bugbountytip
Thread 🧵 : 👇
• Insecure deserialization is a type of vulnerability that can occur in applications that involve the serialization and deserialization of data.
• Serialization is the process of converting an object , data structure into a format that can be transmitted or stored.
• Serialization is the process of converting an object , data structure into a format that can be transmitted or stored.
• XML, or binary data. Deserialization is the process of converting the serialized data back into an object or data structure.
• When an application receives serialized data, it may deserialize it to reconstruct the original object or data structure. However,
• When an application receives serialized data, it may deserialize it to reconstruct the original object or data structure. However,
Here is short writeup on how I found some hardcoded credentials inside of an exe file and got paid 2000$ even the asset was OUT OF SCOPE!
📌THREAD📌
1. I got invited to a private program with new assets
2. The asset was a web application for an Electron desktop app

📌THREAD📌
1. I got invited to a private program with new assets
2. The asset was a web application for an Electron desktop app


3. I tried to find the executable for the In scope app just to understand what the app will looks like when installed in the machine
4. I finally downloaded the app from the official website lf the target and tried to extract the Exe with tools like Winzip (Electron app can be easily extracted)
Collection of RCE write-ups. thanks to all researchers for sharing there findings.
link.medium.com/MyvJZn2E5wb
github.com/httpvoid/write…
link.medium.com/3ZDBao5E5wb
link.medium.com/QJ9Jjt8E5wb
infosecwriteups.com/how-i-found-my… #bugbountytip #bugbountytips #RCE #cybersecurity #Pentesting #writeup
link.medium.com/MyvJZn2E5wb
github.com/httpvoid/write…
link.medium.com/3ZDBao5E5wb
link.medium.com/QJ9Jjt8E5wb
infosecwriteups.com/how-i-found-my… #bugbountytip #bugbountytips #RCE #cybersecurity #Pentesting #writeup

One of the most critical talents a cybersecurity analyst must have is detecting and blocking a malicious IP address.
Here are a few best online tools to detect malicious IP addresses:
🧵
#TheSecureEdge #BugBounty #bugbountytip #hacking #infosec
Here are a few best online tools to detect malicious IP addresses:
🧵
#TheSecureEdge #BugBounty #bugbountytip #hacking #infosec
· AbuseIPDB (abuseipdb.com)
· CheckPhish (checkphish.ai)
· BrightCloud URL/IP Lookup (brightcloud.com/tools/url-ip-l…)
· CheckPhish (checkphish.ai)
· BrightCloud URL/IP Lookup (brightcloud.com/tools/url-ip-l…)
· IBM X-Force Exchange (exchange.xforce.ibmcloud.com)
· IPQualityScore (ipqualityscore.com/free-ip-lookup…)
· Malware Domain List (malwaredomainlist.com/mdl.php)
· IPQualityScore (ipqualityscore.com/free-ip-lookup…)
· Malware Domain List (malwaredomainlist.com/mdl.php)
[0]
Hello Hackers
I just created a tool/script to automate initial recon in #bugbounty.
[ Check the thread for more info about all MODE available in this tool ]
URL:- github.com/thecyberneh/sc…
Hello Hackers
I just created a tool/script to automate initial recon in #bugbounty.
[ Check the thread for more info about all MODE available in this tool ]
URL:- github.com/thecyberneh/sc…

[1]
1. EXP :- FULL EXPLOITATION MODE
contains functions as
- Effective Subdomain Enumeration with different services and open-source tools
- Effective URL Enumeration ( HTTP and HTTPS service )
- Run Vulnerability Detection with Nuclei
Subdomain Takeover Test on previous results
1. EXP :- FULL EXPLOITATION MODE
contains functions as
- Effective Subdomain Enumeration with different services and open-source tools
- Effective URL Enumeration ( HTTP and HTTPS service )
- Run Vulnerability Detection with Nuclei
Subdomain Takeover Test on previous results
[2]
2. SUB : SUBDOMAIN ENUMERATION MODE contains functions as
Effective Subdomain Enumeration with different services and open source tools, You can use this mode if you only want to get subdomains from this tool or we can say Automation of Subdomain Enumeration.
2. SUB : SUBDOMAIN ENUMERATION MODE contains functions as
Effective Subdomain Enumeration with different services and open source tools, You can use this mode if you only want to get subdomains from this tool or we can say Automation of Subdomain Enumeration.
Day 1⃣9⃣/2⃣0⃣ -- [Subdomain Takeover]
➡️ Subdomain Takeover occurs when an attacker gains control over a subdomain of a target domain.
➡️ Below are some of the best Tips & References for Subdomain Takeover (Feel Free To Share)
🧵🧵👇👇
#BugBounty
#bugbountytip
➡️ Subdomain Takeover occurs when an attacker gains control over a subdomain of a target domain.
➡️ Below are some of the best Tips & References for Subdomain Takeover (Feel Free To Share)
🧵🧵👇👇
#BugBounty
#bugbountytip
Day 1⃣8⃣/2⃣0⃣ -- [XXE - XML External Entity]
➡️ XXE - is an application-layer cybersecurity attack that exploits an XXE vulnerability to parse XML input
➡️ Below some of the best Tips & References for XXE (Feel Free To Share)
🧵🧵👇👇
#BugBounty
#bugbountytip
➡️ XXE - is an application-layer cybersecurity attack that exploits an XXE vulnerability to parse XML input
➡️ Below some of the best Tips & References for XXE (Feel Free To Share)
🧵🧵👇👇
#BugBounty
#bugbountytip
Find JavaScript Files
—————————
I've opened My Bug Bounty tips Group => Join Link : t.me/bugbountyresou…
—————————
#bugbounty #Infosec #CyberSec
—————————
I've opened My Bug Bounty tips Group => Join Link : t.me/bugbountyresou…
—————————
#bugbounty #Infosec #CyberSec

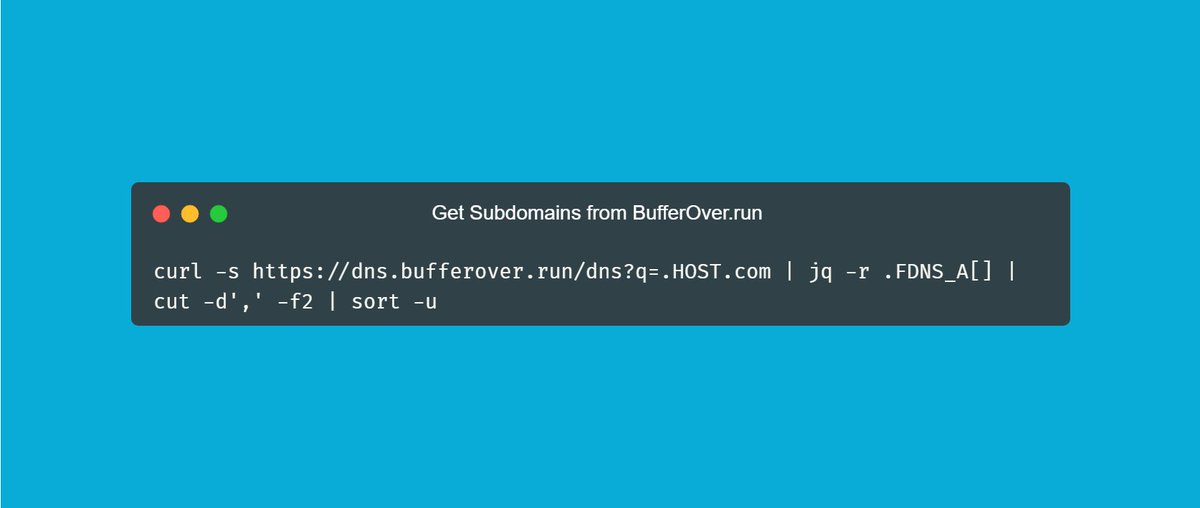
Get Subdomains from BufferOver. run
—————————
I've opened My Bug Bounty tips Group => Join Link : t.me/bugbountyresou…
—————————
#bugbounty #Infosec #CyberSec
—————————
I've opened My Bug Bounty tips Group => Join Link : t.me/bugbountyresou…
—————————
#bugbounty #Infosec #CyberSec
3 Simple broken access control vulnerabilities you should hunt for, while logic vulnerabilities testing
#BugBounty
#bugbountytip
#bugbountytips
#Bugcrowd
👇👇
#BugBounty
#bugbountytip
#bugbountytips
#Bugcrowd
👇👇
If the website allows creating an organisation you have ex.
2 roles admin && admin
access the user's information endpoint with the admin 2 , save the request
With the previous admin downgrade his role to few user and execute the request and see If you can access the users PII
2 roles admin && admin
access the user's information endpoint with the admin 2 , save the request
With the previous admin downgrade his role to few user and execute the request and see If you can access the users PII
2:
Remove the user from the organization and save the join URL For the organization, after removing the user use the same URL And see if you can rejoin the organization using the old URL After you removed from the ORG
Remove the user from the organization and save the join URL For the organization, after removing the user use the same URL And see if you can rejoin the organization using the old URL After you removed from the ORG
➡ Use intruder to send many reset links/token to your email in a short amount of time and compare the links/tokens.
If only a few digits are different you can brute force them. After you can do the same with 2 different emails
If only a few digits are different you can brute force them. After you can do the same with 2 different emails
➡ HTTP Parameter Pollution
When requesting a password reset link:
email=victim@domain.com&youremail@domain.com
When resetting password:
token={token}&email=youremail@domain.com&email=victim@domain.com
When requesting a password reset link:
email=victim@domain.com&youremail@domain.com
When resetting password:
token={token}&email=youremail@domain.com&email=victim@domain.com
30 Search Engines for Cybersecurity Researchers:
1. Dehashed—View leaked credentials.
2. SecurityTrails—Extensive DNS data.
3. DorkSearch—Really fast Google dorking.
4. ExploitDB—Archive of various exploits.
#cybersecurity #infosec #bugbounty
1. Dehashed—View leaked credentials.
2. SecurityTrails—Extensive DNS data.
3. DorkSearch—Really fast Google dorking.
4. ExploitDB—Archive of various exploits.
#cybersecurity #infosec #bugbounty
5. ZoomEye—Gather information about targets.
6. Pulsedive—Search for threat intelligence.
7. GrayHatWarefare—Search public S3 buckets.
8. PolySwarm—Scan files and URLs for threats.
9. Fofa—Search for various threat intelligence.
10. LeakIX—Search publicly indexed information.
6. Pulsedive—Search for threat intelligence.
7. GrayHatWarefare—Search public S3 buckets.
8. PolySwarm—Scan files and URLs for threats.
9. Fofa—Search for various threat intelligence.
10. LeakIX—Search publicly indexed information.
11. DNSDumpster—Search for DNS records quickly.
13. FullHunt—Search and discovery attack surfaces.
14. AlienVault—Extensive threat intelligence feed.
12. ONYPHE—Collects cyber-threat intelligence data.
15. Grep App—Search across a half million git repos.
13. FullHunt—Search and discovery attack surfaces.
14. AlienVault—Extensive threat intelligence feed.
12. ONYPHE—Collects cyber-threat intelligence data.
15. Grep App—Search across a half million git repos.
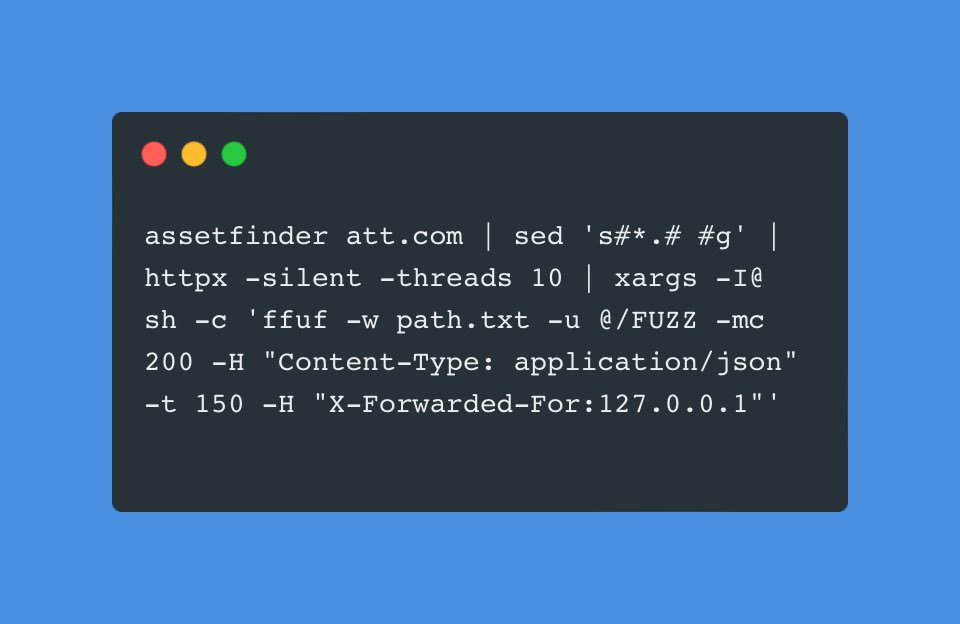
Search to files using assetfinder and ffuf : [Check IMG 👇]
—————————
I've opened My Bug Bounty tips Group => Join Link : t.me/bugbountyresou…
—————————
#bugbounty #bugbountytip #infosec
—————————
I've opened My Bug Bounty tips Group => Join Link : t.me/bugbountyresou…
—————————
#bugbounty #bugbountytip #infosec
Tip #1 #bugbounty #infosec
Use GIT as a recon tool. Find the target's GIT repositories, clone them, and then check the logs for information on the team not necessarily in the source code. Say the target is Reddit and I want to see which developers work on certain projects.
Use GIT as a recon tool. Find the target's GIT repositories, clone them, and then check the logs for information on the team not necessarily in the source code. Say the target is Reddit and I want to see which developers work on certain projects.
Tip #2
Look for GitLab instances on targets or belonging to the target. When you stumble across the GitLab login panel, navigate to /explore. Misconfigured instances do not require authentication to view the internal projects.
Look for GitLab instances on targets or belonging to the target. When you stumble across the GitLab login panel, navigate to /explore. Misconfigured instances do not require authentication to view the internal projects.
How a simple web-app assessment lead to complete #AzureAd tenant takeover 🤯
🧵 👇
#Azure #AzureKubernetesService #aks #Kubernetes #KubernetesSecurity #k8s #bugbounty #bugbountytips #bugbountytip #DevSecOps
🧵 👇
#Azure #AzureKubernetesService #aks #Kubernetes #KubernetesSecurity #k8s #bugbounty #bugbountytips #bugbountytip #DevSecOps
1. Poorly-designed file upload functionality lead to RCE
2. Turned out the app was running in a container managed by #AzureKubernetesService (#AKS)
3. #Container was mounting a service account with permissions to deploy #pods in the same namespace
2. Turned out the app was running in a container managed by #AzureKubernetesService (#AKS)
3. #Container was mounting a service account with permissions to deploy #pods in the same namespace
4. I deployed a new pod with hostPath root volume. Deployment was not blocked by any security policy. #Pod got deployed
5. I exec-ed into the pod's #container and escaped it through its hostPath volume. #privesc to the #AKS node succeeded!
5. I exec-ed into the pod's #container and escaped it through its hostPath volume. #privesc to the #AKS node succeeded!
12 #bugbountytips you NEED to know about! 🧵
A #bugbountytip is a short trick that can help you find your next bug!
Here are some quick wins you can start implementing today to become a better hunter 👇
A #bugbountytip is a short trick that can help you find your next bug!
Here are some quick wins you can start implementing today to become a better hunter 👇
[1️⃣] Automating SSRF by @Regala_
Instead of manually looking for SSRF sinks, why don't we let @Burp_Suite do the hard work? 👇
Instead of manually looking for SSRF sinks, why don't we let @Burp_Suite do the hard work? 👇
[2️⃣] Exploiting e-mail systems by @securinti 📧
Did you know you can exploit an SQL injection using an e-mail address? Neither do developers!
And it's not just SQLi! Find out more 👇
Did you know you can exploit an SQL injection using an e-mail address? Neither do developers!
And it's not just SQLi! Find out more 👇
Introduction to #XSS
Learn the basics of 𝐂𝐫𝐨𝐬𝐬-𝐒𝐢𝐭𝐞 𝐒𝐜𝐫𝐢𝐩𝐭𝐢𝐧𝐠 (𝐗𝐒𝐒)
Thread🧵👇
#bugbounty #bugbountytips #bugbountytip #cybersecurity #cybersecuritytips #infosec #infosecurity #hacking
Learn the basics of 𝐂𝐫𝐨𝐬𝐬-𝐒𝐢𝐭𝐞 𝐒𝐜𝐫𝐢𝐩𝐭𝐢𝐧𝐠 (𝐗𝐒𝐒)
Thread🧵👇
#bugbounty #bugbountytips #bugbountytip #cybersecurity #cybersecuritytips #infosec #infosecurity #hacking
Let's inspect the name first:
The 𝐒𝐜𝐫𝐢𝐩𝐭𝐢𝐧𝐠 part indicates, obviously, scripting, so we can think about what kind of scripting we know exist in Web Apps: HTML & JavaScript being the 2 most common.
Secondly, XSS is part of the INJECTION bug class (see @owasp's Top 10)
The 𝐒𝐜𝐫𝐢𝐩𝐭𝐢𝐧𝐠 part indicates, obviously, scripting, so we can think about what kind of scripting we know exist in Web Apps: HTML & JavaScript being the 2 most common.
Secondly, XSS is part of the INJECTION bug class (see @owasp's Top 10)
So, we now know XSS consists of injecting scripts in websites.
Types of XSS:
1. Reflected
2. Stored
3. DOM-based
They can also be Blind too (you don't see the reflection)
As this thread is aimed at beginners, I will focus on the first 2 as they're easier to understand at first
Types of XSS:
1. Reflected
2. Stored
3. DOM-based
They can also be Blind too (you don't see the reflection)
As this thread is aimed at beginners, I will focus on the first 2 as they're easier to understand at first
TopMost Search Engines for hackers
1. Dehashed—View leaked credentials.
2. SecurityTrails—Extensive DNS data.
3. DorkSearch—Really fast Google dorking.
#cybersecurity #hacking #bugbounty #bugbountytips #bugbountytip #infosec
More👇(1/n) :
1. Dehashed—View leaked credentials.
2. SecurityTrails—Extensive DNS data.
3. DorkSearch—Really fast Google dorking.
#cybersecurity #hacking #bugbounty #bugbountytips #bugbountytip #infosec
More👇(1/n) :

4. ExploitDB—Archive of various exploits.
5. ZoomEye—Gather information about targets.
6. Pulsedive—Search for threat intelligence.
7. GrayHatWarefare—Search public S3 buckets.
#cybersecurity #hacking #bugbounty #bugbountytips #bugbountytip #infosec
More👇(2/n) :
5. ZoomEye—Gather information about targets.
6. Pulsedive—Search for threat intelligence.
7. GrayHatWarefare—Search public S3 buckets.
#cybersecurity #hacking #bugbounty #bugbountytips #bugbountytip #infosec
More👇(2/n) :
8. PolySwarm—Scan files and URLs for threats.
9. Fofa—Search for various threat intelligence.
10. LeakIX—Search publicly indexed information.
11. DNSDumpster—Search for DNS records quickly.
#cybersecurity #hacking #bugbounty #bugbountytips #bugbountytip #infosec
More👇(3/n) :
9. Fofa—Search for various threat intelligence.
10. LeakIX—Search publicly indexed information.
11. DNSDumpster—Search for DNS records quickly.
#cybersecurity #hacking #bugbounty #bugbountytips #bugbountytip #infosec
More👇(3/n) :