Discover and read the best of Twitter Threads about #cybersecuritytips
Most recents (24)
The CIA not only invests with Venture Capitals, but also helps with finding interesting projects and security issues.
Why is it worth #revoking smart contracts that you interacted with?
A thread! 🧵
1/11
#CIA #crypto #approval #revoke #exploit #cybersecuritytips
Why is it worth #revoking smart contracts that you interacted with?
A thread! 🧵
1/11
#CIA #crypto #approval #revoke #exploit #cybersecuritytips
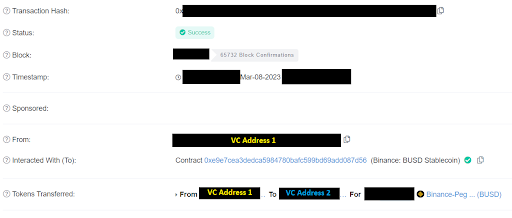
Yesterday, we received an information from one of the Venture Capital company that after sending a transfer to other address, the funds immediately disappeared and according to their findings everything went to 0xdead~.
They asked us for assistance and clarification.
2/11
They asked us for assistance and clarification.
2/11
FREE cybersecurity certifications
- 15 Courses by Qualys 🧵📢
#infosec #cybersecurity #cybersecuritytips #Hacking
1. Vulnerability Management: lnkd.in/g64maMet
2. Global IT Asset Inventory: lnkd.in/gXR5bD5N
3. Scanning Strategies: lnkd.in/g6cQjQuh
- 15 Courses by Qualys 🧵📢
#infosec #cybersecurity #cybersecuritytips #Hacking
1. Vulnerability Management: lnkd.in/g64maMet
2. Global IT Asset Inventory: lnkd.in/gXR5bD5N
3. Scanning Strategies: lnkd.in/g6cQjQuh
4. Reporting Strategies: lnkd.in/gs6Vn-DA
5. Patch Management: lnkd.in/gnWVDCNp
6. Policy Compliance: lnkd.in/g5SXKncJ
7. PCI Compliance: lnkd.in/gZns6Xdf
5. Patch Management: lnkd.in/gnWVDCNp
6. Policy Compliance: lnkd.in/g5SXKncJ
7. PCI Compliance: lnkd.in/gZns6Xdf
8. Endpoint Detection & Response: lnkd.in/gw22Y__E
9. Vulnerability Management 2: lnkd.in/gYAFfAuT
10. Cloud Security Assessment & Response: lnkd.in/grrHivcW
11. API Fundamentals: lnkd.in/gngVxhbu
9. Vulnerability Management 2: lnkd.in/gYAFfAuT
10. Cloud Security Assessment & Response: lnkd.in/grrHivcW
11. API Fundamentals: lnkd.in/gngVxhbu
Here's 30 fun cybersecurity search engines! 📢
Credit: @danielmakelley
#infosec #cybersecuritytips #Hacking 🧵
1. DeHashed—View leaked credentials.
2. SecurityTrails—Extensive DNS data.
3. DorkSearch—Really fast Google dorking.
Credit: @danielmakelley
#infosec #cybersecuritytips #Hacking 🧵
1. DeHashed—View leaked credentials.
2. SecurityTrails—Extensive DNS data.
3. DorkSearch—Really fast Google dorking.
4. ExploitDB—Archive of various exploits.
5. ZoomEye—Gather information about targets.
6. Pulsedive—Search for threat intelligence.
7. GrayHatWarfare—Search public S3 buckets.
8. PolySwarm—Scan files and URLs for threats.
9. Fofa—Search for various threat intelligence.
5. ZoomEye—Gather information about targets.
6. Pulsedive—Search for threat intelligence.
7. GrayHatWarfare—Search public S3 buckets.
8. PolySwarm—Scan files and URLs for threats.
9. Fofa—Search for various threat intelligence.
10. LeakIX—Search publicly indexed information.
11. DNSDumpster—Search for DNS records quickly.
12. FullHunt—Search and discovery attack surfaces.
13. AlienVault—Extensive threat intelligence feed.
14. ONYPHE—Collects cyber-threat intelligence data.
11. DNSDumpster—Search for DNS records quickly.
12. FullHunt—Search and discovery attack surfaces.
13. AlienVault—Extensive threat intelligence feed.
14. ONYPHE—Collects cyber-threat intelligence data.
[0]
Hello Hackers
I just created a tool/script to automate initial recon in #bugbounty.
[ Check the thread for more info about all MODE available in this tool ]
URL:- github.com/thecyberneh/sc…
Hello Hackers
I just created a tool/script to automate initial recon in #bugbounty.
[ Check the thread for more info about all MODE available in this tool ]
URL:- github.com/thecyberneh/sc…

[1]
1. EXP :- FULL EXPLOITATION MODE
contains functions as
- Effective Subdomain Enumeration with different services and open-source tools
- Effective URL Enumeration ( HTTP and HTTPS service )
- Run Vulnerability Detection with Nuclei
Subdomain Takeover Test on previous results
1. EXP :- FULL EXPLOITATION MODE
contains functions as
- Effective Subdomain Enumeration with different services and open-source tools
- Effective URL Enumeration ( HTTP and HTTPS service )
- Run Vulnerability Detection with Nuclei
Subdomain Takeover Test on previous results
[2]
2. SUB : SUBDOMAIN ENUMERATION MODE contains functions as
Effective Subdomain Enumeration with different services and open source tools, You can use this mode if you only want to get subdomains from this tool or we can say Automation of Subdomain Enumeration.
2. SUB : SUBDOMAIN ENUMERATION MODE contains functions as
Effective Subdomain Enumeration with different services and open source tools, You can use this mode if you only want to get subdomains from this tool or we can say Automation of Subdomain Enumeration.
5 PRO tips to use in your enumeration for Active Directory pentesting:
(thread)
(thread)
1. Leverage LDAP queries and enumeration tools such as ADRecon and BloodHound to gather as much information as possible about the Active Directory environment, including user accounts, group memberships, and access rights.
2. Look for common misconfigurations, such as weak passwords and unsecured administrative accounts, as well as access controls that allow users to elevate their privileges or access sensitive data.
Let's learn Red Teaming together
[Thread]🧵👇
[Thread]🧵👇
Day 0⃣8⃣/2⃣0⃣ -- [Hacking File Upload Functionality]
➡️ Hitting P1's - RCE, SQL Injection, SSRF, Stored XSS, LFI, XXE, IDOR e.t.c
➡️ ➰ Below some of the best Tips & References (Feel Free To Share)🧵🧵👇👇
🧵🧵👇👇
#BugBounty
#bugbountytips
#cybersecuritytips
➡️ Hitting P1's - RCE, SQL Injection, SSRF, Stored XSS, LFI, XXE, IDOR e.t.c
➡️ ➰ Below some of the best Tips & References (Feel Free To Share)🧵🧵👇👇
🧵🧵👇👇
#BugBounty
#bugbountytips
#cybersecuritytips
Day 0⃣7⃣/2⃣0⃣ -- [Hacking Different Web Application Functionalities]
➡️ Groups & Teams
➡️ Email Contact
➡️ Submit Feedback
➡️ ➰ Below are Functionalities, Tips & References (Feel Free To Share)🧵🧵👇👇
🧵🧵👇👇
#BugBounty
#bugbountytips
#cybersecuritytips
➡️ Groups & Teams
➡️ Email Contact
➡️ Submit Feedback
➡️ ➰ Below are Functionalities, Tips & References (Feel Free To Share)🧵🧵👇👇
🧵🧵👇👇
#BugBounty
#bugbountytips
#cybersecuritytips
o/n
➡️ Chat Box/Support/Customer Care
➡️ Comment Functionality
➡️ Subscribe/Unsubscribe
➡️ Ecommerce Platform
➡️ Search Functionality
➡️ WebSockets
➡️ User-Agents
➡️ Cookies & Sessions
➡️ JSON Web Tokens
➡️ Chat Box/Support/Customer Care
➡️ Comment Functionality
➡️ Subscribe/Unsubscribe
➡️ Ecommerce Platform
➡️ Search Functionality
➡️ WebSockets
➡️ User-Agents
➡️ Cookies & Sessions
➡️ JSON Web Tokens
Day ➰➰/2⃣0⃣ -- [Hacking Bug Bounty Checklists/Methodologies]
➡️ Day ➰➰, Taking A Break! But Let's Talk About Different Hacking Methodologies.
➡️ Below are Some Of The Best Hacking Methodologies(Feel Free To Share)🧵🧵👇👇
#BugBounty
#bugbountytips
#cybersecuritytips
➡️ Day ➰➰, Taking A Break! But Let's Talk About Different Hacking Methodologies.
➡️ Below are Some Of The Best Hacking Methodologies(Feel Free To Share)🧵🧵👇👇
#BugBounty
#bugbountytips
#cybersecuritytips
Day 0⃣6⃣/2⃣0⃣ -- [Delete/Deactivating An Account & Logout Vulnerabilities]
➡️ Day 6, Have You Ever Known That Deactivating & Logout Feature Can Be Hacked & Earn You Bounties?
➡️ Below are Tips & References (Feel Free To Share)🧵🧵👇👇
#BugBounty
#bugbountytips
#cybersecuritytips
➡️ Day 6, Have You Ever Known That Deactivating & Logout Feature Can Be Hacked & Earn You Bounties?
➡️ Below are Tips & References (Feel Free To Share)🧵🧵👇👇
#BugBounty
#bugbountytips
#cybersecuritytips
Day 0⃣5⃣/2⃣0⃣ -- [Web Application Profile/Dashboard Hacking]
➡️ Day 5, Profile Update/Dashboard Vulnerabilities & References.
➡️ Below are Tips & References (Feel Free To Share)🧵🧵👇👇
#BugBounty
#bugbountytips
#cybersecuritytips
➡️ Day 5, Profile Update/Dashboard Vulnerabilities & References.
➡️ Below are Tips & References (Feel Free To Share)🧵🧵👇👇
#BugBounty
#bugbountytips
#cybersecuritytips
1/n
IDOR on the dashboard
IDOR on the dashboard
2/n
Instagram IDOR
Instagram IDOR
Day 0⃣4⃣/2⃣0⃣ -- [Hacking A Web Application Via Password Change Functionality]
➡️ Day 4, Hack A Web Application Via "Password Change Functionality"
➡️ Below are Tips & References (Feel Free To Share)🧵🧵👇👇
#BugBounty
#bugbountytips
#cybersecuritytips "No Resting Only Hacking!"
➡️ Day 4, Hack A Web Application Via "Password Change Functionality"
➡️ Below are Tips & References (Feel Free To Share)🧵🧵👇👇
#BugBounty
#bugbountytips
#cybersecuritytips "No Resting Only Hacking!"
Day 0⃣3⃣/2⃣0⃣ -- [How To Hack A Login Page!]
➡️ Day 3, How To Hack A Login Page "Exploiting Vulnerabilities On A Login Page"
➡️ Below are Tips & References (Feel Free To Share)🧵🧵👇👇
#BugBounty
#bugbountytips
#cybersecuritytips
➡️ Day 3, How To Hack A Login Page "Exploiting Vulnerabilities On A Login Page"
➡️ Below are Tips & References (Feel Free To Share)🧵🧵👇👇
#BugBounty
#bugbountytips
#cybersecuritytips
Day 0⃣2⃣/2⃣0⃣ -- [Registration/SignUp Page Vulnerabilities]
➡️ Day 2, we will cover potential vulnerabilities that can affect a Registration/Sign-Up Page of a web application
➡️ Below are Tips & References (Feel Free To Share)🧵🧵👇👇
#BugBounty
#bugbountytips
#cybersecuritytips
➡️ Day 2, we will cover potential vulnerabilities that can affect a Registration/Sign-Up Page of a web application
➡️ Below are Tips & References (Feel Free To Share)🧵🧵👇👇
#BugBounty
#bugbountytips
#cybersecuritytips
Day 0⃣1⃣/2⃣0⃣ -- [Bug Bounty Reconnaissance/Information Gathering]
➡️ Being Day 1, Recon is usually the first approach when handling your target.
➡️ Below are some of the Best Checklists/Bug Bounty RECON references & Tips🧵🧵👇👇
#BugBounty
#bugbountytips
#cybersecuritytips
➡️ Being Day 1, Recon is usually the first approach when handling your target.
➡️ Below are some of the Best Checklists/Bug Bounty RECON references & Tips🧵🧵👇👇
#BugBounty
#bugbountytips
#cybersecuritytips
1/n
The Bug Hunter's Methodology v4.0 - Recon Edition by @Jhaddix
The Bug Hunter's Methodology v4.0 - Recon Edition by @Jhaddix
2/n
@_zwink Target Reconnaissance & Approach
@_zwink Target Reconnaissance & Approach
Bug Testing Methodology Series:
𝐒𝐒𝐑𝐅 (𝐒𝐞𝐫𝐯𝐞𝐫 𝐒𝐢𝐝𝐞 𝐑𝐞𝐪𝐮𝐞𝐬𝐭 𝐅𝐨𝐫𝐠𝐞𝐫𝐲)
Learn how to test for #SSRF step by step on real #bugbounty programs
Thread🧵👇
#cybersecurity #cybersecuritytips #infosec #hacking #bugbountytips #infosecurity
𝐒𝐒𝐑𝐅 (𝐒𝐞𝐫𝐯𝐞𝐫 𝐒𝐢𝐝𝐞 𝐑𝐞𝐪𝐮𝐞𝐬𝐭 𝐅𝐨𝐫𝐠𝐞𝐫𝐲)
Learn how to test for #SSRF step by step on real #bugbounty programs
Thread🧵👇
#cybersecurity #cybersecuritytips #infosec #hacking #bugbountytips #infosecurity
Before we start, this thread won't teach how SSRF works, but rather a methodology to follow while actively testing for it.
To learn about how SSRF attacks work, have a read here ➡️ portswigger.net/web-security/s…
To learn about how SSRF attacks work, have a read here ➡️ portswigger.net/web-security/s…
1️⃣ Finding an attack vector
This step simply implies using the web app THOROUGHLY and finding a place where you input a URL and the server fetches it.
Ex: profile pic from URL, URL Redirects, etc.
The best tip I can give you for this step is: CLICK EVERY SINGLE BUTTON YOU SEE
This step simply implies using the web app THOROUGHLY and finding a place where you input a URL and the server fetches it.
Ex: profile pic from URL, URL Redirects, etc.
The best tip I can give you for this step is: CLICK EVERY SINGLE BUTTON YOU SEE
Hey #OSINT, Here are top 10 weather maps that everyone should know.
#OSINT #CyberSec #cybersecurity #cybersecuritytips #bugbountytips #FactCheck #journalism #BookTwitter #Weathercloud #WeatherUpdate #journalist
A thread🧵
#OSINT #CyberSec #cybersecurity #cybersecuritytips #bugbountytips #FactCheck #journalism #BookTwitter #Weathercloud #WeatherUpdate #journalist
A thread🧵
Introduction to #XSS
Learn the basics of 𝐂𝐫𝐨𝐬𝐬-𝐒𝐢𝐭𝐞 𝐒𝐜𝐫𝐢𝐩𝐭𝐢𝐧𝐠 (𝐗𝐒𝐒)
Thread🧵👇
#bugbounty #bugbountytips #bugbountytip #cybersecurity #cybersecuritytips #infosec #infosecurity #hacking
Learn the basics of 𝐂𝐫𝐨𝐬𝐬-𝐒𝐢𝐭𝐞 𝐒𝐜𝐫𝐢𝐩𝐭𝐢𝐧𝐠 (𝐗𝐒𝐒)
Thread🧵👇
#bugbounty #bugbountytips #bugbountytip #cybersecurity #cybersecuritytips #infosec #infosecurity #hacking
Let's inspect the name first:
The 𝐒𝐜𝐫𝐢𝐩𝐭𝐢𝐧𝐠 part indicates, obviously, scripting, so we can think about what kind of scripting we know exist in Web Apps: HTML & JavaScript being the 2 most common.
Secondly, XSS is part of the INJECTION bug class (see @owasp's Top 10)
The 𝐒𝐜𝐫𝐢𝐩𝐭𝐢𝐧𝐠 part indicates, obviously, scripting, so we can think about what kind of scripting we know exist in Web Apps: HTML & JavaScript being the 2 most common.
Secondly, XSS is part of the INJECTION bug class (see @owasp's Top 10)
So, we now know XSS consists of injecting scripts in websites.
Types of XSS:
1. Reflected
2. Stored
3. DOM-based
They can also be Blind too (you don't see the reflection)
As this thread is aimed at beginners, I will focus on the first 2 as they're easier to understand at first
Types of XSS:
1. Reflected
2. Stored
3. DOM-based
They can also be Blind too (you don't see the reflection)
As this thread is aimed at beginners, I will focus on the first 2 as they're easier to understand at first
15 effective websites for pentesting research:
Thread🧵👇
#cybersecurity #cybersecuritytips #infosec #hacking #bugbountytips #infosecurity
Thread🧵👇
#cybersecurity #cybersecuritytips #infosec #hacking #bugbountytips #infosecurity
Bug Testing Methodology Series:
𝐁𝐀𝐂 (𝐁𝐫𝐨𝐤𝐞𝐧 𝐀𝐜𝐜𝐞𝐬𝐬 𝐂𝐨𝐧𝐭𝐫𝐨𝐥)
Learn how to test for Broken Access Control step by step on real #bugbounty programs.
Thread🧵👇
#cybersecurity #cybersecuritytips #infosec #hacking #bugbountytips #infosecurity
𝐁𝐀𝐂 (𝐁𝐫𝐨𝐤𝐞𝐧 𝐀𝐜𝐜𝐞𝐬𝐬 𝐂𝐨𝐧𝐭𝐫𝐨𝐥)
Learn how to test for Broken Access Control step by step on real #bugbounty programs.
Thread🧵👇
#cybersecurity #cybersecuritytips #infosec #hacking #bugbountytips #infosecurity
Before we start, this thread will not teach exactly how Broken Access Control vulnerabilities arise, but rather a testing methodology.
If you want to learn how BAC bugs work, check this out ➡️ portswigger.net/web-security/a…
If you want to learn how BAC bugs work, check this out ➡️ portswigger.net/web-security/a…
1️⃣ Know your target
In order to know what which user role can do, you have to know your target well.
If documentations are available, make full use of them, if not, use the app as much as you can from the perspective of each user role (have a different account for each role)
In order to know what which user role can do, you have to know your target well.
If documentations are available, make full use of them, if not, use the app as much as you can from the perspective of each user role (have a different account for each role)
Hey #OSINT, Twitter is one of the leading social media networks.
Here is the list of 10 Twitter analysis 📈📉 tools to optimise your search and digital investigation.
#CyberSec #cybersecurity #cybersecuritytips #bugbountytips
A THREAD 🧵
Here is the list of 10 Twitter analysis 📈📉 tools to optimise your search and digital investigation.
#CyberSec #cybersecurity #cybersecuritytips #bugbountytips
A THREAD 🧵
1. Tinfoleak - tinfoleak.com
#OSINT #CyberSec #cybersecurity #cybersecuritytips #bugbountytips #FactCheck
#OSINT #CyberSec #cybersecurity #cybersecuritytips #bugbountytips #FactCheck
2. Account Analysis - accountanalysis.app
#OSINT #CyberSec #cybersecurity #cybersecuritytips #bugbountytips #FactCheck #journalism
#OSINT #CyberSec #cybersecurity #cybersecuritytips #bugbountytips #FactCheck #journalism
📌Docker Images for Penetration Testing & Security
• docker pull kalilinux/kali-linux-docker official Kali Linux
• docker pull owasp/zap2docker-stable - official OWASP ZAP
• docker pull wpscanteam/wpscan - official WPScan
🧵👇
#Pentesting #infosec #cybersecuritytips
• docker pull kalilinux/kali-linux-docker official Kali Linux
• docker pull owasp/zap2docker-stable - official OWASP ZAP
• docker pull wpscanteam/wpscan - official WPScan
🧵👇
#Pentesting #infosec #cybersecuritytips
• docker pull metasploitframework/metasploit-framework - Official Metasploit
• docker pull citizenstig/dvwa - Damn Vulnerable Web Application (DVWA)
• docker pull wpscanteam/vulnerablewordpress - Vulnerable WordPress Installation
• docker pull citizenstig/dvwa - Damn Vulnerable Web Application (DVWA)
• docker pull wpscanteam/vulnerablewordpress - Vulnerable WordPress Installation
• docker pull hmlio/vaas-cve-2014-6271 - Vulnerability as a service: Shellshock
• docker pull hmlio/vaas-cve-2014-0160 - Vulnerability as a service: Heartbleed
• docker pull opendns/security-ninjas - Security Ninjas
• docker pull hmlio/vaas-cve-2014-0160 - Vulnerability as a service: Heartbleed
• docker pull opendns/security-ninjas - Security Ninjas