Discover and read the best of Twitter Threads about #cybersecurity
Most recents (24)
Cybersecurity is a rapidly growing field, and the demand for qualified professionals is high. A cybersecurity certificate can help you gain the skills and knowledge you need to start a career in this in-demand field.
Here are some of the benefits of getting a cybersecurity certificate:
1. Increased job opportunities
2. Higher salaries
3. More job security
4. Personal satisfaction
5. Addition To Your Knowledge
1. Increased job opportunities
2. Higher salaries
3. More job security
4. Personal satisfaction
5. Addition To Your Knowledge
AI and Safety:
@owasp has released a list of the top 10 most critical vulnerabilities found in artificial intelligence applications based on large language models (LLMs).
These vulnerabilities include prompt injections, data leakage, and unauthorized code execution.
A 🧵
#AI
@owasp has released a list of the top 10 most critical vulnerabilities found in artificial intelligence applications based on large language models (LLMs).
These vulnerabilities include prompt injections, data leakage, and unauthorized code execution.
A 🧵
#AI

1. Prompt injections:
This involves bypassing filters or manipulating the LLM using carefully crafted prompts that make the model ignore previous instructions or perform unintended actions.
This involves bypassing filters or manipulating the LLM using carefully crafted prompts that make the model ignore previous instructions or perform unintended actions.
2. Data Leakage:
Data leakage occurs when an LLM accidentally reveals sensitive information through its responses. #cybersecurity
Data leakage occurs when an LLM accidentally reveals sensitive information through its responses. #cybersecurity
Network Security is hard!
I’ve pulled together a list of essentials for Beginners in #CyberSecurity.
Give me 3 minutes and I’ll break things down for you 👇
I’ve pulled together a list of essentials for Beginners in #CyberSecurity.
Give me 3 minutes and I’ll break things down for you 👇
1/9 🔒 Network security is a complex field with numerous aspects to consider. If you're starting your journey in cybersecurity, here are key areas to explore further. Let's dive deeper into network security! #NetworkSecurity #InfoSec
2/9 🌐 Network segmentation is crucial for protecting sensitive data. Learn about strategies like virtual LANs (VLANs) and network zoning. Understand how segregating network resources and implementing access controls help mitigate the impact of potential breaches.
1/🧵
So, I'm quietly asked my opinion of @mikko's somewhat ... grandiose claims for artificial general intelligence (AGI) going forward. I invite my questioner to jump in with their own thoughts, but here's mine as cybersecurity's eldest #critic:
So, I'm quietly asked my opinion of @mikko's somewhat ... grandiose claims for artificial general intelligence (AGI) going forward. I invite my questioner to jump in with their own thoughts, but here's mine as cybersecurity's eldest #critic:
2/🧵
My short answer is "I'm okay with anyone making bold claims like this." There's simply no #fearmongering here. @mikko states the obvious and paints a future.
My longer answer centers on the fact @mikko wields a strong character in our industry...
My short answer is "I'm okay with anyone making bold claims like this." There's simply no #fearmongering here. @mikko states the obvious and paints a future.
My longer answer centers on the fact @mikko wields a strong character in our industry...
3/🧵/🧵
...and it's the type of character I would wish on everyone.
I admit @mikko has a style few can muster. But his character? Every one of us can muster that if we wish!
Imagine a world where we all invite software makers to see their work from...
twitter.com/i/events/93951…
...and it's the type of character I would wish on everyone.
I admit @mikko has a style few can muster. But his character? Every one of us can muster that if we wish!
Imagine a world where we all invite software makers to see their work from...
twitter.com/i/events/93951…
#Israeli company #NSOgroup is still selling #PEGASUS,
its CEO Yaron Shohat told Swiss TV @RSInews while @Europarl_EN is ready to vote on #PEGA report
“Tools that allows our customers -government agencies - to gather #intelligence to fight terror and crime”
@EP_PegaInquiry
/1
its CEO Yaron Shohat told Swiss TV @RSInews while @Europarl_EN is ready to vote on #PEGA report
“Tools that allows our customers -government agencies - to gather #intelligence to fight terror and crime”
@EP_PegaInquiry
/1
In his first TV interview, CEO of blacklisted #NSOgroup Yaron Shohat says he’s committed to do “anything possible” to make sure #PEGASUS and other tools are in proper hands and used correctly”
But not 100% sure about misuse
SwissTV @RSInews
@EP_PegaInquiry
@dreynders
/2
But not 100% sure about misuse
SwissTV @RSInews
@EP_PegaInquiry
@dreynders
/2
1/7 🚨 #DataBreach Alert 🚨: Personal data of COVID-19 vaccine recipients in India has reportedly been leaked online via a bot on #Telegram. #CyberSecurity #PrivacyMatters 

2/7 📲 The bot allowed users to input a mobile number and it would respond with personal info connected to the number, including name, gender, DOB, and vaccination center. #InfoSec #DataLeak 

3/7 📂 The leaked data also includes personal info on several politicians and journalists. This is a serious breach of privacy with significant implications. #DataProtection #PrivacyRights
Procuramos vagas PCD 📢
A comunidade PCD Tech no twitter tem o objetivo de auxiliar pessoas com deficiência a encontrarem vagas de emprego. Além disso também tem o objetivo de auxiliar com dúvidas de processos seletivos, currículos e geral.
+
A comunidade PCD Tech no twitter tem o objetivo de auxiliar pessoas com deficiência a encontrarem vagas de emprego. Além disso também tem o objetivo de auxiliar com dúvidas de processos seletivos, currículos e geral.
+
Essa é uma ação 100% sem fins lucrativos. Já tivemos alguns feedbacks de pessoas que foram realocadas através das vagas divulgadas na comunidade. E eu fico muito feliz de saber que essa minha pequena iniciativa tem ajudado algumas pessoas.
+
+
Temos hoje pessoas na comunidade procurando por vagas, esses são os perfis:
- QA Engineer/QA Analyst
- Desenvolvedor Front-end Jr
- Desenvolvedor WordPress Jr
- Cyber Security Pleno. Área: blue team, gestão de vulnerabilidades, complice, soc, conscientização em seg.
+
- QA Engineer/QA Analyst
- Desenvolvedor Front-end Jr
- Desenvolvedor WordPress Jr
- Cyber Security Pleno. Área: blue team, gestão de vulnerabilidades, complice, soc, conscientização em seg.
+
நாம் இணையத்தில் பகிரும் சாதாரணப் புகைப்படங்களை #AI உதவியுடன் நிர்வாணப் புகைப்படங்களாக மாற்றி செக்ஸ்டார்சன் குழுக்கள் மிரட்டிப் பணம் பறிப்பதாக #FBI எச்சரிக்கை விடுத்துள்ளது, திடீரென நமக்கு வீடியோ கால் செய்து ஒரு வினாடி நமது முகத்தை மட்டும் ரெகார்ட் செய்துகொண்டு 

அதைப் பார்ன் வீடியோக்களில் செருகி பணம் பறிப்பது தான் நடைமுறை. ஆனால் தற்போது நமது இணையப் புகைப்படங்களை Deep nude AI செயலியில் அப்லோட் செய்தால், நமது முக வடிவம், கண் அளவு, தோல் நிறத்திற்கு ஏற்ப மிகக் கச்சிதமான ஒரு நிர்வாண உடலைத் தயாரித்து, பல்வேறு கோணங்களில்
நம் முகத்தை அதனுடன் இணைத்து விடும். அலுவலக ஓய்வறையில் தான் எடுத்த சாதாரண புகைப்படத்தை, நிர்வாணமாக மாற்றி மோசடியாளர்கள் பணம் கேட்டு மிரட்டியிருக்கிறார்கள். பெண் தர மறுக்க, புகைப்படத்தை நண்பர்கள், குடும்பம், அலுவலகத் தலைமை எல்லோருக்கும் அனுப்பி விட, பெரும் மன உளைச்சலுடன்
🌱🚀 My Personal Journey When I was a Newbie in Cybersecurity🌟💼
(Thread)
This is inspired by messages I have received and, I thought to share this as a motivation to someone out there reading this.
(Thread)
This is inspired by messages I have received and, I thought to share this as a motivation to someone out there reading this.
I want to share a personal experience that taught me the power of embracing a growth mindset in this ever-evolving field. 🌱💪
When I first started my journey in cybersecurity, I often felt overwhelmed by the vast knowledge and skills required. Imposter syndrome crept in, making me doubt my abilities. But then, I discovered the magic of the growth mindset. 🌟🧠
1/15 🧵💡 Decentralized storage & compute could truly supercharge the #InternetOfThings (#IoT). But how? Let's unpack this crucial evolution for our hyper-connected world. 🌐👇
2/15 📚 First, it's crucial to understand the concepts. #DecentralizedStorage refers to data storage spread across multiple devices or locations, rather than a central server. #DecentralizedCompute refers to computations performed on these distributed devices.💻🌍
3/15 📈 IoT devices generate an enormous amount of data daily. Centralized servers currently deal with this load, but as more and more devices connect, scalability becomes a challenge. Decentralization offers a solution. #EdgeComputing #Scalability
Hey guys,
I see that a lot of people are getting into the cybersecurity industry and are seriously looking at different career paths, learning the basics, getting their hands dirty with hands on experience, joining communities.
This is a thread. Kindly follow along.
I see that a lot of people are getting into the cybersecurity industry and are seriously looking at different career paths, learning the basics, getting their hands dirty with hands on experience, joining communities.
This is a thread. Kindly follow along.
I have also noticed that here on twitter a few CyberNewbies do not actually take their personal branding as serious as they should in line with their learning skills.
So, this is for us to learn how important Personal Branding is.
So, this is for us to learn how important Personal Branding is.
1/14 - 🚨WHAT HAPPENS IF THE US DEFAULTS⁉️
A default on the US debt ceiling would have profound implications. This historic event could trigger economic shocks and disrupt global financial stability. Let’s talk about it!#DebtCeilingDefault #GlobalFinancialStability
A default on the US debt ceiling would have profound implications. This historic event could trigger economic shocks and disrupt global financial stability. Let’s talk about it!#DebtCeilingDefault #GlobalFinancialStability

2/14
History teaches us that financial crises can affect military readiness and operations. A default could hamper US strategic alliances, similar to the effects of the Great Depression. #HistoricalLessons #MilitaryReadiness
History teaches us that financial crises can affect military readiness and operations. A default could hamper US strategic alliances, similar to the effects of the Great Depression. #HistoricalLessons #MilitaryReadiness

3/14
A default could also jeopardize trust in US Treasury bonds, a cornerstone of the global economy. The result? Skyrocketing interest rates and a weakened dollar. #TrustInBonds #DebtCeiling
A default could also jeopardize trust in US Treasury bonds, a cornerstone of the global economy. The result? Skyrocketing interest rates and a weakened dollar. #TrustInBonds #DebtCeiling

Dark Web Data Leak Exposes RaidForums Members
Nearly half a million members of a notorious cybercrime forum have had their details publicly exposed after a key database was published on another hacking site.
#DarkWeb #RaidForums #Cybercrime
infosecurity-magazine.com/news/data-leak…
Nearly half a million members of a notorious cybercrime forum have had their details publicly exposed after a key database was published on another hacking site.
#DarkWeb #RaidForums #Cybercrime
infosecurity-magazine.com/news/data-leak…
"#Cybersecurity researchers at VX-Underground confirmed the news that over 478,000 users of RaidForums had their data leaked on up-and-coming forum Exposed."
"A screenshot shared by Emsisoft threat analyst, Brett Callow, shows the leak was posted by an Exposed admin known as "Impotent."
1/14 🚀 We've put together an in-depth series on APIs, covering everything from fundamentals to AI APIs. Join us on this journey! #APIs #WebDevelopment #Coding
2/14 📚 Starting with API fundamentals, we dive into the basics that every developer should know. Get the solid foundation you need! vegibit.com/%f0%9f%93%9a-a… #APIFundamentals #BackToBasics #LearnToCode
3/14 🌐 HTTP and RESTful APIs are key to modern web services. Learn how these technologies power the web. vegibit.com/%f0%9f%8c%90-h… #RESTfulAPIs #HTTP #WebServices
सायबर सुरक्षा काय आहे? 🔐🪪
#cybersecurity #म #Aiमराठी #मराठी
Cyber Security दोन शब्दांपासून बनली आहे. 1. Cyber 2. Security
🛡️1 CYBER :
जे INTERNET, DATA, INFORMATION, TECHNOLOGY, COMPUTER, NETWORK, APP, SYSTEAM शी संबधीत आहेत त्यांना CYBER असे म्हणतात.
#cybersecurity #म #Aiमराठी #मराठी
Cyber Security दोन शब्दांपासून बनली आहे. 1. Cyber 2. Security
🛡️1 CYBER :
जे INTERNET, DATA, INFORMATION, TECHNOLOGY, COMPUTER, NETWORK, APP, SYSTEAM शी संबधीत आहेत त्यांना CYBER असे म्हणतात.

🛡️2 SECURITY :
या मध्ये SYSTEM SECURITY, NETWORK SECURITY आणि INFORMATION SECURITY चा समावेश होतो.
या मध्ये SYSTEM SECURITY, NETWORK SECURITY आणि INFORMATION SECURITY चा समावेश होतो.
📢 सध्याचे युग हे Technology चे असल्यामुळे सवत्र Internet, Mobile, Computer चा उपयोग मोठ्या प्रमाणात केला जात आहे. सध्याची सर्व काम ही इंटरनेटच्या माध्यमातूनच केली जातात. उदा. पैशांची लेन-देन, विविध कंपन्यांची कामे, सोशल मिडीया, बँक इ. अशा अनेक विविध प्रकारच्या गोष्टींची किंवा
I'm excited to share these 10 FREE cybersecurity
courses from ISC(2) with you!
I've learned a lot from them and I think you will too.
Follow the thread to get started 👇👇
#cybersecurity #security #informationsecurity #freecourses #learnmore #Cloud
courses from ISC(2) with you!
I've learned a lot from them and I think you will too.
Follow the thread to get started 👇👇
#cybersecurity #security #informationsecurity #freecourses #learnmore #Cloud

.@OpenAI's #ChatGPT reached 100M users in two months. It spurred on @Google and @Microsoft to add chatbots to their business models. But what are the consequences of #AI and your personal data? Read this thread to find out more. 🧵⬇️ (1/7) 

We're in the middle of one of the largest tech gold rushes since the early 90s. But the resource these #BigTech companies are digging for is your private data to train their chatbots. Find out how. ⬇️ (2/7)
If you've written a blog post, submitted an online review, posted on sites like @Reddit and @StackOverflow, you've helped teach Big Tech's chatbots how to be human. 🧌☠️ (3/7)
In today's interconnected world, spotting network anomalies early is critical for effective threat detection and response.
NDR is a vital tool for safeguarding your organization's digital assets.
Here's why you should consider implementing NDR in your cybersecurity strategy:
NDR is a vital tool for safeguarding your organization's digital assets.
Here's why you should consider implementing NDR in your cybersecurity strategy:
Proactive Security:
NDR enables cybersecurity teams to monitor and analyze unexpected and suspicious activities in real-time.
This allows for proactive security measures, addressing network vulnerabilities and preventing attacks and breaches!
NDR enables cybersecurity teams to monitor and analyze unexpected and suspicious activities in real-time.
This allows for proactive security measures, addressing network vulnerabilities and preventing attacks and breaches!
Monitoring Internal Threats:
Internal threats pose significant risks to an organization's cybersecurity.
NDR helps detect potential internal threats and malicious users at the network level.
Internal threats pose significant risks to an organization's cybersecurity.
NDR helps detect potential internal threats and malicious users at the network level.
A class 12 passout, former security officer and self taught cybergeek from Hyderabad, Shrinivas Rao Dadi, masterminded a nationwide cyberfraud with a turnover of Rs 3 crore a day. The money was being converted into #cryptocurrency and sent to #China. So, how did he do it? 

There was a hierarchy to how the scamsters operated. Some of them called up citizens, posing as policemen and flashing fake ID cards, over WhatsApp and Skype. Women were targetted the most. In Delhi, one of the scamsters made a video call to a woman, dressed in a khaki uniform.
The victims were told that a parcel he/she had sent by courier was found containing drugs. The terrified victims were deceived into downloading apps, such as Anydesk, that provided the scamster with remote access to his phone screen.
Complete Bug Bounty tool List :)
dnscan github.com/rbsec/dnscan
Knockpy github.com/guelfoweb/knock
Sublist3r github.com/aboul3la/Subli…
massdns github.com/blechschmidt/m…
nmap nmap.org
masscan github.com/robertdavidgra…
#bugbounty #bugbountytips #cybersecurity #hacking
dnscan github.com/rbsec/dnscan
Knockpy github.com/guelfoweb/knock
Sublist3r github.com/aboul3la/Subli…
massdns github.com/blechschmidt/m…
nmap nmap.org
masscan github.com/robertdavidgra…
#bugbounty #bugbountytips #cybersecurity #hacking
EyeWitness github.com/ChrisTruncer/E…
DirBuster sourceforge.net/projects/dirbu…
dirsearch github.com/maurosoria/dir…
Gitrob github.com/michenriksen/g…
git-secrets github.com/awslabs/git-se…
sandcastle github.com/yasinS/sandcas…
bucket_finder digi.ninja/projects/bucke…
DirBuster sourceforge.net/projects/dirbu…
dirsearch github.com/maurosoria/dir…
Gitrob github.com/michenriksen/g…
git-secrets github.com/awslabs/git-se…
sandcastle github.com/yasinS/sandcas…
bucket_finder digi.ninja/projects/bucke…
GoogD0rker github.com/ZephrFish/Goog…
Wayback Machine web.archive.org
waybackurls gist.github.com/mhmdiaa/adf6bf…
Sn1per github.com/1N3/Sn1per/
XRay github.com/evilsocket/xray
wfuzz github.com/xmendez/wfuzz/
patator github.com/lanjelot/patat…
datasploit github.com/DataSploit/dat…
Wayback Machine web.archive.org
waybackurls gist.github.com/mhmdiaa/adf6bf…
Sn1per github.com/1N3/Sn1per/
XRay github.com/evilsocket/xray
wfuzz github.com/xmendez/wfuzz/
patator github.com/lanjelot/patat…
datasploit github.com/DataSploit/dat…
[1/13] As we're witnessing recurring layoffs, it's crucial to stay prepared. This thread is based on my experience of interviewing with Western companies in early 2022. I'll share insights & resources that proved invaluable. Hopefully, it aids your #InterviewPreparation journey.
[2/13] Struggling with HTTPS and digital certificates? This comprehensive guide will clear your doubts - cryptobook.nakov.com. A strong foundation in #CyberSecurity is essential in today's digital landscape.
[3/13] Mobile System Design was a challenging topic due to scarce resources. Until I found this repository - github.com/weeeBox/mobile…. It's a goldmine of information for any aspiring #MobileSystemDesign enthusiast.
DATA: Americans Fear Their Own Government Spying on Them Almost As Much as Foreign Adversaries 🕵🏻♂️ 👁️ #RESTRICTAct #PatriotAct #Surveillance #Cybersecurity #1A thenationalpulse.com/2023/04/26/dat…
1/ 🚨 A recent surge in phishing scams via Google search ads has led to users losing approximately $4 million.
ScamSniffer has investigated multiple cases where users clicked on malicious ads and were directed to fraudulent websites.
#PhishingScams #GoogleAds
ScamSniffer has investigated multiple cases where users clicked on malicious ads and were directed to fraudulent websites.
#PhishingScams #GoogleAds
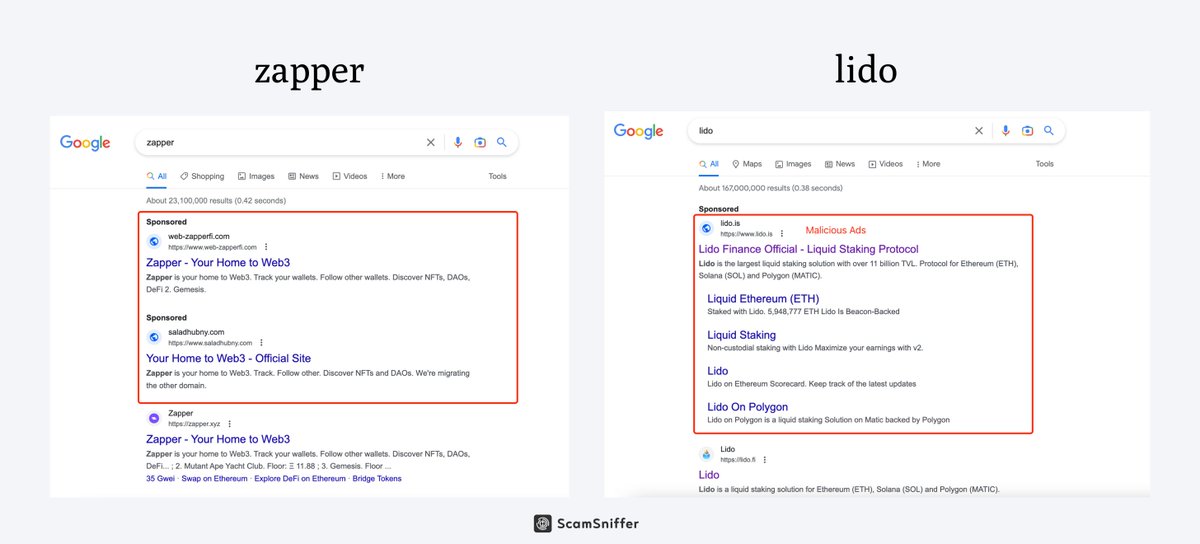
2/ 🕵️♂️ Investigation into the keywords used by victims has uncovered numerous malicious ads at the forefront of search results.
Most users, unaware of the deceptive nature of search ads, click on the first available option, leading them to malicious websites.
#Cybersecurity
Most users, unaware of the deceptive nature of search ads, click on the first available option, leading them to malicious websites.
#Cybersecurity

3/ 🎯 Some of the malicious ads and websites target brands such as @zapper_fi , @LidoFinance , @StargateFinance and @DefiLlama.
These advertisers have been identified as placing these malicious ads:
ТОВАРИСТВО З ОБМЕЖЕНОЮ ВІДПОВІДАЛЬНІСТЮ «РОМУС-ПОЛІГРАФ»
TRACY ANN MCLEISH.

These advertisers have been identified as placing these malicious ads:
ТОВАРИСТВО З ОБМЕЖЕНОЮ ВІДПОВІДАЛЬНІСТЮ «РОМУС-ПОЛІГРАФ»
TRACY ANN MCLEISH.


If you’ve been interested in pivoting into tech, learn how tech is used everywhere - for FREE 🥳🎉👏 From Cyber to Data Science, Cloud Security, Networking, Engineering and more! 🧵
Cisco Networking Academy is hosting a series of FREE trainings and events to showcase how data, cyber and #tech is used to address climate change.
Yes, I know - who thinks about cyber, data and cloud in climate change??? Well these trainings and events will enlighten you! 🚀



Yes, I know - who thinks about cyber, data and cloud in climate change??? Well these trainings and events will enlighten you! 🚀




Join Cisco and tech leaders for International Girls in ICT Day! 👩🏽💻👩🏻💻👩🏼💻

