Discover and read the best of Twitter Threads about #BugBountyTips
Most recents (24)
Some of the major vulnerabilities and related POC’s:
➡SQLi
➡XSS
➡SSRF
➡XXE
➡Path Traversal
➡Open Redirection
➡Account Takeover
➡Remote code execution
➡IDOR
➡CSRF
#hacking #bugbounty #bugbountytips
Are Found Below🧵(1/n)👇
➡SQLi
➡XSS
➡SSRF
➡XXE
➡Path Traversal
➡Open Redirection
➡Account Takeover
➡Remote code execution
➡IDOR
➡CSRF
#hacking #bugbounty #bugbountytips
Are Found Below🧵(1/n)👇
SQLi POC’s:
#hacking #bugbounty #bugbountytips
1. medium.com/@mahitman1/hac…
2. krevetk0.medium.com/burpsuit-sqlma…
#hacking #bugbounty #bugbountytips
1. medium.com/@mahitman1/hac…
2. krevetk0.medium.com/burpsuit-sqlma…
XSS POC’s:
#hacking #bugbounty #bugbountytips
🔗1.
medium.com/@jonathanbouma…
🔗2.
medium.com/@jonathanbouma…
🔗3.
medium.com/@jonathanbouma…
#hacking #bugbounty #bugbountytips
🔗1.
medium.com/@jonathanbouma…
🔗2.
medium.com/@jonathanbouma…
🔗3.
medium.com/@jonathanbouma…
Nuclei + AI = Money 🤑
Here's how to use AI and nuclei to make money while you sleep 👇🧵
#bugbountytips #bugbounty
Here's how to use AI and nuclei to make money while you sleep 👇🧵
#bugbountytips #bugbounty
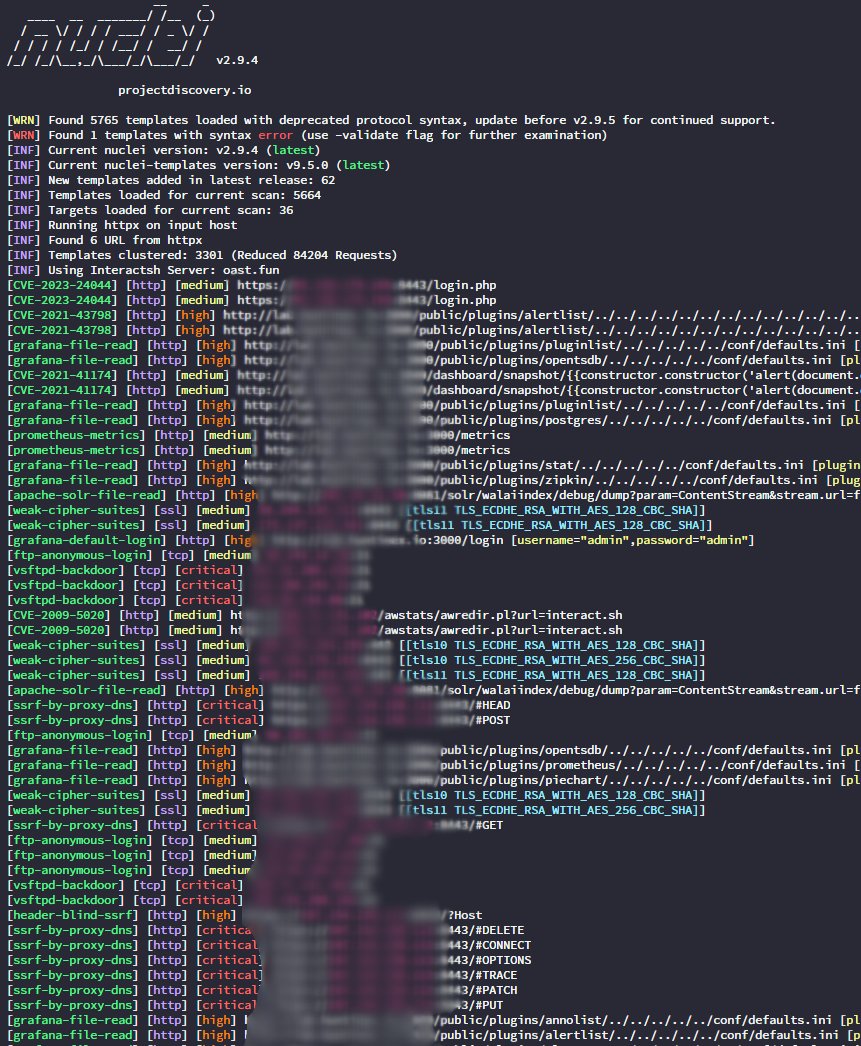
1. Run nuclei
First of all, if you can use a server or any kind of droplet (for Axiom, Hakq or Nuclei Cloud) that would be great!
Use them and run nuclei on a large number of subdomains.
See the final command in the next tweet 👇
First of all, if you can use a server or any kind of droplet (for Axiom, Hakq or Nuclei Cloud) that would be great!
Use them and run nuclei on a large number of subdomains.
See the final command in the next tweet 👇
2. Nuclei config
- max number of templates to be executed in parallel (-c)
- number of hosts to be analyzed in parallel per template (-bs)
- rate limit number (-rl)
Final command:
"nuclei -o output.txt -bs <> -c <> -rl <>"
Learn more about @pdnuclei 👇
nuclei.projectdiscovery.io/nuclei/get-sta…
- max number of templates to be executed in parallel (-c)
- number of hosts to be analyzed in parallel per template (-bs)
- rate limit number (-rl)
Final command:
"nuclei -o output.txt -bs <> -c <> -rl <>"
Learn more about @pdnuclei 👇
nuclei.projectdiscovery.io/nuclei/get-sta…
Complete Bug Bounty tool List :)
dnscan github.com/rbsec/dnscan
Knockpy github.com/guelfoweb/knock
Sublist3r github.com/aboul3la/Subli…
massdns github.com/blechschmidt/m…
nmap nmap.org
masscan github.com/robertdavidgra…
#bugbounty #bugbountytips #cybersecurity #hacking
dnscan github.com/rbsec/dnscan
Knockpy github.com/guelfoweb/knock
Sublist3r github.com/aboul3la/Subli…
massdns github.com/blechschmidt/m…
nmap nmap.org
masscan github.com/robertdavidgra…
#bugbounty #bugbountytips #cybersecurity #hacking
EyeWitness github.com/ChrisTruncer/E…
DirBuster sourceforge.net/projects/dirbu…
dirsearch github.com/maurosoria/dir…
Gitrob github.com/michenriksen/g…
git-secrets github.com/awslabs/git-se…
sandcastle github.com/yasinS/sandcas…
bucket_finder digi.ninja/projects/bucke…
DirBuster sourceforge.net/projects/dirbu…
dirsearch github.com/maurosoria/dir…
Gitrob github.com/michenriksen/g…
git-secrets github.com/awslabs/git-se…
sandcastle github.com/yasinS/sandcas…
bucket_finder digi.ninja/projects/bucke…
GoogD0rker github.com/ZephrFish/Goog…
Wayback Machine web.archive.org
waybackurls gist.github.com/mhmdiaa/adf6bf…
Sn1per github.com/1N3/Sn1per/
XRay github.com/evilsocket/xray
wfuzz github.com/xmendez/wfuzz/
patator github.com/lanjelot/patat…
datasploit github.com/DataSploit/dat…
Wayback Machine web.archive.org
waybackurls gist.github.com/mhmdiaa/adf6bf…
Sn1per github.com/1N3/Sn1per/
XRay github.com/evilsocket/xray
wfuzz github.com/xmendez/wfuzz/
patator github.com/lanjelot/patat…
datasploit github.com/DataSploit/dat…
🧵NEW THREAD🧵
Here is how I was able to takeover the whole company's AWS infrastructure under 10 min after a new asset launch at @Hacker0x01 private program

Here is how I was able to takeover the whole company's AWS infrastructure under 10 min after a new asset launch at @Hacker0x01 private program
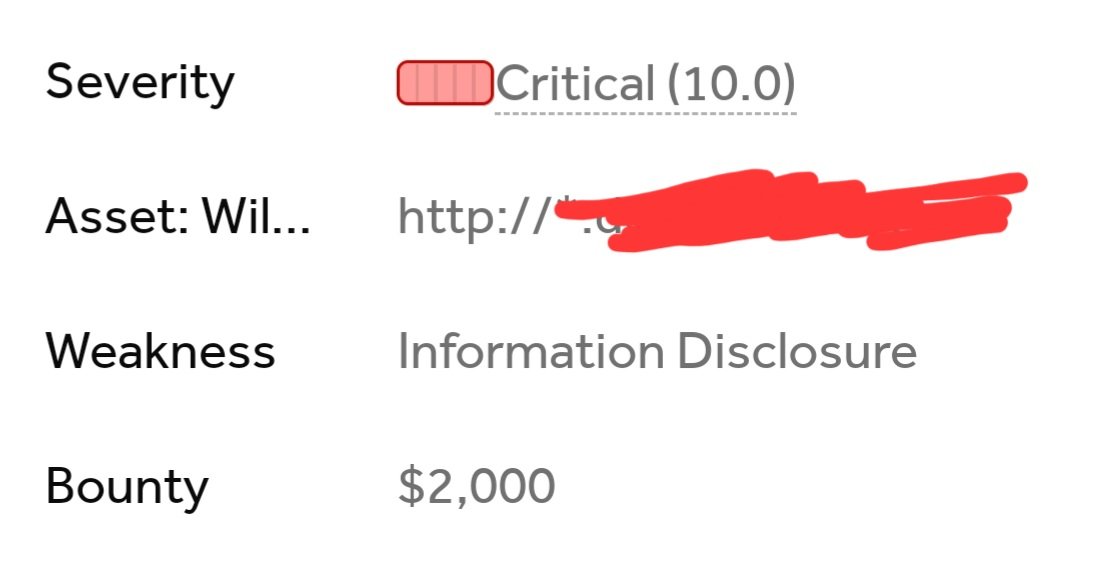
1. I was invited in the morning to a private program at H1 and the program updated the scope in the evening, So I decided to take a look to see if there is something to hack
2. I visited the main website in scope, to my surprise and thanks to @trufflesec Chrome extension Trufflehog which could be found here chrome.google.com/webstore/detai…
🧵NEW Thread🧵
Here is how I found the easiest SQLi and possible RCE in less than 30 min of recon and dorking
1. I was invited to a private program at @Hacker0x01 and the first thing I usually do is to look at the scope and see if it is a wildcard domain or just a small scope.

Here is how I found the easiest SQLi and possible RCE in less than 30 min of recon and dorking
1. I was invited to a private program at @Hacker0x01 and the first thing I usually do is to look at the scope and see if it is a wildcard domain or just a small scope.


2. Found that the program accepts all vulnerabilities related to their assets and of course third party assets are OOS
3. I used @leak_ix search engine at leakix.net and used this dork [+target_name ++plugin:"GitConfigHttpPlugin"]
Note : this is used to search for already scanned websites that have /.git exposed
Note : this is used to search for already scanned websites that have /.git exposed
A lesser-known yet effective way of #bugbounty hunting is called "hacktivity" hunting. It involves bypassing fixes on disclosed reports found on @Hacker0x01's hacktivity page. This approach helped me score a $5k bounty! Here's how it works.👇
#InfoSec #CyberSecurity
#InfoSec #CyberSecurity
With hacktivity hunting, the hard part - finding interesting behavior or insecure features - is already done for you. Your main role is to find a bypass.
For example, I found a bypass for a report on hackerone.com/reports/949643
#BugBountyTips
For example, I found a bypass for a report on hackerone.com/reports/949643
#BugBountyTips
The original report tried to restrict access to /admin by restricting the path in Nginx. However, I bypassed it using simple encoding - /%2561dmin. Endpoints required authentication, but I bypassed this by adding ".json" at the end.
#BugBounty #Hacking
#BugBounty #Hacking
I've recently become obsessed with getting better at pen testing Android apps. So, I would like to start a thread. Post useful tools, #bugbountytips , and tricks you know here! I'll start:
1] You can recompile an APK using "APK-MITM" tool which removes certificate pinning...
1] You can recompile an APK using "APK-MITM" tool which removes certificate pinning...
This allows you to install the APK to an unrooted device and install a user CA (EG: Burp, MITM proxy, etc.) to intercept the app traffic. Its life changing. Formerly I had used Frida with Nox Emulator but if your app requires physical things (EG: bluetooth), Nox may not work. ..
2] The "apkleaks" program makes a great attempt at farming out secrets and URLs from APKs, but in my experience it misses a bunch. Does anyone know of anything better here that attempts to find URLs, secrets, etc. from the APK to save time?
Google Dorks - Cloud Storage #2:
site:dev.azure.com "example[.]com"
site:onedrive.live.com "example[.]com"
site:digitaloceanspaces.com "example[.]com"
Find sensitive data and company assets
#recon #bugbountytips #infosec #seo
site:dev.azure.com "example[.]com"
site:onedrive.live.com "example[.]com"
site:digitaloceanspaces.com "example[.]com"
Find sensitive data and company assets
#recon #bugbountytips #infosec #seo

Combine:
site:dev.azure.com | site:onedrive.live.com | site:digitaloceanspaces.com "example[.]com"
Add something to narrow the results: "confidential" "privileged" "apikey"
site:dev.azure.com | site:onedrive.live.com | site:digitaloceanspaces.com "example[.]com"
Add something to narrow the results: "confidential" "privileged" "apikey"
More Cloud Dorks: infosecwriteups.com/uncover-hidden…
Google Dorks - File Storage:
site:dropbox.com/s "example[.]com"
site:box.com/s "example[.]com"
site:docs.google.com inurl:"/d/" "example[.]com"
Find sensitive data and company accounts
#recon #bugbountytips #infosec #seo
site:dropbox.com/s "example[.]com"
site:box.com/s "example[.]com"
site:docs.google.com inurl:"/d/" "example[.]com"
Find sensitive data and company accounts
#recon #bugbountytips #infosec #seo

Combine:
site:dropbox.com/s | site:box.com/s | site:docs.google.com "example[.]com"
Add something to narrow the results: "confidential" "privileged" "not for public release"
site:dropbox.com/s | site:box.com/s | site:docs.google.com "example[.]com"
Add something to narrow the results: "confidential" "privileged" "not for public release"
More Google Dorks: infosecwriteups.com/uncover-hidden…
Vulnexp 90 | Day69
CRLF Areas to Inspect
➡️Areas to Inspect:
#bugbountytips #bugbountytip
Thread 🧵 : 👇
CRLF Areas to Inspect
➡️Areas to Inspect:
#bugbountytips #bugbountytip
Thread 🧵 : 👇

Areas to Inspect:
• HTTP Headers: CRLF Injection attacks can occur in HTTP headers, such as the "User-Agent" or "Referer" headers. Attackers can insert CRLF sequences into these headers to inject additional headers or modify the response.
• HTTP Headers: CRLF Injection attacks can occur in HTTP headers, such as the "User-Agent" or "Referer" headers. Attackers can insert CRLF sequences into these headers to inject additional headers or modify the response.
• Cookies: Cookies are often used to store user session information, and they can also be vulnerable to CRLF Injection attacks. An attacker can insert CRLF sequences into a cookie value to modify the response or inject additional headers.
Vulnexp 90 | Day68
CRLF Injection
CRLF is a type of web-based attack that allows an attacker to inject malicious code or unwanted data into the HTTP response of a web application.
➡️Vulnerabilities Occur:
#bugbountytips #bugbountytip
Thread 🧵 : 👇
CRLF Injection
CRLF is a type of web-based attack that allows an attacker to inject malicious code or unwanted data into the HTTP response of a web application.
➡️Vulnerabilities Occur:
#bugbountytips #bugbountytip
Thread 🧵 : 👇

Vulnerabilities Occur:
• CRLF can occur when a web application fails to properly sanitize user-supplied input or validate input parameters. Specifically, they can occur in any part of the HTTP response that accepts user input, including HTTP headers, cookies, and form input.
• CRLF can occur when a web application fails to properly sanitize user-supplied input or validate input parameters. Specifically, they can occur in any part of the HTTP response that accepts user input, including HTTP headers, cookies, and form input.
• For example, an attacker can insert a CRLF sequence into an HTTP header to inject additional headers or modify the response. Alternatively, they may use CRLF to inject malicious code, such as JavaScript, into the response body, leading to cross-site scripting (XSS) attacks.
Few months ago @osiryszzz and me discovered an interesting case of SQL injection on the @SynackRedTeam target which was black box testing.
During recon we noticed that there was an unrestricted file upload mechanism available to the any user. #bugbounty #bugbountytips /1
During recon we noticed that there was an unrestricted file upload mechanism available to the any user. #bugbounty #bugbountytips /1
We noticed that the target was only processing the ZIP files but where the content unzipped wasn't clear which was preventing potential RCE or file overwrite via ZIP bombing. /2
However it appears that each file entry inside the ZIP file was added to the database after unpacking, which we wanted to see if it's possible to achieve SQL injection, by simply making file name with SQL injection payload. /3
HTTP Parameter Pollution @SecGPT has seen in its training. 

1. ATO via password reset
The attacker manipulates the HTTP parameters of the password reset page to change the email address associated with the account; then use the password reset link => ATO.
The attacker manipulates the HTTP parameters of the password reset page to change the email address associated with the account; then use the password reset link => ATO.
2. Price manipulation in e-commerce platforms
The attacker manipulates the HTTP parameters of an e-commerce website to change the price of a product. The attacker can then purchase the product at a lower price than intended.
The attacker manipulates the HTTP parameters of an e-commerce website to change the price of a product. The attacker can then purchase the product at a lower price than intended.
🚀🔒Exciting news! SecGPT is now LIVE!
Trained on thousands of cybersecurity reports, SecGPT revolutionizes cybersecurity with AI-driven insights.👇
Trained on thousands of cybersecurity reports, SecGPT revolutionizes cybersecurity with AI-driven insights.👇

1. Trained on an extensive collection of cybersecurity reports, @SecGPT provides you with a deeper understanding of vulnerabilities, exploitation techniques, and emerging trends in cybersecurity.
Its knowledge increases as more reports and writeups are published.
Its knowledge increases as more reports and writeups are published.
2. Explore SecGPT's capabilities and see how it can assist you in enhancing your cybersecurity expertise.
Try it out for free at alterai.me
#ai #cybersecurity #infosec #pentesting #ethicalhacking #bugbounty #bugbountytips #secgpt
Try it out for free at alterai.me
#ai #cybersecurity #infosec #pentesting #ethicalhacking #bugbounty #bugbountytips #secgpt
In the world of bug bounty hunting, Insecure Direct Object References (IDORs) can be a goldmine. In this thread, we'll share advanced tips to sharpen your IDOR detection skills. Let's dive in! 🌊🔍
#bugbountytip #bugbountytips #CyberSecurityAwareness
1/n
#bugbountytip #bugbountytips #CyberSecurityAwareness
1/n
Always begin with a thorough understanding of the application you're testing. Identify all possible user roles and their access rights. This knowledge is crucial for accurately identifying IDOR vulnerabilities. 🧠📝
Pay attention to API endpoints that handle user-specific data. Keep an eye out for patterns in URL parameters or request payloads. Examine how the application validates user input and authorization checks for these sensitive resources. 📡🔬
#bugbountytips for testing Business Logic errors, a thread:
1. You need to have a good understanding of how the application is supposed to function. This requires reviewing the app's docs, reading about the business model, and testing the app to see how it behaves normally.
1. You need to have a good understanding of how the application is supposed to function. This requires reviewing the app's docs, reading about the business model, and testing the app to see how it behaves normally.
2. Identify critical business processes: Once you have a good understanding of the logic, identify the critical processes that the application performs. These are the processes that are essential to the application's functionality and are likely to be the target of attacks.
3. Test for edge cases: Business logic errors often occur when the application encounters unexpected or edge cases. Test the application to see how it behaves when inputs are outside the expected range or when multiple processes are occurring simultaneously.
1/
Vuln: SSTI
Severity: Severity of the issue depends on from the engine that has been used
Server-side template injection occurs when user input is unsafely embedded into a server-side template, allowing users to inject template directives.
#bugbountytips #securitytips #SSTI
Vuln: SSTI
Severity: Severity of the issue depends on from the engine that has been used
Server-side template injection occurs when user input is unsafely embedded into a server-side template, allowing users to inject template directives.
#bugbountytips #securitytips #SSTI
2/
Constructing a server-side template injection attack
Detect → Identify → Exploit
- Detect if SST is vulnerable to attack
• Identify the engine that the server uses. There are a huge number of templating languages, characters.
• Develop exploit on received data
Constructing a server-side template injection attack
Detect → Identify → Exploit
- Detect if SST is vulnerable to attack
• Identify the engine that the server uses. There are a huge number of templating languages, characters.
• Develop exploit on received data
3/
How you can detect SSTI:
Try fuzzing the template by injecting a sequence of special characters, such as `${{<%[%'"}}%`
Vulnerable code: render('Hello ' + username)
Request: "vulnerable-website.com/?username=${7*7}"
If the resulting output - `Hello 49` executes a mathematical operation
How you can detect SSTI:
Try fuzzing the template by injecting a sequence of special characters, such as `${{<%[%'"}}%`
Vulnerable code: render('Hello ' + username)
Request: "vulnerable-website.com/?username=${7*7}"
If the resulting output - `Hello 49` executes a mathematical operation

Unlocking the Secrets: Breaking Access Controls, the basics 👇
(from the AI model I'm currently training on security reports)
(from the AI model I'm currently training on security reports)
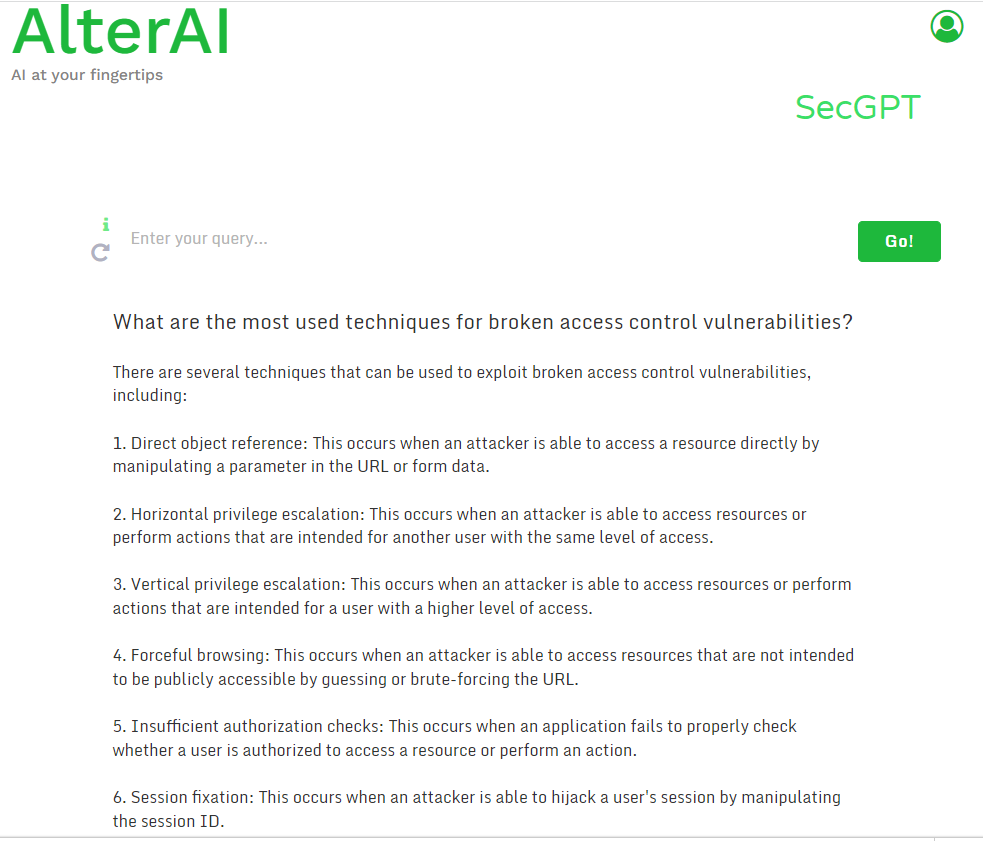
1. Direct object reference
This occurs when an attacker is able to access a resource directly by manipulating a parameter in the URL or form data.
This occurs when an attacker is able to access a resource directly by manipulating a parameter in the URL or form data.
2. Horizontal privilege escalation
This occurs when an attacker is able to access resources or perform actions that are intended for another user with the same level of access.
This occurs when an attacker is able to access resources or perform actions that are intended for another user with the same level of access.
Vulnexp 90 | Day53
➡️Insecure deserialization
when an attacker manipulates the way that HTTP requests are interpreted by a web server or a proxy server.
#bugbountytips #bugbountytip
Thread 🧵 : 👇
➡️Insecure deserialization
when an attacker manipulates the way that HTTP requests are interpreted by a web server or a proxy server.
#bugbountytips #bugbountytip
Thread 🧵 : 👇
• Insecure deserialization is a type of vulnerability that can occur in applications that involve the serialization and deserialization of data.
• Serialization is the process of converting an object , data structure into a format that can be transmitted or stored.
• Serialization is the process of converting an object , data structure into a format that can be transmitted or stored.
• XML, or binary data. Deserialization is the process of converting the serialized data back into an object or data structure.
• When an application receives serialized data, it may deserialize it to reconstruct the original object or data structure. However,
• When an application receives serialized data, it may deserialize it to reconstruct the original object or data structure. However,
Often times to simplify my work I build scripts.👇
I recently discovered katana by @pdiscoveryio. And I turned this:
katana -d 5 -c 50 -p 20 -ef "ttf,woff,svg,jpeg,jpg,png,ico,gif,css" -u <https://tld> -cs "regex-to-restrict-to-tld-and-subdomains"
into this:
kata <tld>
I recently discovered katana by @pdiscoveryio. And I turned this:
katana -d 5 -c 50 -p 20 -ef "ttf,woff,svg,jpeg,jpg,png,ico,gif,css" -u <https://tld> -cs "regex-to-restrict-to-tld-and-subdomains"
into this:
kata <tld>

1. The long command does the following:
-d => depth 5
-c => concurrency 50
-p => threads in parallel 20
-ef => exclude these
-u => supply the top level domain (i.e. twitter.com)
-cs => scope for this regex (limited to the tld and its subdomains)
-d => depth 5
-c => concurrency 50
-p => threads in parallel 20
-ef => exclude these
-u => supply the top level domain (i.e. twitter.com)
-cs => scope for this regex (limited to the tld and its subdomains)
2. You can download the kata bash script from my repo below. Use it as:
kata <tld>
Do me a favor and star the repo, thanks!
#pentesting #infosec #cybersecurity #ethicalhacking #bugbounty #bugbountytips
github.com/CristiVlad25/s…
kata <tld>
Do me a favor and star the repo, thanks!
#pentesting #infosec #cybersecurity #ethicalhacking #bugbounty #bugbountytips
github.com/CristiVlad25/s…
🚨Security Career Resource Thread 🚨
1️⃣ 2️⃣ resources to break into the field or take your career to the next level 👇
#infosec #cybersecurity #security
1️⃣ 2️⃣ resources to break into the field or take your career to the next level 👇
#infosec #cybersecurity #security
Learn:
🎓 How to get into various fields: pentesting, SOC analyst, AppSec, ...
🎫 Certs - do they matter? For which roles?
🧪 Doing security research
📣 Building your brand via blog posts, conference talks, and more
💸 How to think about compensation
🎓 How to get into various fields: pentesting, SOC analyst, AppSec, ...
🎫 Certs - do they matter? For which roles?
🧪 Doing security research
📣 Building your brand via blog posts, conference talks, and more
💸 How to think about compensation
📺 Launch your cybersecurity career: @IppSec's advice on how to become a skilled professional
* Technical tips
* Keeping a positive mindset
* Life is what you make it
#bugbounty #bugbountytips
* Technical tips
* Keeping a positive mindset
* Life is what you make it
#bugbounty #bugbountytips
Here is short writeup on how I found some hardcoded credentials inside of an exe file and got paid 2000$ even the asset was OUT OF SCOPE!
📌THREAD📌
1. I got invited to a private program with new assets
2. The asset was a web application for an Electron desktop app

📌THREAD📌
1. I got invited to a private program with new assets
2. The asset was a web application for an Electron desktop app


3. I tried to find the executable for the In scope app just to understand what the app will looks like when installed in the machine
4. I finally downloaded the app from the official website lf the target and tried to extract the Exe with tools like Winzip (Electron app can be easily extracted)
XSS PoC - AI Generated:
1. platform.openai.com/codex-javascri…
2. Prompt w/ description
3. Export to JSFiddle
4. Host it
5. Include external script
6. Escalate your alert()
#bugbountytips #infosec #xss #ai #GPT
👇🧵 for Prompt & Code
1. platform.openai.com/codex-javascri…
2. Prompt w/ description
3. Export to JSFiddle
4. Host it
5. Include external script
6. Escalate your alert()
#bugbountytips #infosec #xss #ai #GPT
👇🧵 for Prompt & Code

You guys always ask me how do I find SQL injections, its just simple. Avoid what everyone does and make your own methodology. Here is mine:
1. I don't normally go if the target is just target.com. I always prefer the target with wide scope.
1/n
#BugBounty
1. I don't normally go if the target is just target.com. I always prefer the target with wide scope.
1/n
#BugBounty
2. I always prefer to avoid main domain & focus on subdomain instead. Main domain is targeted by hundreds already, So go deeper, if you go deeper its more dark there & you will see its less crowded.
3. Make your own word-list using CeWL or anything
#bugbountytips
2/n
3. Make your own word-list using CeWL or anything
#bugbountytips
2/n
4. Use your word list to find hidden parameters. Read this well written article by @KathanP19 medium.com/geekculture/pa…
5. Use your word list to find hidden subdomains, I found 10s of more subdomains using WL created using the common words used in the source.
3/n
5. Use your word list to find hidden subdomains, I found 10s of more subdomains using WL created using the common words used in the source.
3/n


