Discover and read the best of Twitter Threads about #Cryptomining
Most recents (8)
Guys arguing BTC can be classified as a security under Howey test.
1/8: Let's explore why #Bitcoin and similar #cryptocurrencies aren't classified as securities under the Howey Test. This test assesses whether an arrangement involves an investment contract. #Crypto #HoweyTest
1/8: Let's explore why #Bitcoin and similar #cryptocurrencies aren't classified as securities under the Howey Test. This test assesses whether an arrangement involves an investment contract. #Crypto #HoweyTest
2/8: The Howey Test has 4 key points: an investment of money, expectation of profits, a common enterprise, and efforts of a promoter or third party. Let's break these down for Bitcoin. #CryptoRegulation #Bitcoin
3/8: Investment of Money: Yes, Bitcoin miners invest money in hardware and electricity, but they're not buying an investment contract from a third party. They contribute resources to validate transactions & secure the network. #CryptoMining
#Crypto Roundup: Top #CryptoNews This Week!
1/ #OKX, a leading crypto platform, is making a bold move by establishing a strong presence in France.
1/4
1/ #OKX, a leading crypto platform, is making a bold move by establishing a strong presence in France.
1/4
2/ The CEO of #FTX, a prominent #cryptocurrency exchange, has hinted at a significant update called '2.0 Reboot.'
3/ Hong Kong is defying regional crackdowns and embracing #cryptocurrencies.
2/4
3/ Hong Kong is defying regional crackdowns and embracing #cryptocurrencies.
2/4
4/ The #SEC is taking a controversial step by scrutinising #cryptomining equipment.
5/ Troubling allegations surround #Binance Exchange, suggesting the commingling of customer funds and company revenue.
3/4
5/ Troubling allegations surround #Binance Exchange, suggesting the commingling of customer funds and company revenue.
3/4
Since #RiotBlockchain changed their name to @RiotPlatforms, it's time to update our pinned thread!
#Bitcoin #Proofofwaste #Cryptomining #RiotBlockchain #NCAC
@WhinstoneUS @chadeverett @JasonLes_ @BenjaminYi21M @GVictoriaB @BitcoinPierre @Alexis_Brock_ @MorgensternNJ

#Bitcoin #Proofofwaste #Cryptomining #RiotBlockchain #NCAC
@WhinstoneUS @chadeverett @JasonLes_ @BenjaminYi21M @GVictoriaB @BitcoinPierre @Alexis_Brock_ @MorgensternNJ


@RiotPlatforms has a bitcoin mine in Milam County TX.
They get 100% property tax abatements for ten years.
#Bitcoin #Proofofwaste #Cryptomining #RiotBlockchain #NCAC
@WhinstoneUS @chadeverett @JasonLes_ @BenjaminYi21M @GVictoriaB @BitcoinPierre @Alexis_Brock_ @MorgensternNJ
They get 100% property tax abatements for ten years.
#Bitcoin #Proofofwaste #Cryptomining #RiotBlockchain #NCAC
@WhinstoneUS @chadeverett @JasonLes_ @BenjaminYi21M @GVictoriaB @BitcoinPierre @Alexis_Brock_ @MorgensternNJ

@RiotPlatforms decided to expand.
They misrepresented themselves as a "Data Center Project" to our local gov.
#Bitcoin #Proofofwaste #Cryptomining #RiotBlockchain #NCAC
@WhinstoneUS @chadeverett @JasonLes_ @BenjaminYi21M @GVictoriaB @BitcoinPierre @Alexis_Brock_ @MorgensternNJ
They misrepresented themselves as a "Data Center Project" to our local gov.
#Bitcoin #Proofofwaste #Cryptomining #RiotBlockchain #NCAC
@WhinstoneUS @chadeverett @JasonLes_ @BenjaminYi21M @GVictoriaB @BitcoinPierre @Alexis_Brock_ @MorgensternNJ

The first Network Security session at #PESW (organized by @FIT_CTU) has been started by @vaclavbartos1, the chair who introduces our speaker Lukáš Hejcman @FIT_VUT & @CESNET_cz. You may still visit us in Horoměřice at pesw.fit.cvut.cz/2022 until Saturday! 

Matej Hulák (@FIT_CTU & @CESNET_cz) is the second speaker. We move from Packet Capture by Lukáš H. to Traffic classification topic by Matej. 

3rd speaker of "Session 3 - Traffic Capture and Detection" - Richard Plný presents #CryptoMining #detection in #network #traffic. Using #IPFIX and "weak classifiers". 

(1/6) Our facility, a Thread:
We started out as a home mining operation with 5 Whatsminer D1's, and quickly grew a passion for crypto mining. #CryptoCommunity
We started out as a home mining operation with 5 Whatsminer D1's, and quickly grew a passion for crypto mining. #CryptoCommunity

I took a few photos over the weekend. It felt good to get out and shoot..but..as I pressed the shutter, I realized I wasn't just taking a photo, I was also mining $KOII 🤯
How is this possible? A short 🧵on what $KOII is and how you can mine @KoiiNetwork tokens with a camera.
How is this possible? A short 🧵on what $KOII is and how you can mine @KoiiNetwork tokens with a camera.

1/ Cryptographic tokens are mined through consensus mechanisms (i.e. Bitcoins Proof of Work) the @koiinetwork has a unique consensus mechanism called Proof of Real Traffic or PoRT whereby $KOII is mined through the verified traffic that visits a particular piece of content.
2/ When you take a photo and upload it to the @Koiinetwork it is registered as an Atomic NFT and stored permanently on the #Arweave permaweb.
#photographylovers
#photographylovers
(1) Possible buyout of #ARM by #NVIDIA does have an effect on the #Bioinformatics field: many applications now are deployable on CPU/GPUs with #ARM and/or #NVIDIA chips on them. Some recent examples are:
(a) the Oxford @nanopore MinION Mk1c device, which originally was specced at Jetson TX2 ARM+Pascal GPU accelerators (ARM processor 6 cores, 256 Core GPU), 8 GB RAM (may have changed since then.
#Campaign in tweets - @Guardicore Labs in a new tradition; we find the attacks, you get to know them and learn the attackers' tricks and techniques. This time, let's get familiarized with "Lemon_Duck", a #cryptomining campaign involving a sophisticated #propagation tool. 🍋🦆 
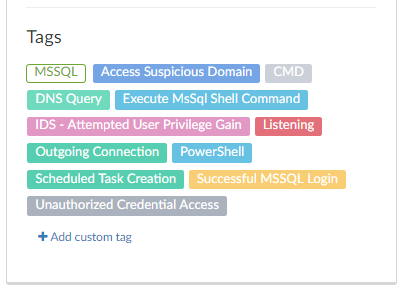
Before we start: all scripts, binaries and IOCs are available on our github repository. In addition, malicious IPs, attack servers and domains appear on @Guadicore Cyber Threat Intelligence portal. You're welcome to take a look :)
threatintelligence.guardicore.com/?utm_medium=or…
github.com/guardicore/lab…
threatintelligence.guardicore.com/?utm_medium=or…
github.com/guardicore/lab…
Lemon_Duck starts by breaching machines over the #MSSQL service or the #SMB protocol. We'll focus on the MS-SQL flow. Once inside the machine, the attacker enables #xp_cmdshell to run shell commands. It will take only a single command line to trigger the rest of the attack.