Discover and read the best of Twitter Threads about #vulnerabilities
Most recents (24)
⚠️ A browser extension is always a double-edged sword.
In general, there isn't much to disagree with in what @panosmek has written in this fantastic thread, but here are few additional thoughts:
🧵👇 [1/13]
In general, there isn't much to disagree with in what @panosmek has written in this fantastic thread, but here are few additional thoughts:
🧵👇 [1/13]
Very proud of this team effort "A regional integrated assessment of the impacts of #climatechange and of the potential #adaptation avenues for #Quebec’s #forests" is now published
A (very long) thread. Buckle up!
cdnsciencepub.com/doi/pdf/10.113…
@cflscf @NRCan
1/n
A (very long) thread. Buckle up!
cdnsciencepub.com/doi/pdf/10.113…
@cflscf @NRCan
1/n
First, I would like to acknowledge the work of all my colleagues including Jesus, Annie Claude, Yves, @mariehbrice, @DominicCyr, Louis, Daniel, @GauthierSylvie9 , Pierre, @Guillemette_L , Mathieu, Maryse, Tadeusz, Martin-Hugues, @ethiffault , @Tremblay_Jun and Stephen
2/n
2/n
Quebec’s #forests goes from northern hardwood with sugar #maple, beech, hemlock in the south, to pure boreal black #spruce forests up north. Natural #disturbances, go from single-tree windthrow or mortality in the south, to large stand-replacing #fires in the north.
3/n



3/n




WARNING:
There are new pathogens in our midst.
My latest article about media #manipulators, velocity #hacking, and the latest Covid origin #controversy.
Maybe some #mainstream journalists & influencers take a good look in the mirror.
Read:
protagonistfuture.substack.com/p/the-rise-of-…
There are new pathogens in our midst.
My latest article about media #manipulators, velocity #hacking, and the latest Covid origin #controversy.
Maybe some #mainstream journalists & influencers take a good look in the mirror.
Read:
protagonistfuture.substack.com/p/the-rise-of-…

How much should we think about the role of information in society?
In this article, I use the recent media coverage surrounding #lableak versus #zoonosis to point toward a new threat we have not yet wrapped our heads around:
Information pathogens with high #velocity.
In this article, I use the recent media coverage surrounding #lableak versus #zoonosis to point toward a new threat we have not yet wrapped our heads around:
Information pathogens with high #velocity.

#Velocity is a metric for the transmission efficacy of information given a particular content payload, its viral packaging, and its host environment.
Basically the R0 of information, a measure of #contagiousness.
Info pathogens with high velocity outcompetes good information.
Basically the R0 of information, a measure of #contagiousness.
Info pathogens with high velocity outcompetes good information.

🚨New #MicrosoftExchange #vulnerabilities were disclosed, including CVE-2022-41040 and CVE-2022-41082. Threat actors can easily exploit the new vulnerabilities, and bypass #ProxyNotShell URL rewrite mitigations, resulting in many companies facing further #ransomware #attacks.
An example of what such an exploit can do is shown in the picture below, where the #threat actor #FIN7 developed tailored systems to quickly discover and infiltrate the high-value targets by performing mass scans using #Microsoft #exchange #vulnerabilities. 

Our PTI team has already observed activities involving recent vulnerabilities in the wild. Therefore, #PRODAFT recommends that companies fix the vulnerabilities as soon as possible to avoid serious consequences.
Who determines how severe a vulnerability is?
Severity is how much damage a hacker can inflict exploiting a product using that vulnerability. It doesn’t mean this is the most critical risk facing your system, but many developers mistakenly think it is.
Severity is how much damage a hacker can inflict exploiting a product using that vulnerability. It doesn’t mean this is the most critical risk facing your system, but many developers mistakenly think it is.
1/ Severity & other information related to a known issue are catalogued in a Common Vulnerabilities & Exposures (CVE) database.
Several orgs track CVEs, including the National Institute of Standards & Technology @NIST #severity #vulnerabilities
Several orgs track CVEs, including the National Institute of Standards & Technology @NIST #severity #vulnerabilities
2/ The rubric for scoring severity is the Common Vulnerability Scoring System (CVSS), an open framework for communicating the characteristics & severity of software vulnerabilities.
Several factors are classified into three categories: base, temporal & environmental.
Several factors are classified into three categories: base, temporal & environmental.
🧵Let's talk about #Telegram - here are ten useful cybersecurity groups and channels we watch:
A thread:
A thread:
1. Cyber Security News (30k+ members)
Cyber Security News is a feed channel for links to breaking news stories across the internet, everything from #TechCrunch to #Portswigger. It’s a one-stop shop for cyber-related news with your morning coffee.
telegram.me/cyber_security…
Cyber Security News is a feed channel for links to breaking news stories across the internet, everything from #TechCrunch to #Portswigger. It’s a one-stop shop for cyber-related news with your morning coffee.
telegram.me/cyber_security…
2. Cyber Security Experts (23k+ members)
A great channel for exchanging #information about #cyber, #IT, and #security. Mainly used to get answers to questions and help other security experts to enhance their security maturity.
t.me/cybersecuritye…
A great channel for exchanging #information about #cyber, #IT, and #security. Mainly used to get answers to questions and help other security experts to enhance their security maturity.
t.me/cybersecuritye…
⬇️very useful document offering a network perspective on societal ills currently plaguing us.
I am certainly appreciating the insights offered here and fully agree with many of the things outlined.
Please give it a read:
1/
I am certainly appreciating the insights offered here and fully agree with many of the things outlined.
Please give it a read:
1/
I've been thinking more on a complexity framework to account for the non-linearity of the systems we are part of, as well as emergence and control theory.
But network & graph theory plays an enormous role there as well because complex systems can be abstracted into networks
2/


But network & graph theory plays an enormous role there as well because complex systems can be abstracted into networks
2/



The really interesting question is not what framework or models we use to #conceptualize the relationships between society and our broken info spheres, but whether or not they are #useful to understand why we currently experience #democratic backsliding around the world
3/


3/



Another new idea for #PenetrationTesting and #Bug-hunting:
Tester:
Enhance the force of #vulnerabilities by doing things like
I discovered a free #URL that leads somewhere else.
Put this in my report and move on ?
Tester:
Enhance the force of #vulnerabilities by doing things like
I discovered a free #URL that leads somewhere else.
Put this in my report and move on ?
To the contrary, changing the #payload allowed me to transform it into a reflected #XSS #vulnerability. Is this the final question?
Obviously not if I have any hope of carrying on.
Obviously not if I have any hope of carrying on.
Here's a list of free #PenetrationTesting and #RedTeam Labs you may set up in your own home to enhance your #hacking abilities :
1) Red Team Attack Lab
A simulated setting where red teams can practice exploiting #vulnerabilities in various operating systems.
lnkd.in/ernefQv8
A simulated setting where red teams can practice exploiting #vulnerabilities in various operating systems.
lnkd.in/ernefQv8
2) Capsulecorp Pentest
#Capsulecorp is a lightweight virtual infrastructure operated using Vagrant and Ansible. One #Linux attacking system running #Xubuntu is included, along with four #Windows 2019 servers hosting a variety of #exploitable services.
lnkd.in/eYfGmNBe
#Capsulecorp is a lightweight virtual infrastructure operated using Vagrant and Ansible. One #Linux attacking system running #Xubuntu is included, along with four #Windows 2019 servers hosting a variety of #exploitable services.
lnkd.in/eYfGmNBe
Here are some of my favorite 💯 FREE TryHackMe Path /Rooms to learn Web Hacking.
#Hackingtime #hacking #tryhackme #Website #Pentesting #vulnerabilities
👇
#Hackingtime #hacking #tryhackme #Website #Pentesting #vulnerabilities
👇
Room 1⃣: HTTP In Detail
⁃ Learn about how you request content from a web server using the HTTP protocol.
🔗
tryhackme.com/room/httpindet…
⁃ Learn about how you request content from a web server using the HTTP protocol.
🔗
tryhackme.com/room/httpindet…
Room 2⃣: Burp Suite: The Basics
⁃ An introduction to using Burp Suite for Web
Application #Pentesting .
🔗
tryhackme.com/room/burpsuite…
⁃ An introduction to using Burp Suite for Web
Application #Pentesting .
🔗
tryhackme.com/room/burpsuite…
Since your malicious cyberattack timelines matched cybersecurity’s research to strengthen security for years and now, you hack alone but with a cooperative goal to damage national security. Which Advanced Persistent Threats group/s #APTs are you in, #Animez_UK? 

Converting traditional crime to cyber-enabled crime and becomes a malicious attacker against the UK, for
1- financial income,
2- #sexual desire and #harassment with #pornography sent to #women,
3- attacks for #politics against the UKGOV.
#Animez_UK

1- financial income,
2- #sexual desire and #harassment with #pornography sent to #women,
3- attacks for #politics against the UKGOV.
#Animez_UK


1st stage- early life:
-Experienced #exclusion/#discrimination.
-Didn’t learn to communicate with #women.
-favours #authoritarianism.
-enjoys #control targeted women & whom against his will.
- Expresses hidden #hatred & #violence on through cyberattacks.
#Animez_UK

-Experienced #exclusion/#discrimination.
-Didn’t learn to communicate with #women.
-favours #authoritarianism.
-enjoys #control targeted women & whom against his will.
- Expresses hidden #hatred & #violence on through cyberattacks.
#Animez_UK


Having fun with cyberstalking #UKGOV, attacking organisations, universities & individuals connected to the justice system, UK #military against #NCSC, treating #intelligence & #GCHQ as jokes to your 15- 20 yrs malicious #hacking for #China & #Russia inside #Britain, @Animez_UK?01
Converting #traditional crime to cyber-enabled crime and becomes a malicious #cyberattacker against the UK, for
1- #financial income,
2- #sexual desire and #harassment with #pornography sent to #women,
3- attacks for #politics against the #UKGOV.
@Animez_UK @NCSC
02
1- #financial income,
2- #sexual desire and #harassment with #pornography sent to #women,
3- attacks for #politics against the #UKGOV.
@Animez_UK @NCSC
02

1st stage- early life:
-Experienced #exclusion/#discrimination.
-Didn’t learned to communicate with #women.
-favours #authoritarianism.
-enjoys to #control targeted women & whom against his will.
- Expresses hidden #hatred & #violence on through cyberattacks.
@Animez_UK @NCSC
-Experienced #exclusion/#discrimination.
-Didn’t learned to communicate with #women.
-favours #authoritarianism.
-enjoys to #control targeted women & whom against his will.
- Expresses hidden #hatred & #violence on through cyberattacks.
@Animez_UK @NCSC

Top 10 Blockchain Attacks That resulted in cryptocurrency losses all around the world.
A Thread 🧵👇
#Web3 #cryptotrading #cryptocrash #Bitcoin #Blockchain #cybersecuritytips #hacking #vulnerabilities #javascript
A Thread 🧵👇
#Web3 #cryptotrading #cryptocrash #Bitcoin #Blockchain #cybersecuritytips #hacking #vulnerabilities #javascript
1⃣ Exchange Hack
2⃣ DeFi Hack
Recently I contributed to a paper on "Reporting Cyber Risk to Boards". It summarizes findings and best practices from a CISO Working Group, and is a must read for CISOs, CIOs, and other Cybersecurity executives that report to the Board.
Highlights🧵
Highlights🧵

Boards often fail to see the continuous importance of cybersecurity and have knee jerk reactions to breaking cyber stories in the media then quickly forget about it until the next big cyber incident. Typically, cybersecurity only becomes an issue when it is already too late.
In cases where cybersecurity reporting to the Board is taking place, there is a wide variety of methods, tools, and processes in use. Organizations struggle with what to report and how to obtain effective feedback from the Board.
17. Hi, this is @akgungor_c again. Let’s come back to where we had left: Post-disaster controversies… These are indeed closely associated with how we individually and socially (re)construct the #catastrophe.
18. A disaster is the outcome(s) of a physical occurrence as well as how we perceive and process them. Like any “event”, for every disaster, there are as many accounts as the number of people who’ve been exposed to it.
19. Individual #narratives of a disaster are the expression of how we position ourselves vis-a-vis the catastrophe and its effects on us, in a sense, fabricating our own #reality.
9. Hello again, @akgungor_c continues from where he has left :) So, I tend to think of #disasters as systemic “radiographs”. I’m not sure when I first came up with this analogy but I usually associate this idea with my own experience as a search & rescue volunteer.
10. After all, looking around in a disaster-stricken zone, few people don't come to reflect on their own #vulnerability first, then, gradually, about the vulnerability of human societies to massive #disruptions.
11. The greater the impact, the thinner seems the protective bubble provided by our physical and social systems.
#SecurityExplained S-61: CWE-787: Out-of-bounds Write
The Out-of-bounds Write is a software security vulnerability that occurs when the data is written beyond the boundaries (i.e. past the end, before the beginning) of the intended buffer.
1/n
The Out-of-bounds Write is a software security vulnerability that occurs when the data is written beyond the boundaries (i.e. past the end, before the beginning) of the intended buffer.
1/n
2/n
This weakness is also listed in the CWE TOP 25 (2021). This has been given the CWE ID as CWE-787
- This vulnerability could result in buffer overflows, memory corruption, the crash of the software or even a code execution.
This weakness is also listed in the CWE TOP 25 (2021). This has been given the CWE ID as CWE-787
- This vulnerability could result in buffer overflows, memory corruption, the crash of the software or even a code execution.
3/n
As per the cwe.mitre.org, The software may modify an index or perform pointer arithmetic that references a memory location that is outside of the boundaries of the buffer. A subsequent write operation then produces undefined or unexpected results.
As per the cwe.mitre.org, The software may modify an index or perform pointer arithmetic that references a memory location that is outside of the boundaries of the buffer. A subsequent write operation then produces undefined or unexpected results.
1. Never click on unsafe links: Avoid clicking on links in spam messages or on unknown websites. If you click on malicious links, an automatic download could be started, which could lead to your computer being infected.
2. Avoid disclosing personal information: If you receive a call, text message, or #email from an untrusted source requesting personal information, do not reply. #Cybercriminals who are planning a #Ransomware attack might try to collect personal information in advance,
We have had a busy 2021 and we look forward to 2022 which is brightened further with the spirit of Indovation and ideation. Cheers to each of you and your families. 

2/n 2021 was a challenging year personally for many with #Covid 2nd wave but it presented professional opportunities for #startup ecosystem too. @SucSEED_IN built its maiden #AngelFund #IndovationFund, amongst overwhelming response & kept growing its strength as #AngelNetwork too 



3/n At #IndovationFund, we believe that early-stage discovery is best handled with the help of Experienced folks. We have great #SectoralCommittee structure helping us to discover, screen, curate, invest and mentor these startups, in 6 sectors of our #Fundfocus #SucSEEDfamily 

RDP brute-force attacks were up again in T2 2021, with 55 billion detections – a 104% increase compared to T1 2021. #ESETreserach also saw a massive surge in #RDP attacks against Spanish entities in August, accounting for a third of global all detections that month. 1/4 
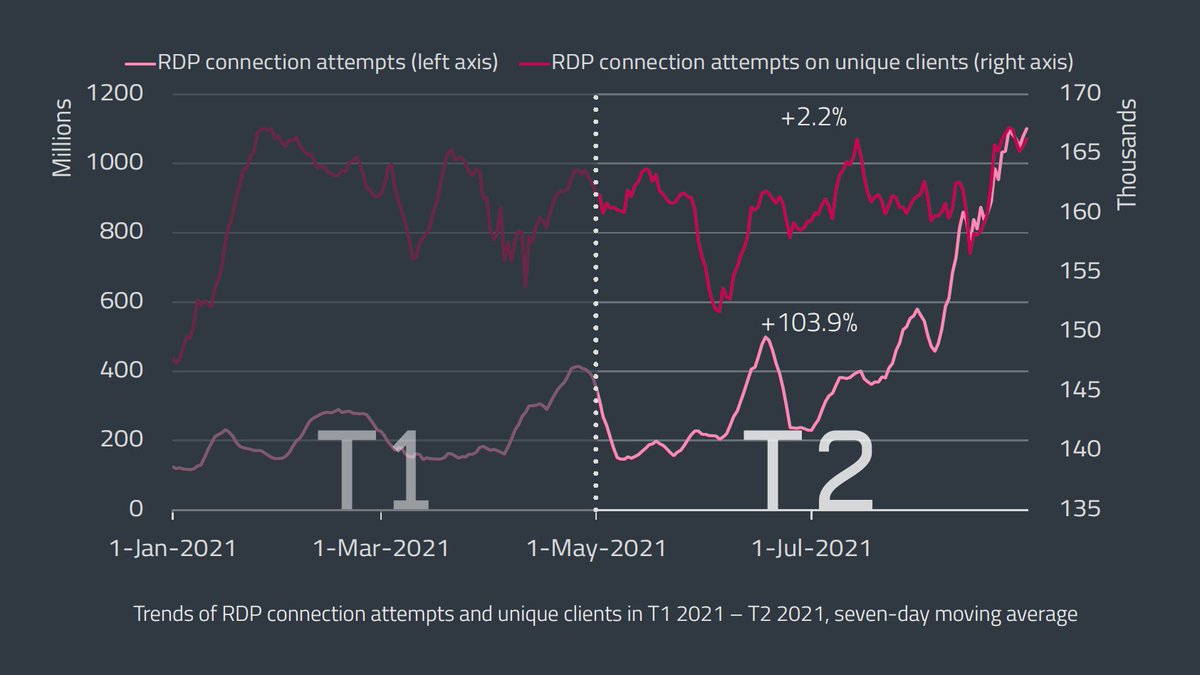
Attackers seem to have a hard time finding new #RDP targets, yet those that are already on their list are hit more aggressively, confirmed by an increase in average daily attacks per unique client, which doubled from 1,392 attempts in T1 2021 to 2,756 in T2 2021. 2/4 

Password guessing was the top external network intrusion vector with 53%, followed by attempts to exploit #ProxyLogon #vulnerabilities (22%) and attempted deployment of NSA backdoor #DoublePulsar (10%). 3/4 

So #ICYMI #OnThisDay in 1974, and into the following day, was the #Tornado #SuperOutbreak This montage of images is on the @NWS pages at: weather.gov/iln/19740403 

I have the following image as a poster in my office for several reasons, which I will expound upon in subsequent tweets. Firstly it was produced by hand by Theodore ‘Ted’ Fujita, who developed the F-scale (later the EF-Scale based in wind intensity and damage. 

What I really noticed in the key/legend on the map was how he was also looking at the type of structure where fatalities occurred, something that other scientists (@StephenMStrader) were looking at before I came along, but once you start, you can’t stop. I’m pretty much obsessed. 

This thread brings together all my #infographics until today (2years of work).
These are all infographics about #infosec 🔐
Feel free to share this tweet if you think it may be useful for your #community 📚
Follow me ➡ @SecurityGuill fore more about #security #hacking #news



These are all infographics about #infosec 🔐
Feel free to share this tweet if you think it may be useful for your #community 📚
Follow me ➡ @SecurityGuill fore more about #security #hacking #news



How does an #Antivirus works? 

Quick presentation of the different #Bluetooth Hacking Techniques 

Daily Bookmarks to GAVNet 01/12/2021 greeneracresvaluenetwork.wordpress.com/2021/01/12/dai…
It’s our birthday! #CISAgov was established on November 16, 2018. From elections to COVID-19 to natural disasters and more, year two has been action-packed. Let’s take a trip down memory lane… 

Informed by #cyber intelligence and real-world events, we issued several insight products, providing background on #cyber threats, #vulnerabilities, and mitigation activities: cisa.gov/insights #InfoSec
One key insight was in in January when we warned partners about potential Iranian retaliation against U.S. organizations—and advised them on how to assess and strengthen their physical & cyber security. This is the kind of rapid information-sharing we aim for! #InfoSecurity