Discover and read the best of Twitter Threads about #QuasarRAT
Most recents (3)
1/ #QuasarRAT 🐀 was observed being delivered via #OneNote. Shoutout to @dr4k0nia for helping me with deobfuscating the "injector" ✏️ and showing me some .NET dark arts.
C2: ghcc.duckdns[.]org:4782
Extracted configuration: github.com/RussianPanda95… twitter.com/i/web/status/1…



C2: ghcc.duckdns[.]org:4782
Extracted configuration: github.com/RussianPanda95… twitter.com/i/web/status/1…

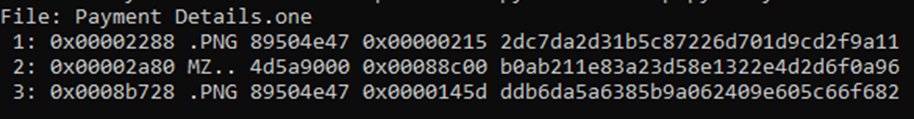


@dr4k0nia 2/
➡️Dropped CAB file: %temp%\OneNote\16.0\Exported\{3990CE71-148C-4B04-8347-A8BB7F676C8D}\NT\0\view.EXE
➡️Dropped VBS payload: %temp%\IXP000.TMP\new.vbs"
➡️Dropped CAB file: %temp%\OneNote\16.0\Exported\{3990CE71-148C-4B04-8347-A8BB7F676C8D}\NT\0\view.EXE
➡️Dropped VBS payload: %temp%\IXP000.TMP\new.vbs"

@dr4k0nia 3/ The cab file extracts and executes new.vbs file (MD5: f7e7099eea0cc25fc49d04cd53c573a1), which retrieves the PowerShell script from hxxps://transfer[.]sh/get/MHXbtP/ss.ps1 (404 now) but you can still grab the script from VT (MD5: 970aca768e68faa580f758a1a379686b)
1/ #ThreatHunting:
#QuasarRAT is another RAT we see from time to time in our IR cases and was also used against NATO facilities in March. [1]
We can hunt for
1⃣ The default port within the FW logs
2⃣Mutexes
3⃣User-Agent
4⃣Persistence mechanisms
🧵
#QuasarRAT is another RAT we see from time to time in our IR cases and was also used against NATO facilities in March. [1]
We can hunt for
1⃣ The default port within the FW logs
2⃣Mutexes
3⃣User-Agent
4⃣Persistence mechanisms
🧵
2/ @qualys has published an excellent paper ("Stealthy Quasar Evolving to Lead the RAT Race") about Quasar, where the whole builder and much more are described in detail. [2]
#ESETresearch identified malicious MS Excel documents automatically downloaded upon visiting the websites of cryptocurrencies #HotDoge, www.hotdogetoken[.]com, and #DonutCatBSC, www.donutcatbsc[.]com. Opening the document led to stealing the victim’s private information. 1/6 



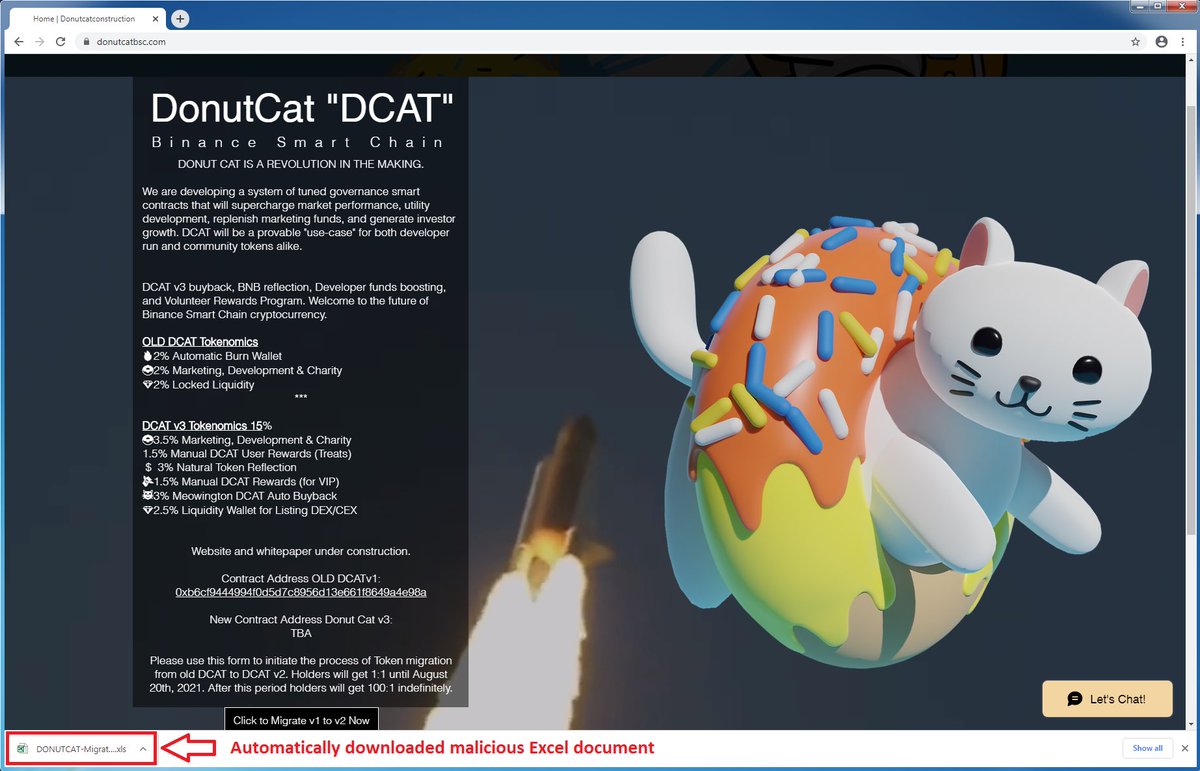



We contacted @HotDogeTokenBSC and provided them with the information to remediate the threat. They resolved the issue and the websites no longer serve the malicious documents. 2/6
We attribute this campaign to the 🇰🇵North Korea-linked APT group #Kimsuky. The Excel document contains a malicious Excel V4.0 macro that uses the #Squiblydoo technique to download and execute an XML file with a VBS scriptlet. 3/6

