Discover and read the best of Twitter Threads about #Kimsuky
Most recents (5)
🚨 1/ Ongoing campaign primarily targeting security researchers here on Twitter.
Possibly they are trying to exploit some vulnerability in Internet Explorer and database tools like Navicat. I haven't been able to get the malicious payload yet, but something fishy is going on 🤔



Possibly they are trying to exploit some vulnerability in Internet Explorer and database tools like Navicat. I haven't been able to get the malicious payload yet, but something fishy is going on 🤔



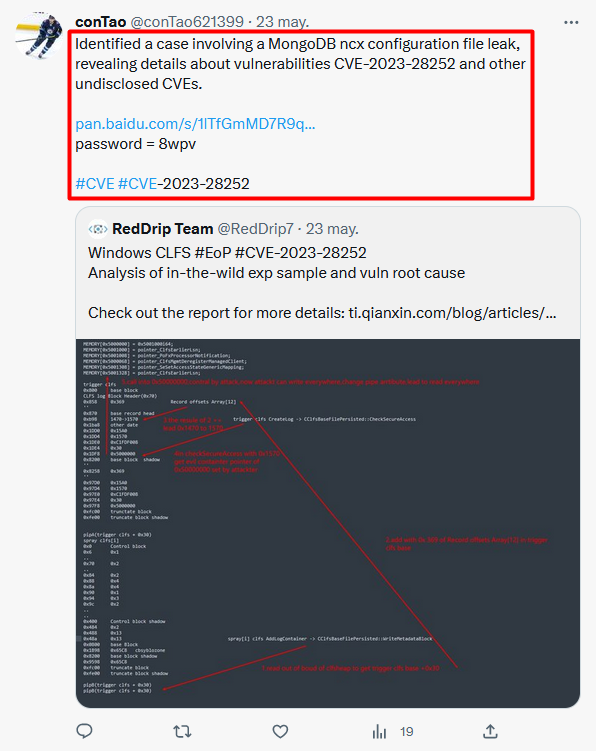
2/ Tweets mention things like #0day, #databreach, #Kimsuky, #Lazarus and point to a file download on pan[.]baidu[.]com, just now removed.
There is also a repo on Github with connection data and credentials to supposed DBs and Web Apps that ask to use IE 🤭



There is also a repo on Github with connection data and credentials to supposed DBs and Web Apps that ask to use IE 🤭




We (@interlab_kr) have been tracking a threat actor we classify as UCID902. This actor is utilising watering hole credential harvesting attacks to target activists related to the advocacy of human rights in the Korea peninsular.
We first observed UCID902 in 2021 when working with activists based in SK and with lures aimed to appear as Naver security alerts, prompting users to input credentials. We found that typical infrastructure was set up on legitimate web development organisations web servers.
Over the last 2 years, we have seen consistent efforts to target individuals from the human rights and civil society communities.
#ESETresearch identified malicious MS Excel documents automatically downloaded upon visiting the websites of cryptocurrencies #HotDoge, www.hotdogetoken[.]com, and #DonutCatBSC, www.donutcatbsc[.]com. Opening the document led to stealing the victim’s private information. 1/6 



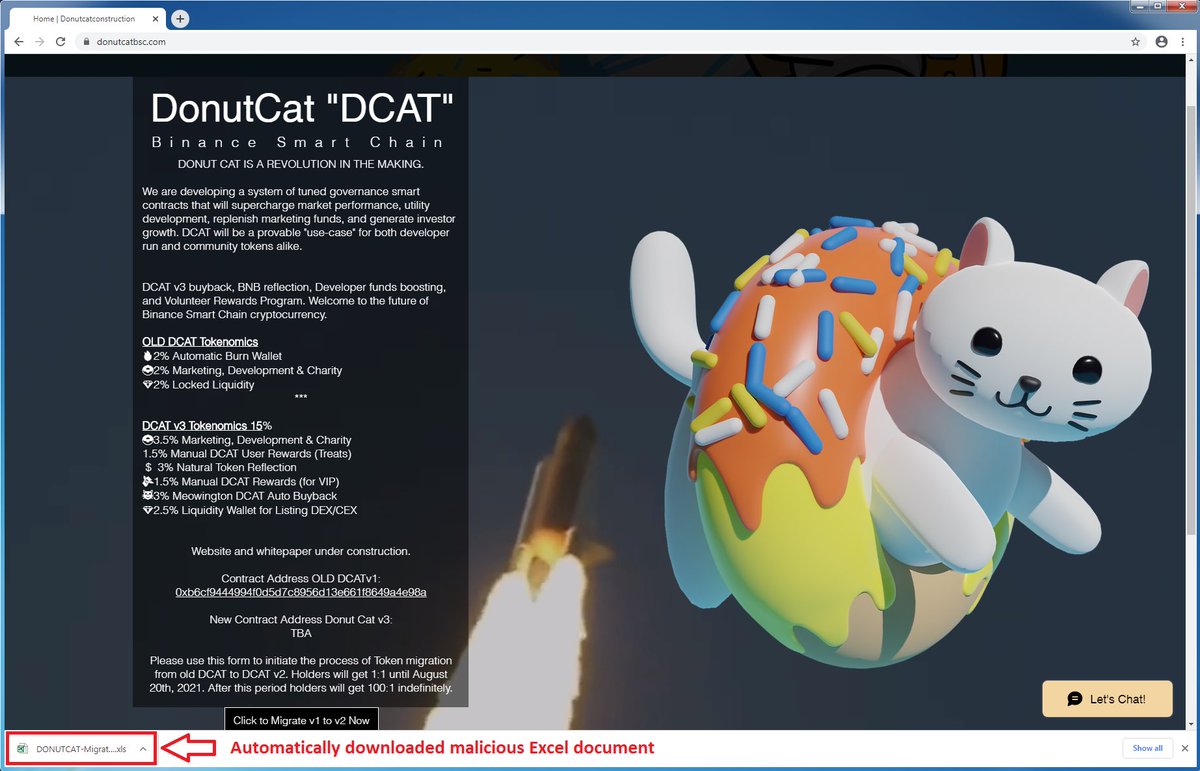



We contacted @HotDogeTokenBSC and provided them with the information to remediate the threat. They resolved the issue and the websites no longer serve the malicious documents. 2/6
We attribute this campaign to the 🇰🇵North Korea-linked APT group #Kimsuky. The Excel document contains a malicious Excel V4.0 macro that uses the #Squiblydoo technique to download and execute an XML file with a VBS scriptlet. 3/6
#niet_in_journaal #nieuwsuur #1V #Op1 #bbvpro #NPOradio1 #Mozambique #Cabo_Delgado #human_rights_abuses allafrica.com/stories/202010…
#NorthKorea #Kimsuky #zhaozhongcheng
김민관 부부장 토론문.hwp
03da25ae8b98ae05b2a18e61ebb88d08
c2 : sportgame.mypressonline[.]com
김민관 부부장 토론문.hwp
03da25ae8b98ae05b2a18e61ebb88d08
c2 : sportgame.mypressonline[.]com









