Discover and read the best of Twitter Threads about #Reverseengineering
Most recents (17)
Y si os digo que hay una #Blockchain cuyo objetivo es robarte y espiarte a ti como usuario. Es decir, en si es un #Malware encubierto. O al menos la billetera principal del proyecto lo es. La blockchain es #ceilingcatcoin Adelante HILO.
Esta historia comienza con varios usuarios afectados que me contactaron por Redes, indicando que les han #robado todos sus fondos #crypto en diferentes blockchain y diferentes billeteras (Claves privadas), yo no me lo creía hasta que lo comprobé.
Todos tenían una cosa en común, habían invertido en un nuevo proyecto nuevo, que se llama #ceilingcatcoin. Como buen analista, con buen pensamiento lateral empiezo por lo que han hecho en común.
𝐌𝐚𝐥𝐰𝐚𝐫𝐞 𝐚𝐧𝐝 𝐑𝐞𝐯𝐞𝐫𝐬𝐞 𝐄𝐧𝐠𝐢𝐧𝐞𝐞𝐫𝐢𝐧𝐠 𝐂𝐨𝐧𝐭𝐞𝐧𝐭𝐬 📢
#infosec #Hacking #redteam
#malware #ReverseEngineering
#RE
Awesome Malware and Reverse Engineering
lnkd.in/dZFy_k6d
lnkd.in/dZh9hbpq
#infosec #Hacking #redteam
#malware #ReverseEngineering
#RE
Awesome Malware and Reverse Engineering
lnkd.in/dZFy_k6d
lnkd.in/dZh9hbpq
Awesome Reverse Engineering
lnkd.in/etvePWr
lnkd.in/dh25YEkn
lnkd.in/daEcJEJ9
lnkd.in/ds88s46R
Awesome Malware Analysis
lnkd.in/dh_tMmyY
lnkd.in/e3KJ7rC
lnkd.in/dbn94MUW
lnkd.in/etvePWr
lnkd.in/dh25YEkn
lnkd.in/daEcJEJ9
lnkd.in/ds88s46R
Awesome Malware Analysis
lnkd.in/dh_tMmyY
lnkd.in/e3KJ7rC
lnkd.in/dbn94MUW
Malware API
malapi.io
lnkd.in/djqeN7RS
Malware Analysis and Reverse Engineering
lnkd.in/dXjFkZ7a
Retoolkit
lnkd.in/dwn8bRi3
Malware Bazar
bazaar.abuse.ch
Malware Analysis Journey
lnkd.in/d9B6UGQ8
malapi.io
lnkd.in/djqeN7RS
Malware Analysis and Reverse Engineering
lnkd.in/dXjFkZ7a
Retoolkit
lnkd.in/dwn8bRi3
Malware Bazar
bazaar.abuse.ch
Malware Analysis Journey
lnkd.in/d9B6UGQ8
Have you been interested in #reverseengineering but don't know where to begin or what tools to use? Are you still stuck in OllyDBG? Our researcher @pastaCLS recommends the coolest tools you'll see out there. Plus, our team uses them to defeat protection💙 

#Ghidra is useful for static analysis of binaries; it disassembles and decompiles to "C pseudo code." It supports a lot of architecture, has hundreds of plugins from the community and, last but not least, an active community.💪
ghidra-sre.org
ghidra-sre.org
@x64dbg is a debugger for Windows x86 and x64, perfect for analyzing the behavior of the program while running and freezing it in specific points to examine a feature.
x64dbg.com
x64dbg.com
#Iran, maestro del #Reverseengineering, sta ottenendo armamenti Nato catturati dai russi in Ucraina per studiarli e sviluppare dispositivi "home made". Il destino di sistemi, soprattutto a spalla, come Javelin e Stinger, abbandonati sul campo edition.cnn.com/2023/03/10/pol…
dai militari #Ucraina è stato più volte affrontato in questo anno di guerra. Storicamente gli iraniani hanno sviluppato i propri armamenti partendo proprio da attrezzature "catturate" al nemico, come il sistema Toophan, derivante dal Tow, oppure i famigerati Shahed, copia
dell'RQ-170 prodotto da @LockheedMartin. La "retro ingegneria" rappresenta la cifra dell'industria bellica iraniana con importanti risultati soprattutto nei sistemi missilistici derivanti da prodotti acquistati da partner come Russia, Nord Corea o Cina, oppure prelevati da
______________________
Can you think of any one Contributor who has provided
SO MUCH on ALL OF IT ?
I want my fucking dog biscuits.
🐶
Can you think of any one Contributor who has provided
SO MUCH on ALL OF IT ?
I want my fucking dog biscuits.
🐶
Want to know more about Reverse Engineering? Check out these resources. #ReverseEngineering #infosecurity 📢
1. Reverse Engineering for Beginners by Ophir Harpaz: begin.re
2. Reverse Engineering for Everyone by Kevin Thomas My Technotalent lnkd.in/eUqUDdXS
1. Reverse Engineering for Beginners by Ophir Harpaz: begin.re
2. Reverse Engineering for Everyone by Kevin Thomas My Technotalent lnkd.in/eUqUDdXS
3. Reverse Engineering for beginners by Dennis Yurichev (available in many languages) lnkd.in/eHsdurZG
4. Malware Analysis In 5+ Hours - Full Course - Learn Practical Malware Analysis! by HuskyHacks lnkd.in/eR3_ki-6
#infosec
4. Malware Analysis In 5+ Hours - Full Course - Learn Practical Malware Analysis! by HuskyHacks lnkd.in/eR3_ki-6
#infosec
5. Malware Analysis – Mind Map by Thatintel lnkd.in/evyAhNWt
6. Malware Analysis Tutorials: a Reverse Engineering Approach by Dr Xiang Fu lnkd.in/eHZFTSqp
#Hacking #cybersecuriy #infosec
6. Malware Analysis Tutorials: a Reverse Engineering Approach by Dr Xiang Fu lnkd.in/eHZFTSqp
#Hacking #cybersecuriy #infosec
No matter how benevolent a dictatorship is, it's still a dictatorship, and subject to the dictator's whims. We must demand that the owners and leaders of tech platforms be fair and good - but we must also be prepared for them to fail at this, sometimes catastrophically. 1/ 

If you'd like an essay-formatted version of this thread to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
pluralistic.net/2022/12/23/sem… 2/
pluralistic.net/2022/12/23/sem… 2/
If you want to browse the customer service locations of the Hungarian State Treasury on allamkincstar.gov.hu, it is good to have some basic #ReverseEngineering skills. 😉 #UXFail @AdobeFlash in 2022. Thread 1/🧵⬇️ 

It is relatively easy to navigate to a customer service selector page. At the bottom there should be a county chooser according to the text, but there is nothing below. Let’s see why. 2/🧵⬇️ 

In the source code we can see that the webpage contains a Flash (SWF) object included. Yes, the county chooser of allamkincstar.gov.hu is a flash object, even though it is 2022 and @AdobeFlash is EOL and support has been removed from the browsers for over >1.5 year. 3/🧵⬇️ 

I'm getting messages from folks seeking favors for learning exploit development. I'm posting this thread for those who wanna explore the art of binary exploitation.
NB: There's no specific path, practice makes perfect 💯
#infosec #exploitdevelopment #ReverseEngineering
🧵🧵
NB: There's no specific path, practice makes perfect 💯
#infosec #exploitdevelopment #ReverseEngineering
🧵🧵
pwn college is organized as a set of modules covering different topics. Each module has a set of lecture slides and videos and practice problems auto-generated for each aspiring hacker to practice on.
pwn.college
pwn.college
Nightmare is an intro to binary exploitation / reverse engineering course based around CTF challenges.
guyinatuxedo.github.io
guyinatuxedo.github.io
#ESETresearch is offering you a #behindthescenes look at the diligent work required to see through the
obfuscation techniques used in the recently described #Wslink, unique and undocumented
malicious loader that runs as a server. 1/5
@HrckaVladislav
welivesecurity.com/2022/03/28/und…
obfuscation techniques used in the recently described #Wslink, unique and undocumented
malicious loader that runs as a server. 1/5
@HrckaVladislav
welivesecurity.com/2022/03/28/und…
Wslink’s multilayered #virtualmachine introduced a diverse arsenal of #obfuscation techniques, which
we were able to overcome to reveal a part of the deobfuscated malicious code. 2/5
we were able to overcome to reveal a part of the deobfuscated malicious code. 2/5

We also described the code we developed to facilitate our research. It is provided to the community
@github 3/5
github.com/eset/wslink-vm…
@github 3/5
github.com/eset/wslink-vm…
You are starting #ReverseEngineering and don't really know what to do with your binary ? Let's see how you can use @cutter_re to approach a reverse challenge in a CTF competition. Thread ⬇️
First of all, let's install cutter AppImage: cutter.re/download/ and then give it execution rights. This tool is a GUI built on top of @rizinorg, a radare2 fork with a better focus on stability and code quality.
Then open cutter, select your binary and run it with aaa for basic analysis. Note that you can also select the "Load in write mode" if you want to edit the binary (i.e. change its behavior).
Daily Bookmarks to GAVNet 03/29/2021 greeneracresvaluenetwork.wordpress.com/2021/03/29/dai…
Testing mobile air purifiers in a school classroom: Reducing the airborne transmission risk for SARS-CoV-2
tandfonline.com/doi/full/10.10…
#AirPurifiers #SchoolClassrooms #AirborneTransmission #COVID19 #risk
tandfonline.com/doi/full/10.10…
#AirPurifiers #SchoolClassrooms #AirborneTransmission #COVID19 #risk
What Does the World Need? More Humans
bloomberg.com/opinion/articl…
#PopulationDecline #ExistentialThreat
bloomberg.com/opinion/articl…
#PopulationDecline #ExistentialThreat
"The Lancet‘s fraudulent concealment of genetics, and its own conflicting interests, while condemning #coronavirus conspiracy theorists, gives the appearance of “crisis capitalism,” and complicity in the COVID-19-SARS/HIV-1 #Wuhan ‘Event 201‘ biocrime." 

The 'Scientific' arguments going on behind the scenes on #Covid_19 should be a wake-up call to the 'TRUE' dangers the world is being exposed to! 'BOTH' sides of the argument are labelling the other 'Conspiracy Theorists'. Only one of them can be! 
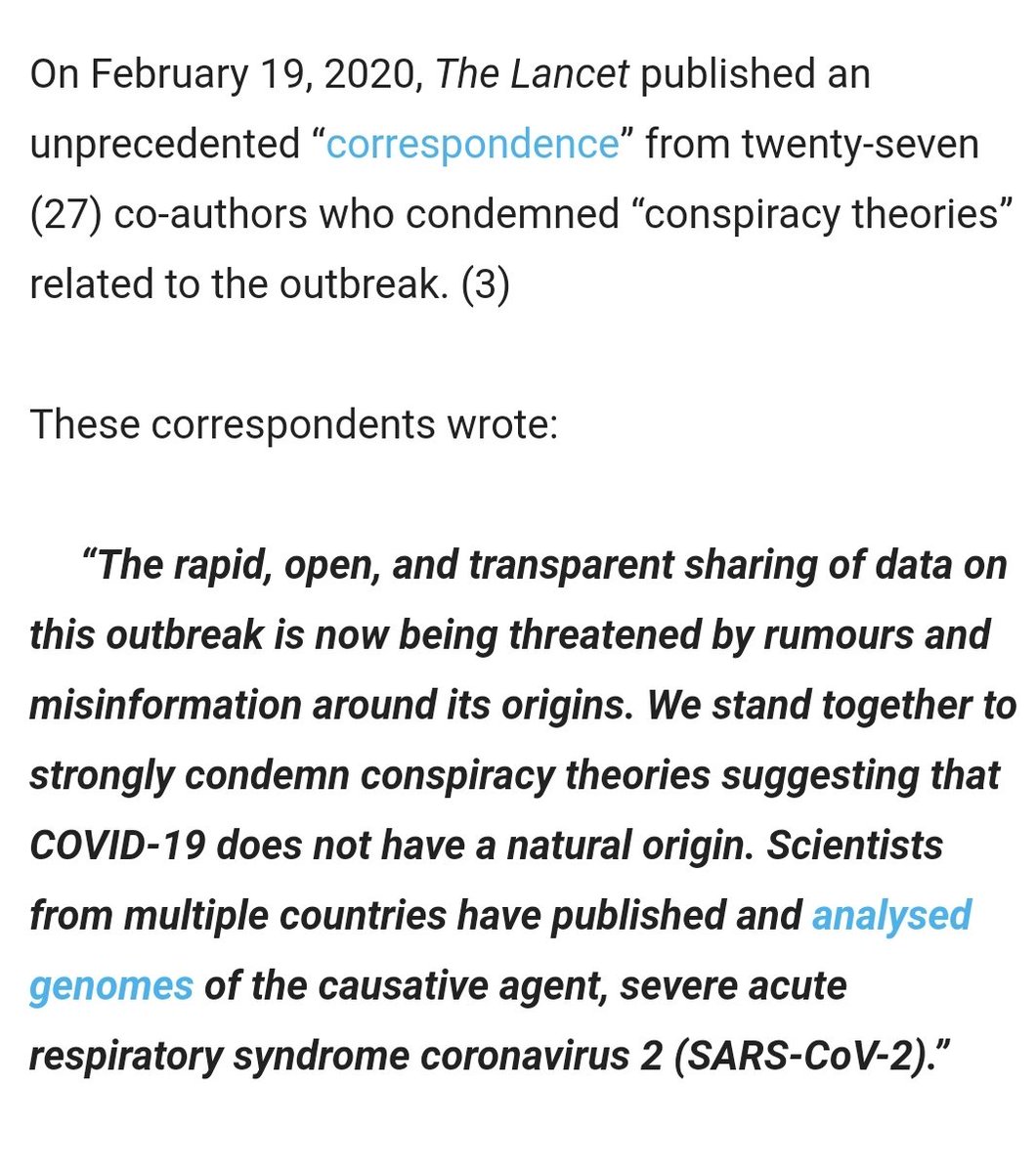
The Lancet writes that "Conspiracy theories do nothing but create fear, rumours, and prejudice...." #Covid_19 
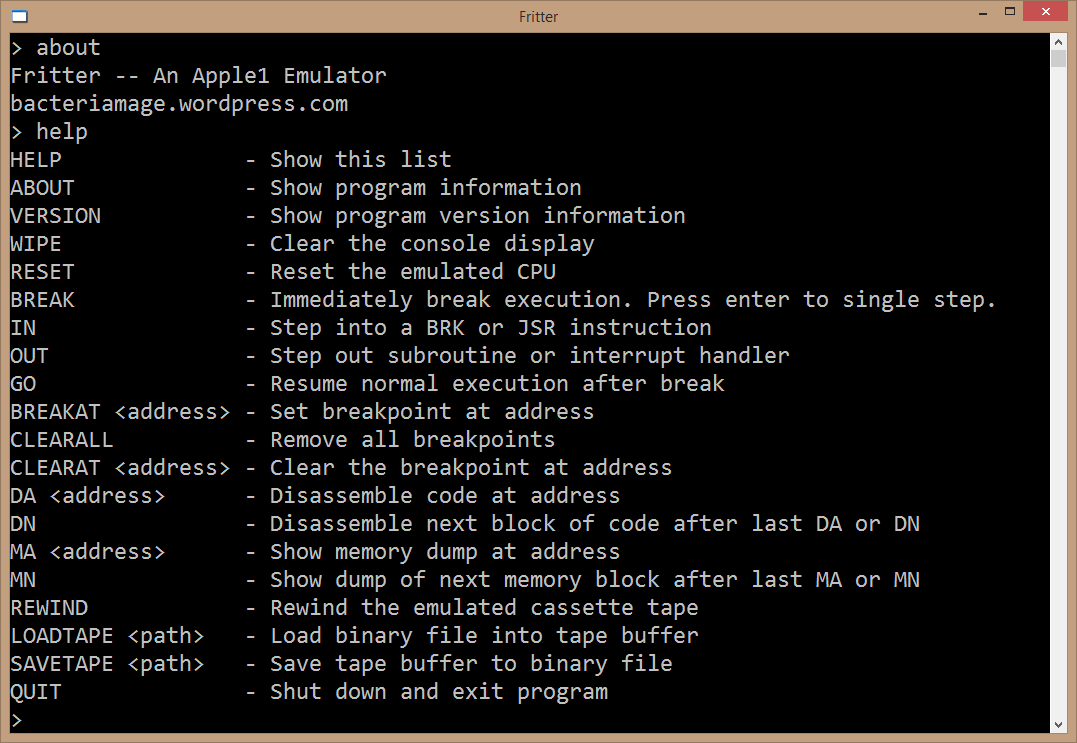
Recently I've gotten really interested in the #Apple1. The forerunner to the much better known Apple II and the machine that originally launched @Apple in 1970s.
Here are some of the more interesting points on my adventure. #Thread
Here are some of the more interesting points on my adventure. #Thread
It's such a simple machine that a minimally technical article I read earlier this year had enough details to write a simple #emulator.
Which I ended up doing; my very first attempt at creating one. #MOS6502
Here it is running @stevewoz's original 256-byte "monitor" firmware/OS.
Which I ended up doing; my very first attempt at creating one. #MOS6502
Here it is running @stevewoz's original 256-byte "monitor" firmware/OS.

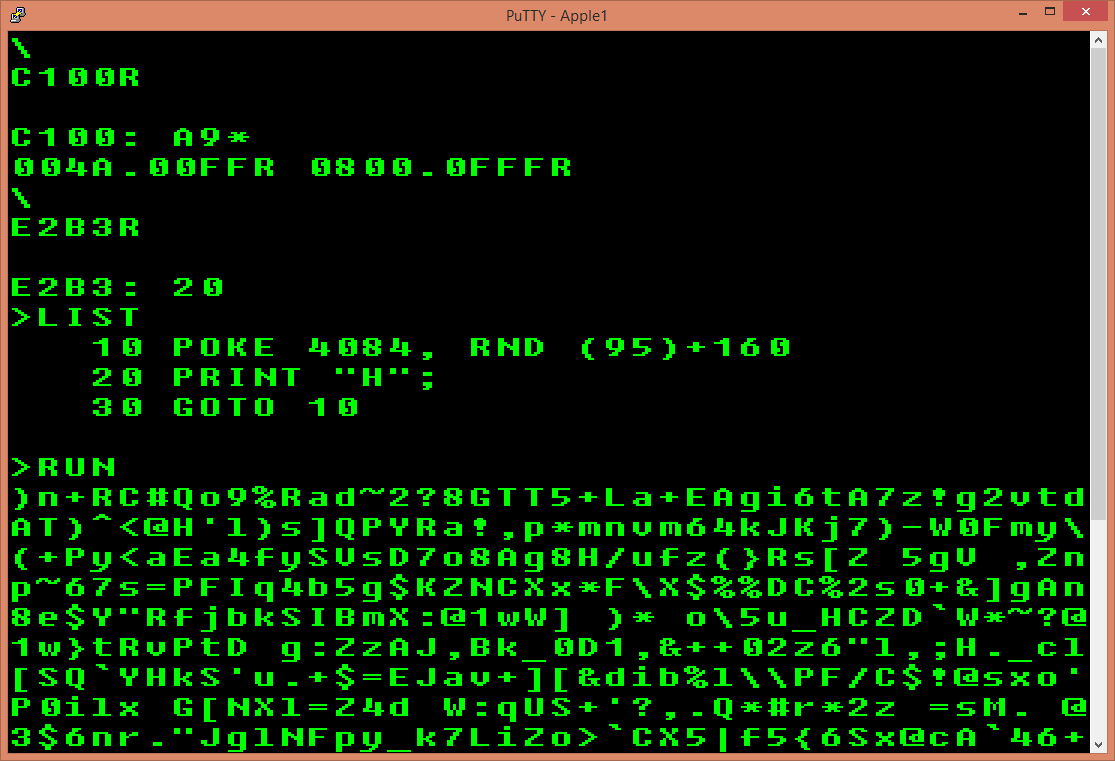
My emulator is just a console app with a command line to control the emulation.
The actual I/O text streams for the emulated machine are just pushed through a local socket connection.
#PuTTY works great as a front end.
A real Apple-1 would need a TV screen and keyboard.

The actual I/O text streams for the emulated machine are just pushed through a local socket connection.
#PuTTY works great as a front end.
A real Apple-1 would need a TV screen and keyboard.
So lately I've been working on some #DOS game #reverseengineering (preservation!). One of the targets I'm working on is "Fuzzy's World Of Miniature Space Golf" from "Pixel Painters", which is a game I played forever when I was a kid. mobygames.com/game/dos/fuzzy…
So far, I've managed to get the files unpacked (pretty easy) and animations extracted. Here is an example of the intro I've been able to decode (loops nicely!), although if you ever played the game you might notice there is something missing... (besides the speed being wrong)
The stars, of course! They are not part of the animation itself, but they are generated randomly every time the game starts. Not even the colors used by them are part of the palette, they get added after loading the image, which is really interesting.
I know I tweet alot about IDA. That's because I used to be an instructor, and realize how difficult it can be for new reversers to become accustomed to it (and to learn RE generally). But, owning IDA is not a barrier for entry into the RE community. #reverseengineering 1/5
There's tools like Ghidra, Radare, x64dbg, Windbg, gdb that are all free. Binary Ninja comes in at a much lower price point if you get a personal license. You can also download IDA Free, if you'd like to become more familiar with IDA. 2/5
The fact is reverse engineering is a process, and each of these tools facilitates that process in different ways, sometimes for the better, and sometimes not so much. If you give an experienced RE any one of these tools, given some spinup time, they'd still get the job done. 3/5
IDA's remote debugger is my go-to for debugging malware so that I never have to restore my VM and lose. If you're interested in trying it, I've attached some instructions on how to set it up to debug a DLL. (1/4) #malware #reverseengineering




