Discover and read the best of Twitter Threads about #Sysmon
Most recents (4)
#SecurityOnion 2.3.180 now available!
Featuring:
✅#Elastic 8.4.3
✅#Suricata 6.0.8
✅#Zeek 5.0.2
✅New and improved #sysmon dashboards!
Thanks to @markrussinovich and team for #sysmon!
Need a #sysmon config? Check out @SwiftOnSecurity's!
Blog post:
blog.securityonion.net/2022/10/securi…



Featuring:
✅#Elastic 8.4.3
✅#Suricata 6.0.8
✅#Zeek 5.0.2
✅New and improved #sysmon dashboards!
Thanks to @markrussinovich and team for #sysmon!
Need a #sysmon config? Check out @SwiftOnSecurity's!
Blog post:
blog.securityonion.net/2022/10/securi…




@markrussinovich @SwiftOnSecurity Our updated #Sysmon Overview dashboard gives you a nice overview of all of the different types of #Sysmon data you are collecting: 

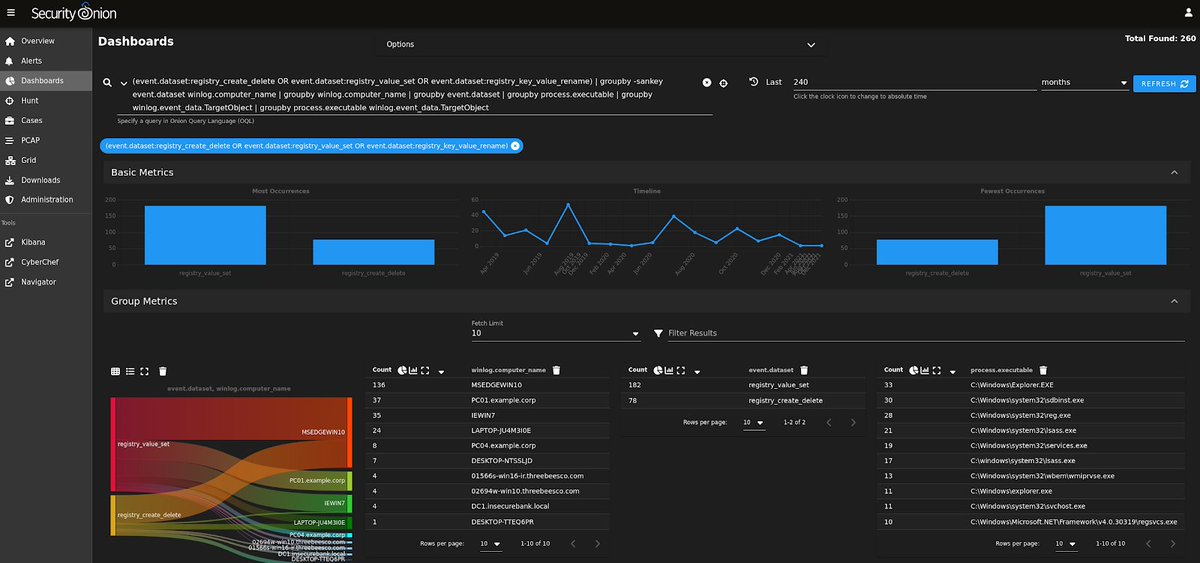
@markrussinovich @SwiftOnSecurity Our new #Sysmon Registry dashboard allows you to drill into registry events like registry_value_set and registry_create_delete: 
Spent some time today at work playing with @msftsecurity Windows InstallerFileTakeOver LPE (CVE-2021-41379 bypass - github.com/klinix5/Instal…) and managed to create some detections on it.
Detection will be based on Sysmon/SIEM, here we go... 1/n #threathunting #detection #dfir
Detection will be based on Sysmon/SIEM, here we go... 1/n #threathunting #detection #dfir
The exploit requires the user to overwrite elevation_service.exe with a compromised one (in this case with InstallerFileTakeOver.exe).
We can monitor this using #Sysmon event ID 11 - File Creation events:
We can monitor this using #Sysmon event ID 11 - File Creation events:
event_id:11 AND event_data.TargetFilename:*\\elevation_service.exe
How to detect software supply chain attacks with #Sysmon, #MicrosoftDefender, or any other #EDR:
1. You use specific software in your environment.
2. The software is usually installed on a few servers that have privileges across the environment.
1. You use specific software in your environment.
2. The software is usually installed on a few servers that have privileges across the environment.
3. You probably have a naming convention for your servers. Also, servers have defined IP subnets.
4. Your EDR or Sysmon has "Company" information in the process event or process network logs.
Combining all together:
4. Your EDR or Sysmon has "Company" information in the process event or process network logs.
Combining all together:
Without even knowing what kind of software is used in the environment, you can analyze your process event logs to see if your servers have a 3rd party software installed. The same logs provide the computer name and/or the computer IP.
Do you do Windows event log analysis? A round up of tips follows: #DFIR
If you manage Internet facing Windows boxes, here are 7 pages of post-compromise actions by RDP brute forcers: #DFIR
Use your infrastructure as a sensor. How to use Windows Event Forwarding:
