Discover and read the best of Twitter Threads about #dfir
Most recents (24)
Last year I analysed the police's responses in all the parliamentary committees on #forensic science. I produced a video I hoped would be useful if we ever have another parliamentary enquiry or if journalists decided to look into these issues again.
/1
/1
My goal was to show that the police responses are predictable and present a remarkably weak argument to justify their defunding of #forensic science. I hope the APPG ( fyi @ctmccartney) watch at least some of it before they question police witnesses and the FSR. /2
@ctmccartney As for us experts, everyone needs to start calling out their BS by countering it with real life examples. Please watch some of my long winded nonsense, you may find it useful when drafting your responses to the APPG. /3
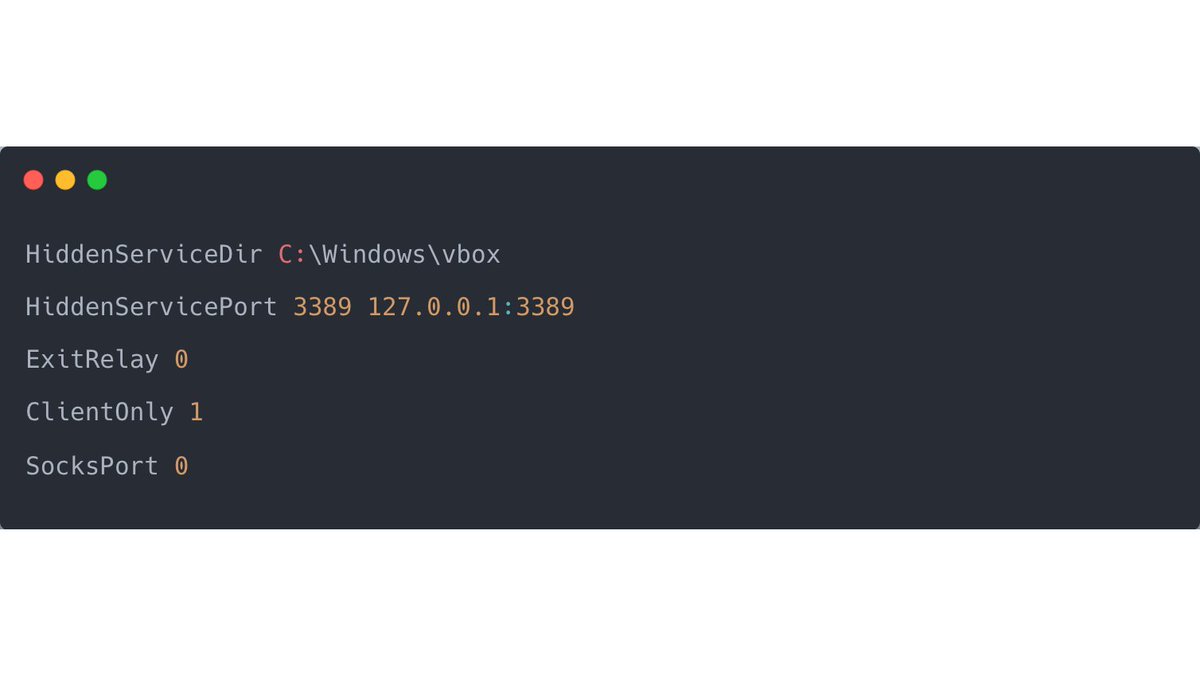
1/ The content below is from a file named install.bat and stems from a recent investigation where a TA launched this batch file. 👀
What's going on?
Well, VboxUpdate.exe is, in fact, tor.exe, and a new service is created, launching tor with a config file.
🧵 #CyberSecurity
What's going on?
Well, VboxUpdate.exe is, in fact, tor.exe, and a new service is created, launching tor with a config file.
🧵 #CyberSecurity

2/ Below is an excerpt from the content of config.txt; the configuration file passed as an argument to the tor service.
If you think this looks a lot like RDP Tunneling, you are absolutely right. 🥇
If you think this looks a lot like RDP Tunneling, you are absolutely right. 🥇
3/ Head over to the allthingsdfir blog to read a more profound write-up about the techniques used here and how they work together.
allthingsdfir.com/rdp-over-tor/
allthingsdfir.com/rdp-over-tor/
Sometimes I do threads about members of the OSINT-community. For example, you may have already read about @Sox0j or @rly0nheart.
Today I want to talk about 9 tools lists made by @SerScorza, #osint and #dfir specialist from Italy.
🧵🧵🧵
Today I want to talk about 9 tools lists made by @SerScorza, #osint and #dfir specialist from Italy.
🧵🧵🧵

There are many paths you could take with this scenario. At a high level, the big question you want to be answered is whether the user or an attacker set up the forwarding rule. But, you've got to ask other, more specific questions to figure that out. #InvestigationPath #DFIR
A lot of great responses this week so I won't rehash every path, but there's an opportunity to explore the disposition and prevalence of the client IP, the timing of the rule creation versus AD auth, potential outgoing spam activity,
A few folks pointed out the timing of the rule creation, which is undoubtedly significant. Was the rule created well before djenkins went on their trip? Right before? During it? Those timings all have different implications.
Grow your cybersecurity skills with this incredible collection of FREE learning resources.
⚡️ Get ready to level up!
Follow & share the 🧵
#infosec #cybersecurity #pentesting #bugbounty
#hacking #blueteam #redteam #technology #DataSecurity #CyberSec #Linux#soc #dfir
⚡️ Get ready to level up!
Follow & share the 🧵
#infosec #cybersecurity #pentesting #bugbounty
#hacking #blueteam #redteam #technology #DataSecurity #CyberSec #Linux#soc #dfir
For everyone who responded to this #DFIR question below. I gathered all your feedback and put it into a repository which can be found below. I'll continue to update with everything related. #DigitalForensics #AntiForensics
github.com/ashemery/Anit-…
github.com/ashemery/Anit-…
I will add what we already cover in our anti-forensics course already
JFYI, if you check my past publications, you'll notice I've covered so many of what have been mentioned here back in 2015/2016 ... but I want to see if I'm missing anything new and it turned out YES, there is one/two that I did now know. Thank you all for sharing, appreciate it.
During my last #DFIR training for 2022; I did many new video recording. Some have already been added to the #CCDFA course, while others will be added very soon. The course "currently" has 55+ hands-on labs, 50+ videos, and over 40 Q&As.
Why am I saying this? 1/3
Why am I saying this? 1/3
Because @cyber5w and @hexordia are both running a 30% discount on all #DFIR courses and training which ends tomorrow! Therefore, I highly recommend you take advantage of this discount and register for the #CCDFA course. 2/3
academy.cyber5w.com/courses/ccdfa-…
academy.cyber5w.com/courses/ccdfa-…

Check the syllabus below & you'll be surprised with what is covered in each section. Also, this is the only #DFIR course that we currently have that covers disks, volumes, and file system forensics (FAT+NTFS) #EOM
academy.cyber5w.com/courses/ccdfa-…
academy.cyber5w.com/courses/ccdfa-…
1/ #Azure In a recent case, the TA was able to compromise the user despite MFA (MFA fatigue).
After logging in, the attacker registered another mobile number as "Alternate Mobile Phone Call".
In the audit logs, we see this event within "Authentication Methods":
🧵 #DFIR
After logging in, the attacker registered another mobile number as "Alternate Mobile Phone Call".
In the audit logs, we see this event within "Authentication Methods":
🧵 #DFIR

#DFIR Android 13 is keeping track of when apps are launched and from where in the database “SimpleStorage” found in USERDATA/data/com.google.android.as/databases/. The table storing the info is “EchoAppLaunchMetrcisEvents” /1 

Columns of importance: timestampMillis, packageName, and launchLocationId. First two are self explanatory. The third provides what its name suggest: from where an app was launched. There are several numerical values in the column. /2
Observed values so far are:
1 - Home Screen
2 - Suggested Apps (bottom of Home Screen - New in Android 12)
4 - App Drawer
7 - Suggested Apps (top of App Drawer)
8 - Search (top of App Drawer or QuickSearchBox)
12 - Recent Apps/Multi-tasking
1000 - Notification
/3
1 - Home Screen
2 - Suggested Apps (bottom of Home Screen - New in Android 12)
4 - App Drawer
7 - Suggested Apps (top of App Drawer)
8 - Search (top of App Drawer or QuickSearchBox)
12 - Recent Apps/Multi-tasking
1000 - Notification
/3
In this Mega thread, you will find 10 FREE online courses with a certificate of completion from :
1 - ISC ²
2 - Cisco Academy
3 - Fortinet
4 - EC-Council
5 - AWS
#CyberSecurity #Cisco #AWS #dfir #infosec #infosecurity #threats #Python #100DaysOfHacking
1 - ISC ²
2 - Cisco Academy
3 - Fortinet
4 - EC-Council
5 - AWS
#CyberSecurity #Cisco #AWS #dfir #infosec #infosecurity #threats #Python #100DaysOfHacking
1⃣ Free Cybersecurity Training
- Information Security Awareness
- The Evolution of Cybersecurity
- NSE 2 Cloud Security
- NSE 2 Endpoint Security
- NSE 2 Threat Intelligence
- NSE 2 Security Information & Event Management
- Security Operations &
🖇️
training.fortinet.com
- Information Security Awareness
- The Evolution of Cybersecurity
- NSE 2 Cloud Security
- NSE 2 Endpoint Security
- NSE 2 Threat Intelligence
- NSE 2 Security Information & Event Management
- Security Operations &
🖇️
training.fortinet.com
2⃣ Introduction to Dark Web, Anonymity, and Cryptocurrency
Learn to access Dark Web, and Tor Browser and know about Bitcoin cryptocurrency
🖇️
codered.eccouncil.org/course/introdu…
Learn to access Dark Web, and Tor Browser and know about Bitcoin cryptocurrency
🖇️
codered.eccouncil.org/course/introdu…
At #IWCON2022, we have 15+ amazing #cybersecurity speakers from around the world 🌍
To share unique methods and findings with y’all 😍🙌
Get ready with your questions. Our experts will answer you live 🔥
Book your ticket: iwcon.live
Meet our speakers 🧵👇
To share unique methods and findings with y’all 😍🙌
Get ready with your questions. Our experts will answer you live 🔥
Book your ticket: iwcon.live
Meet our speakers 🧵👇

#1 Gabrielle Hempel @gabsmashh, #security engineer @Netwitness 🥳
Her topic: #Threat hunting in #cloud environments 🌩️
Time: 17th Dec, 7:30 pm IST
Want to attend this talk? 😍
Book your ticket here: iwcon.live
#cloudhunting #threathunting
Her topic: #Threat hunting in #cloud environments 🌩️
Time: 17th Dec, 7:30 pm IST
Want to attend this talk? 😍
Book your ticket here: iwcon.live
#cloudhunting #threathunting

#2 Luke Stephens @hakluke, founder of @haksecio 🔥
His topic: How I used #recon techniques to identify a prolific #scammer 👊
Time: 17th Dec, 6:30 pm IST ❤️
Don't wanna miss it?
Register today: iwcon.live
#infosec #hacking #hackingthehacker
His topic: How I used #recon techniques to identify a prolific #scammer 👊
Time: 17th Dec, 6:30 pm IST ❤️
Don't wanna miss it?
Register today: iwcon.live
#infosec #hacking #hackingthehacker

#IWCON2022 — The much-awaited virtual #Infosec conference is happening in a month 😍🙌
We have expert talks covering NINE major #security verticals🔥🔥
Join us & learn new skills before 2022 ends: iwcon.live 👊
Here are the session topics 🧵👇
We have expert talks covering NINE major #security verticals🔥🔥
Join us & learn new skills before 2022 ends: iwcon.live 👊
Here are the session topics 🧵👇

#1 Cloud Security:
1. #Threat #hunting in cloud environments by @gabsmashh (#security engineer @Netwitness)
2. #Hacking #cloud: for fun and profit by Dhiyaneshwaran B (#AppSec #researcher at @pdiscoveryio)
1. #Threat #hunting in cloud environments by @gabsmashh (#security engineer @Netwitness)
2. #Hacking #cloud: for fun and profit by Dhiyaneshwaran B (#AppSec #researcher at @pdiscoveryio)
#2 Bug Bounty:
1. My approach to accessing #admin panels by @hunter0x7 (admin pwner)
2. Reading #RFCs for #hacking by @securinti (head of #hackers @intigriti)
1. My approach to accessing #admin panels by @hunter0x7 (admin pwner)
2. Reading #RFCs for #hacking by @securinti (head of #hackers @intigriti)
#Qakbot Infection New TTPs 🚨
[+] Deliver ISO (T1204.002)
[+] DLL Search Order Hijacking (T1574.001)🔥
[+] Regsvr32 (T1218.010)
[+] Process Hollowing (T1055.012)
[+] Discovery (TA0007)
[+] Credentials from Web Browsers (T1555.003)
[+] Data from Local System (T1005)



[+] Deliver ISO (T1204.002)
[+] DLL Search Order Hijacking (T1574.001)🔥
[+] Regsvr32 (T1218.010)
[+] Process Hollowing (T1055.012)
[+] Discovery (TA0007)
[+] Credentials from Web Browsers (T1555.003)
[+] Data from Local System (T1005)


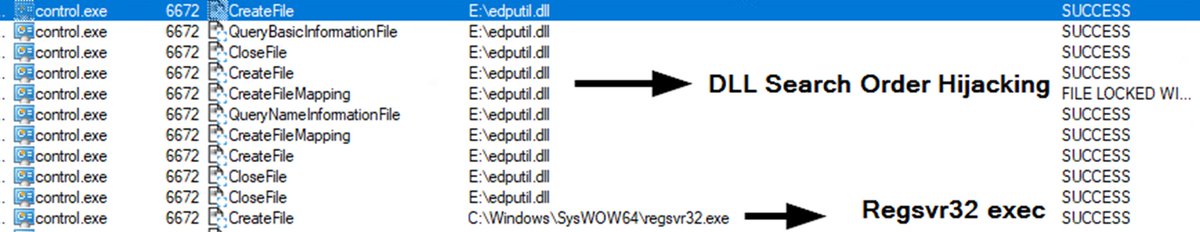

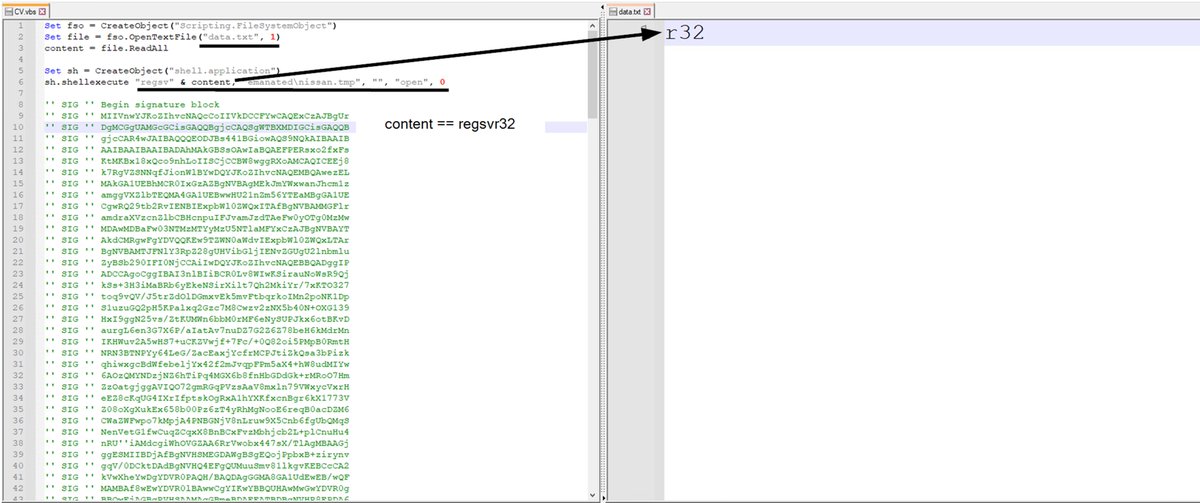
#Qakbot New TTPs IMG File Infection
[+] IMG File instead of ISO 🔥
[+] VBS Script (ShellExecute) instead of LNK 🔥
[+] .tmp (DLL loader) exec via Regsvr32.exe
[+] Process Injection
[+] Discovery commands
[+] C2 connection
#DFIR exec flow: img > vbs > tmp > injection


[+] IMG File instead of ISO 🔥
[+] VBS Script (ShellExecute) instead of LNK 🔥
[+] .tmp (DLL loader) exec via Regsvr32.exe
[+] Process Injection
[+] Discovery commands
[+] C2 connection
#DFIR exec flow: img > vbs > tmp > injection


#Qakbot C2 server:
IP: 70.121.198[.]103
Port: 2078
Artifact: POST /t5 HTTP/1.1
Additional C2 IPs:
200.93.14[.]206
174.115.87[.]57
102.157.73[.]215
98.30.233[.]14
94.70.37[.]145
82.31.37[.]241
172.90.139[.]138
IP: 70.121.198[.]103
Port: 2078
Artifact: POST /t5 HTTP/1.1
Additional C2 IPs:
200.93.14[.]206
174.115.87[.]57
102.157.73[.]215
98.30.233[.]14
94.70.37[.]145
82.31.37[.]241
172.90.139[.]138

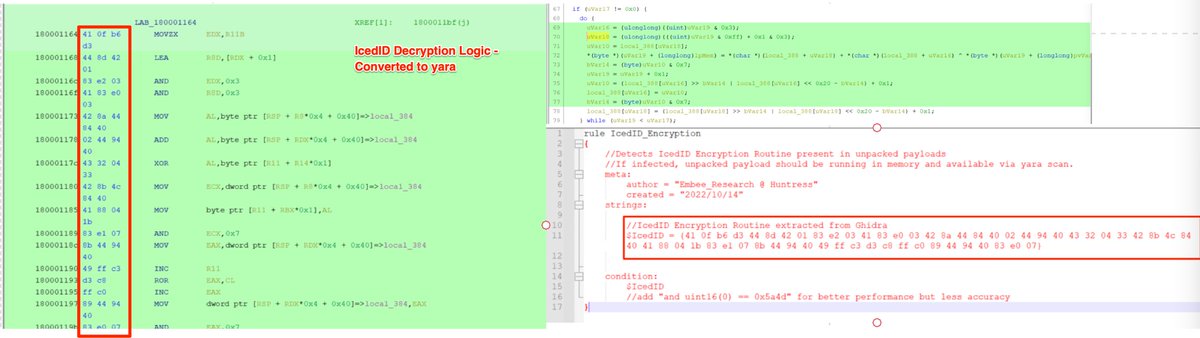
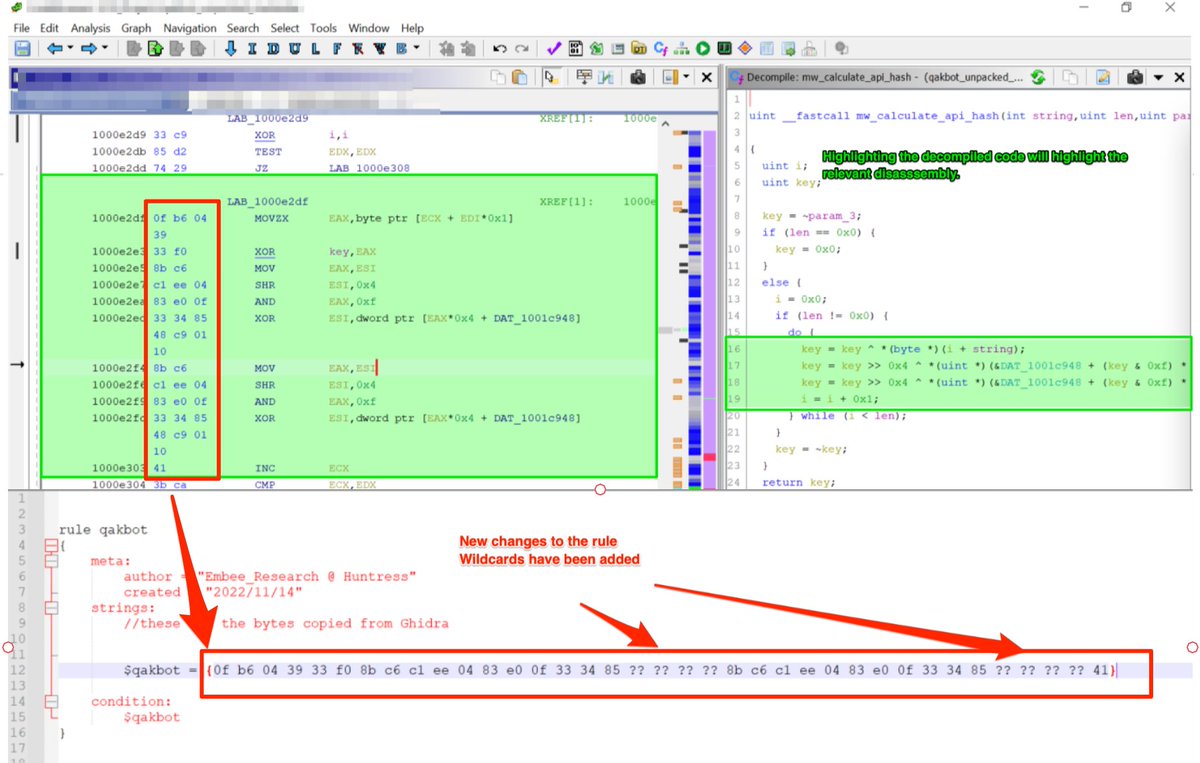
🐲 Ghidra Tips 🐲- Malware Encryption and Hashing functions often produce byte sequences that are great for #Yara rules.
Using #Ghidra and a Text Editor - You can quickly develop Yara rules to detect common malware families.
(Demonstrated with #Qakbot)
[1/20]
#Malware #RE



Using #Ghidra and a Text Editor - You can quickly develop Yara rules to detect common malware families.
(Demonstrated with #Qakbot)
[1/20]
#Malware #RE


[2/20]
Hashing and encryption functions make good targets for #detection as they are reasonably unique to each malware family and often contain lengthy and specific byte sequences due to the mathematical operations involved.
These characteristics make for good Yara rules 😁
Hashing and encryption functions make good targets for #detection as they are reasonably unique to each malware family and often contain lengthy and specific byte sequences due to the mathematical operations involved.
These characteristics make for good Yara rules 😁
[3/20] The biggest challenge is locating the functions responsible for hashing and encryption. I'll leave that for another thread, but for now...
You can typically recognize hashing/encryption through the use of bitwise operators inside a loop. (xor ^ and shift >> etc).
You can typically recognize hashing/encryption through the use of bitwise operators inside a loop. (xor ^ and shift >> etc).
🦖Day 37 of the @velocidex #velociraptor #ArtifactsOfAutumn series
Artifact: Exchange[.]Windows[.]Detection[.]ISOMount
Author: @ConorQuinn92
Link: docs.velociraptor.app/exchange/artif…
Artifact: Exchange[.]Windows[.]Detection[.]ISOMount
Author: @ConorQuinn92
Link: docs.velociraptor.app/exchange/artif…
After Microsoft decided to block Office macros by default, threat actors began pivoting to a usage of container files such as .iso, .rar, and .lnk files for malware distribution.
This is because TAs can then bypass the "Mark of the web" restrictions for downloaded files.
This is because TAs can then bypass the "Mark of the web" restrictions for downloaded files.
When downloaded, container files will have the MOTW attribute because they were downloaded from the internet. However, the document inside, such as a macro-enabled spreadsheet, will not.
🦖Day 36 of the @velocidex #velociraptor #ArtifactsOfAutumn series
Artifact: MacOS[.]System[.]QuarantineEvents
Link: docs.velociraptor.app/artifact_refer…
Artifact: MacOS[.]System[.]QuarantineEvents
Link: docs.velociraptor.app/artifact_refer…

This artifact parses the 'com[.]apple.LaunchServices.QuarantineEventsV2' sqlite database to provide defenders with information around files that have been downloaded from the internet.
Information includes:
- DL Time
- DL URL
- Origin
- Agent Name/Bundle
- User
- Event UUID
Information includes:
- DL Time
- DL URL
- Origin
- Agent Name/Bundle
- User
- Event UUID
1\ #DFIR: Chrome Forensics - How to Recover CLEARED History
If a user just cleared their browser history, you can still recover everything they were just looking at from the session files:
%appdata%\Local\Google\Chrome\User Data\Default\Sessions
inversecos.com/2022/10/recove…
If a user just cleared their browser history, you can still recover everything they were just looking at from the session files:
%appdata%\Local\Google\Chrome\User Data\Default\Sessions
inversecos.com/2022/10/recove…

1\ #DFIR: How to investigate insider threats
Sharing the forensic methodology I follow when I'm investigating insiders 😍
This is where an employee sells creds/changes configs/runs malware leading to full DA compromise and then say they didn't do it O_o
inversecos.com/2022/10/how-to…
Sharing the forensic methodology I follow when I'm investigating insiders 😍
This is where an employee sells creds/changes configs/runs malware leading to full DA compromise and then say they didn't do it O_o
inversecos.com/2022/10/how-to…

2\ The questions that I use to guide the analysis and prioritisation of analysis are:
1. How was the device accessed around the suspected behaviour?
2. Where was the user/device when this occurred?
3. Was the insider active on their system?
4. What did the user do?
1. How was the device accessed around the suspected behaviour?
2. Where was the user/device when this occurred?
3. Was the insider active on their system?
4. What did the user do?
3\ To answer the first question, I look at SRUM, specifically the App Timeline Provider details.
I pull:
> Execution time of the malicious thingz
> Duration of execution
> User SID
Then, I cross correlate that user info with their corresponding ActivitiesCache.db. #DFIRISS3XY
I pull:
> Execution time of the malicious thingz
> Duration of execution
> User SID
Then, I cross correlate that user info with their corresponding ActivitiesCache.db. #DFIRISS3XY

🦖Day 14 of the @velocidex #velociraptor #ArtifactsOfAutumn series
Artifact: 'Windows[.]Detection[.]BinaryRename'
Author: @mgreen27
Link: docs.velociraptor.app/exchange/artif…
Artifact: 'Windows[.]Detection[.]BinaryRename'
Author: @mgreen27
Link: docs.velociraptor.app/exchange/artif…

This artifact will detect renamed binaries commonly abused by adversaries.
Renaming binaries is a defense evasion technique used to bypass brittle process name and path-based detections. It is used by many actors/groups, including from commodity malware and nation states.
Renaming binaries is a defense evasion technique used to bypass brittle process name and path-based detections. It is used by many actors/groups, including from commodity malware and nation states.
I wanted to share some findings about RDP, Network Layer Authentication, LogonTypes and brute forcing 🔭
Recently, we perused some EventID 4625s (login failures) originating from public IPv4s brute forcing...
🧵
Recently, we perused some EventID 4625s (login failures) originating from public IPv4s brute forcing...
🧵

I kept finding LogonType 3s (network)
However only RDP was externally exposed on the machine, which usually records LogonType 10....
When this has happened before, I usually just assume its Windows jank and continue with my investigation 🤷♂️
But this time, I wanted to know WHY
However only RDP was externally exposed on the machine, which usually records LogonType 10....
When this has happened before, I usually just assume its Windows jank and continue with my investigation 🤷♂️
But this time, I wanted to know WHY

The wise @DaveKleinatland suggested Network Layer Authentication (NLA) would explain this:
"
NLA takes place before the session is started... without NLA things can be exposed before any sort of authentication.... like domain name, usernames, last logged on user, etc
"
- Dave 🧙♂️
"
NLA takes place before the session is started... without NLA things can be exposed before any sort of authentication.... like domain name, usernames, last logged on user, etc
"
- Dave 🧙♂️
🔔I published a new script to parse the log of #AppLocker🔒 , which I called Get-AppLockerEventlog.ps1
It compiles all the useful data needed in #threathunting and #DFIR
You can find the script and the documentation here:
👉github.com/RomaissaAdjail…
It compiles all the useful data needed in #threathunting and #DFIR
You can find the script and the documentation here:
👉github.com/RomaissaAdjail…

1\ #DFIR: How to detect Linux Timestomping
Analyse the entries in these two files:
> filesystem.db
> filesystem.db-wal
Most writeups focus on detecting the use of "touch". But you can timestomp without using "touch". 😈
Check out my blog below 👇
inversecos.com/2022/08/detect…
Analyse the entries in these two files:
> filesystem.db
> filesystem.db-wal
Most writeups focus on detecting the use of "touch". But you can timestomp without using "touch". 😈
Check out my blog below 👇
inversecos.com/2022/08/detect…
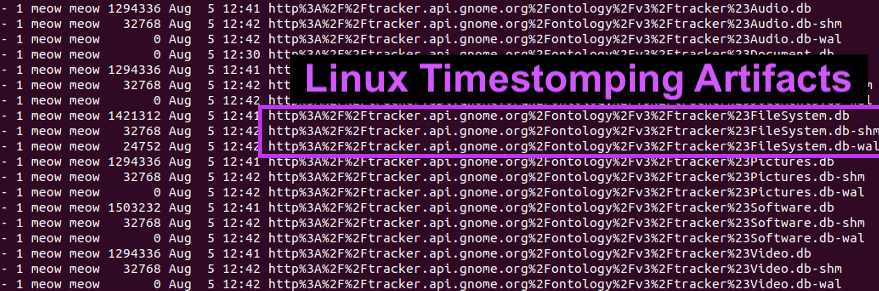
2\ The file "filesystem.db" (enabled by default) tracks:
> fileCreated time
> fileLastAccessed time
Look for discrepancies in the fileCreated time in this DB file vs the times that "stat" show on a file.
There's also a correlating WAL that contains uncommitted data :3
> fileCreated time
> fileLastAccessed time
Look for discrepancies in the fileCreated time in this DB file vs the times that "stat" show on a file.
There's also a correlating WAL that contains uncommitted data :3
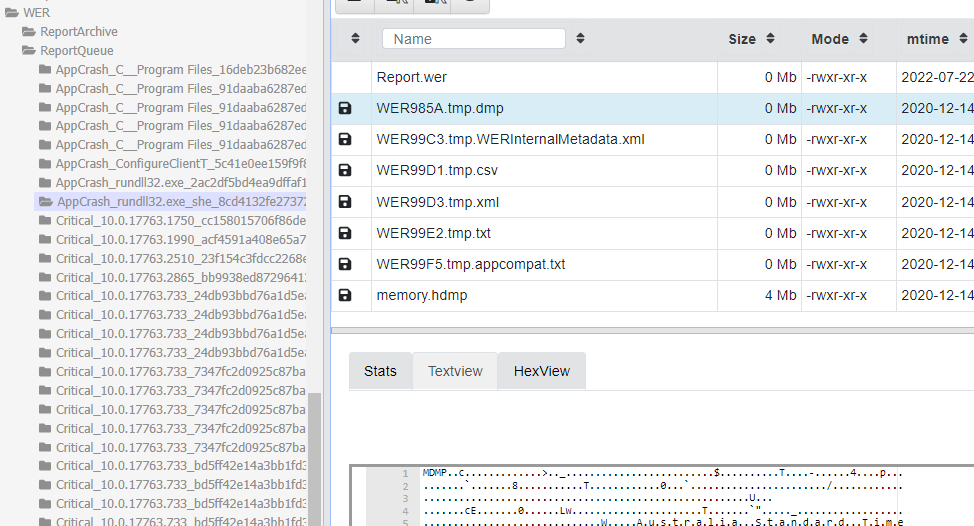
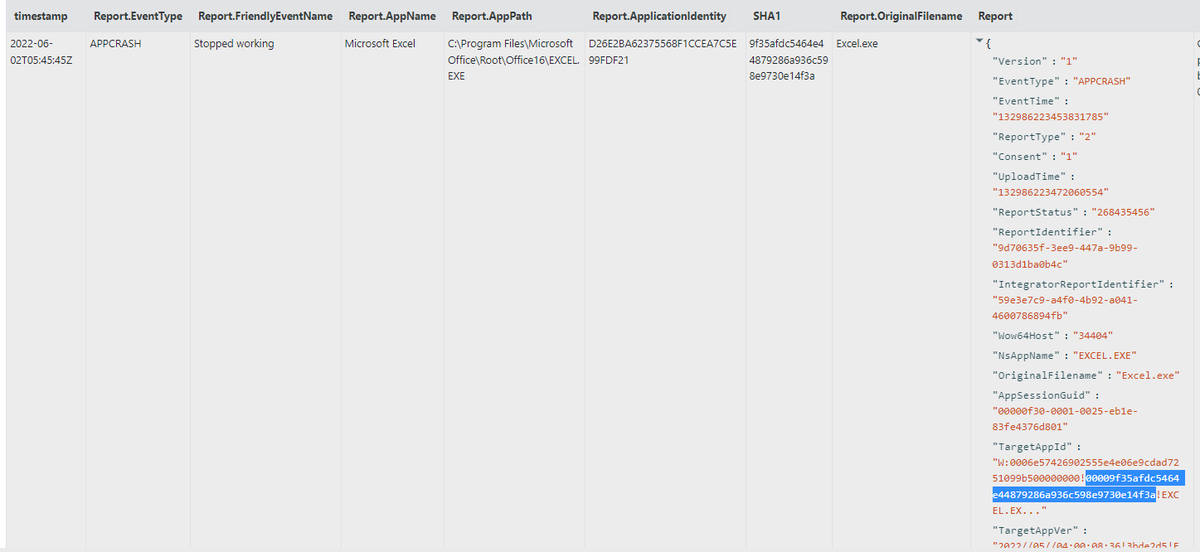
1/ Windows Error Reporting (WER) can provide investigators with a wealth of data including:
• SHA1 hashes of crashed processes
• Snapshot of process trees at time of crash
• Loaded modules of crash
• Process minidumps
#DFIR #Threathunting
See 🧵 for new #Velociraptor artefact
• SHA1 hashes of crashed processes
• Snapshot of process trees at time of crash
• Loaded modules of crash
• Process minidumps
#DFIR #Threathunting
See 🧵 for new #Velociraptor artefact