Discover and read the best of Twitter Threads about #Velociraptor
Most recents (20)
1/ I used #AutoRuns v14.09 (GUI) in my lab setup but noticed that it failed to find (or display) the malware in the Startup folder, although the file is there (screenshot below).
I checked back and forth, searched manually for the file, and restarted the OS and AutoRuns.
🧵
I checked back and forth, searched manually for the file, and restarted the OS and AutoRuns.
🧵

2/ With #Velociraptor, I ran the hunt Sysinternals.Autoruns, and with the CLI version of AutoRuns, the malware is found in the Startup folder. 

1/ Do you monitor newly created services within your environment, and would you notice when a (vulnerable) driver is loaded?
The screenshot below (#Velociraptor 🤩) is from a recent #XMRig CoinMiner investigation ⤵️
🧵 #CyberSecurity
The screenshot below (#Velociraptor 🤩) is from a recent #XMRig CoinMiner investigation ⤵️
🧵 #CyberSecurity

2/ We talked about vulnerable drivers before:
3/ And here:
1/ #Velociraptor has covered hunting for malicious WMI Event Consumers for some time. [1]
However, Velociraptor does not provide an eradication hunt for malicious WMI Event Consumers out of the box.
🧵 #CyberSecurity
However, Velociraptor does not provide an eradication hunt for malicious WMI Event Consumers out of the box.
🧵 #CyberSecurity
2/ @threatpunter wrote a detailed blog about WMI persistences and how to remove them.
"The simplest method to remove the entry from the WMI database is to use Autoruns. Launch Autoruns as an administrator and select the WMI tab to review WMI-related persistence." ✂️
"The simplest method to remove the entry from the WMI database is to use Autoruns. Launch Autoruns as an administrator and select the WMI tab to review WMI-related persistence." ✂️

1.Zeek: zeek.org : monitorea y analiza el tráfico de red en tiempo real, captura paquetes, registra eventos y genera alertas de actividad sospechosa. Ampliamente utilizado en la industria y en la investigación académica. #Zeek #seguridad #red
2.ClamAV: clamav.net :detectar y eliminar virus, malware y otras amenazas en archivos y mensajes de correo electrónico. Se utiliza a menudo en servidores de correo y sistemas de red para proteger contra amenazas de seguridad.#ClamAV #virus #seguridad #malware
🦖Day 69 of the @velocidex #velociraptor #ArtifactsOfAutumn series
Artifact: Exchange[.]MacOS[.]Applications[.]NetworkUsage
Link: docs.velociraptor.app/exchange/artif…
Artifact: Exchange[.]MacOS[.]Applications[.]NetworkUsage
Link: docs.velociraptor.app/exchange/artif…

If an unknown application, or an application that doesn't typically communicate over the network at all suddenly shows signs of large amount of inbound our outbound traffic, it can be considered suspicious.
Similarly, deviations from normal patterns of communication from typical network-connected programs can also be considered suspicious.
🦖Day 68 of the @velocidex #velociraptor #ArtifactsOfAutumn series
Artifact: Linux[.]Sys[.]JournalCtl
Link: docs.velociraptor.app/exchange/artif…
Artifact: Linux[.]Sys[.]JournalCtl
Link: docs.velociraptor.app/exchange/artif…

This artifact parses the output of the 'journalctl' command. It is used to view systemd logs on a Linux host.
These logs can contain valuable information to incident responders, such as hardware events, kernel messages, network connectivity, service status, and user events.
These logs can contain valuable information to incident responders, such as hardware events, kernel messages, network connectivity, service status, and user events.

Information provided by this artifact includes:
- Timestamp
- Message
- Boot ID
- Machine ID (h)
- Cursor
- Syslog facility/priority (h)
- Monotonic timestamp (h)
- Transport (h)
*h -> column is hidden from the output by default, and can be viewed with the column selector.
- Timestamp
- Message
- Boot ID
- Machine ID (h)
- Cursor
- Syslog facility/priority (h)
- Monotonic timestamp (h)
- Transport (h)
*h -> column is hidden from the output by default, and can be viewed with the column selector.
🦖Day 67 of the @velocidex #velociraptor #ArtifactsOfAutumn series
Artifact: Windows[.]Forensics[.]RecycleBin
Author: @svch0st
Link: docs.velociraptor.app/artifact_refer…
Artifact: Windows[.]Forensics[.]RecycleBin
Author: @svch0st
Link: docs.velociraptor.app/artifact_refer…

This artifact parses the $I files found in the Windows Recycle Bin folder ($Recycle.Bin, as of Windows Vista) to obtain the time of deletion and the original path and file name.
This folder contains:
- $I files ("Recycled" file metadata)
- $R files (the original data)
This folder contains:
- $I files ("Recycled" file metadata)
- $R files (the original data)
The contents of the Recycle Bin directory are organized by SID ('C:\$Recycle.Bin\%SID%\').
It's important to note that this artifact uses the API to read available $I data. There may be additional unallocated but readable $I files referenced in the MFT that may be recoverable.
It's important to note that this artifact uses the API to read available $I data. There may be additional unallocated but readable $I files referenced in the MFT that may be recoverable.
🦖Day 66 of the @velocidex #velociraptor #ArtifactsOfAutumn series
Artifact: Server[.]Orgs[.]NewOrg
Link: docs.velociraptor.app/artifact_refer…
Artifact: Server[.]Orgs[.]NewOrg
Link: docs.velociraptor.app/artifact_refer…

With support for multi-tenancy added to Velociraptor in version 0.6.6, we can now manage multiple organizations within a single Velociraptor deployment!
🦖Day 38 of the @velocidex #velociraptor #ArtifactsOfAutumn series
Artifact: Linux[.]Sys[.]Pslist
Link: docs.velociraptor.app/artifact_refer…
Artifact: Linux[.]Sys[.]Pslist
Link: docs.velociraptor.app/artifact_refer…

This artifact enumerates the running processes on a Linux system. This can be useful to check for proper configuration or misalignment across a fleet of hosts, or for identifying suspicious processes generated by, or leveraged by malware.
Some of the Information provided by the artifact:
- Process ID
- Parent process ID
- Command line
- Executable
- Hash
- Username
- Created time
- RSS (how much memory allocated to the process)
- Process ID
- Parent process ID
- Command line
- Executable
- Hash
- Username
- Created time
- RSS (how much memory allocated to the process)
🦖Day 37 of the @velocidex #velociraptor #ArtifactsOfAutumn series
Artifact: Exchange[.]Windows[.]Detection[.]ISOMount
Author: @ConorQuinn92
Link: docs.velociraptor.app/exchange/artif…
Artifact: Exchange[.]Windows[.]Detection[.]ISOMount
Author: @ConorQuinn92
Link: docs.velociraptor.app/exchange/artif…
After Microsoft decided to block Office macros by default, threat actors began pivoting to a usage of container files such as .iso, .rar, and .lnk files for malware distribution.
This is because TAs can then bypass the "Mark of the web" restrictions for downloaded files.
This is because TAs can then bypass the "Mark of the web" restrictions for downloaded files.
When downloaded, container files will have the MOTW attribute because they were downloaded from the internet. However, the document inside, such as a macro-enabled spreadsheet, will not.
🦖Day 36 of the @velocidex #velociraptor #ArtifactsOfAutumn series
Artifact: MacOS[.]System[.]QuarantineEvents
Link: docs.velociraptor.app/artifact_refer…
Artifact: MacOS[.]System[.]QuarantineEvents
Link: docs.velociraptor.app/artifact_refer…

This artifact parses the 'com[.]apple.LaunchServices.QuarantineEventsV2' sqlite database to provide defenders with information around files that have been downloaded from the internet.
Information includes:
- DL Time
- DL URL
- Origin
- Agent Name/Bundle
- User
- Event UUID
Information includes:
- DL Time
- DL URL
- Origin
- Agent Name/Bundle
- User
- Event UUID
🦖Day 14 of the @velocidex #velociraptor #ArtifactsOfAutumn series
Artifact: 'Windows[.]Detection[.]BinaryRename'
Author: @mgreen27
Link: docs.velociraptor.app/exchange/artif…
Artifact: 'Windows[.]Detection[.]BinaryRename'
Author: @mgreen27
Link: docs.velociraptor.app/exchange/artif…

This artifact will detect renamed binaries commonly abused by adversaries.
Renaming binaries is a defense evasion technique used to bypass brittle process name and path-based detections. It is used by many actors/groups, including from commodity malware and nation states.
Renaming binaries is a defense evasion technique used to bypass brittle process name and path-based detections. It is used by many actors/groups, including from commodity malware and nation states.
🦖Day 4 of the @velocidex #velociraptor #ArtifactsOfAutumn series
Artifact: 'Windows.System.Services'
Link: docs.velociraptor.app/artifact_refer…
Artifact: 'Windows.System.Services'
Link: docs.velociraptor.app/artifact_refer…

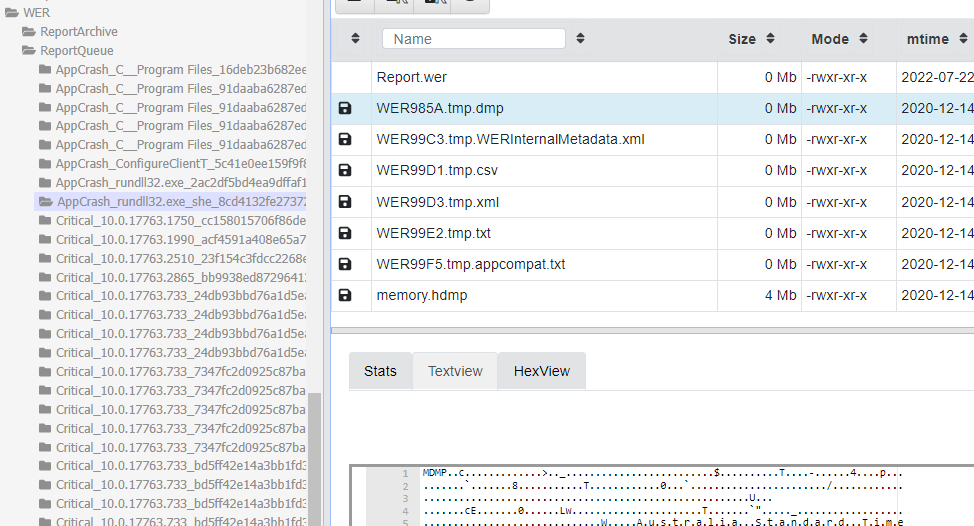
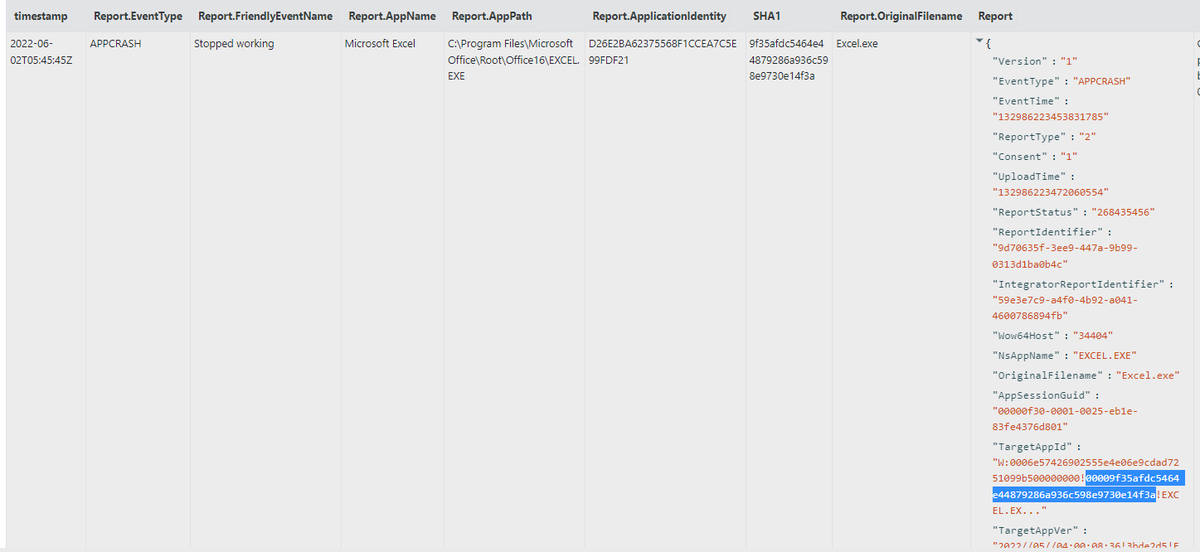
1/ Windows Error Reporting (WER) can provide investigators with a wealth of data including:
• SHA1 hashes of crashed processes
• Snapshot of process trees at time of crash
• Loaded modules of crash
• Process minidumps
#DFIR #Threathunting
See 🧵 for new #Velociraptor artefact
• SHA1 hashes of crashed processes
• Snapshot of process trees at time of crash
• Loaded modules of crash
• Process minidumps
#DFIR #Threathunting
See 🧵 for new #Velociraptor artefact

Welcome to the 5th and final of my #PrehistoricPlanet threads in which I talk about the science and background to what we showed in this new @AppleTVPlus @bbcstudios production. This time we look at EP 5: FORESTS… #dinosaurs #Cretaceous 





I was lead scientific consultant on #PrehistoricPlanet and was extensively involved in our many decisions, all of which were science-led or scientifically informed. I was, of course, merely one among many in a HUGE team that involved hundreds of very talented people!
Ep 5 focuses on the #dinosaurs and #pterosaurs that lived in forests during the Maastrichtian (the final part of the Late #Cretaceous). The Maastrichtian world was heavily forested, with temperate, subtropical & tropical woodland covering around 78% of the land surface…
Ok, here we go on a thread relating to the science and decisions behind ep 3 (FRESHWATER) of #PrehistoricPlanet , our new @AppleTVPlus @bbcstudios series devoted to Late #Cretaceous life. Here we go... #dinosaurs #pterosaurs #plesiosaurs #frogs 



Freshwater kicks off in north-east Asia (a location consistent with the geology, climate and animals we show) with a spectacular waterfall connected to canyons. Juvenile #pterosaurs - they're young #azhdarchids - have gathered here to roost... #PrehistoricPlanet 

We know essentially nothing of the roosting or resting habits of #azhdarchids but see it as likely that they would have gathered in numbers (fossil evidence does show that they were social) in places that predators couldn't easily get to. Hat-tip to discussion with @MarkWitton ..
Join me in this thread as I talk about the science and decisions behind what we show in ep 2 - DESERTS - of the new @AppleTVPlus @bbcstudios series #PrehistoricPlanet . Deserts aired on Tuesday, but better late than never. Here we go... 

Deserts kicks off in western South America on an arid plain where a mass gathering of the giant #titanosaur #Dreadnoughtus have gathered to display and compete for mates. Dreadnoughtus, from Argentina, was named in 2014 by @kenlacovara [shown in photo!] and colleagues... 



The idea that sauropods might have gathered and competed is based on behaviour seen in modern birds, mammals and other animals. Remember that events like this MUST have happened in the past, as they do today...
El mononykus de #PrehistoricPlanet 😍
Bonsoir ! 👋 Merci encore pour vos nombreux retours enthousiastes & partages, hier. 😊💚 Aujourd'hui, on va parler des #compétences requises, des #contraintes & #avantages du métier (d'où la photo ci-dessous, vous allez comprendre) !
🔽🔽🔽 #sciart #scicom
🔽🔽🔽 #sciart #scicom

On a déjà vu ces derniers jours que certaines compétences techniques sont requises dans mon métier : maîtrise des outils de création, veille #naturaliste, entraînement régulier, etc. 🖌️ 

Mais le métier d'#illustrateur·rice #scientifique réclame bien d'autres compétences que ce qu'on appelle trivialement "savoir #dessiner".
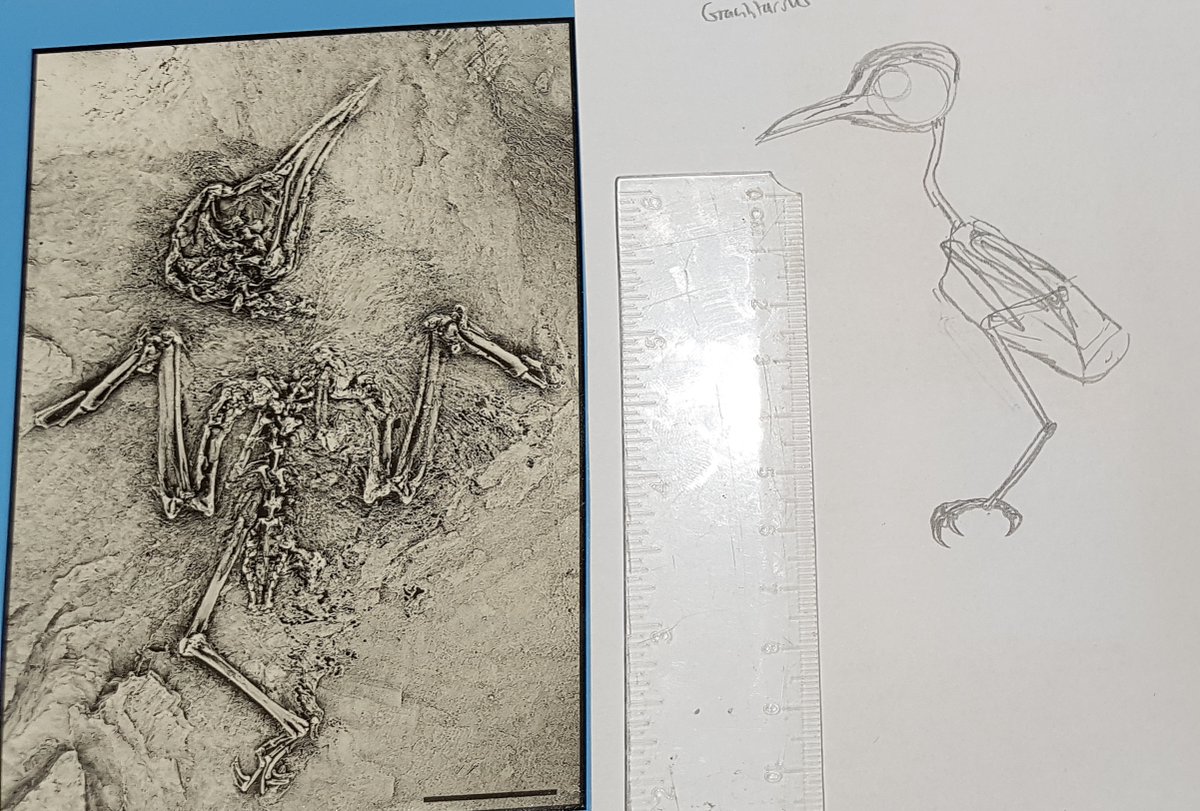
At this point, I've reconstructed about a million fossil birds (and other vertebrates) and it pains me that this stuff is sitting in my files, UNPUBLISHED. It's because I >>can't<< make time to finish my textbook, not yet anyway. Let's talk about Paleogene birds. So.... (thread) 

How do you reconstruct Paleogene #birds? The good news is that some of the relevant taxa - eg, those from Messel - are known from articulated skeletons, sometimes with plumage preserved and even feather patterns and melanosomes revealing colour... [pic Gerald Mayr/Volker Wilde]