Discover and read the best of Twitter Threads about #appsec
Most recents (24)
I never rely on automation alone.
In a recent external pentest, I was going over the assets manually, while running some tools in the background, including nuclei.
In a recent external pentest, I was going over the assets manually, while running some tools in the background, including nuclei.
1. One instance was running a software vulnerable to arbitrary file deletion. Nuclei didn't even smell it, unfortunately.
What I usually do, is to look over famous exploits for the specific software. And this one was a victim.
What I usually do, is to look over famous exploits for the specific software. And this one was a victim.
2. Another instance was running a software vulnerable to RCE. Thanks @infosec_au for the amazing work that help uncover this.
Nuclei has some templates for this, but they didn't catch it.
Similar to #1, I dug deeper manually and confirmed the vulnerabilty.
Nuclei has some templates for this, but they didn't catch it.
Similar to #1, I dug deeper manually and confirmed the vulnerabilty.
I just checked a thread today on API endpoints vulnerability and it got me thinking on how Developers take #appsec for granted. Here are some ways to implement best practices for reducing vulnerabilities in API endpoints in your Android application using Firebase.
1. Use HTTPS: Make sure that all your API endpoint URLs use the HTTPS protocol instead of HTTP. You can ensure this by using the https prefix when accessing Firebase API endpoints.
2. Validate user input: When reading or writing data to Firebase, make sure to validate and sanitize all user input before sending it to the server. For example, use TextUtils to check if input strings are empty or Pattern to validate input against a regular expression.
🚨Security Career Resource Thread 🚨
1️⃣ 2️⃣ resources to break into the field or take your career to the next level 👇
#infosec #cybersecurity #security
1️⃣ 2️⃣ resources to break into the field or take your career to the next level 👇
#infosec #cybersecurity #security
Learn:
🎓 How to get into various fields: pentesting, SOC analyst, AppSec, ...
🎫 Certs - do they matter? For which roles?
🧪 Doing security research
📣 Building your brand via blog posts, conference talks, and more
💸 How to think about compensation
🎓 How to get into various fields: pentesting, SOC analyst, AppSec, ...
🎫 Certs - do they matter? For which roles?
🧪 Doing security research
📣 Building your brand via blog posts, conference talks, and more
💸 How to think about compensation
📺 Launch your cybersecurity career: @IppSec's advice on how to become a skilled professional
* Technical tips
* Keeping a positive mindset
* Life is what you make it
#bugbounty #bugbountytips
* Technical tips
* Keeping a positive mindset
* Life is what you make it
#bugbounty #bugbountytips
As much as I love automation in recon, 98% of the findings in my pentests have nothing to do with it. Why? 👇
1. Inspired by @NahamSec recent video.
First, in a large majority of the web pentests, clients want me to focus only on their app and it's features. So, there's no need for subdomain enumeration/bruteforcing or any other large recon tactic.
First, in a large majority of the web pentests, clients want me to focus only on their app and it's features. So, there's no need for subdomain enumeration/bruteforcing or any other large recon tactic.
2. This doesn't mean that I don't use automation. I automate some of the boring and repetitive tasks via bash and python.
More practice, less theory (but not 0 theory)
In the past, I criticized Top 1% THM who know close to nothing about the real-world aspects of a pentest.
My point was not understood and I got a lot of hate for it.
In the past, I criticized Top 1% THM who know close to nothing about the real-world aspects of a pentest.
My point was not understood and I got a lot of hate for it.

1. Again, there's less value in being Top 1% if your experience is purely theoretical.
Yet, you will go way further if you complement your experience (from day-to-day work in cybersecurity) with continuous practice on THM and other platforms (focusing on non-CTFish materials).
Yet, you will go way further if you complement your experience (from day-to-day work in cybersecurity) with continuous practice on THM and other platforms (focusing on non-CTFish materials).
2. If you're not working in cybersecurity yet, but you want to, no problem.
Get your daily real-world experience from VDPs (and not paid bounties).
Get your daily real-world experience from VDPs (and not paid bounties).
1. Subscribe to my free newsletter. At cristivlad.substack.com.
2. Like and retweet this post (the top post of the thread).
SSRF via PDF? Now made easy.
(thread)
(thread)
1. Go to @jonasl github and clone this repo. Can't paste the link, for some reason @twitter thinks it's malicious... 

2. Copy Burp Collaborator URL to the clipboard.
Privilege escalation in Windows using 4 tools for red teamers and pentesters.
(thread)
(thread)
1. WinPEAS - it's a simple .exe script you can run as: winpeas.exe > outputfile.txt
Get it here: github.com/carlospolop/PE…
Get it here: github.com/carlospolop/PE…
Top Python Libraries used by Hackers
(thread)
(thread)
1. socket: A library that provides low-level core networking services.
2. scapy: A powerful interactive packet manipulation library and tool.
Look for these file extensions in your pentests and appsec assessments.
(thread)
(thread)
1. .env - commonly used to store environment variables, including sensitive information such as passwords and tokens.
2. .yml/.yaml - commonly used in configuration files for software written in programming languages like Ruby, Python and JavaScript.
Squeezing the juices out of robots.txt.
A fully automated workflow that you've never seen before.
(thread)
A fully automated workflow that you've never seen before.
(thread)
1. This script scrapes the disallowed paths from the robots.txt files of a list of domains and saves them to a single file. It also removes any unwanted entries and sorts the file in a particular way.
Can you write it yourself? Here’s how the script should look like.
Can you write it yourself? Here’s how the script should look like.
2. Create a directory called "massrobots" in the pwd. This is where you'll save all the robots.txt files for later processing.
2023 Hacker's Guide: How to Break into Pentesting and AppSec.
(thread)
(thread)
1. Hands down, one of the best practical resources is @RealTryHackMe. I would take the "Complete Beginner" learning path, then the "Jr. Penetration Tester" path. It will get you off the ground in no time.
tryhackme.com/path-action/be…
tryhackme.com/path-action/be…
2. Simultaneously, I would practice at @PortSwigger Academy. Personally, I'd focus on all things Broken Access Control.
portswigger.net/web-security/a…
portswigger.net/web-security/a…
1. Web Application Pentesting Checklist - based on @owasp by Hariprasaanth.
This has 500+ test cases and it's well written: hariprasaanth.notion.site/hariprasaanth/…
This has 500+ test cases and it's well written: hariprasaanth.notion.site/hariprasaanth/…
2. Web Application Penetration Testing Checklist - by @e11i0t_4lders0n
I like this because it's detailed. It has 200+ test cases: alike-lantern-72d.notion.site/Web-Applicatio…
I like this because it's detailed. It has 200+ test cases: alike-lantern-72d.notion.site/Web-Applicatio…
How to learn reverse engineering fast. A Practical approach.
(thread)
(thread)
1. Go to crackmes.one and start playing with the challenges there.
2. Study from the book "Reverse Engineering for Beginners". You can do it for free at: beginners.re
Static and dynamic testing of Android apps. A quick guide:
(thread)
(thread)
(static analysis) 1. Decompile the app to understand how the code works. Use jadx.
(static analysis) 2. Analyze the app's resources for potential hardcoded credentials or sensitive information.
5 sources to learn smart contract hacking by example.
(thread)
(thread)
1. Response manipulation
- it usually happens when the server doesn't check client-side input
- it usually happens when the server doesn't check client-side input
2. OTP/MFA/2FA code leak in the response
- it usually happens when the verification code is leaked in the response
- it usually happens when the verification code is leaked in the response
How I do subdomain enumeration by aggregating multiple tools in a bash script. The script contains the following tools:
(thread)
(thread)
2. assetfinder @TomNomNom
- takes: $1, looks for -subs-only, sorts unique, and appends to the above file
- takes: $1, looks for -subs-only, sorts unique, and appends to the above file
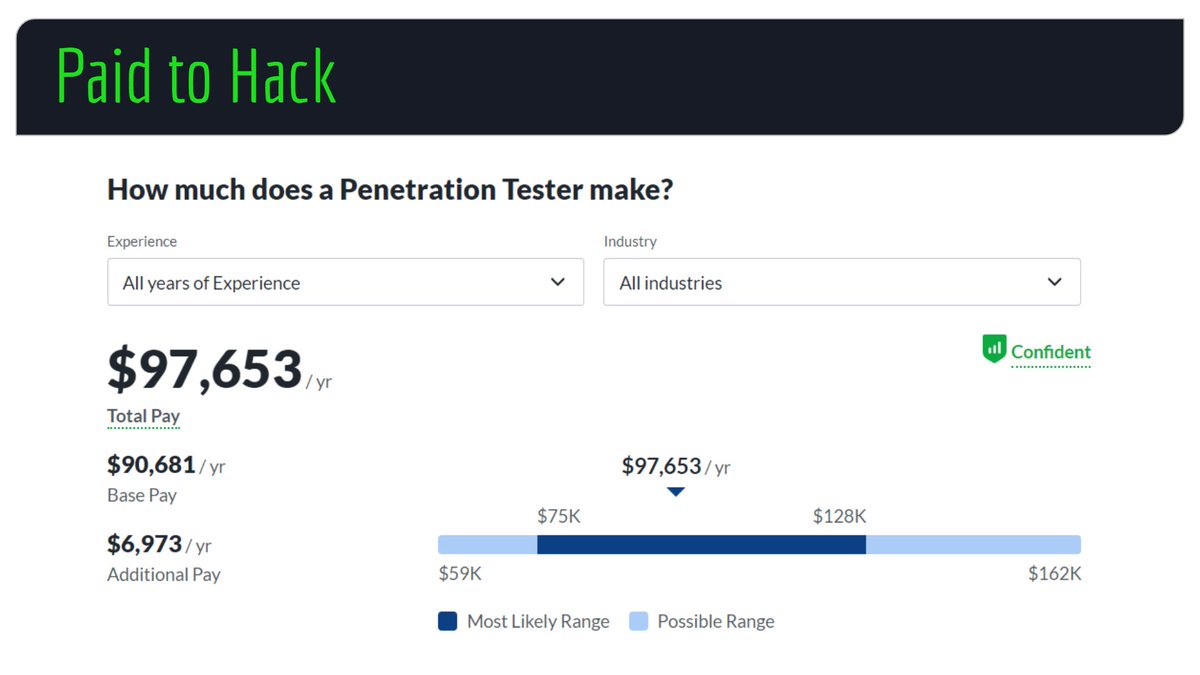
Paid to Hack!
How much money can you make in cybersecurity?
(thread)
How much money can you make in cybersecurity?
(thread)
1. Researchers at Check Point used AI models, including OpenAI's ChatGPT and Codex, to create a full infection flow for a cyber attack without writing any code themselves.
2. The attack began with a spear-phishing email, impersonating a hosting company, generated by #ChatGPT