Discover and read the best of Twitter Threads about #Lazarus
Most recents (21)
🚨 1/ Ongoing campaign primarily targeting security researchers here on Twitter.
Possibly they are trying to exploit some vulnerability in Internet Explorer and database tools like Navicat. I haven't been able to get the malicious payload yet, but something fishy is going on 🤔



Possibly they are trying to exploit some vulnerability in Internet Explorer and database tools like Navicat. I haven't been able to get the malicious payload yet, but something fishy is going on 🤔



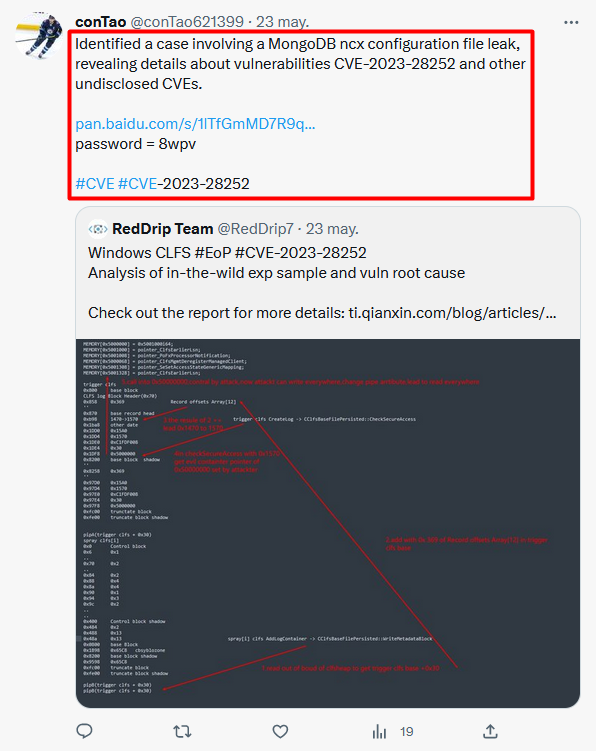
2/ Tweets mention things like #0day, #databreach, #Kimsuky, #Lazarus and point to a file download on pan[.]baidu[.]com, just now removed.
There is also a repo on Github with connection data and credentials to supposed DBs and Web Apps that ask to use IE 🤭



There is also a repo on Github with connection data and credentials to supposed DBs and Web Apps that ask to use IE 🤭




⚠️ Heads up y'all—we're seen a huge increase in the # of ultra-targeted spearphishes lately.
The most deadly one? A Google Doc share that appears to come from *someone you know* about *something you're interested in*
It won’t be flagged and looks super legit.
DO NOT CLICK! 🙏
The most deadly one? A Google Doc share that appears to come from *someone you know* about *something you're interested in*
It won’t be flagged and looks super legit.
DO NOT CLICK! 🙏

This campaign is the work of #Lazarus / #APT38 / #DangerousPassword / #T444
aka the same crew that compromised Ronin, Harmony, bZx, Bondly, EasyFi, mngr, Arthur0x, Hugh Karp, etc. etc. etc.
Their spear-phishing methods are diverse, targetted, and hard-to-detect.
aka the same crew that compromised Ronin, Harmony, bZx, Bondly, EasyFi, mngr, Arthur0x, Hugh Karp, etc. etc. etc.
Their spear-phishing methods are diverse, targetted, and hard-to-detect.

For the last five years, I've been working on a book on the Raising of #Lazarus, today's beautiful Gospel reading from Jn 11, called "Come Forth." The book includes some images of Lazarus from art, as well as photos of current-day Bethany, Al Eizariya. The first is the oldest... 

1/ Today the FBI identified the North Korean hacker group Lazarus Group and APT38 as the Horizon Bridge attackers, with the hacker group using malware called 'TraderTraitor' to carry out the attack.
1/and laundered over $60 million in stolen Ether through a privacy protocol called Railgun. What are "TraderTraitor" and Railgun? @evilcos
#ESETresearch has discovered #Lazarus attacks against targets in 🇳🇱 and 🇧🇪, spreading via spearphishing emails and exploiting the CVE-2021-21551 vulnerability to disable the monitoring of all security solutions on compromised machines @pkalnai welivesecurity.com/2022/09/30/ama…
@pkalnai The attack started with spearphishing emails connected to fake job offers, targeting an aerospace company in the Netherlands, and a political journalist in Belgium. The attackers then deployed a VMProtect-ed version of #BLINDINGCAN, a fully featured HTTP(S) backdoor. 2/6 
@pkalnai Notably, the attackers used a rootkit named FudModule.dll, that modifies kernel variables and removes kernel callbacks to disable monitoring of all security solutions on the system. This is the first recorded abuse of the CVE-2021-21551 vulnerability in Dell DBUtil drivers. 3/6
#ESETresearch #BREAKING A signed Mac executable disguised as a job description for Coinbase was uploaded to VirusTotal from Brazil 🇧🇷. This is an instance of Operation In(ter)ception by #Lazarus for Mac. @pkalnai @dbreitenbacher 1/7 

Malware is compiled for both Intel and Apple Silicon. It drops three files: a decoy PDF document Coinbase_online_careers_2022_07.pdf, a bundle FinderFontsUpdater.app and a downloader safarifontagent. It is similar to #ESETresearch discovery in May. 2/7
1/20 Some thoughts on the ban of #TornadoCash by OFAC:
2/20 On 8/8/22, "TORNADO CASH", tornado.cash websites + some related smart contracts were added to the list of Specially Designated Nationals + Blocked Persons (#SDN List) under the OFAC's Cyber-Related Sanctions program [CYBER2]
3/20 #CYBER2 requires US persons to block the property and interests in property of persons added to the #SDN list. CYBER2’s legal basis is Executive Order (EO) 13757 (Dec 28, 2016), which amends EO 13694 (Apr 1, 2015). home.treasury.gov/system/files/1…
தேவசகாயம் பிள்ளை புனிதரா?? சதியா??
300 ஆண்டுகளுக்கு முன்பு வாழ்ந்த தேவசகாயம் பிள்ளை க்கு, வாடிகனால் தற்போது புனிதர் பட்டம் வழங்கப்பட்டதின் பின்னணி என்ன என்று ஆராய்ந்து பார்த்தால் புரியும், இது மிஷனரிகளின் சதி என்று
300 ஆண்டுகளுக்கு முன்பு வாழ்ந்த தேவசகாயம் பிள்ளை க்கு, வாடிகனால் தற்போது புனிதர் பட்டம் வழங்கப்பட்டதின் பின்னணி என்ன என்று ஆராய்ந்து பார்த்தால் புரியும், இது மிஷனரிகளின் சதி என்று
23-4-1712 அன்று கேரளா மாநிலத்தில், (தற்போது தமிழ்நாட்டில் உள்ள கன்னியாகுமரி) உள்ள, நட்டனத்தில், ஹிந்து பெற்றோருக்கு புதல்வனாக நீலகண்டப் பிள்ளை பிறந்தார்.
அப்போது கன்னியாகுமரியை, திருவிதாங்கூர் அரசரான மார்த்தாண்ட வர்மா என்னும் மாவீரர் ஆட்சி செலுத்தி வந்தார்.
அப்போது கன்னியாகுமரியை, திருவிதாங்கூர் அரசரான மார்த்தாண்ட வர்மா என்னும் மாவீரர் ஆட்சி செலுத்தி வந்தார்.
படை எடுத்து வந்த டச்சுக்காரர்களை, மார்ர்த்தாண்ட வர்மா துவம்சம் செய்து விரட்டியது ஒரு சரித்திர நிகழ்ச்சி!
மார்த்தாண்ட வர்மாவிடம் பணிபுரிந்த நீலகண்டப் பிள்ளை, டச்சு கடற்படை கேப்டன் ஆவுஸ்டாஷியஸ் டி லெனாய் (Austachius De Lanoy) என்பவனின் சூழ்ச்சியால்,
மார்த்தாண்ட வர்மாவிடம் பணிபுரிந்த நீலகண்டப் பிள்ளை, டச்சு கடற்படை கேப்டன் ஆவுஸ்டாஷியஸ் டி லெனாய் (Austachius De Lanoy) என்பவனின் சூழ்ச்சியால்,
#ESETresearch In November 2020, a Windows executable called mozila.cpl was submitted to VirusTotal from Germany 🇩🇪. At that time, it had zero detection rate and it is still very low now. The file is a trojanized sqlite-3.31.1 library and we attribute
it to #Lazarus. @pkalnai 1/4
it to #Lazarus. @pkalnai 1/4

The library contains an embedded payload. A command line argument S0RMM-50QQE-F65DN-DCPYN-5QEQA must be provided for its decryption and additional parameters are passed to the payload. 2/4
The payload is an instance of the HTTP(s) uploader mentioned in the report by HvS-Consulting from December 2020. Its main purpose is to exfiltrate RAR archives from a victim’s system.
hvs-consulting.de/public/ThreatR… 3/4
hvs-consulting.de/public/ThreatR… 3/4
#ESETresearch A year ago, a signed Mach-O executable disguised as a job description was uploaded to VirusTotal from Singapore 🇸🇬. Malware is compiled for Intel and Apple Silicon and drops a PDF decoy. We think it was part of #Lazarus campaign for Mac. @pkalnai @marc_etienne_ 1/8 

The document, named BitazuCapital_JobDescription.pdf, reminds a strong similarity with a lure from Lazarus attacks using 2 TOY GUYS code-signing certificates for Windows, targeting aerospace and defense industries. welivesecurity.com/wp-content/upl… 2/8 

Thread on #APT grps, #hacktivists, #Ransomware gangs with their ‘likely’ associations (as per TTPs and reports) that are playing a significant role in impending #Ukraine #Russian conflict. Correct me if i am wrong or missing any one. 1/
Firstly on Russian 🇷🇺side there are #GhostWriter (#Belarus Govt Backed) #CozyBear (Russian Foreign Intel aka #SVR) #UNC1151 (Minsk based) #FancyBears & #SandWorm (Russian Military Intel aka #GRU) #Turla and #Gamaredon (Russian Internal Intel #FSB Former KGB) 2/
Other hacking groups incl #Lazarus (Russia & North Korea backed) #RedBanditsRU #Coomingproject #Freecivilian #DigitalCobraGang #Stormous #XakNet #Killnet #Zatoichi #Conti 3/
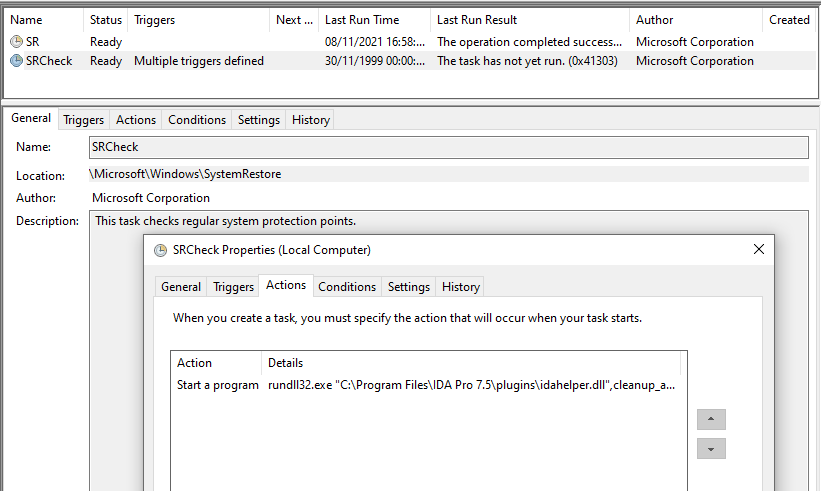
#ESETresearch discovered a trojanized IDA Pro installer, distributed by the #Lazarus APT group. Attackers bundled the original IDA Pro 7.5 software developed by @HexRaysSA with two malicious components. @cherepanov74 1/5 


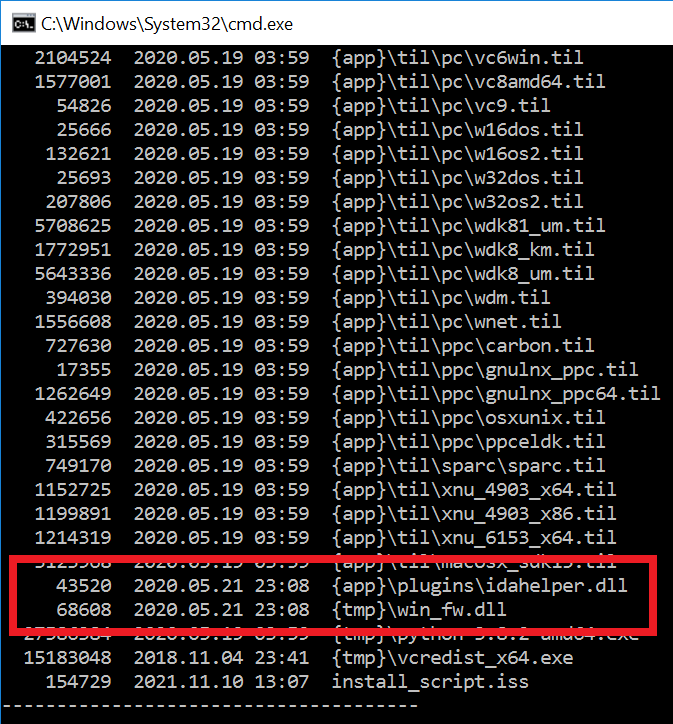
Some updates on this suspected #Lazarus #APT:(thread, 1/4)
1) The remote template is VBA stomped or at least it was able to hide itself from olevba and oledump
2) The remote template drops an obfuscated vbs file and registers it as a scheduled service



1) The remote template is VBA stomped or at least it was able to hide itself from olevba and oledump
2) The remote template drops an obfuscated vbs file and registers it as a scheduled service



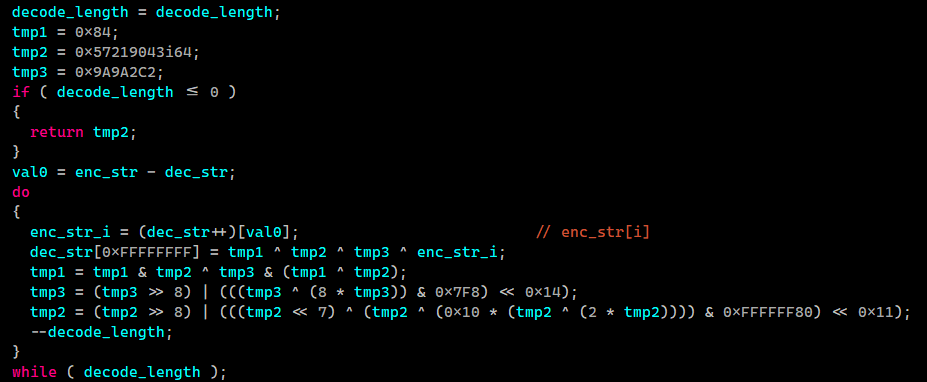
3) All the strings in "OneDriveUpdateNew.vbs" are obfuscated and are decoded using "string_decoder" function with a hardcoded key table.
You can see the decoder and list of the decoded strings used by this vbs file here:
github.com/HHJazi/APT
2/4

You can see the decoder and list of the decoded strings used by this vbs file here:
github.com/HHJazi/APT
2/4
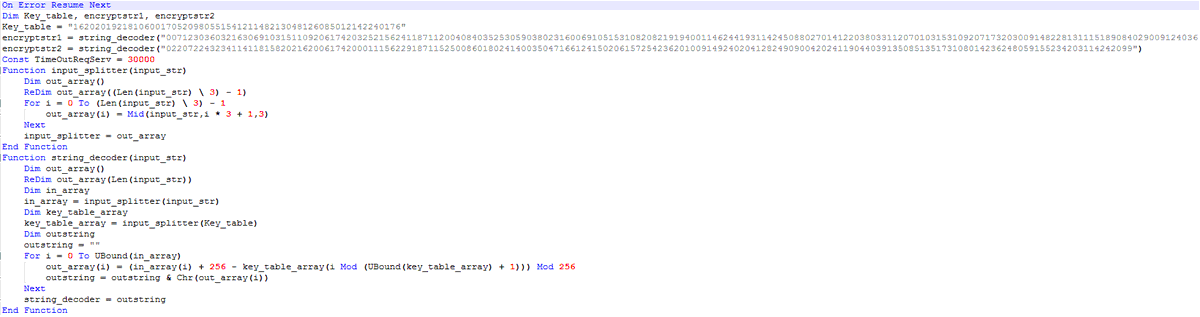

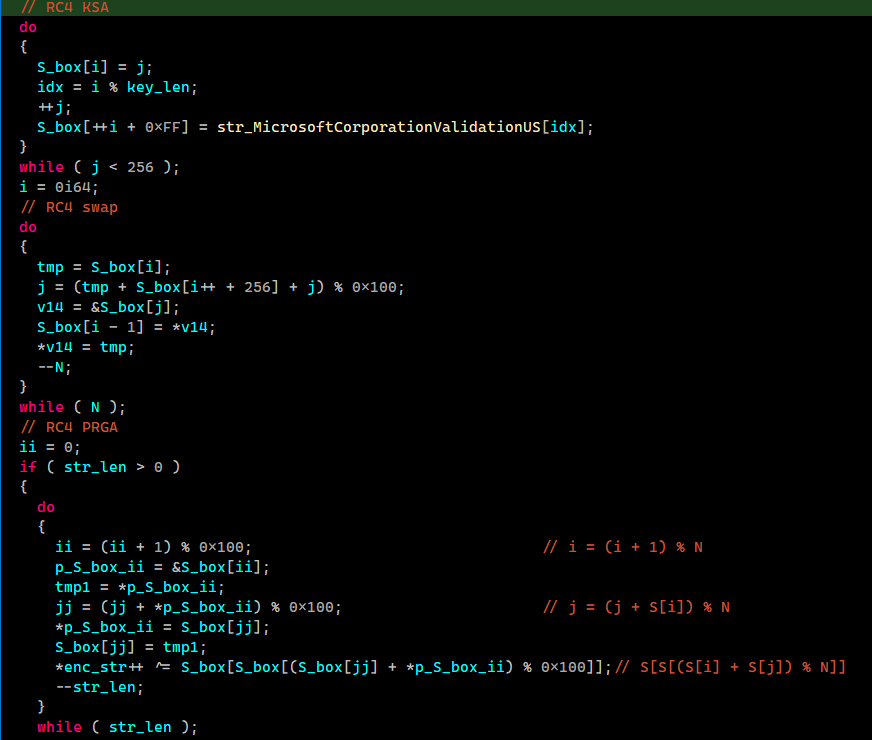
Diving into the #Lazarus sample that mentioned in nice blog tinyurl.com/mdyxr8m3. I recognized it uses 2 custom algorithms for decoding strings.
- 1st is modified RC4 to decrypt API functions name.
- 2nd is custom algo to decrypt C2 urls and user agent strings (1/4)
- 1st is modified RC4 to decrypt API functions name.
- 2nd is custom algo to decrypt C2 urls and user agent strings (1/4)
296. #SophieJones (2021) A raw and resonant coming of age story about dealing with grief and overcome pain,it feels very personal. The cinematography is gorgeous and visually stunning with excellent performances by the cast especially the lead who is great.Really good. ⭐⭐⭐1/2 







296. #Moxie (2021) A fun and entertaining coming of age movie that might be a bit flawed, but the performances by the cast is good and it is a bit long however it deals with a lot of important issues and it have a really powerful scene at the end, the direction is strong. ⭐⭐⭐ 







297. #TheHitchHiker (1953) A swift thrilling noir film that is visually pleasing with great direction, it is very tense,suspensful and fast paced (yeah it's only 70 min)anchored by a trio of great performances by the cast. The story might not fully fleshed but still fun. ⭐⭐⭐⭐ 







1. The more I look at these Trump election contests the more apparent they're all linked to the criminal conspiracy to impair the @USPS. Question for me: Do the lawyers know the the criminal purpose sufficiently to have incurred criminal liability?
2. For Rudy & Sidney Powell, I think it likely. For run-of-the-mill local counsel, absent more proof, I would think not. But Rudy & Powell likely will be seeking pardons that may have been part of their deal. And with them, Trump will dig himself a deeper hole and the ongoing
3. nature of the conspiracy will bring Rudy and Grisham a taste of my #Lazarus Theory that says you cannot successfully pardon an on-going conspiracy because the continued agreement plus a single overt act in furtherance of the unlawful purpose done by any conspirator
#ESETresearch discovered a supply-chain attack performed by #Lazarus APT group against South Korean 🇰🇷 internet users. @cherepanov74 @pkalnai welivesecurity.com/2020/11/16/laz… 1/7
#ESETresearch analyzed operation #Interception, a new espionage campaign targeting aerospace & defense companies in Europe and the Middle East. Initial contact was made via #LinkedIn, where attackers approached targets with fake job offers @jiboutin welivesecurity.com/2020/06/17/ope… 1/5 
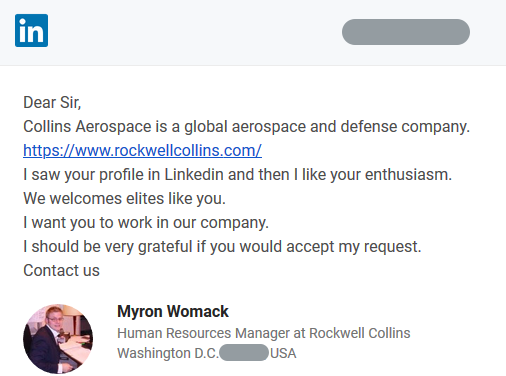
The attackers sent a password protected RAR archive containing a LNK file responsible for showing a decoy PDF and downloading additional malware. In some cases, this archive was sent directly through #LinkedIn instant messenger. #ESETresearch 2/5 

1. Snippet of pardon law from 2017 in the context of a crime boss in the @WhiteHouse. And I'll add that a dangle, offer and act of pardoning a witness can be bribery, tampering and conspiracy by the official and his/her staff. Sorry Roger. Suck it up. @TheJusticeDept @FBIWFO
2. If Trump pardon's him, Roger has to talk. Also I don't see that a pardon works for an ongoing conspiracy. The defendant who has not withdrawn, still agrees to the conspiracy and agreeing to not testify with one overt act and conspiracy liability comes back to life. #Lazarus.
3. Easy fact pattern: Bob BankRobber plans a bank robbery with Cal Conspirator. Bob gets caught after agreement and overt act and charged with conspiracy. Pres DirtyDon pardons Bob who agrees to refuse to testify against Cal. Assume an overt act in furtherance of conspiracy.
Die #IT-Umgebung des indischen #AKW's Kudankulam wurde nicht nur gehackt, sondern als Command and Control Server benutzt.
Hoffentlich war die #OT nicht auch öffentlich am Netz!
#KRITIS Sektor #Energie #nuclear #nuclearsafety #Resilienz #Cyber #Security
Hoffentlich war die #OT nicht auch öffentlich am Netz!
#KRITIS Sektor #Energie #nuclear #nuclearsafety #Resilienz #Cyber #Security
Zur Unterscheidung:
IT sind Informationstechnische Systeme (#PC #Laptop #Windows #Office, #Buchhaltung...)
OT sind Operative Systeme (#ICS #SCADA #SPS #HMI #PLC #Steuertechnik...)
IT sind Informationstechnische Systeme (#PC #Laptop #Windows #Office, #Buchhaltung...)
OT sind Operative Systeme (#ICS #SCADA #SPS #HMI #PLC #Steuertechnik...)
Angemessener Stand der Technik #SdT wie in #KRITIS gefordert wurde offenbar im #AKW nicht eingehalten.
Strikte #Trennung zwischen #OT-Steuersystemen und #IT ist eine wesentliche #Sicherheitsmaßnahme!
Weitere #Maßnahmen und #Forderungen finder Ihr hier.
ag.kritis.info/politische-for…
Strikte #Trennung zwischen #OT-Steuersystemen und #IT ist eine wesentliche #Sicherheitsmaßnahme!
Weitere #Maßnahmen und #Forderungen finder Ihr hier.
ag.kritis.info/politische-for…