Discover and read the best of Twitter Threads about #cybersecurityawareness
Most recents (11)
A class 12 passout, former security officer and self taught cybergeek from Hyderabad, Shrinivas Rao Dadi, masterminded a nationwide cyberfraud with a turnover of Rs 3 crore a day. The money was being converted into #cryptocurrency and sent to #China. So, how did he do it? 

There was a hierarchy to how the scamsters operated. Some of them called up citizens, posing as policemen and flashing fake ID cards, over WhatsApp and Skype. Women were targetted the most. In Delhi, one of the scamsters made a video call to a woman, dressed in a khaki uniform.
The victims were told that a parcel he/she had sent by courier was found containing drugs. The terrified victims were deceived into downloading apps, such as Anydesk, that provided the scamster with remote access to his phone screen.
1/ 🚨 A recent surge in phishing scams via Google search ads has led to users losing approximately $4 million.
ScamSniffer has investigated multiple cases where users clicked on malicious ads and were directed to fraudulent websites.
#PhishingScams #GoogleAds
ScamSniffer has investigated multiple cases where users clicked on malicious ads and were directed to fraudulent websites.
#PhishingScams #GoogleAds
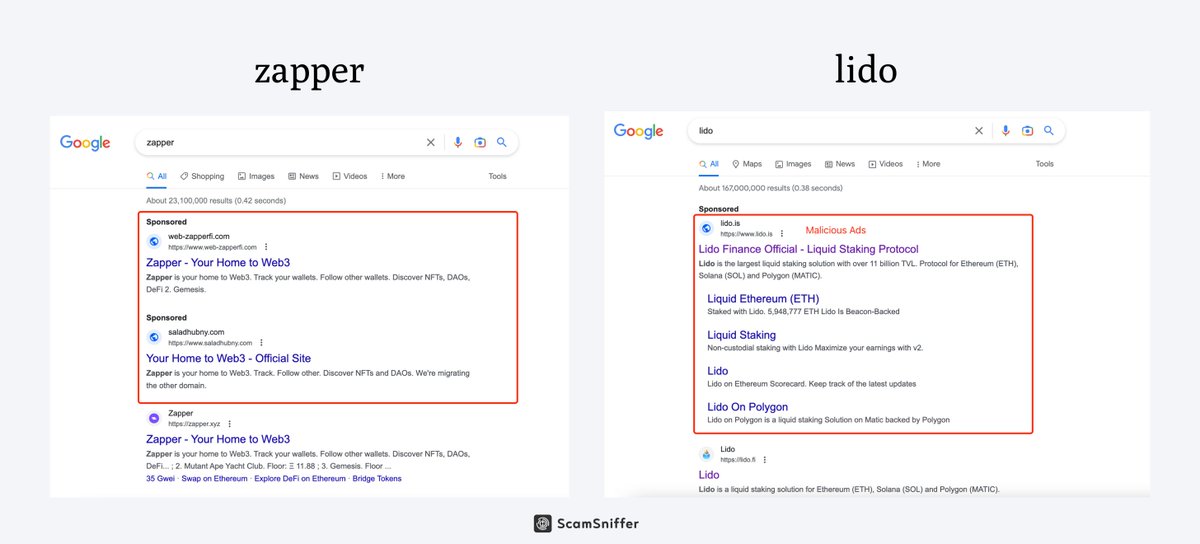
2/ 🕵️♂️ Investigation into the keywords used by victims has uncovered numerous malicious ads at the forefront of search results.
Most users, unaware of the deceptive nature of search ads, click on the first available option, leading them to malicious websites.
#Cybersecurity
Most users, unaware of the deceptive nature of search ads, click on the first available option, leading them to malicious websites.
#Cybersecurity

3/ 🎯 Some of the malicious ads and websites target brands such as @zapper_fi , @LidoFinance , @StargateFinance and @DefiLlama.
These advertisers have been identified as placing these malicious ads:
ТОВАРИСТВО З ОБМЕЖЕНОЮ ВІДПОВІДАЛЬНІСТЮ «РОМУС-ПОЛІГРАФ»
TRACY ANN MCLEISH.

These advertisers have been identified as placing these malicious ads:
ТОВАРИСТВО З ОБМЕЖЕНОЮ ВІДПОВІДАЛЬНІСТЮ «РОМУС-ПОЛІГРАФ»
TRACY ANN MCLEISH.


In the world of bug bounty hunting, Insecure Direct Object References (IDORs) can be a goldmine. In this thread, we'll share advanced tips to sharpen your IDOR detection skills. Let's dive in! 🌊🔍
#bugbountytip #bugbountytips #CyberSecurityAwareness
1/n
#bugbountytip #bugbountytips #CyberSecurityAwareness
1/n
Always begin with a thorough understanding of the application you're testing. Identify all possible user roles and their access rights. This knowledge is crucial for accurately identifying IDOR vulnerabilities. 🧠📝
Pay attention to API endpoints that handle user-specific data. Keep an eye out for patterns in URL parameters or request payloads. Examine how the application validates user input and authorization checks for these sensitive resources. 📡🔬
15 𝐅𝐑𝐄𝐄 𝐂𝐞𝐫𝐭𝐢𝐟𝐢𝐜𝐚𝐭𝐢𝐨𝐧 𝐩𝐫𝐨𝐯𝐢𝐝𝐞𝐝 𝐛𝐲 𝐭𝐡𝐞 𝐂𝐈𝐒𝐀 (Cyber & Infrastructure Security Agency of the United States)
1. Cloud Computing Security lnkd.in/dE62kGXX
2. Cloud Security - What Leaders Need to Know lnkd.in/dDSMg7xa
1. Cloud Computing Security lnkd.in/dE62kGXX
2. Cloud Security - What Leaders Need to Know lnkd.in/dDSMg7xa
3. Cryptocurrency for Law Enforcement for the Public lnkd.in/dNkVm-4j
4. Cyber Supply Chain Risk Management for the Public lnkd.in/dxEaQA8w
5. Cyber-essentials lnkd.in/dCQr2ket
6. Don’t Wake Up to a Ransomware Attack lnkd.in/d36WV_g5
4. Cyber Supply Chain Risk Management for the Public lnkd.in/dxEaQA8w
5. Cyber-essentials lnkd.in/dCQr2ket
6. Don’t Wake Up to a Ransomware Attack lnkd.in/d36WV_g5
7. Foundations of Cybersecurity for Managers lnkd.in/dg4Ed4Gf
8. Fundamentals of Cyber Risk Management lnkd.in/dXjpdZMr
9. Introduction to Cyber Intelligence lnkd.in/dB9cgC99
10. Securing Internet-Accessible Systems lnkd.in/dv_nYHbP
8. Fundamentals of Cyber Risk Management lnkd.in/dXjpdZMr
9. Introduction to Cyber Intelligence lnkd.in/dB9cgC99
10. Securing Internet-Accessible Systems lnkd.in/dv_nYHbP
Be safer online in 2023 by following these basic tips.
#CyberSecurityAwareness #cybersecurity #privacy
🧵
#CyberSecurityAwareness #cybersecurity #privacy
🧵
Check if your emails, phone numbers, passwords, etc. have been breached on @haveibeenpwned / Firefox Monitor.
More info -
More info -
Use secure passwords that are unique for every account you have. Do not include PII in your passwords, such as your name or birthdate.
I suggest using a passphrase with at least five words or a complex password with at least 25 characters. A password manager can come in handy.
I suggest using a passphrase with at least five words or a complex password with at least 25 characters. A password manager can come in handy.
Here's a list of 5 FREE Cybersecurity trainings.
🧵👇
.
.
.
#bugbounty #cybersecurity #infosec #hacking #tech #learninig #datasecurity #linux #ransomware #ethicalhacking #cybersecuritytraining #cybersecurityawareness #malware #informationsecurity #isecurity
🧵👇
.
.
.
#bugbounty #cybersecurity #infosec #hacking #tech #learninig #datasecurity #linux #ransomware #ethicalhacking #cybersecuritytraining #cybersecurityawareness #malware #informationsecurity #isecurity
#IGF2022
@SFLCin team will be attending this years @intgovforum in #AddisAbaba, Ethiopia from 28 November to 2 December 2022.
The the overarching theme for #IGF2022 is - "Resilient Internet for a Shared Sustainable and Common Future."
#ResilientInternet #IGF #DigitalDefenders
@SFLCin team will be attending this years @intgovforum in #AddisAbaba, Ethiopia from 28 November to 2 December 2022.
The the overarching theme for #IGF2022 is - "Resilient Internet for a Shared Sustainable and Common Future."
#ResilientInternet #IGF #DigitalDefenders

#eventupdates
We are hosting 2 sessions and participating in one. We are looking forward to having interesting conversations around "Resilient Internet for a Shared Sustainable and Common Future".
The session details are given below -
We are hosting 2 sessions and participating in one. We are looking forward to having interesting conversations around "Resilient Internet for a Shared Sustainable and Common Future".
The session details are given below -
Session 01: "Help! The Kill switch is taking away my limited agency"
Speakers-
@RadhikaJhalani🔗 @SFLCin,
Oliver Spencer 🔗 @FreeExpressMm, @agrabeli_🔗 @OpenObservatory, @PrasanthTweets🔗 @SFLCin,
@arzakkhan,
@FelAnthonio🔗 @accessnow.
intgovforum.org/en/content/igf…
Speakers-
@RadhikaJhalani🔗 @SFLCin,
Oliver Spencer 🔗 @FreeExpressMm, @agrabeli_🔗 @OpenObservatory, @PrasanthTweets🔗 @SFLCin,
@arzakkhan,
@FelAnthonio🔗 @accessnow.
intgovforum.org/en/content/igf…
Start your Career in Cyber-Security / Information-Security by spending $0
These are FREE University courses that are available online for you to take!
🧵
#infosec #infosecurity #Harvard #NetworkSecurity #CyberMonday2022 #CyberSecurityAwareness
These are FREE University courses that are available online for you to take!
🧵
#infosec #infosecurity #Harvard #NetworkSecurity #CyberMonday2022 #CyberSecurityAwareness
𝐈𝐁𝐌 - 𝐂𝐲𝐛𝐞𝐫𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐁𝐚𝐬𝐢𝐜𝐬
This course gives you the background needed to understand the basics of Cybersecurity.
🖇️
edx.org/course/cyberse…
This course gives you the background needed to understand the basics of Cybersecurity.
🖇️
edx.org/course/cyberse…
𝐂𝐲𝐛𝐞𝐫𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐅𝐮𝐧𝐝𝐚𝐦𝐞𝐧𝐭𝐚𝐥𝐬
Learn cybersecurity fundamentals, including how to detect threats, protect systems and networks, and anticipate potential cyber attacks.
🖇️
edx.org/course/cyberse…
Learn cybersecurity fundamentals, including how to detect threats, protect systems and networks, and anticipate potential cyber attacks.
🖇️
edx.org/course/cyberse…
Want to break into cybersecurity? We've got something special to ease
your journey.😎
In this webinar, we will discuss industry secrets guaranteed to help you land your dream cybersecurity job.
your journey.😎
In this webinar, we will discuss industry secrets guaranteed to help you land your dream cybersecurity job.

WHAT WILL YOU LEARN?
1. How to identify a cybersecurity niche and choose a career path.
2. Learn about the technical tools and technology required for entry-level roles.
3. Ways to connect with cybersecurity mentors both home and abroad.
1. How to identify a cybersecurity niche and choose a career path.
2. Learn about the technical tools and technology required for entry-level roles.
3. Ways to connect with cybersecurity mentors both home and abroad.
4. Interview preparation steps (Mock interview).
5. How to find entry-level cybersecurity job opportunities.
You can't afford to miss this, so register here: bit.ly/bicbyhacktales
5. How to find entry-level cybersecurity job opportunities.
You can't afford to miss this, so register here: bit.ly/bicbyhacktales
Think Before You Share (thread) #cybersecurity #SocialMedia #scam #CriticalThinking #CyberSecurityAwareness
Things to think about before you share something on social media:
A few basic questions to ask before sharing anything you did not write yourself, especially something you found on social media:
A few basic questions to ask before sharing anything you did not write yourself, especially something you found on social media:
(1) Who wrote this?
(2) When was it written? Is it still current?
(3) What do you know about the author (not the person who shared it, the *author*) that makes them a trustworthy source? What conflicts of interest do they have?
(2) When was it written? Is it still current?
(3) What do you know about the author (not the person who shared it, the *author*) that makes them a trustworthy source? What conflicts of interest do they have?




