Discover and read the best of Twitter Threads about #Hacker
Most recents (24)
Iran-linked hackers Agrius deploying new ransomware against Israeli orgs
An Iran-linked advanced persistent threat #APT group is using new #ransomware while targeting a familiar adversary in the Middle East, researchers have found.
#Iran #CyberAttack
therecord.media/iran-hackers-a…
An Iran-linked advanced persistent threat #APT group is using new #ransomware while targeting a familiar adversary in the Middle East, researchers have found.
#Iran #CyberAttack
therecord.media/iran-hackers-a…
"Check Point’s Incident Response Team investigated the deployment of the ransomware against #Israeli organizations and claimed by a group dubbing itself Moneybird."
"Researchers found that it bore the hallmarks of Agrius, a #hacker group that has been around since 2020 and has attempted to disguise itself with aliases like BlackShadow."
⚠️ A browser extension is always a double-edged sword.
In general, there isn't much to disagree with in what @panosmek has written in this fantastic thread, but here are few additional thoughts:
🧵👇 [1/13]
In general, there isn't much to disagree with in what @panosmek has written in this fantastic thread, but here are few additional thoughts:
🧵👇 [1/13]
Breve thread/ Se davvero la brigata #Wagner è dietro gli sbarchi come sostengono i ministri @GuidoCrosetto e @Antonio_Tajani, allora stiamo assistendo a un'offensiva di #guerranonlineare contro l'#Italia senza precedenti e portata avanti su più piani 1/
Le #migrazioni vengono usate come arma di #guerranonlineare per rendere difficile al #governo il controllo del fenomeno e per creare aspro confronto nell'opinione pubblica 2/
Gli attacchi #hacker prendono di mira il nostro Paese in modo sempre più frequente e presto dai siti delle istituzioni si passerà anche a quelli delle aziende chiave 3/
#havanasyndrome @PFPAOfficial @DeptofDefense @FBI @CIA @DHSgov Citizens are carrying their own chip. This is a #neuroweapon off of the cell towers in a loop. Your smartphone is a Swiss Army knife. In good faith of the investigation. twitter.com/i/broadcasts/1…
My digital forensics investigation brought back 19 cell towers the hacker attempted to erase from my smartphone. Theirs a reason why they erased them towers. #neuroweapon
Does anyone think that a fusion center is going to attack. The embassy workers kids? My theory. Corruption has hired sit at home remote workers. Although your neighbor could be in on it. Right in your phones. Hidden drug network. Human trafficking. Imsi catcher used at first.
Top 9 Hacker Gadgets
1. Raspberry Pi:
This is a low cost credit card sized desktop computer that runs Linux and it also provides a set of GPIO (general purpose input/output) pins. It enables people to explore computing and learn Programming.
1. Raspberry Pi:
This is a low cost credit card sized desktop computer that runs Linux and it also provides a set of GPIO (general purpose input/output) pins. It enables people to explore computing and learn Programming.

[THREAD] 15 ans de #SEO : Quand je sors des sentiers battus !
Pratiquant le White Hat depuis mes débuts, je reste curieux du Black même si je ne fais prendre aucun risque à mes clients. Il m’arrive, toutefois, de sortir des sentiers battus.🤫
Pratiquant le White Hat depuis mes débuts, je reste curieux du Black même si je ne fais prendre aucun risque à mes clients. Il m’arrive, toutefois, de sortir des sentiers battus.🤫
1) Acheter du trafic pour remonter sur la marque : lorsqu’un de mes clients se lance dans un pays, j’achète des clics géolocalisés, faisant la recherche sur Google locale et cliquant sur l’url qu’on veut faire remonter.
2) #Offuscation de liens : j’ai abusé de cette Technique pendant 15 ans, j’utilise, aujourd’hui, d’autres stratégies pour la réduction de liens doublons ou non contextuels.
🚨 "Il Computer Security Incident Response Team Italia (Csirt-IT) dell’Agenzia per la Cybersicurezza Nazionale (ACN), ha rilevato un massiccio attacco" #hacker "tramite ransomware già in circolazione che prende di mira i server VMware ESXi".
2/n
Secondo l'agenzia, l'attacco è in corso in tutto il mondo e riguarda "qualche migliaio di server compromessi", da "Paesi europei come Francia – paese più colpito - Finlandia e Italia, fino al Nord America, in Canada e negli Stati Uniti".
Secondo l'agenzia, l'attacco è in corso in tutto il mondo e riguarda "qualche migliaio di server compromessi", da "Paesi europei come Francia – paese più colpito - Finlandia e Italia, fino al Nord America, in Canada e negli Stati Uniti".
3/n
I tecnici dell'Acn hanno già censito "diverse decine di sistemi nazionali verosimilmente compromessi e allertato numerosi soggetti i cui sistemi sono esposti ma non ancora compromessi".
I tecnici dell'Acn hanno già censito "diverse decine di sistemi nazionali verosimilmente compromessi e allertato numerosi soggetti i cui sistemi sono esposti ma non ancora compromessi".
Un pullback del mercato di martedì si è trasformato in un ritorno di mercoledì quando il bitcoin è salito oltre i $ 23.700 prima di ritirarsi leggermente. Eth sale sopra i $1.618. Altre criptovalute come #APT,registrano guadagni del 48% nelle ultime 24 ore,
Thread
Thread

At #IWCON2022, we have 15+ amazing #cybersecurity speakers from around the world 🌍
To share unique methods and findings with y’all 😍🙌
Get ready with your questions. Our experts will answer you live 🔥
Book your ticket: iwcon.live
Meet our speakers 🧵👇
To share unique methods and findings with y’all 😍🙌
Get ready with your questions. Our experts will answer you live 🔥
Book your ticket: iwcon.live
Meet our speakers 🧵👇

#1 Gabrielle Hempel @gabsmashh, #security engineer @Netwitness 🥳
Her topic: #Threat hunting in #cloud environments 🌩️
Time: 17th Dec, 7:30 pm IST
Want to attend this talk? 😍
Book your ticket here: iwcon.live
#cloudhunting #threathunting
Her topic: #Threat hunting in #cloud environments 🌩️
Time: 17th Dec, 7:30 pm IST
Want to attend this talk? 😍
Book your ticket here: iwcon.live
#cloudhunting #threathunting

#2 Luke Stephens @hakluke, founder of @haksecio 🔥
His topic: How I used #recon techniques to identify a prolific #scammer 👊
Time: 17th Dec, 6:30 pm IST ❤️
Don't wanna miss it?
Register today: iwcon.live
#infosec #hacking #hackingthehacker
His topic: How I used #recon techniques to identify a prolific #scammer 👊
Time: 17th Dec, 6:30 pm IST ❤️
Don't wanna miss it?
Register today: iwcon.live
#infosec #hacking #hackingthehacker

Lo scopo di #PropOrNot è stato quello di indurre le persone a chiedere che la libertà di parola venga annullata. Questo doveva/deve essere fatto distruggendo i media basati sui fatti: l'intero piano è strutturato a partire dal 2015, quando ha iniziato a prendere forma.
26/49
26/49

Queste persone vogliono che la realtà sia modellata su ciò che il gruppo dominante voglia diventi reale, indipendentemente da quali siano i fatti: la realtà basata sulla percezione come in un social media, in cui vengono create narrazioni per plasmare l'opinione pubblica.
27/49
27/49

Questo è l'hacker di #PravySektor RUH8. Il filo conduttore di questi hacker è chiaro se si legge il materiale linkato sui profili che compongono queste organizzazioni. Lavorano per #Bellingcat, #Informnapalm, il #ConsiglioAtlantico, l'Intelligence ucraina e la diaspora.
28/49
28/49

#Thread
How_To_Became a Great #hacker
1. Learn TCP/IP, Basic Information
gathering, Proxies, Socks, SSL, VPN, VPS, RDP,
FTP, POP3, SMTP, Telnet, SSH.
2. Learn Linux, Unix, Windows - You can do
this using vmware or any virtual desktop
utility.
#CybersecurityAwarenessMonth
How_To_Became a Great #hacker
1. Learn TCP/IP, Basic Information
gathering, Proxies, Socks, SSL, VPN, VPS, RDP,
FTP, POP3, SMTP, Telnet, SSH.
2. Learn Linux, Unix, Windows - You can do
this using vmware or any virtual desktop
utility.
#CybersecurityAwarenessMonth
3. Learn a programming language that's
compatible with all OS - Perl, Python, C, ASM
4. Learn HTML, PHP, Javascript, ASP, XML, SQL,
XSS, SQLI, RFI, LFI
5. Learn Reverse engineering and crack
some programs for serials easy ones like
mirc, winzip, winrar or old games.
compatible with all OS - Perl, Python, C, ASM
4. Learn HTML, PHP, Javascript, ASP, XML, SQL,
XSS, SQLI, RFI, LFI
5. Learn Reverse engineering and crack
some programs for serials easy ones like
mirc, winzip, winrar or old games.
6. Code a fuzzer for common protocols - ftp,
pop3, 80, 8080 - Pick some free software
like ftp server, mail server, apache or iis
webserver or a webserver all-in-one pack,
or teamspeak, ventrilo, mumble.
pop3, 80, 8080 - Pick some free software
like ftp server, mail server, apache or iis
webserver or a webserver all-in-one pack,
or teamspeak, ventrilo, mumble.
Complete roadmap to get into #cybersecurity in 2022:
Thread🧵👇
#cybersecurity #cybersecuritytips #infosec #hacking #hacker #bugbounty #bugbountytips #infosecurity
Thread🧵👇
#cybersecurity #cybersecuritytips #infosec #hacking #hacker #bugbounty #bugbountytips #infosecurity
1️⃣ IT Fundamentals
Before jumping into more advanced fields, you gotta know the basics.
You can learn everything you need for FREE from
@ProfessorMesser's course ➡️ professormesser.com/free-a-plus-tr…
For reference, you should be apt for @CompTIA's A+ certification before the next step.
Before jumping into more advanced fields, you gotta know the basics.
You can learn everything you need for FREE from
@ProfessorMesser's course ➡️ professormesser.com/free-a-plus-tr…
For reference, you should be apt for @CompTIA's A+ certification before the next step.
2️⃣ Networking
It's time to get technical.
Networking will teach you how the internet works, and it's CRUCIAL to have a SOLID understanding of this subejct.
You don't have to be a network engineer, but know things like the OSI Model, TCP/IP, Ports & Services, CIDR, Subnets, etc
It's time to get technical.
Networking will teach you how the internet works, and it's CRUCIAL to have a SOLID understanding of this subejct.
You don't have to be a network engineer, but know things like the OSI Model, TCP/IP, Ports & Services, CIDR, Subnets, etc
#Hacker
#AudioLeaks
توقع کے عین مطابق ن لیگ نے بھی عمران خان کی آڈیو ریلیز کر دی۔
اس آڈیو میں عمران خان اپنے پرنسپل سیکرٹری اعظم خان کے ساتھ گفتگو کر رہے ہیں کہ سائفر والی سازش پہ کیسے بیانیہ بنانا ہے
1 یہ آڈیوز شاکر بھائی نےنہیں ریلیز کی بلکہ یہ ن لیگ کا اپنا
@OfficialDGISPR
#AudioLeaks
توقع کے عین مطابق ن لیگ نے بھی عمران خان کی آڈیو ریلیز کر دی۔
اس آڈیو میں عمران خان اپنے پرنسپل سیکرٹری اعظم خان کے ساتھ گفتگو کر رہے ہیں کہ سائفر والی سازش پہ کیسے بیانیہ بنانا ہے
1 یہ آڈیوز شاکر بھائی نےنہیں ریلیز کی بلکہ یہ ن لیگ کا اپنا
@OfficialDGISPR

سٹنگ آپریشن ہے جسے خود مریم نواز نے بنی گالہ میں گھس کر سرانجام دیا لہذا اس اہم کامیابی پہ ن لیگ کو مبارکباد بنتی ہے ۔
2 بگنگ میں آڈیوز کبھی صاف نہیں ہوتیں کیونکہ یہ ہیڈ فونز سے سننی ہوتی ہے اور لانگ ٹرم ڈیٹا ریکوائرمنٹ رکھی جاتی ہے لیکن ن لیگ نے اس آڈیو کو اس قدر صاف رکھا ہے
2 بگنگ میں آڈیوز کبھی صاف نہیں ہوتیں کیونکہ یہ ہیڈ فونز سے سننی ہوتی ہے اور لانگ ٹرم ڈیٹا ریکوائرمنٹ رکھی جاتی ہے لیکن ن لیگ نے اس آڈیو کو اس قدر صاف رکھا ہے
کہ کوئی شور بھی نہیں اور تمام الفاظ بلکل صاف سنائی دے رہے ہیں ۔ ن لیگ کی اس اہم پیش رفت پہ ٹیکنالوجی ماہرین بھی ن لیگ کو خراجِ تحسین پیش کر رہے ہیں ۔
3 آڈیو میں ساری گفتگو اعظم خان کی ہے کیونکہ اس کو پہلے انتہائی کم سنا گیا ہے۔ ہاں عمران خان کی مختلف پریس کانفرنسز کے دوران
3 آڈیو میں ساری گفتگو اعظم خان کی ہے کیونکہ اس کو پہلے انتہائی کم سنا گیا ہے۔ ہاں عمران خان کی مختلف پریس کانفرنسز کے دوران
🚨Things you need to know Before/After the Merge & BEWARE Replay Attacks? 🎯🕵️
The #Merge is less than 10 days away like it or NOT but What should we expect and do with our $ETH, Staking, and #NFTs
Let's explore the Myths/Risk and the Truth around it.
🚨🚀🍻 🧵⚡️🕵️
The #Merge is less than 10 days away like it or NOT but What should we expect and do with our $ETH, Staking, and #NFTs
Let's explore the Myths/Risk and the Truth around it.
🚨🚀🍻 🧵⚡️🕵️

1/13
Before we start if you haven't checked my last thread 🧵about the forks and the potential #Airdrops that come with #merge make sure to check below :)
Your Like/RT/ comment and follow are highly appreciated. ❤️
Before we start if you haven't checked my last thread 🧵about the forks and the potential #Airdrops that come with #merge make sure to check below :)
Your Like/RT/ comment and follow are highly appreciated. ❤️
2/13
The Merge is tentatively scheduled for September 15. The countdown to #Mainnet is based on a target #TTD of #58750000000000000000 💥
The merge is simply a change of consensus mechanism used to verify #transactions and secure the #network.
The Merge is tentatively scheduled for September 15. The countdown to #Mainnet is based on a target #TTD of #58750000000000000000 💥
The merge is simply a change of consensus mechanism used to verify #transactions and secure the #network.

#Learn365 - Day 4⃣
SOP 🫧, Same Origin Policy.
A browser security framework that every #hacker should know.
Know what is it in this thread 🧵👇
#infosec #security #appsec #cybersecurity #SOP #http
SOP 🫧, Same Origin Policy.
A browser security framework that every #hacker should know.
Know what is it in this thread 🧵👇
#infosec #security #appsec #cybersecurity #SOP #http

SOP is browser security model, and I find lot of folks out there, who still dont understand it in and out.
Let me cover it here, in few threads.
Let's Start.
Let me cover it here, in few threads.
Let's Start.
It is a browser security model 🔥. Now what does that means ?
It simply means this control is enforced by browser to make user visiting a site more secure from attackers.
Browser creates virtual boundaries to segregate sites and this boundary is identified with ORIGINS.
It simply means this control is enforced by browser to make user visiting a site more secure from attackers.
Browser creates virtual boundaries to segregate sites and this boundary is identified with ORIGINS.
Since your malicious cyberattack timelines matched cybersecurity’s research to strengthen security for years and now, you hack alone but with a cooperative goal to damage national security. Which Advanced Persistent Threats group/s #APTs are you in, #Animez_UK? 

Converting traditional crime to cyber-enabled crime and becomes a malicious attacker against the UK, for
1- financial income,
2- #sexual desire and #harassment with #pornography sent to #women,
3- attacks for #politics against the UKGOV.
#Animez_UK

1- financial income,
2- #sexual desire and #harassment with #pornography sent to #women,
3- attacks for #politics against the UKGOV.
#Animez_UK


1st stage- early life:
-Experienced #exclusion/#discrimination.
-Didn’t learn to communicate with #women.
-favours #authoritarianism.
-enjoys #control targeted women & whom against his will.
- Expresses hidden #hatred & #violence on through cyberattacks.
#Animez_UK

-Experienced #exclusion/#discrimination.
-Didn’t learn to communicate with #women.
-favours #authoritarianism.
-enjoys #control targeted women & whom against his will.
- Expresses hidden #hatred & #violence on through cyberattacks.
#Animez_UK


Having fun with cyberstalking #UKGOV, attacking organisations, universities & individuals connected to the justice system, UK #military against #NCSC, treating #intelligence & #GCHQ as jokes to your 15- 20 yrs malicious #hacking for #China & #Russia inside #Britain, @Animez_UK?01
Converting #traditional crime to cyber-enabled crime and becomes a malicious #cyberattacker against the UK, for
1- #financial income,
2- #sexual desire and #harassment with #pornography sent to #women,
3- attacks for #politics against the #UKGOV.
@Animez_UK @NCSC
02
1- #financial income,
2- #sexual desire and #harassment with #pornography sent to #women,
3- attacks for #politics against the #UKGOV.
@Animez_UK @NCSC
02

1st stage- early life:
-Experienced #exclusion/#discrimination.
-Didn’t learned to communicate with #women.
-favours #authoritarianism.
-enjoys to #control targeted women & whom against his will.
- Expresses hidden #hatred & #violence on through cyberattacks.
@Animez_UK @NCSC
-Experienced #exclusion/#discrimination.
-Didn’t learned to communicate with #women.
-favours #authoritarianism.
-enjoys to #control targeted women & whom against his will.
- Expresses hidden #hatred & #violence on through cyberattacks.
@Animez_UK @NCSC

Si les humains sont #hackables comme disait Yuval Noah #Harari, quelles sont nos options pour les réveiller?
Certains vaccinés semblent refuser de réfléchir aux sujets #Covid, malgré des faits, études, vidéos. On est face à un mur. Comment on pourrait #hacker cela? (suite..⏬)
Certains vaccinés semblent refuser de réfléchir aux sujets #Covid, malgré des faits, études, vidéos. On est face à un mur. Comment on pourrait #hacker cela? (suite..⏬)
Je poste des études mais l'argument logique ne marche pas sur tout le monde. Car cela implique de faire une pause pour y penser.
Je vois d'ailleurs une indifférence à chaque nouvelle étude, décès ou effet secondaire suite aux💉. Peut-être que c'est une mauvaise stratégie? ⏬
Je vois d'ailleurs une indifférence à chaque nouvelle étude, décès ou effet secondaire suite aux💉. Peut-être que c'est une mauvaise stratégie? ⏬
🇷🇺🇺🇦
Second attempt at starting a new Russia - Ukraine thread....fingers crossed !
The original Mega thread ends here
Second attempt at starting a new Russia - Ukraine thread....fingers crossed !
The original Mega thread ends here
🇷🇺🇺🇦
There is talk that the Ukr CinC Zaluzhny & Zelensky had a meeting during which the withdrawal from #Lisichansk agglomeration was discussed.
The only feasible way is going by the road to Seversk which is not physically cut but can be shelled from Rus held territory
There is talk that the Ukr CinC Zaluzhny & Zelensky had a meeting during which the withdrawal from #Lisichansk agglomeration was discussed.
The only feasible way is going by the road to Seversk which is not physically cut but can be shelled from Rus held territory

🇷🇺🇺🇦
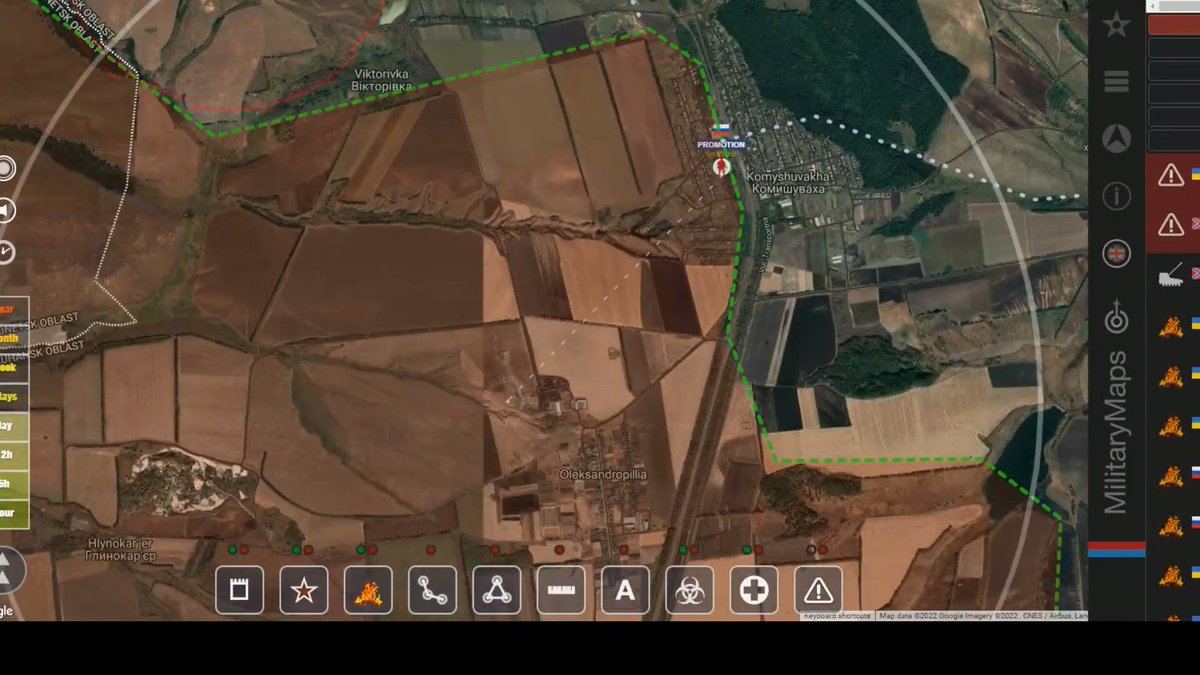
Situation at #Kamishevakha which is NE of Popasna & part of the Gorskoe (Hirske) - Zolotoe "bag"

Situation at #Kamishevakha which is NE of Popasna & part of the Gorskoe (Hirske) - Zolotoe "bag"

1/10
DIARIO DI GUERRA (GIORNO 77): DRAGHI RESTA DRAGHI, NUOVE ARMI PER KIEV (NONOSTANTE CONTE)
Il tentativo di far passare la ricerca della pace come un cambiamento della linea del premier sulla guerra in #Ucraina c'è stato.
DIARIO DI GUERRA (GIORNO 77): DRAGHI RESTA DRAGHI, NUOVE ARMI PER KIEV (NONOSTANTE CONTE)
Il tentativo di far passare la ricerca della pace come un cambiamento della linea del premier sulla guerra in #Ucraina c'è stato.

2/10
Quello di raccontarlo come un cedimento alle richieste dei "neutralisti" italici pure.
dangelodario.it/2022/05/10/cos…
Il Blog lo ha denunciato ieri, ma sarebbe bastato in verità seguire con costanza le dichiarazioni di Mario #Draghi da inizio guerra per evitare una figuraccia.
Quello di raccontarlo come un cedimento alle richieste dei "neutralisti" italici pure.
dangelodario.it/2022/05/10/cos…
Il Blog lo ha denunciato ieri, ma sarebbe bastato in verità seguire con costanza le dichiarazioni di Mario #Draghi da inizio guerra per evitare una figuraccia.
3/10
Draghi lo ha ribadito anche poco fa, nella conferenza stampa all'ambasciata d'Italia a Washington.
Qui trovate tutte le sue dichiarazioni:
Draghi lo ha ribadito anche poco fa, nella conferenza stampa all'ambasciata d'Italia a Washington.
Qui trovate tutte le sue dichiarazioni:
Alright, you wanted me to do it, so here goes.
A real quick and dirty tutorial on how to use #Universal #Radio #Hacker or #URH to do something useful.
A real quick and dirty tutorial on how to use #Universal #Radio #Hacker or #URH to do something useful.
You can find the tool here: github.com/jopohl/urh
It's a bit flaky at times, but it appears to support capture and replay on most hardware out in the field today, which is GREAT
It's a bit flaky at times, but it appears to support capture and replay on most hardware out in the field today, which is GREAT
The tool comes in useful when you're confronted with a radio link and want to find out the details (modulation, bitrate, etc) when those aren't made public by the manufacturer. It's also handy when you just have a signal and no device in hand.
Bir çoğunuzun haberi yoktur fakat geçtiğimiz hafta büyük bir kaç #ransomware vakası yaşandı. VmCenter açığından faydalanarak gerçekleştirilen bu saldırıdan 2 #datacenter etkilendi. Acilen olay yerine müdahale etmemiz istendi.
Saldırının analizini yapmak, zafiyete sebebiyet veren açığı tespit etmek, olası güvenlik tedbirleri vb çalışmaları yapmaya zaman yoktu. Yüzlerce sunucudan oluşan bir veri kaybının olduğu bir yerde önceliğin bu olması mantıklı da olmazdı zaten.
Birinci önceliğimiz tüm sistemi yeniden ayağa kaldırmak ve mağduriyeti gidermek olduğu için kolları sıvadık ve çalışmalara başladık. Öncesinde #hacker ile bazı iletişimler kurulduğunu ve bir miktar fidye ödendiğini olay yerine ulaştıktan sonra öğrendik.
#POV alla #DoctorManhattan. Accade tutto contemporanamente
È il 2022, siamo in un conflitto devastante che minaccia il cuore dell'#Europa
È il 1957, un ragazzino non vedente di nome Joe Engressia scopre che fischiando una particolare nota i nastri registrati che ascolta al
È il 2022, siamo in un conflitto devastante che minaccia il cuore dell'#Europa
È il 1957, un ragazzino non vedente di nome Joe Engressia scopre che fischiando una particolare nota i nastri registrati che ascolta al
telefono si bloccano. Incuriosito chiama la compagnia telefonica. John Draper scopre che non serve l'orecchio assoluto: basta un fischietto.
È il 2022, e la #Russia pensa a come censurare tutte le informazioni che dimostrano che la loro #liberazione dell'#Ucraina è solo una
È il 2022, e la #Russia pensa a come censurare tutte le informazioni che dimostrano che la loro #liberazione dell'#Ucraina è solo una
Mini thread 1/ #Ucraina sotto attacco #hacker, allarmi bomba quotidiani, #troll e macchina della #propaganda in azione. #Esercito regolare sui confini come forma di deterrenza, #wagner e paramilitari in #Donbass
2/ Ci sono tutti gli ingredienti principali della #guerranonlineare della #Russia. #Putin vuole il riconoscimento della #Crimea come soggetto della #Federazionerussa, la garanzia che #Ucraina non entrerà mai nella #Nato
3/ L’obiettivo della strategia russa è destabilizzare l’#Ucraina dall’interno, polarizzare il dibattito politico e nella società civile en #occidente e che parte dell’opinione pubblica internazionale pensi che la #Russia ha ragione




